Day 35 of 90DaysOfDevOps Challenge: Enhancing MySQL Deployment with ConfigMaps and Secrets 🔒🔑🛡️
 ANSAR SHAIK
ANSAR SHAIK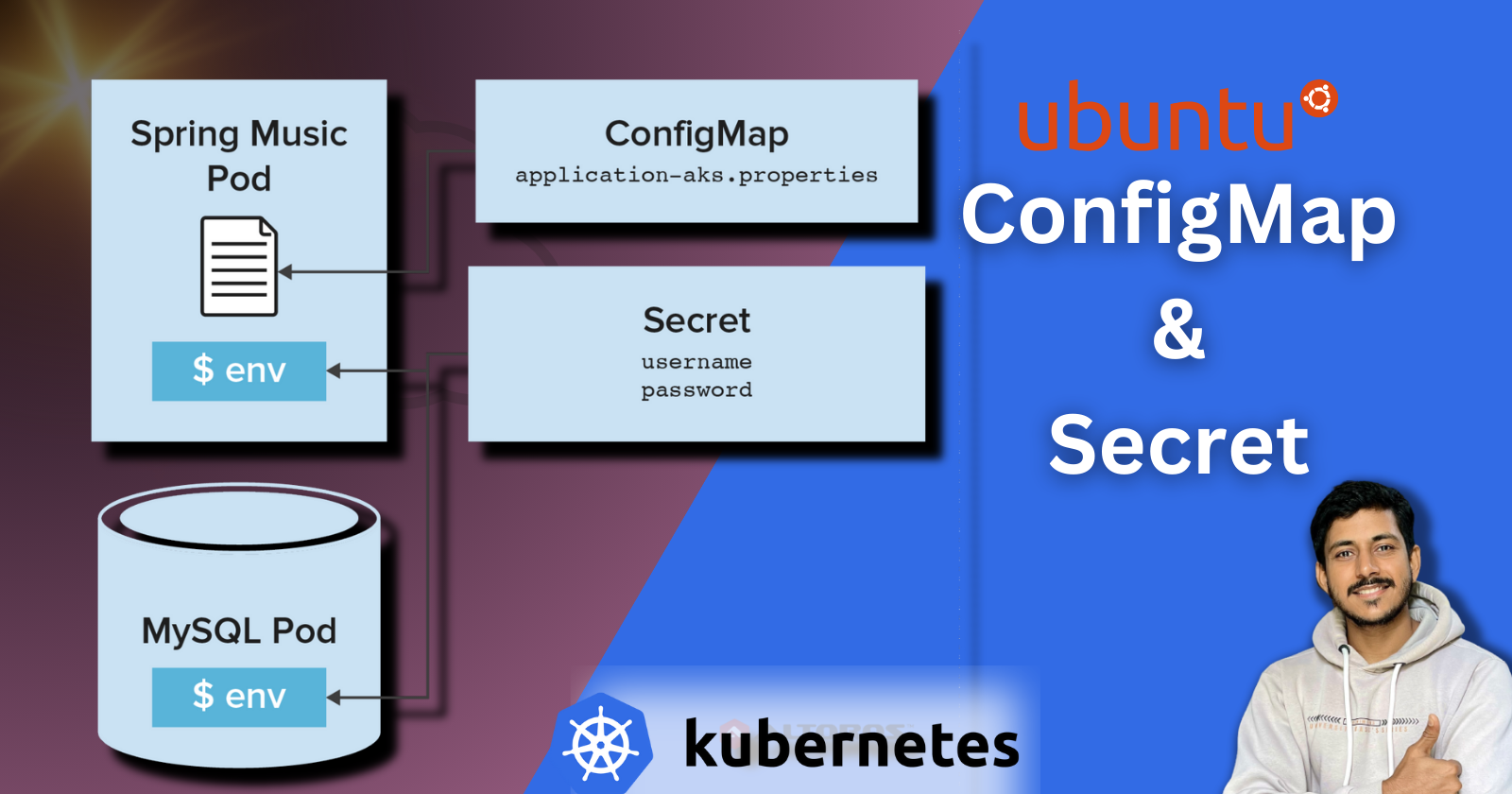
Introduction
Welcome back to the 90DaysOfDevOps challenge! On Day 35, we're taking our MySQL deployment to the next level by incorporating ConfigMaps and Secrets in Kubernetes. These powerful tools will enable us to manage configurations seamlessly and secure sensitive information.
What are ConfigMaps and Secrets in Kubernetes?
ConfigMaps enable the separation of configuration details from containerized applications. They store configuration data, like environment variables or command-line arguments, in key-value pairs. ConfigMaps simplify the management of configurations, allowing updates without altering application code.
Secrets focus on securing sensitive information such as passwords or API keys. Kubernetes Secrets encode and store confidential data, preventing easy exposure. They support various data types, including key-value pairs, SSH keys, or binary content.
Now, let's embark on the hands-on tasks for today.
MySQL Deployment YAML Overview
Before we dive into the enhancements, let's review the current state of our MySQL deployment YAML (mysql-deployment.yml).
apiVersion: apps/v1
kind: Deployment
metadata:
name: mysql-deployment
namespace: mysql
labels:
app: mysql
spec:
replicas: 1
selector:
matchLabels:
app: mysql
template:
metadata:
labels:
app: mysql
spec:
containers:
- name: mysql-container
image: mysql
ports:
- containerPort: 3306
env:
- name: MYSQL_DATABASE
valueFrom:
configMapKeyRef:
name: mysql-configmap
key: MYSQL_DATABASE
- name: MYSQL_ROOT_PASSWORD
valueFrom:
secretKeyRef:
name: mysql-secret
key: MYSQL_PASSWORD
In this YAML, we have a basic MySQL deployment with specified ports and environment variables. Now, let's enhance it with ConfigMaps and Secrets.
Task 1: ConfigMaps for MySQL Configuration
Step 1: Creating a ConfigMap
Before implementing ConfigMaps, let's review our initial MySQL deployment YAML (mysql-deployment.yml).
yamlCopy codeapiVersion: apps/v1
kind: Deployment
metadata:
name: mysql-deployment
namespace: mysql
labels:
app: mysql
spec:
replicas: 1
selector:
matchLabels:
app: mysql
template:
metadata:
labels:
app: mysql
spec:
containers:
- name: mysql-container
image: mysql
ports:
- containerPort: 3306
Pods Status in mysql namespace:
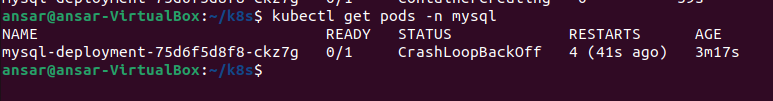
Start by creating a ConfigMap named mysql-configmap to manage MySQL configuration.
Through Command Line:
kubectl create configmap mysql-configmap --from-literal=MYSQL_DATABASE=mydatabase -n mysql
Through YAML file:

Step 2: Updating MySQL Deployment with ConfigMap
Now, update the deployment YAML to include references to the ConfigMap for MYSQL_DATABASE.
# Inside mysql-deployment.yml
env:
- name: MYSQL_DATABASE
valueFrom:
configMapKeyRef:
name: mysql-configmap
key: MYSQL_DATABASE
Step 3: Applying the Updated Deployment
Apply the updated deployment to incorporate the ConfigMap.
kubectl apply -f mysql-deployment.yml -n mysql
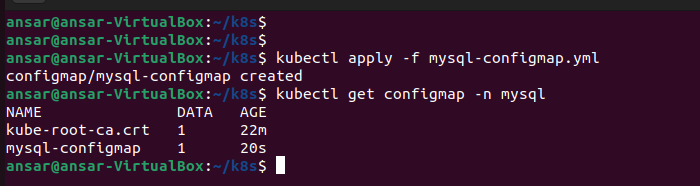
Step 4: Verifying ConfigMap Integration
Check the status of the ConfigMap integration within the MySQL namespace.
kubectl get configmaps -n mysql
Task 2: Secrets for MySQL Root Password
Step 1: Creating a Secret
Create a secret named mysql-secret to securely store the MySQL root password.
Through Command Line:
kubectl create secret generic mysql-secret --from-literal=MYSQL_PASSWORD=<your-password> -n mysql
Through YAML file:
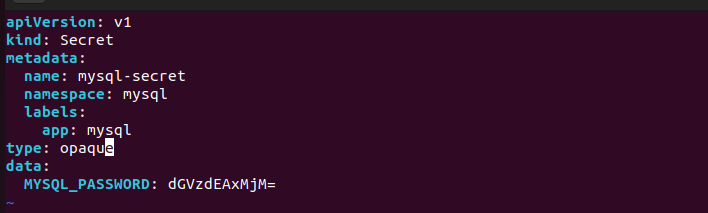
We need to provide encoded password(Use base64 for encoding):
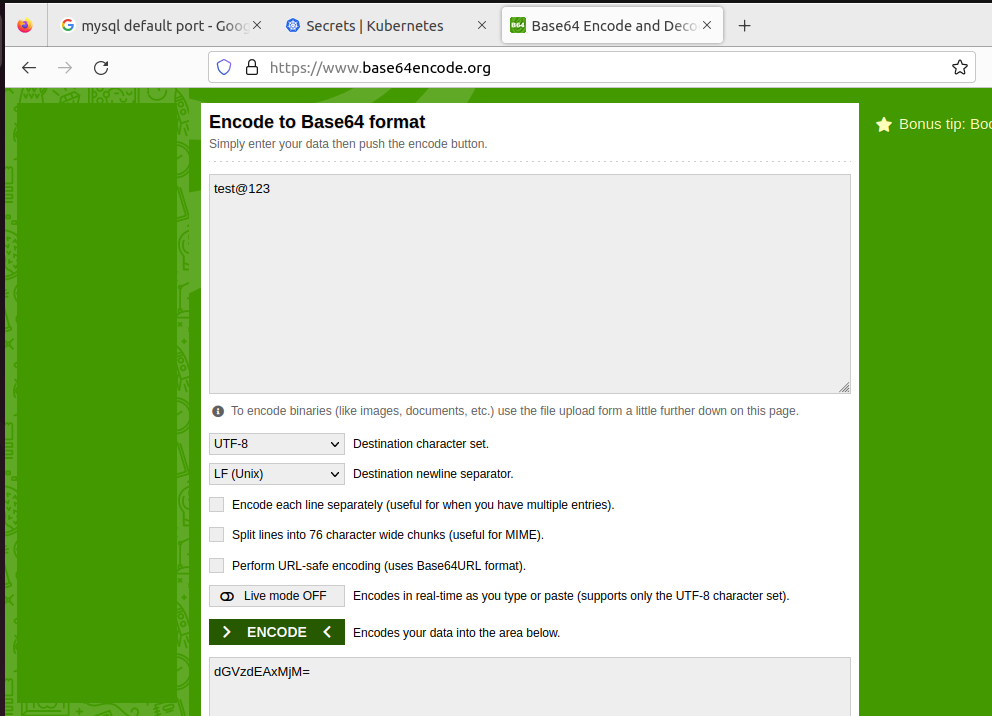
Step 2: Updating MySQL Deployment with Secret
Update the deployment YAML to reference the secret for MYSQL_ROOT_PASSWORD.
# Inside mysql-deployment.yml
env:
- name: MYSQL_ROOT_PASSWORD
valueFrom:
secretKeyRef:
name: mysql-secret
key: MYSQL_PASSWORD
Step 3: Applying the Updated Deployment
Apply the updated deployment to incorporate the secret.
kubectl apply -f mysql-deployment.yml -n mysql
Step 4: Verifying Secret Integration
Check the status of the secret integration within the MySQL namespace.
kubectl get secrets -n mysql
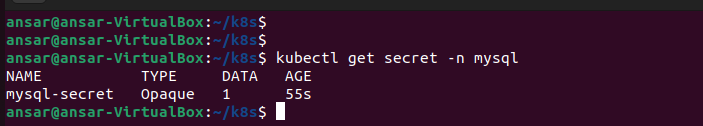
Pods Status in mysql namespace:
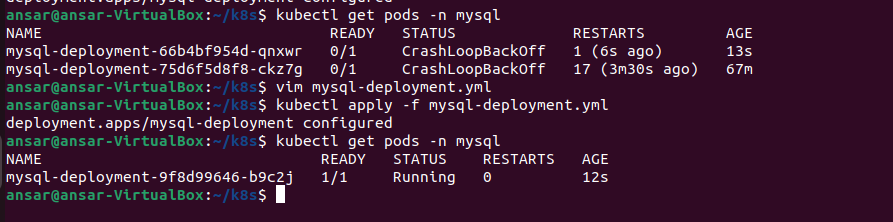
Conclusion
Congratulations! You've successfully elevated your MySQL deployment by integrating ConfigMaps for configuration management and Secrets for secure password storage. These practices enhance the efficiency and security of your Kubernetes applications. Stay tuned for more challenges in the 90DaysOfDevOps journey! 🔒🚀
Subscribe to my newsletter
Read articles from ANSAR SHAIK directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

ANSAR SHAIK
ANSAR SHAIK
AWS DevOps Engineer