Mastering ConfigMaps and Secrets in Kubernetes
 Amit Parad
Amit Parad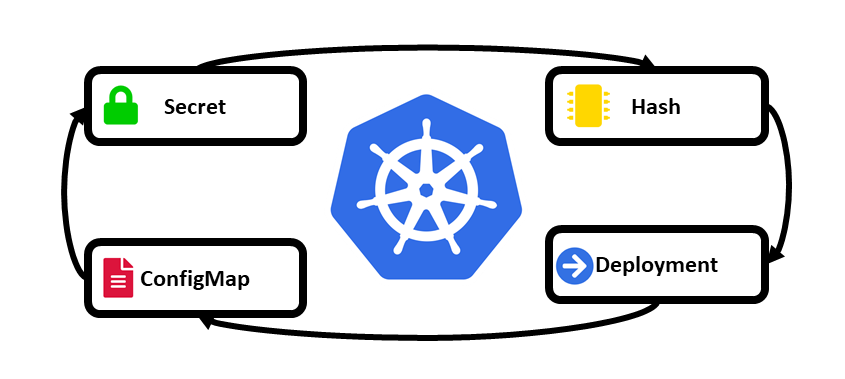
What are ConfigMaps and Secrets in k8s?
In Kubernetes, ConfigMaps and Secrets are used to store configuration data and secrets, respectively. ConfigMaps store configuration data as key-value pairs, while Secrets store sensitive data in an encrypted form.
Example:- Imagine you're in charge of a big spaceship (Kubernetes cluster) with lots of different parts (containers) that need information to function properly. ConfigMaps are like a file cabinet where you store all the information each part needs in simple, labeled folders (key-value pairs). Secrets, on the other hand, are like a safe where you keep important, sensitive information that shouldn't be accessible to just anyone (encrypted data). So, using ConfigMaps and Secrets, you can ensure each part of your spaceship (Kubernetes cluster) has the information it needs to work properly and keep sensitive information secure!
Task 1:
Create a ConfigMap for your Deployment
Create a ConfigMap for your Deployment using a file or the command line
Verify that the ConfigMap has been created by checking the status of the ConfigMaps in your Namespace
Update the deployment.yml file to include the ConfigMap
Apply the updated deployment using the command:
kubectl apply -f deployment.yml -n <namespace-name>
Steps:
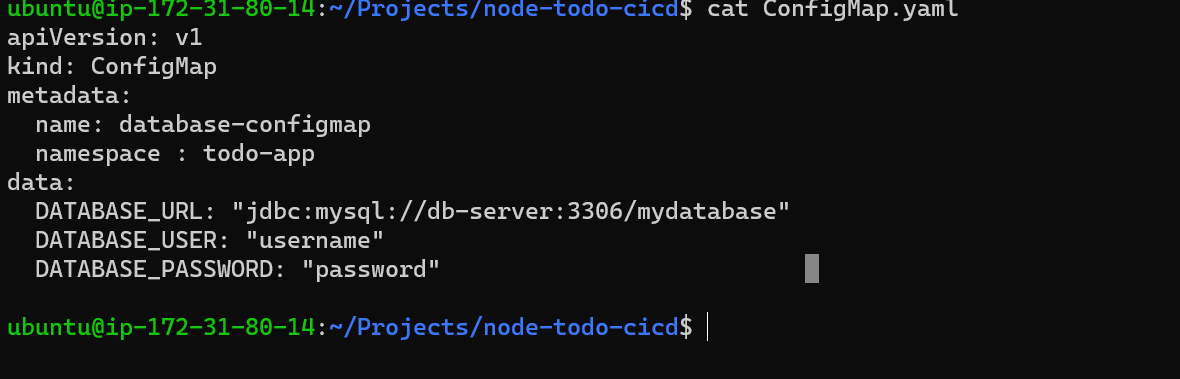
Step 1: Lets begin with creating ConfigMap.yaml with below syntax
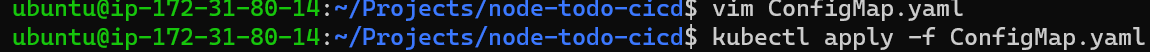
Step 2: Create ConfigMap using kubectl apply -f configMap.yaml command and verrify the same.
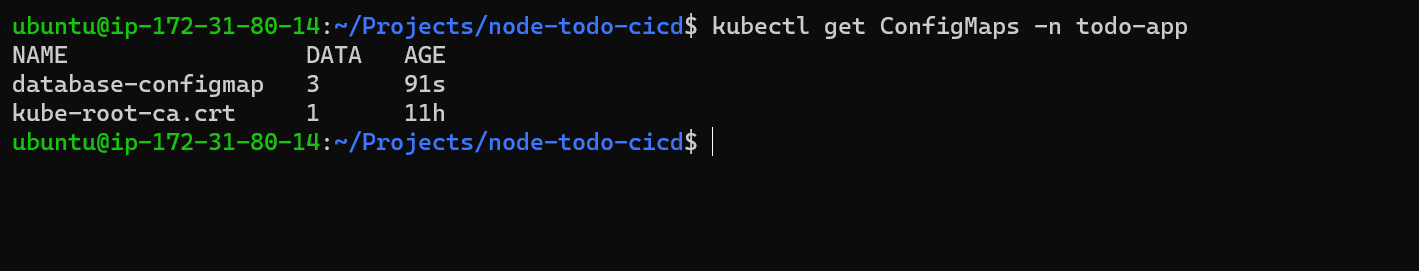
While using with describe command we can check more details for configmap.
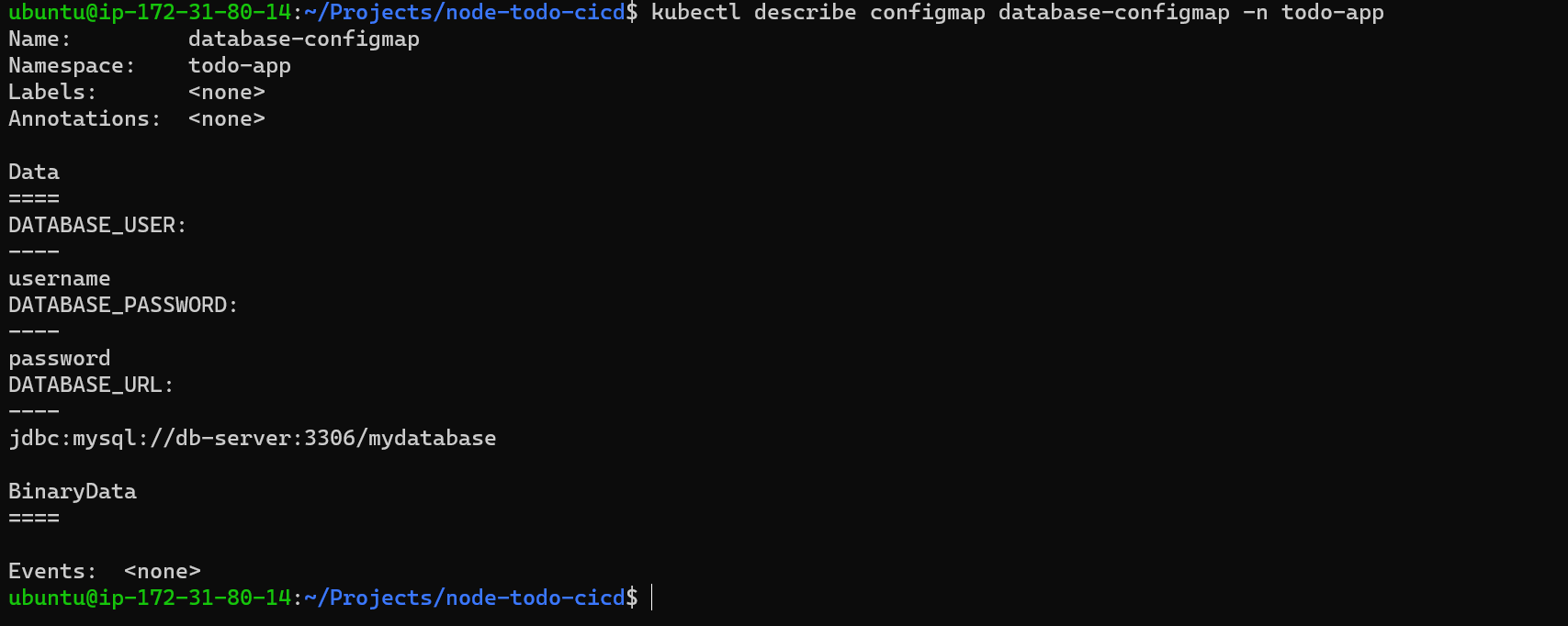
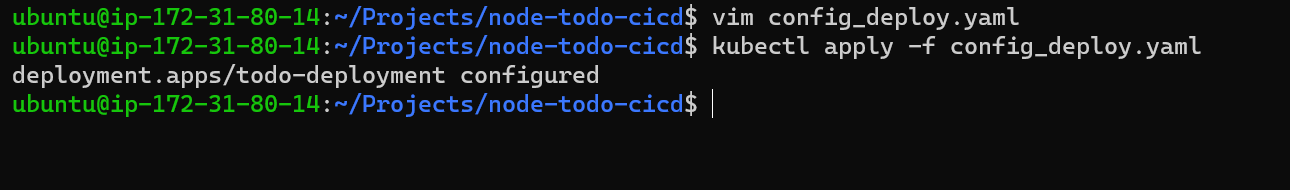
Step 3: Now update deployment.yaml file and add configmap details like below.
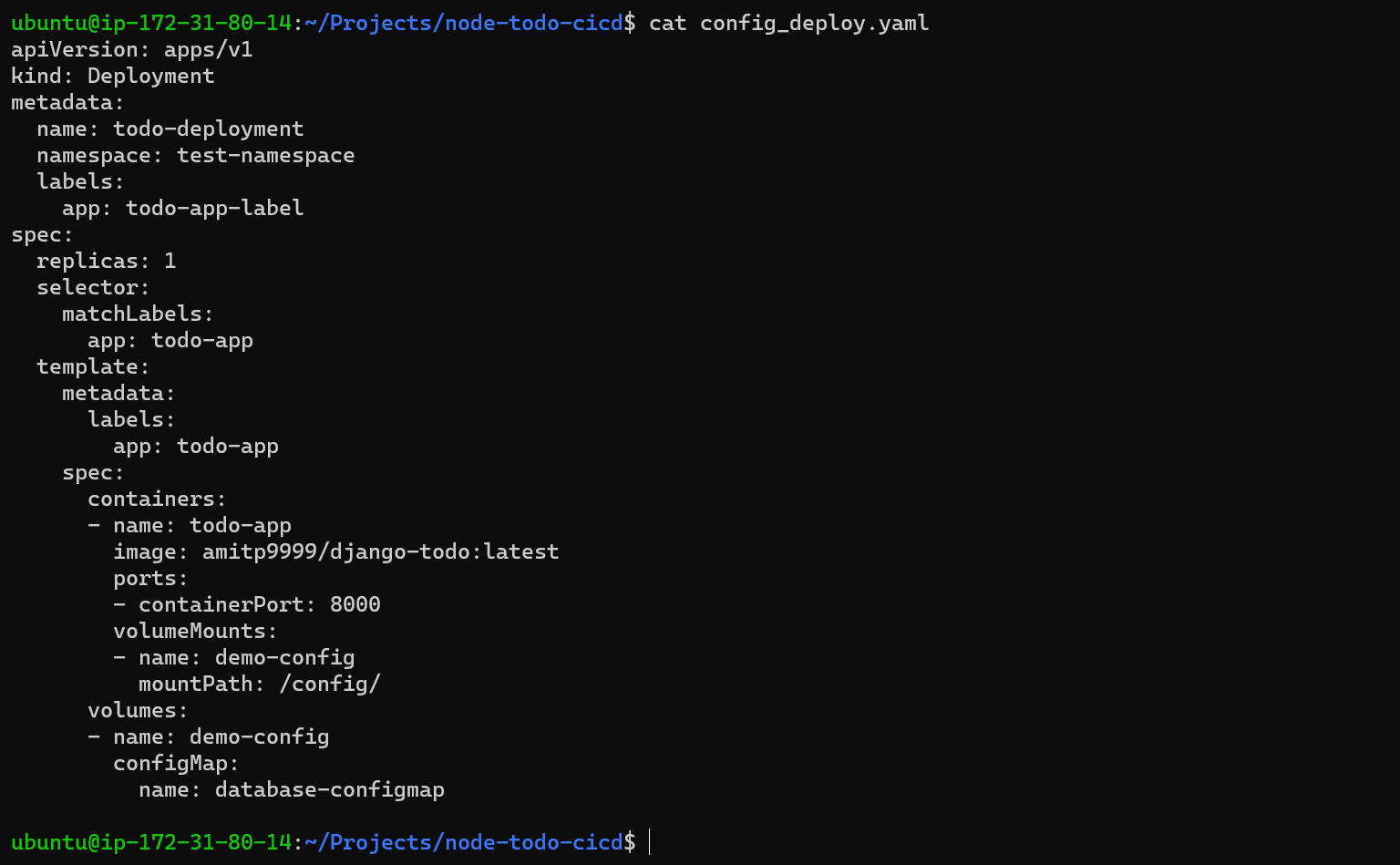
Step 4: Apply the deployment file and check pod's details
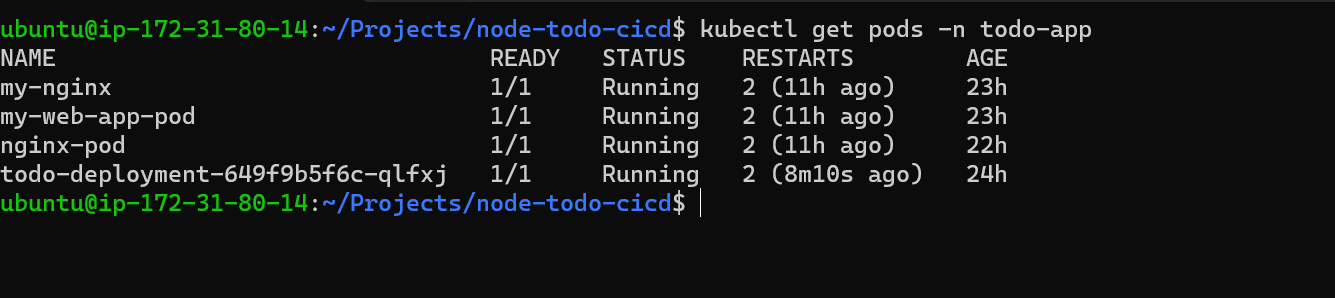
We can use the following command to view the key-value pairs of a variable in a ConfigMap inside a cluster or a pod:
kubectl exec -it <pod-name> -- bash
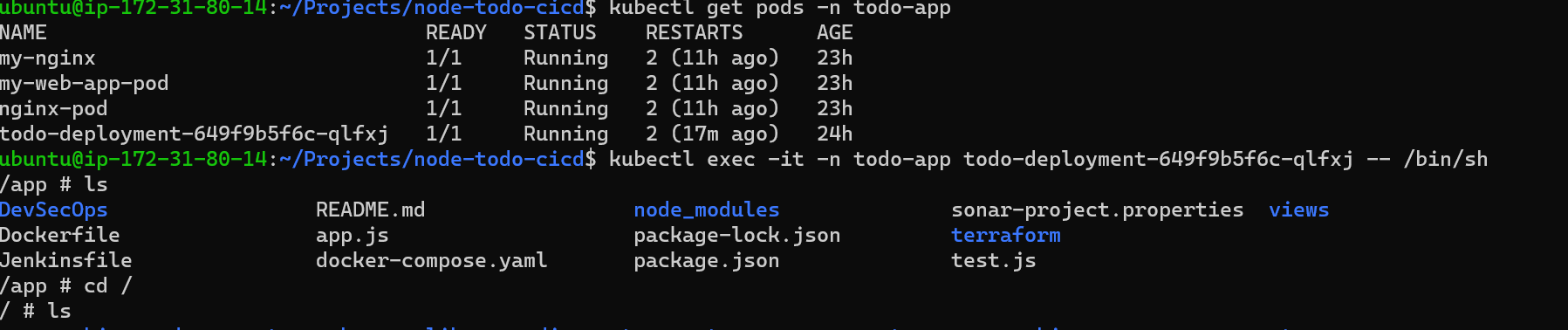
Task 2:
Create a Secret for your Deployment
Create a Secret for your Deployment using a file or the command line
Update the deployment.yml file to include the Secret
Apply the updated deployment using the command:
kubectl apply -f deployment.yml -n <namespace-name>Verify that the Secret has been created by checking the status of the Secrets in your Namespace.
-Solution
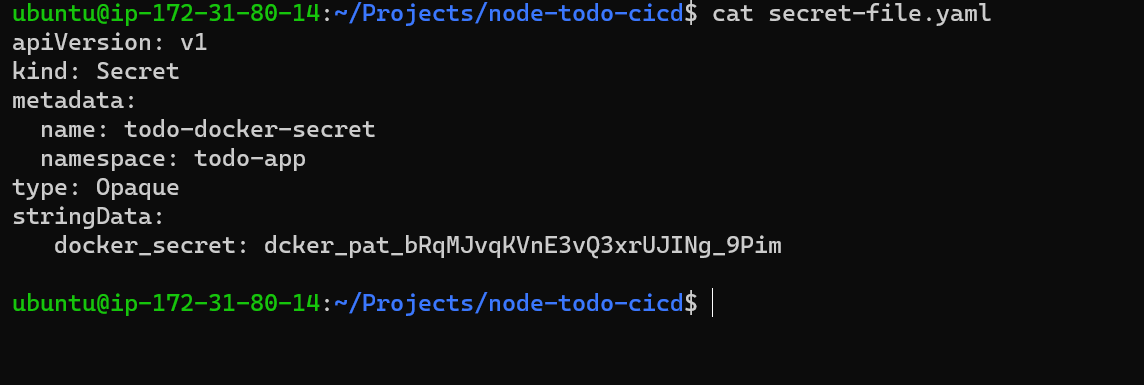
Step 1: Let's create secret-file.yaml and mention the secret (For our task I have created a secret for docker login)
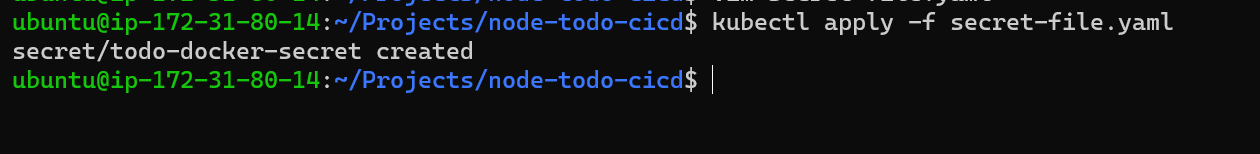
Step 2: With kubectl apply -f secret-file.yaml we will create a secret in todo-app namespace.
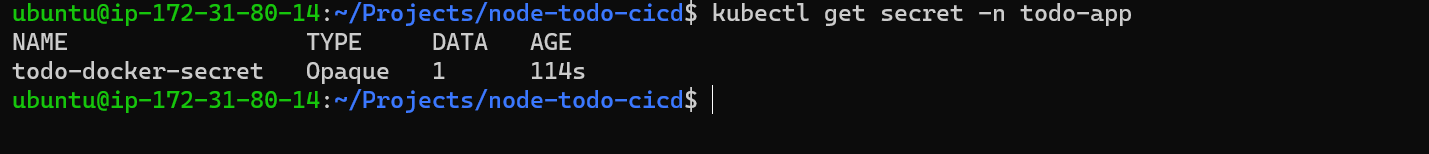
Step 3: Verify the sceret.
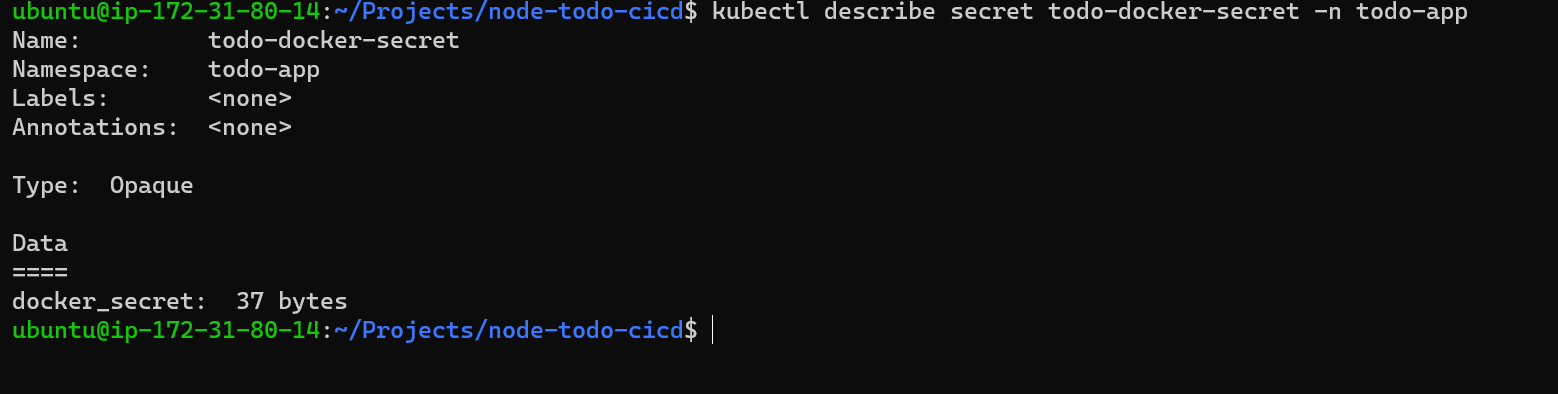
Step 4: Updated deployment.yaml file with secrete and deploy in kubernetes.
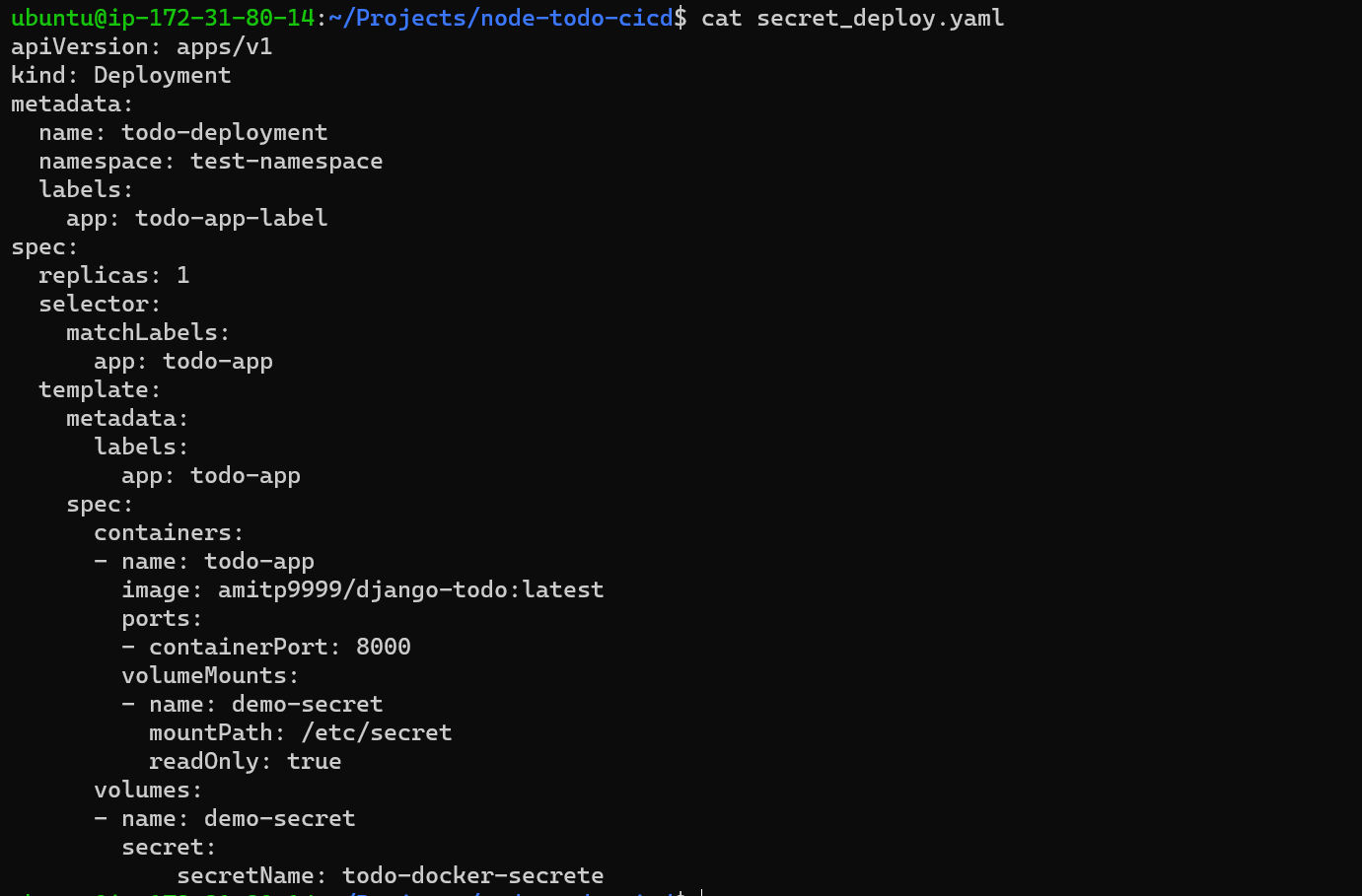
In above file we have added VolumeMount path /etc/secret will create a new directory and saves the secret file. Even added "readonly" parameter to restrict it from the edit.
Post this we can use the command "kubectl apply -f secret-deploy.yaml"
& with kubectl get pods -n todo-app we are able to se the new todo-app-django container has been created in pod.
Ultimately, ConfigMaps and Secrets play pivotal roles in overseeing application configurations and safeguarding critical data within a Kubernetes setup. ConfigMaps handle configuration data, covering aspects like environment variables, command-line arguments, and configuration files. In contrast, Secrets securely store sensitive information like passwords, API keys, and credentials.
Thank You!!
Happy Learning !!
Subscribe to my newsletter
Read articles from Amit Parad directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Amit Parad
Amit Parad
Experienced Cloud / DevOps Engineer with a passion for automating infrastructure and streamlining software delivery processes. Skilled in AWS, Docker, Kubernetes, CI/CD pipelines, Ansible, Terraform & Jenkins. Proven ability to collaborate with development, operations, and QA teams to ensure efficient and reliable deployments.