Day 35: Mastering ConfigMaps and Secrets in Kubernetes🔒🔑🛡️
 Maher Messaoudi
Maher Messaoudi
1.ConfigMaps
In Kubernetes, ConfigMaps and Secrets are used to store configuration data and secrets, respectively. ConfigMaps store configuration data as key-value pairs, while Secrets store sensitive data in an encrypted form.
- Example:- Imagine you're in charge of a big spaceship (Kubernetes cluster) with lots of different parts (containers) that need information to function properly. ConfigMaps are like a file cabinet where you store all the information each part needs in simple, labeled folders (key-value pairs). Secrets, on the other hand, are like a safe where you keep important, sensitive information that shouldn't be accessible to just anyone (encrypted data). So, using ConfigMaps and Secrets, you can ensure each part of your spaceship (Kubernetes cluster) has the information it needs to work properly and keep sensitive information secure! 🚀
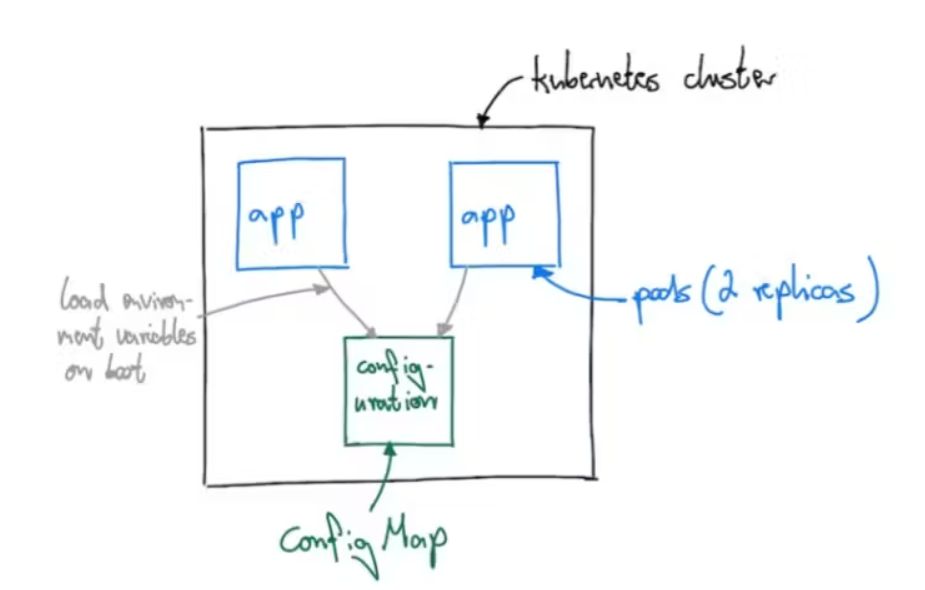
ConfigMaps are Kubernetes objects that allow you to separate configuration data/files from image content to keep containerized applications portable.
ConfigMaps bind configuration files, command-line arguments, surroundings variables, port numbers, and alternative configuration artifacts to your Pods containers and system parts at run-time.
ConfigMaps are helpful for storing and sharing non-sensitive, unencrypted configuration data. Like Secrets, you’ll be able to produce config maps from files and with yaml declaration.
2.Secrets in Kubernetes:
If you are deploying some containerized applications in Kubernetes the configuration of these applications contains some sensitive data such as usernames, passwords, keys, etc. This data is very sensitive in nature it is strongly recommended that not use that sensitive data in plain text format in the manifest file.
3.How do you manage such sensitive data in Kubernetes?
The answer is Kubernetes secrets, let’s start exploring Kubernetes secrets.
Kubernetes secret is an object that contains a small amount of sensitive data which includes passwords, keys, tokens, etc. It Secrets is the solution to handling and managing the secrets inside pod manifest files, so the main aim of the secrets is to reduce the risk of accidental exposure of confidential data.
Kubernetes secrets are created outside of Pods, once it gets created it can be deployed on any pod and any number of times, so we do create secrets before it can be used anywhere inside the pod.
K8’s secrets are stored inside etcd database on Kubernetes.
You can store secrets as:
Literal Value
File
Directory
The maximum size of kubernetes secrets is 1 MB. so secrets cannot be more than 1 MB.
Once secrets are created the question is how do we inject into a pod?
There are two ways to inject secrets into pods:
Volumes
Env variables
You can mount secrets as volume or expose secrets as environment variables inside a Pod.
There are two ways to create secrets :
kubectl command
Manifest File
Task 1:
Create a ConfigMap for your Deployment
Create a ConfigMap for your Deployment using a file or the command line
Update the deployment.yml file to include the ConfigMap
Apply the updated deployment using the command:
kubectl apply -f deployment.yml -n <namespace-name>Verify that the ConfigMap has been created by checking the status of the ConfigMaps in your Namespace.
There are many ways to create a config map, like from literal[key-value pair],from file and yaml file also.
Step1:
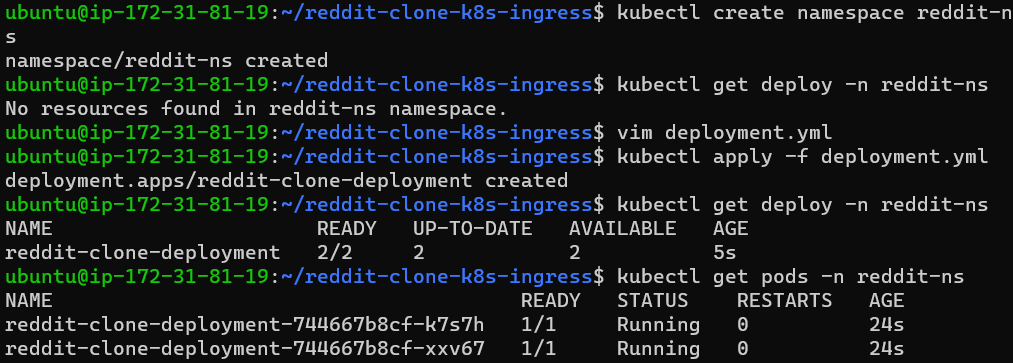
Create a namespace and just mention the created namespace inside of your previously created deployment file[reddit-clone project].
Then check whether deployment and pods are properly created or not and their status also, as deployment and pods are now a part of a particular namespace so, to check their status execute the command below.
Step 2:
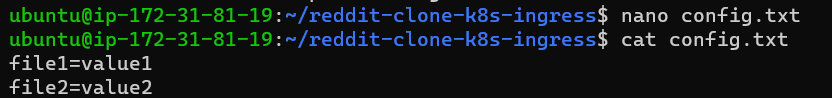
This is the first method of creating the configmap(cm)from the command line from the file method, for that create a file first and mention that file like below.
Then check the created configmap's status.
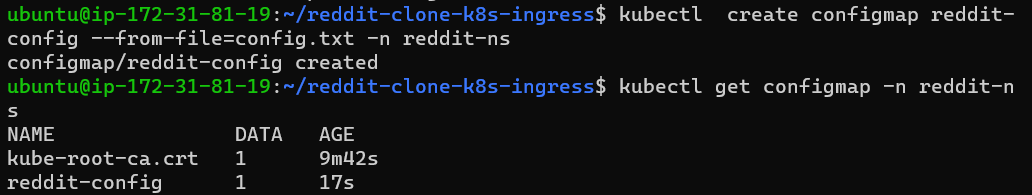
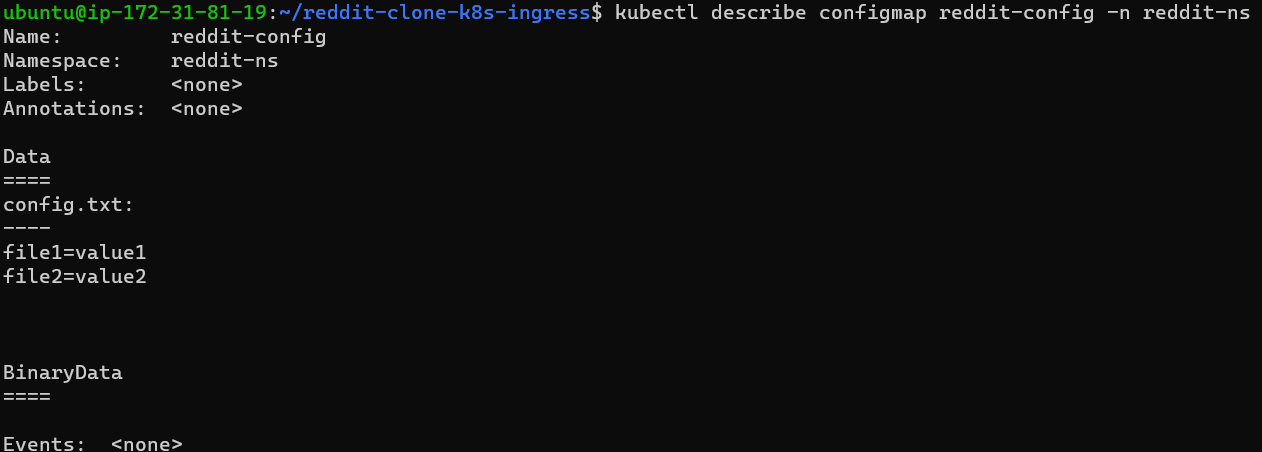
Step 3:
Now describe the created configmap and see that it is a plain text file that will be visible to all,configmaps are not secure for sensitive data.
kubectl describe configmap reddit-config -n reddit-ns
Step 4:
This is the most useful method to create a cm by writing a manifest yaml file.
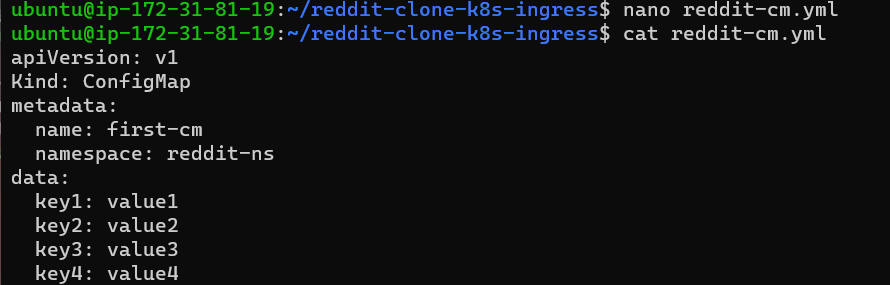
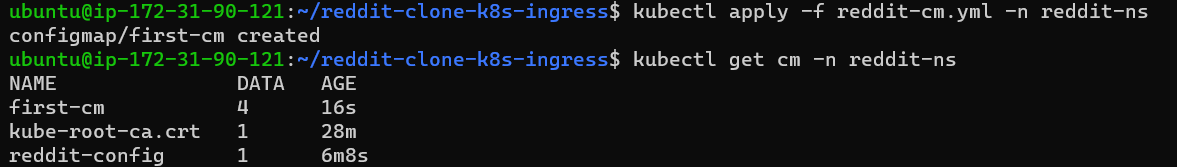
Step 5:
Describe the cm as the below image.
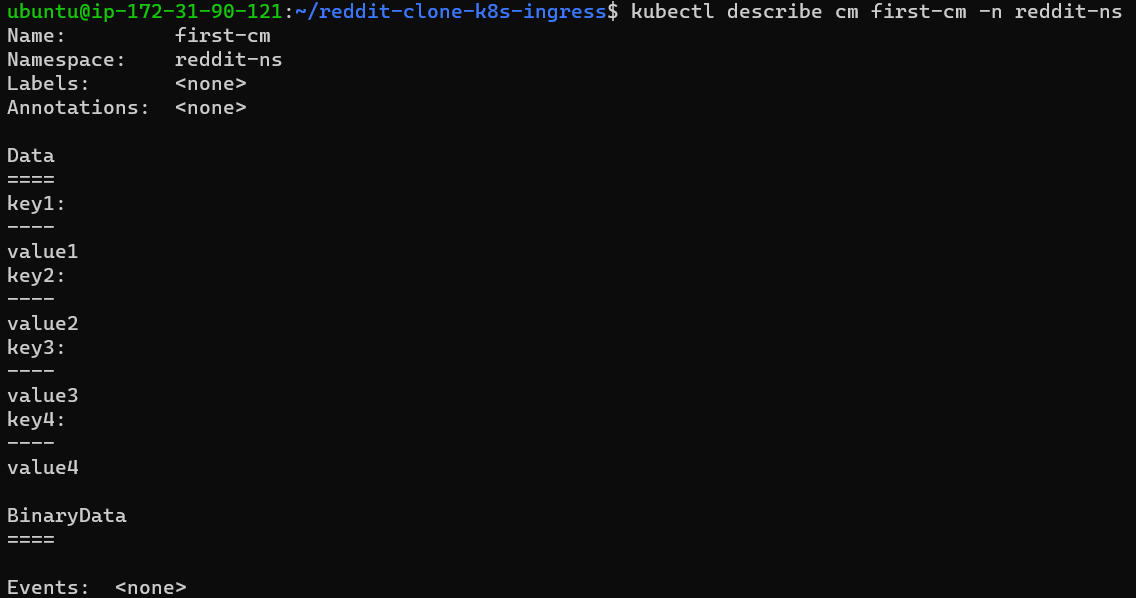
Step 6:
You can enter the data in yaml file by giving a pipe(|) symbol in the key section followed by their value.
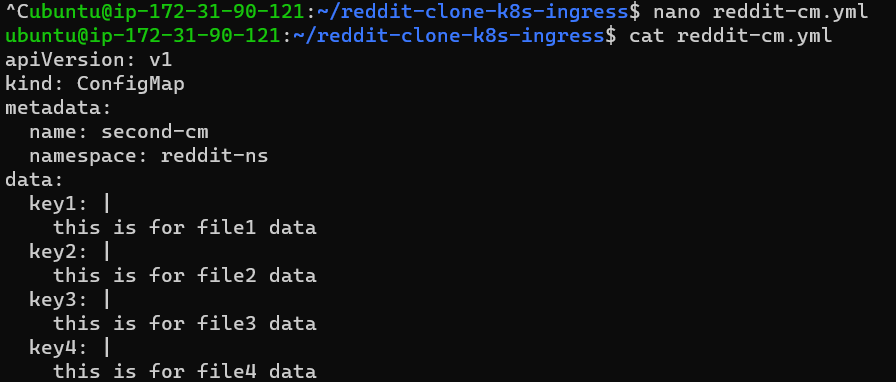
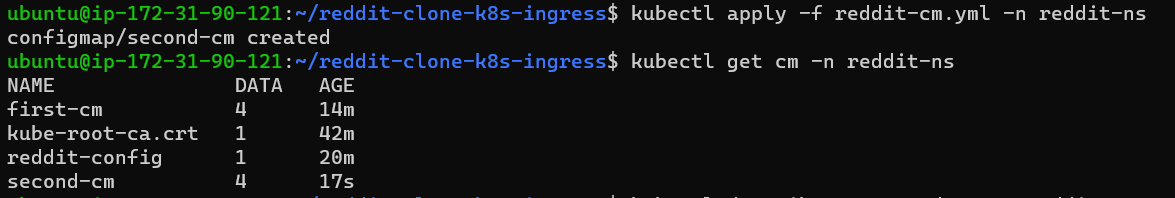
Step 7:
Describe the created cm .
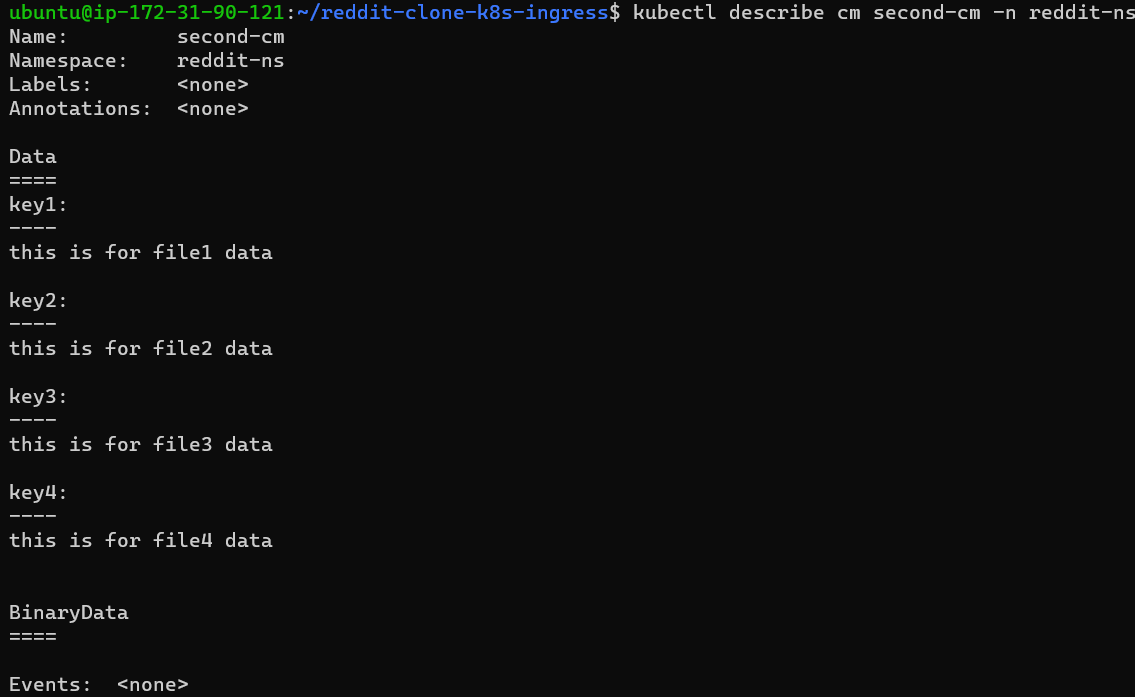
Step 8:
Okay. Now it's time to inject the created in the pods.
There are two ways to mount the config maps as data volumes or environment variables to be used by a container in a pod.
Inject the created cm inside the pod as an environment variable(check the last three lines of deployment file envFrom pod's section)and mention the cm name which you want to add to the pod.
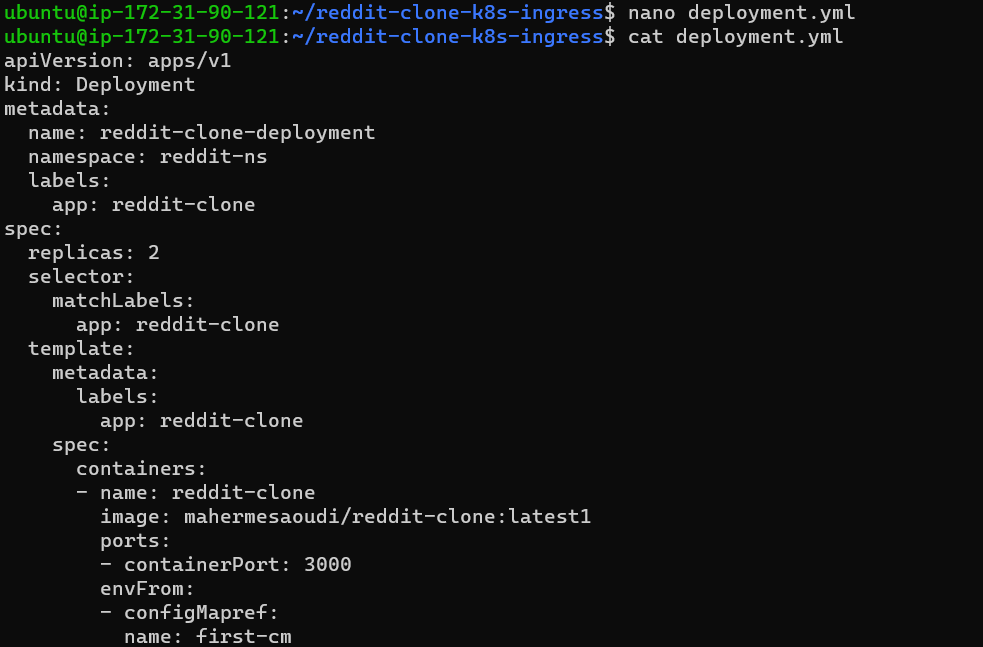
Step 9:
Now create the deployment and check the status of the deployment, pods.
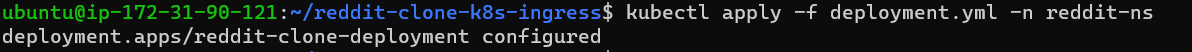
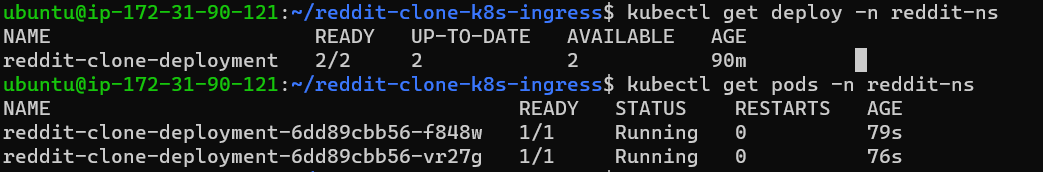
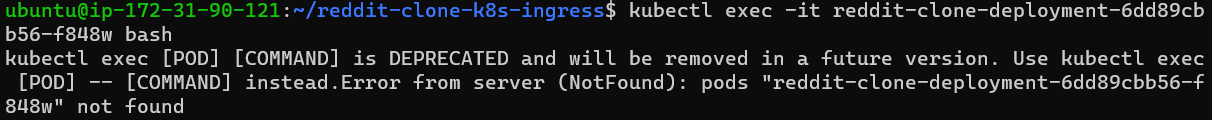
Step 10:
I was getting this error because of the pod's name(not sure)while trying to exec into the container.
So, I created a pod of nginx image as an example.
Step 11:
Mention the env variable inside the pod's section and create the pod. nano pod.yml
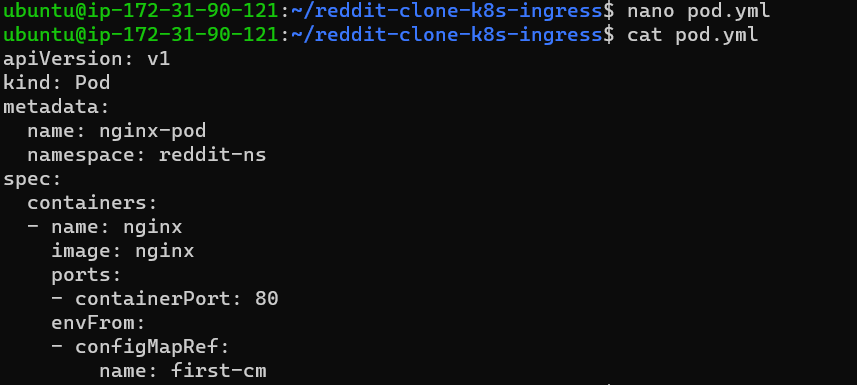
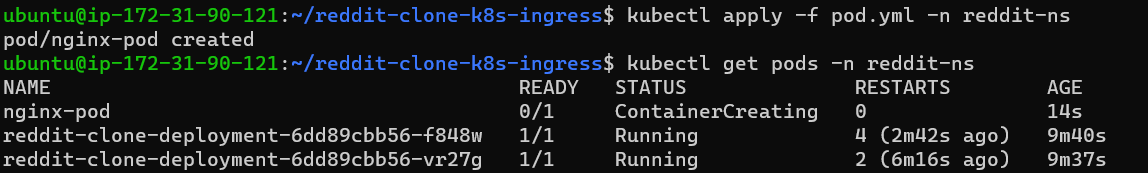
Step 12:
Now go inside the container to check if the configmap got injected or not, and run the env command .
you can see that (check from key4=value1) cm got injected successfully as an env variable.
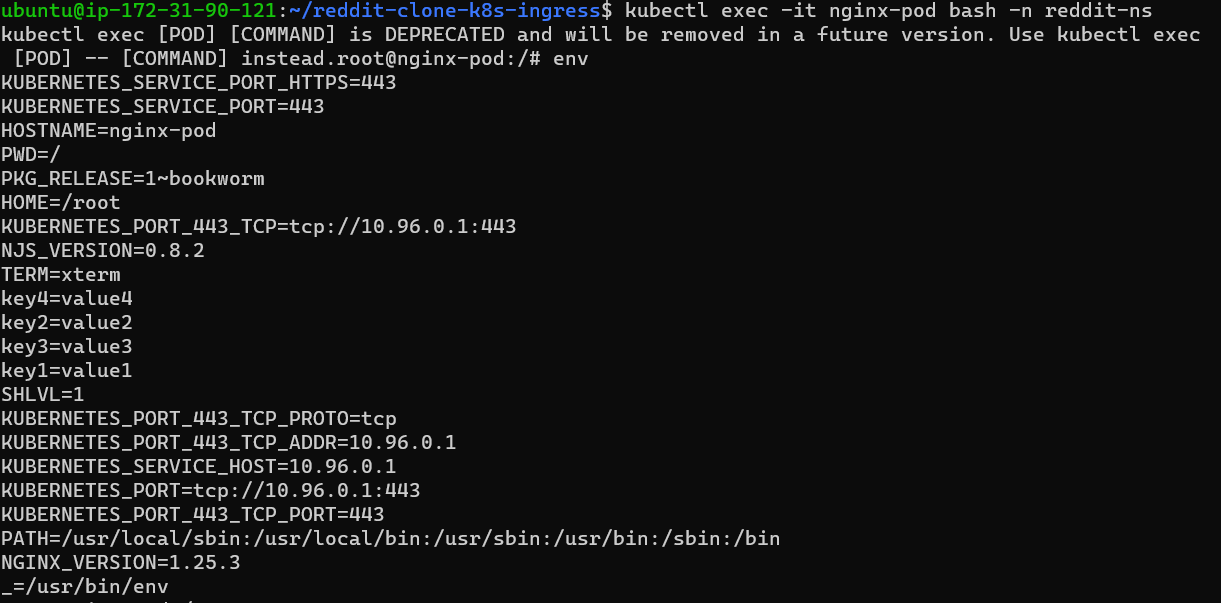
Step 13:
Now, a config-map file can be mounted inside a pod as volume.
Create a pod and create the volume(check from the volumeMounts part) to inject the cm as a volume. nano pod.yml
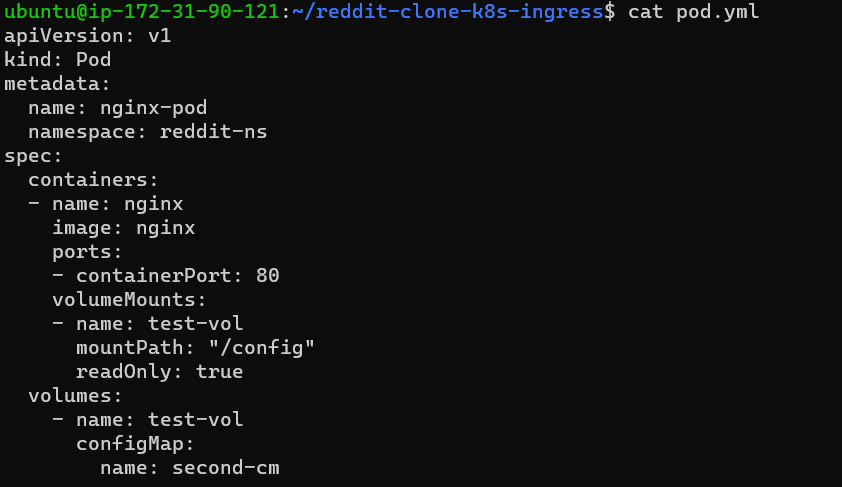
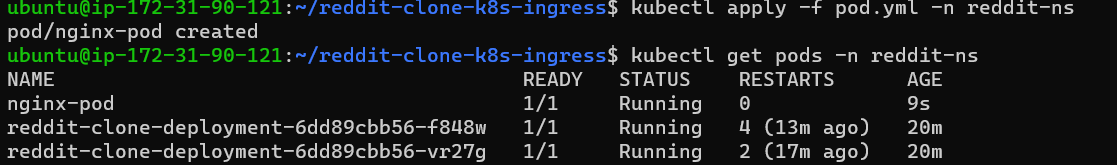
Step 14:
Check the volume,go inside of the pod by executing the exec command and search for the volume mount path(here it is config).
volumes mounted successfully(do ls).
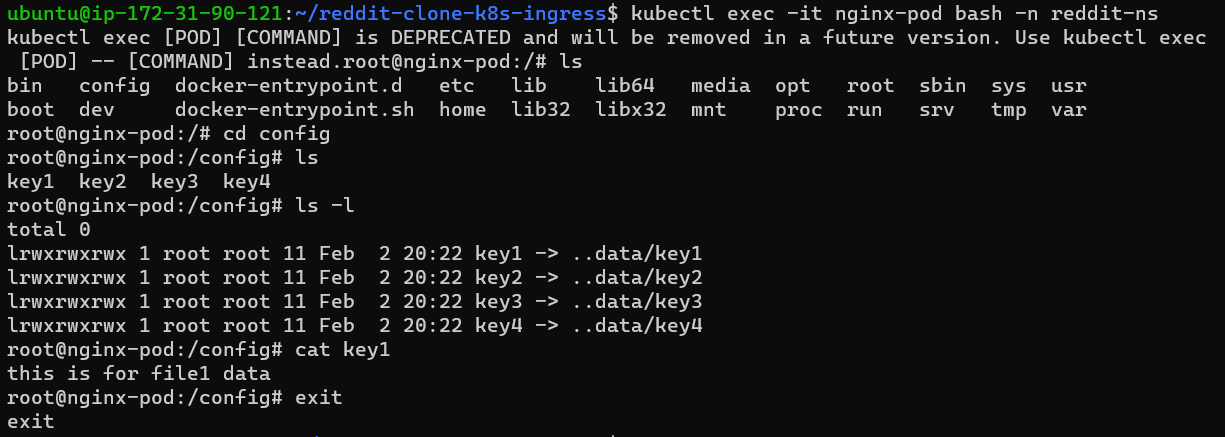
3.Task 2:
Create a Secret for your Deployment
Create a Secret for your Deployment using a file or the command line
Update the deployment.yml file to include the Secret
Apply the updated deployment using the command:
kubectl apply -f deployment.yml -n <namespace-name>Verify that the Secret has been created by checking the status of the Secrets in your Namespace.
Step 1:
Secrets can be created as same as configmap, the same way and steps too.
The difference only that you can't see the secrets file in plain text as it will be encrypted way whenever you will mention the file(such as your database password or any other sensitive data) as secret.It helps keep sensitive data and refer to that in your container.
Create a file and write some data inside it(such as your username,password etc.)
When you will check a secret's status type will show in Opaque format and if you will describe the secret like cm it will show the data in byte format.
Now, like cm try to mount the secret file as env format and mention the created secret name.
nano secret.yml
username and password should be converted to base64
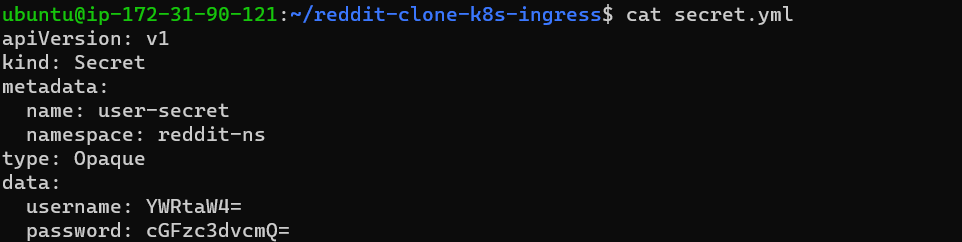
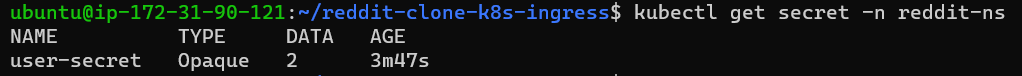
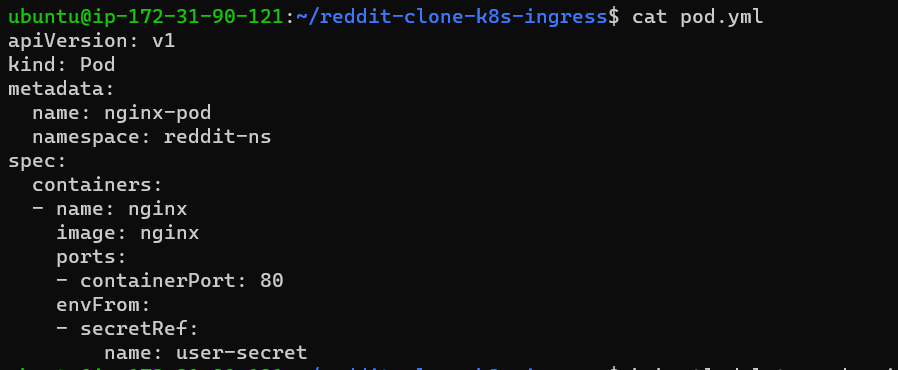
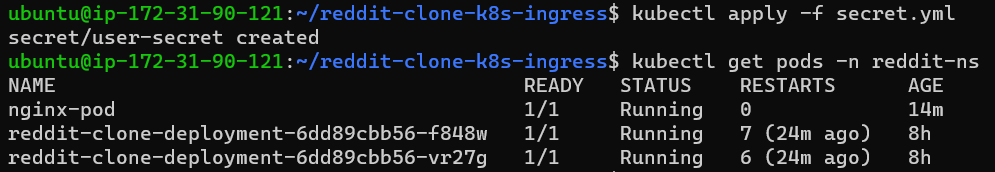
step 2:
now exec the pod and run the env command.
After running the env command the secret file will now show in a plain text format(only the created user can check that but no one else can access it).
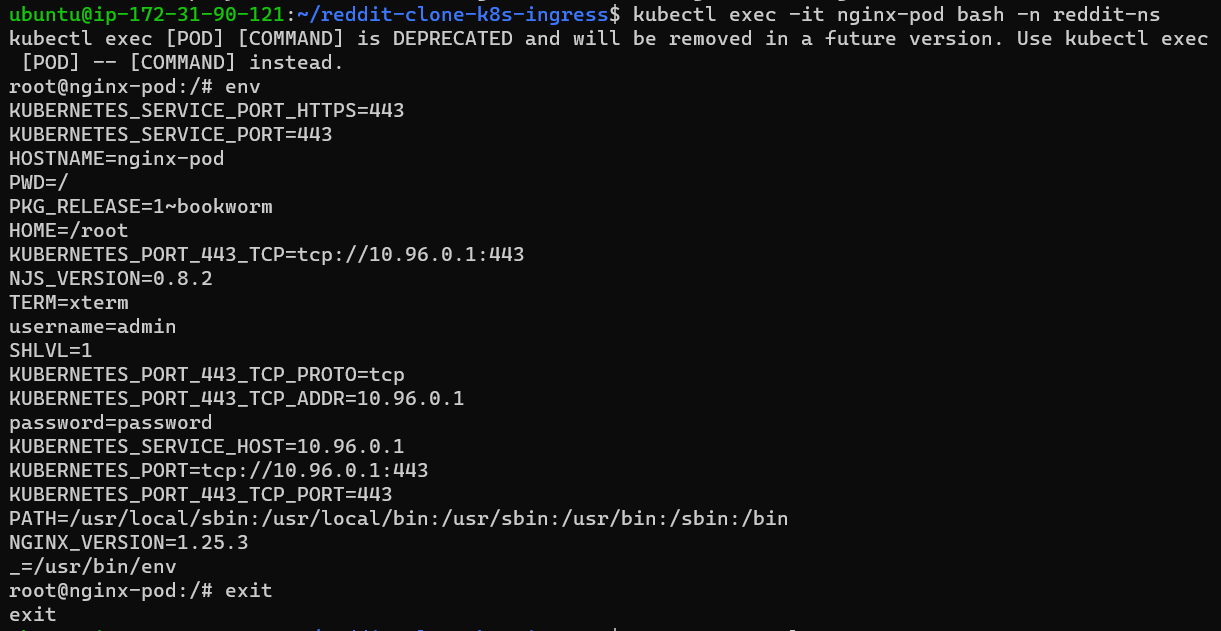
Step 3:
Now create another yaml file,remember that whenever you keep any data inside of a yaml file don't put the value directly, always convert the data(like a password or IP addresses) into base64 format like the below format(an encrypted way).
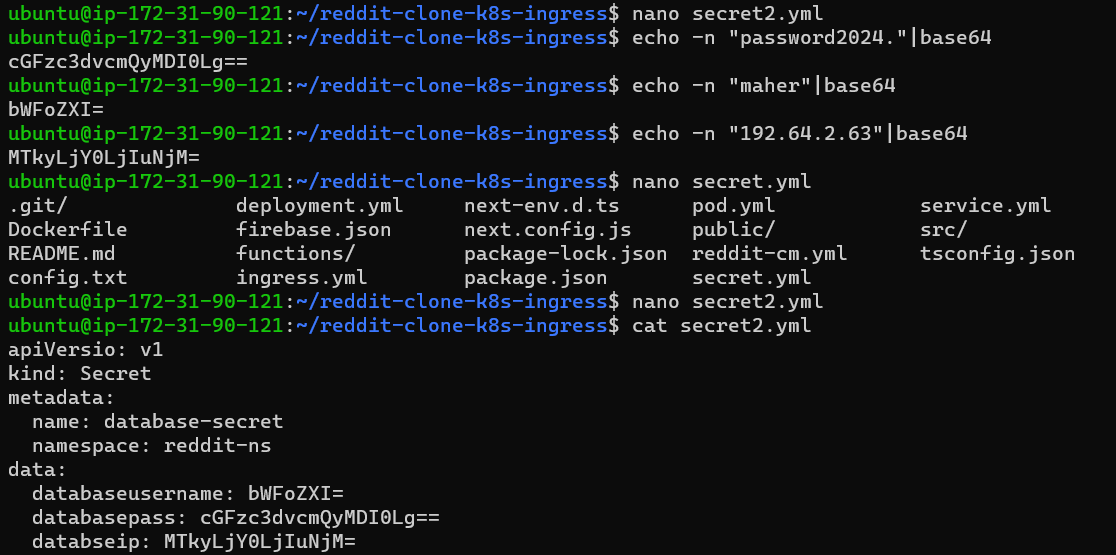
Step 4:
Describe the created secret and look at the output.
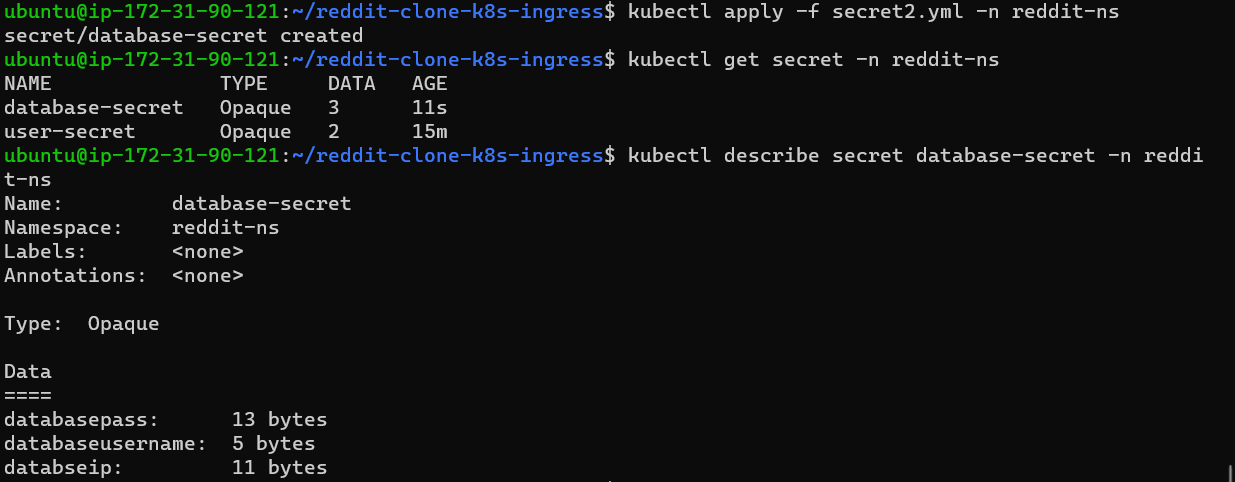
Step 5:
Create the pod and mount the secret file as a volume similar to configmap.
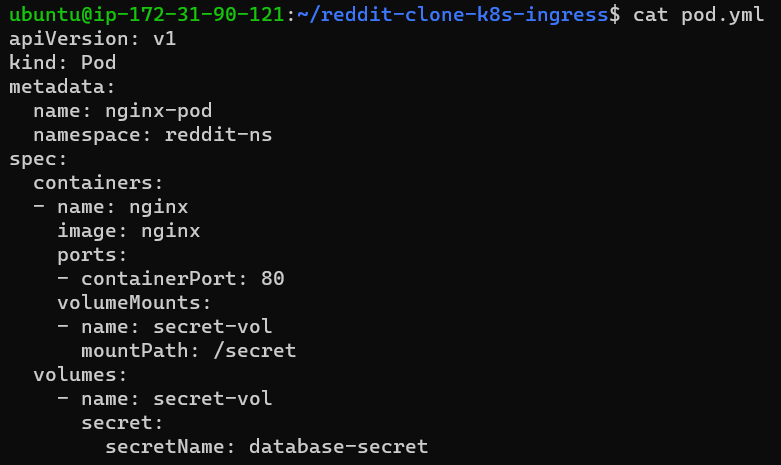
Step 6:
Access the pod to check whether the volume has mounted successfully or not.
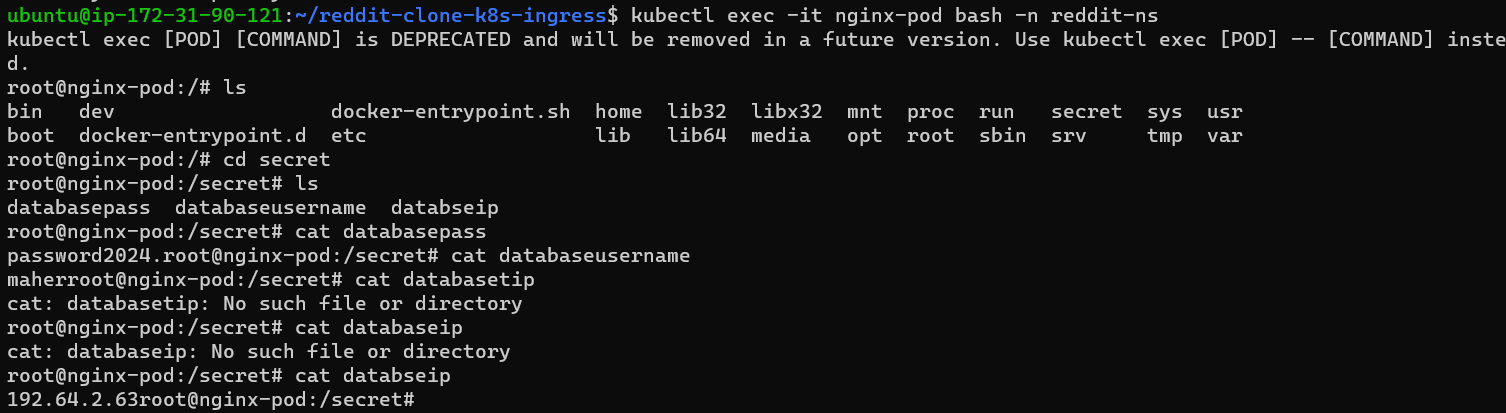
Thank You For Reading...😉
Subscribe to my newsletter
Read articles from Maher Messaoudi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
