Day 39: AWS and IAM Basics ☁
 ANSAR SHAIK
ANSAR SHAIK
Welcome back to the 90DaysOfDevOps challenge! On day 39, we delve into the fundamental aspects of AWS, focusing on Identity and Access Management (IAM). As we progress in our journey, understanding IAM becomes crucial for maintaining a secure and efficient cloud infrastructure.
AWS IAM: Empowering Your Cloud Security
IAM, or Identity and Access Management, is a service provided by AWS that allows you to control access to your AWS resources. It helps you manage users, groups, and roles, defining who can do what in your AWS environment.
User Data in AWS: A Time-Saving Hack
Before we dive into IAM, let's explore a handy feature called User Data. When launching an instance in Amazon EC2, you can pass user data to automate configuration tasks and run scripts post-instance start. This is a game-changer, especially when installing applications like Apache, Docker, or Jenkins.
Task 1: Launching EC2 Instance with Jenkins
Let's demonstrate the power of User Data by launching an EC2 instance with Jenkins pre-installed. Follow these steps:
Launch an EC2 instance.
Provide user data with the script to install Jenkins.
Once the instance is up, access Jenkins using the provided IP address.
Using template:
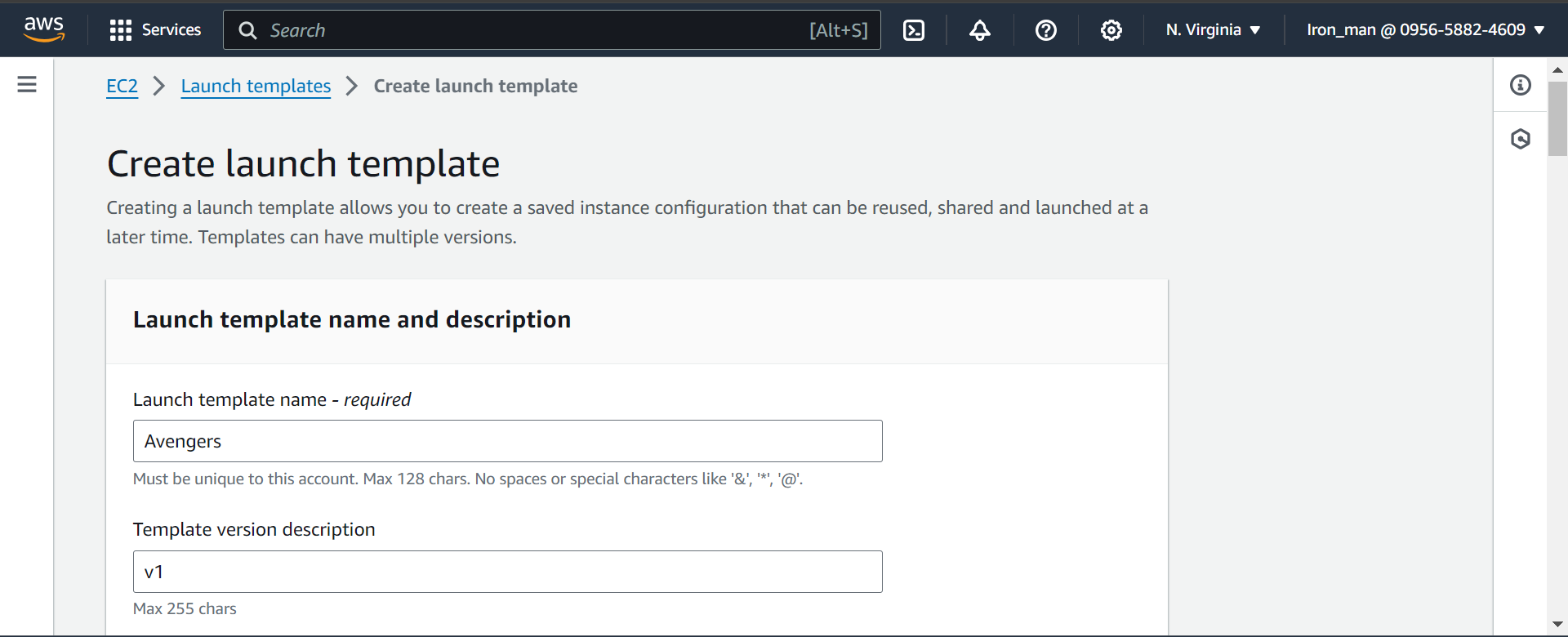
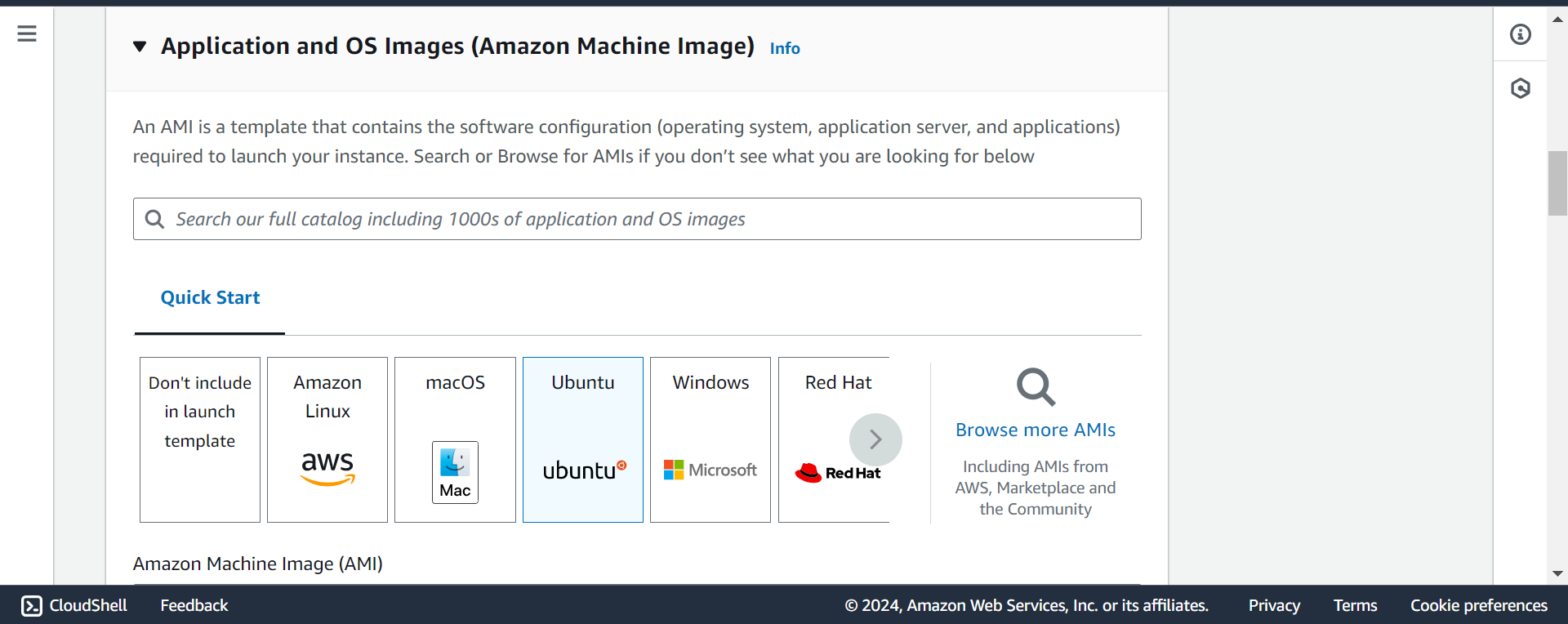
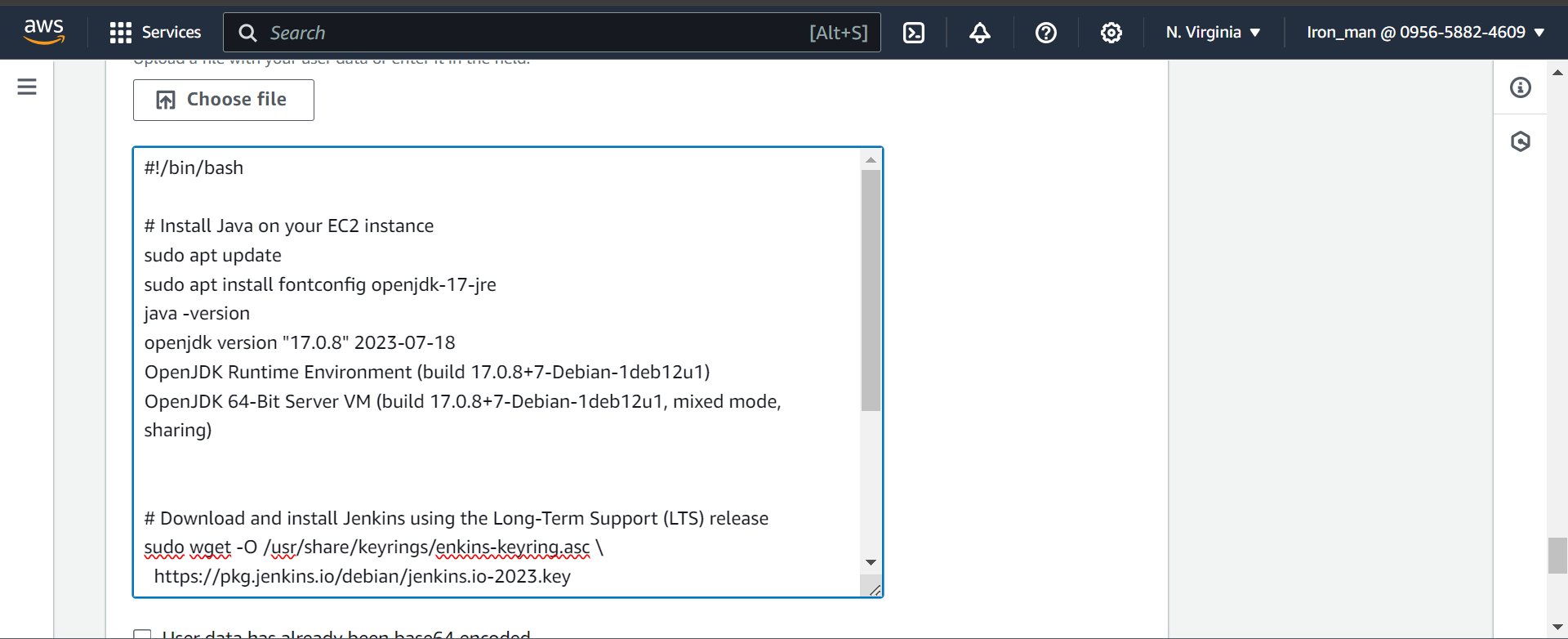
#!/bin/bash
# Install Java on your EC2 instance
sudo apt update
sudo apt install fontconfig openjdk-17-jre
java -version
openjdk version "17.0.8" 2023-07-18
OpenJDK Runtime Environment (build 17.0.8+7-Debian-1deb12u1)
OpenJDK 64-Bit Server VM (build 17.0.8+7-Debian-1deb12u1, mixed mode, sharing)
# Download and install Jenkins using the Long-Term Support (LTS) release
sudo wget -O /usr/share/keyrings/jenkins-keyring.asc \
https://pkg.jenkins.io/debian/jenkins.io-2023.key
echo deb [signed-by=/usr/share/keyrings/jenkins-keyring.asc] \
https://pkg.jenkins.io/debian binary/ | sudo tee \
/etc/apt/sources.list.d/jenkins.list > /dev/null
sudo apt-get update
sudo apt-get install jenkins
# Install Docker
sudo apt install docker.io -y
Launch instance from template:
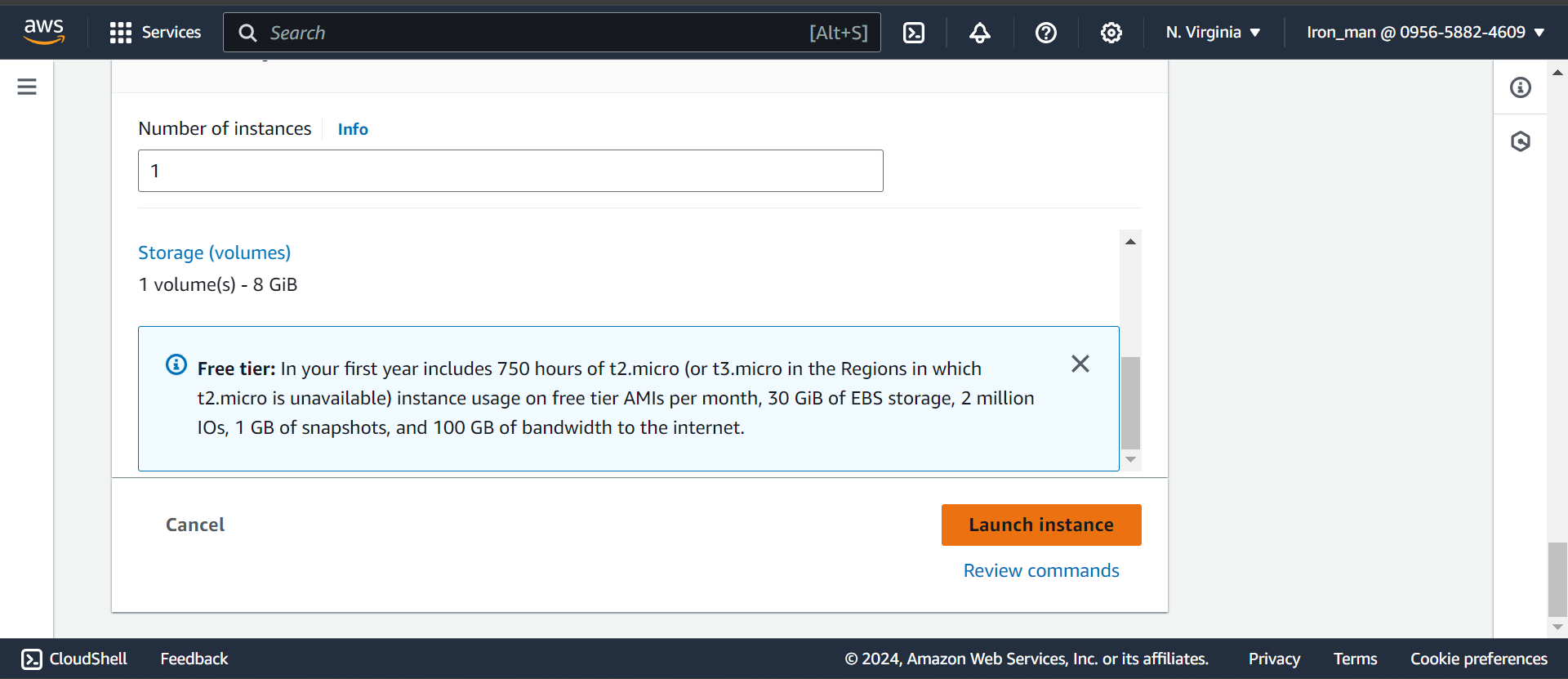
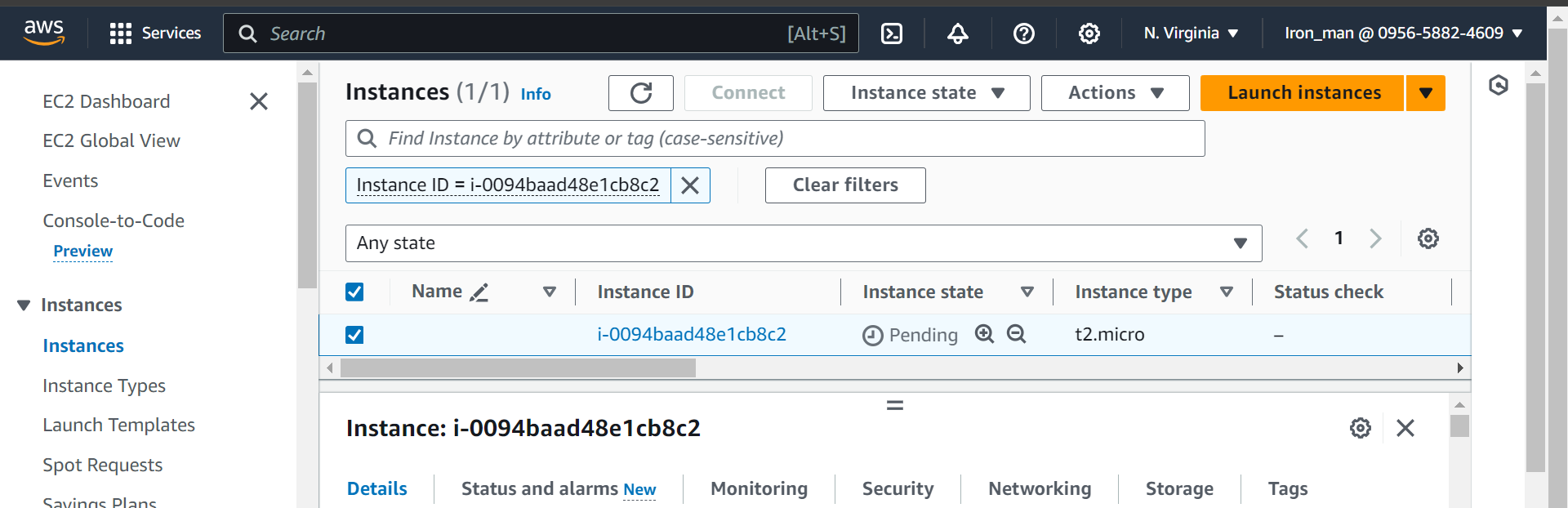
Edit inbound rules:
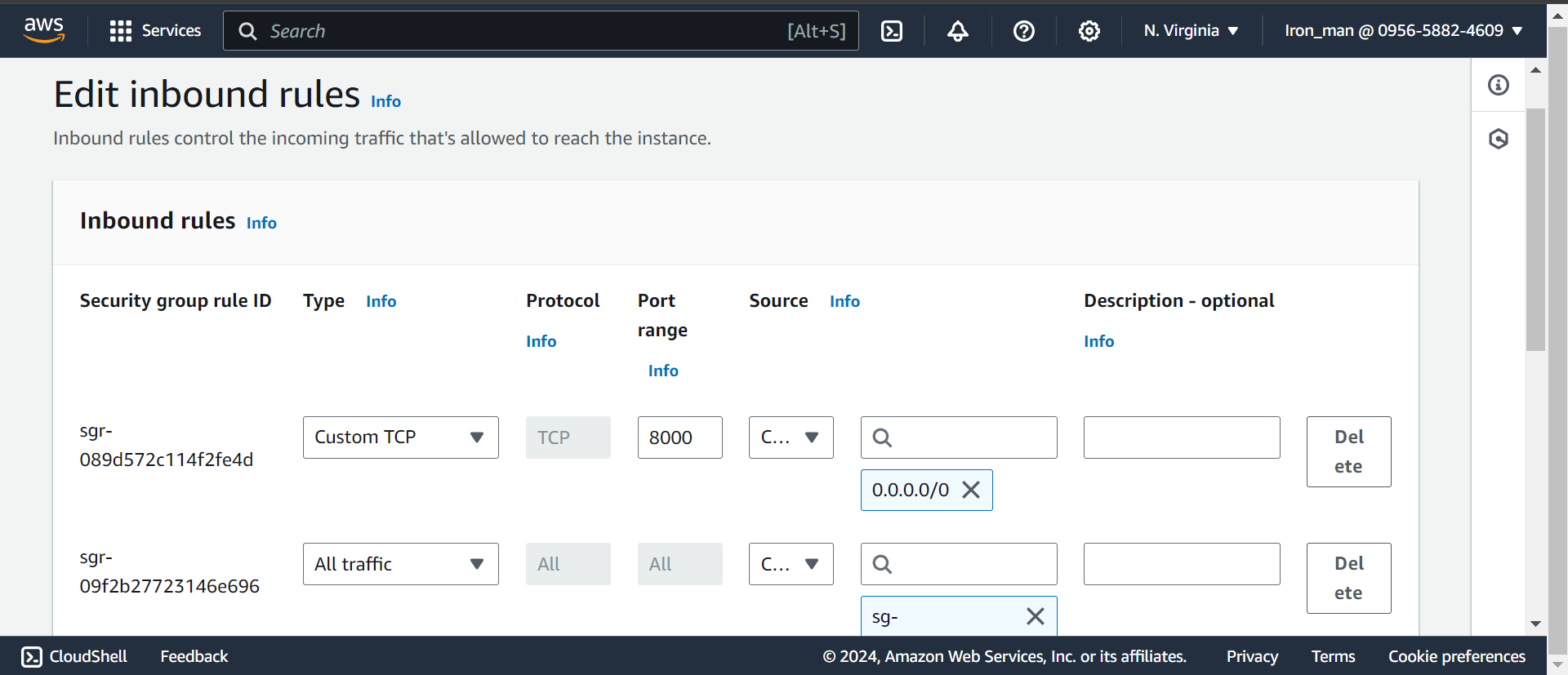
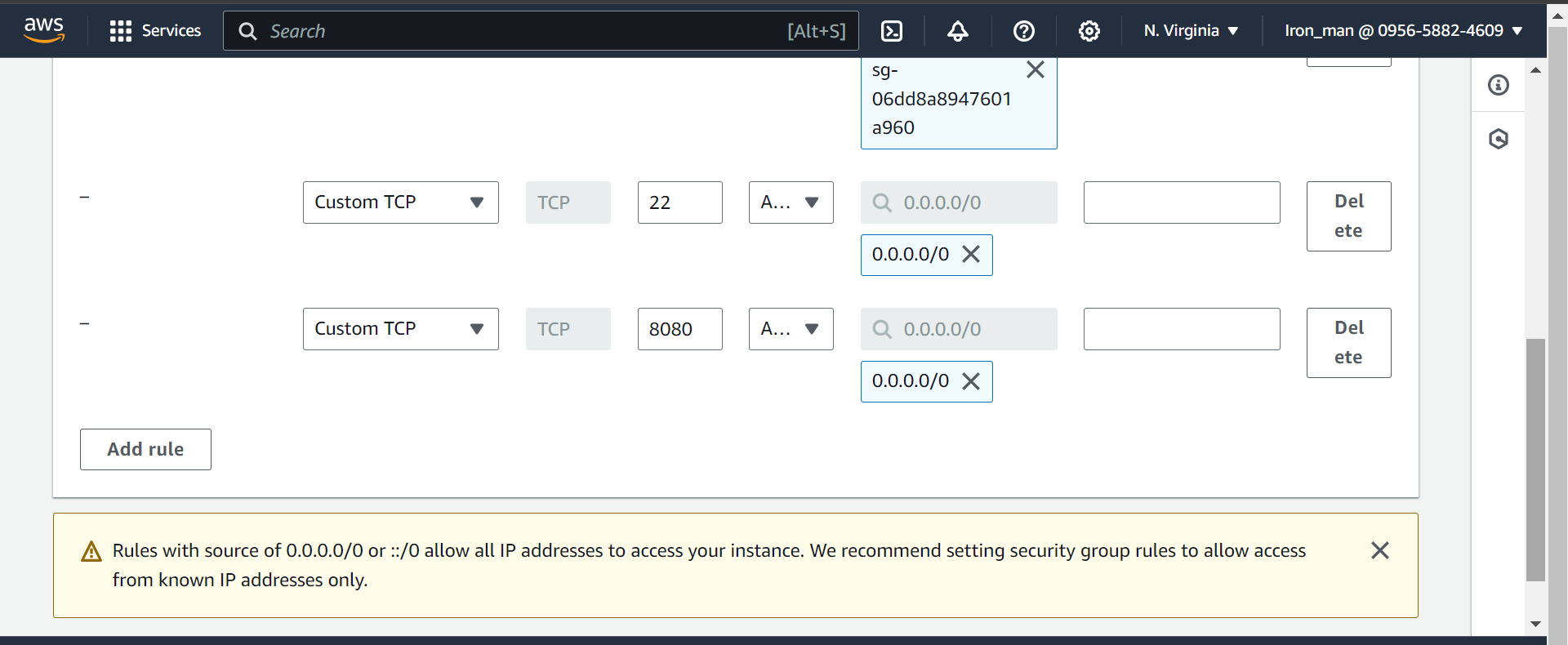
Connect Through SSH:
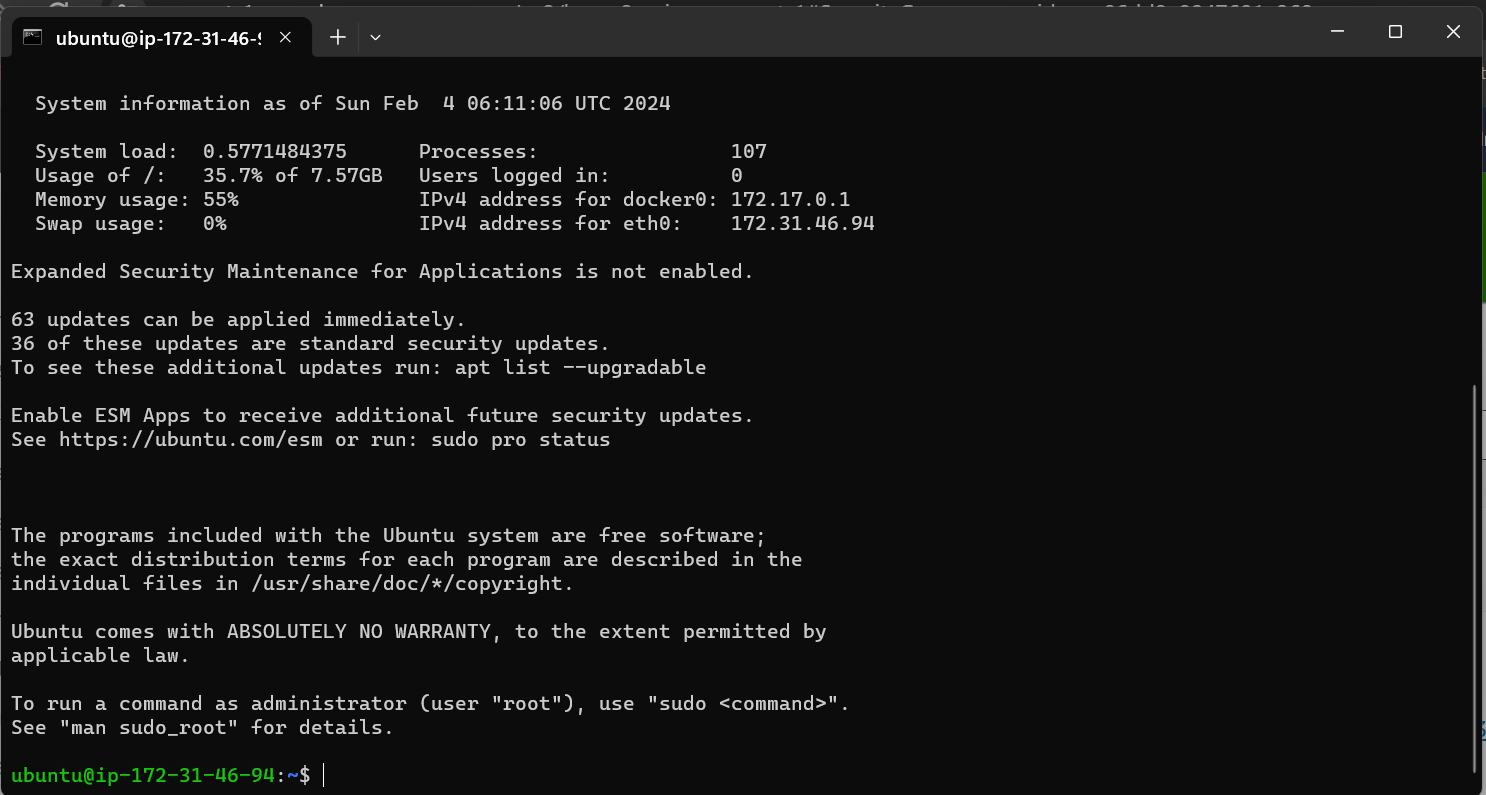
Jenkins is running:
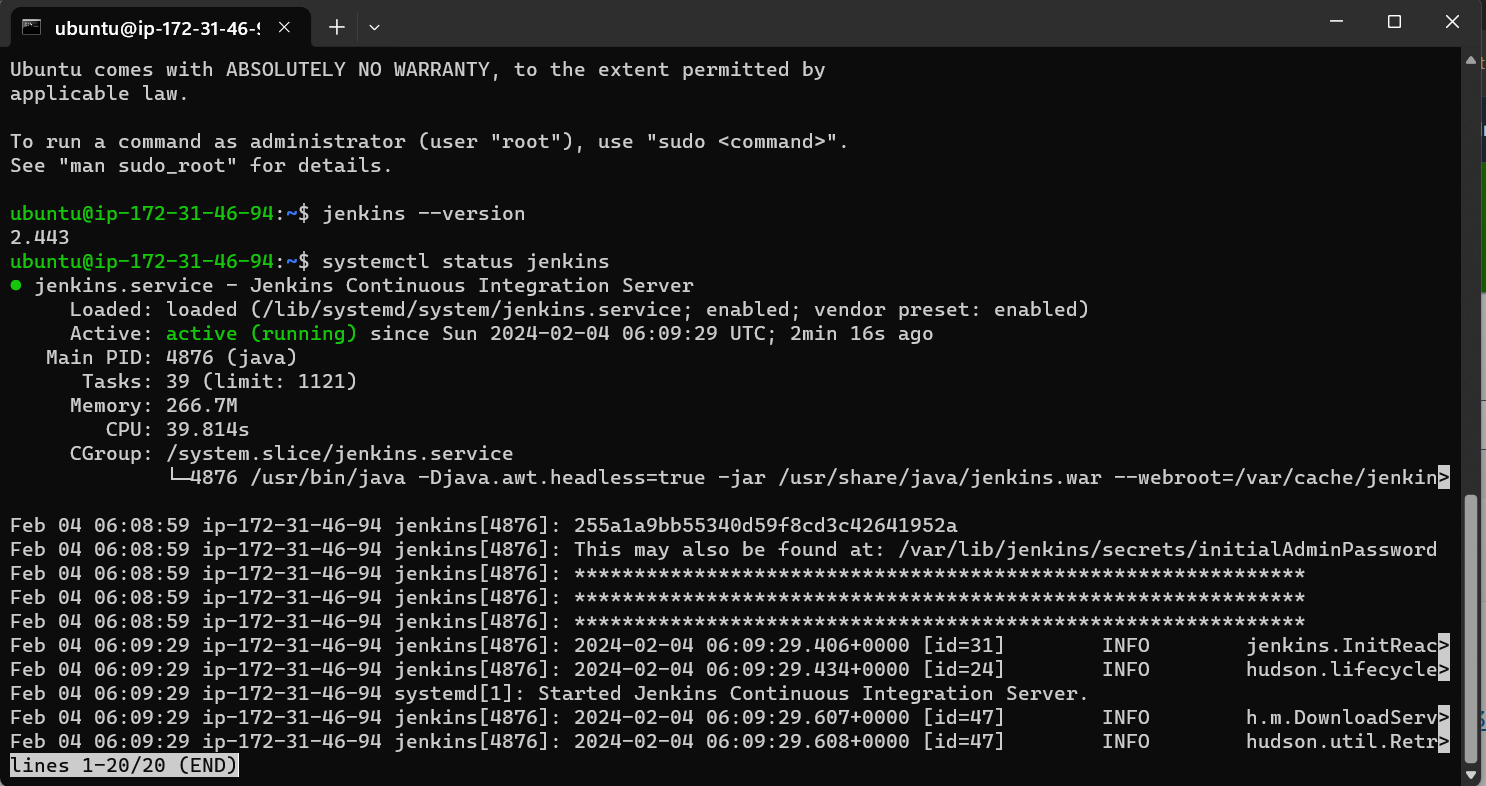
Access using instance IP:
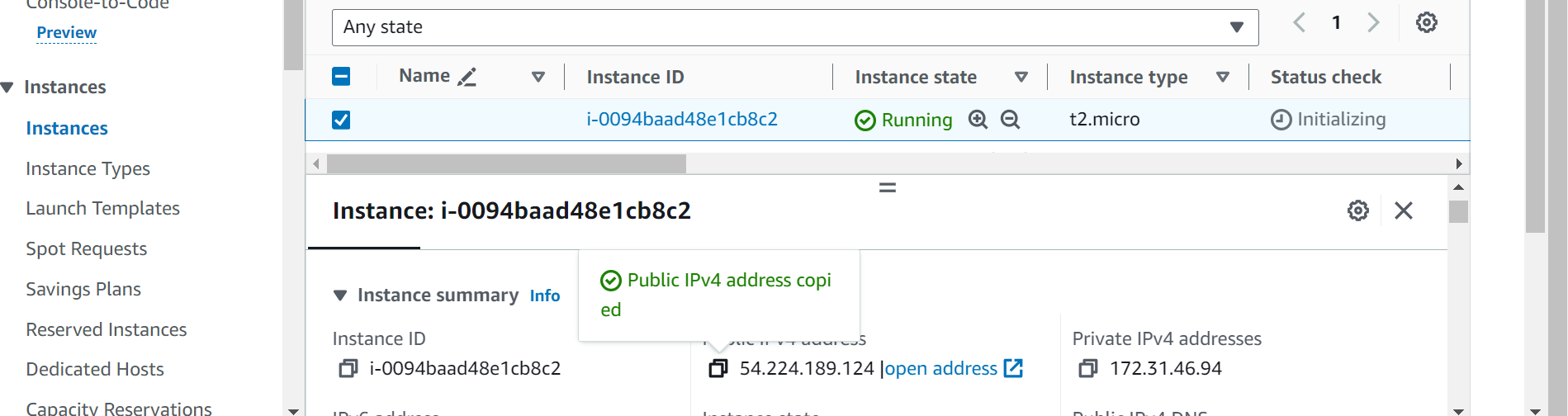
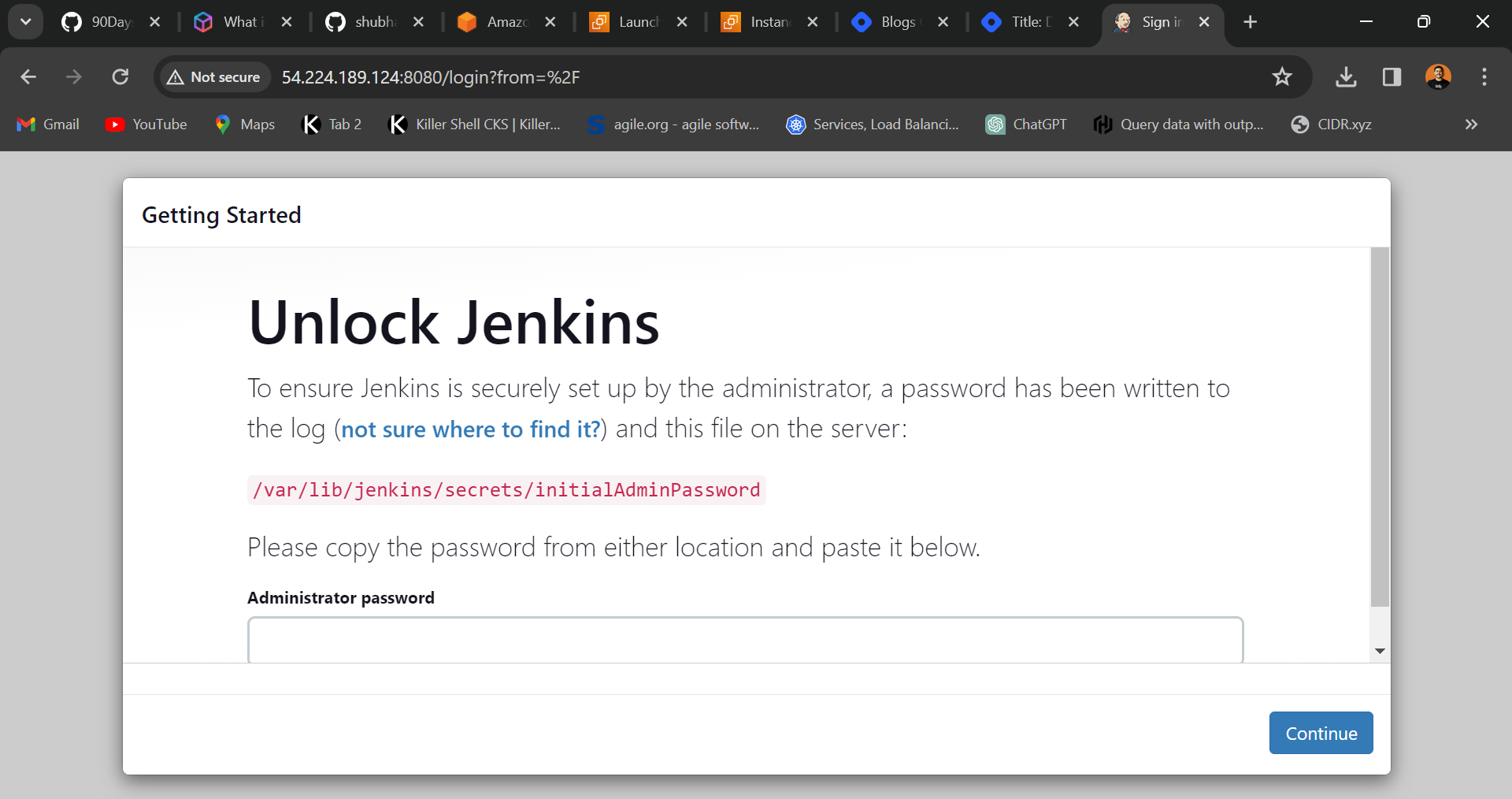
This not only saves time but also ensures consistency in your environment.
Task 2: Unraveling IAM Roles
IAM Roles play a pivotal role in managing access to AWS resources securely. Let's break down the key components:
IAM Users: These are entities with unique security credentials, allowing them to interact with AWS services. Users can have individual permissions tailored to their needs.
IAM Groups: Groups are collections of users. Instead of assigning permissions individually, you assign them to groups, making it easier to manage access for multiple users with similar needs.
IAM Roles: Roles are similar to users but are not associated with a specific person. They are meant to be assumed by anyone who needs them, providing temporary permissions.
Creating Three Roles: DevOps-User, Test-User, Admin
In the AWS Management Console, navigate to IAM and create three roles:
DevOps-User Role: Tailor permissions for DevOps-related tasks.
Test-User Role: Configure permissions suitable for testing activities.
Admin Role: Grant comprehensive permissions for administrative tasks.
IAM Roles enhance security and follow the principle of least privilege, ensuring users and systems have only the permissions they need.
As we progress through the 90DaysOfDevOps challenge, mastering IAM is crucial for building secure and scalable AWS environments. Stay tuned for more insights and hands-on experiences. Happy cloud computing! ☁🚀
Subscribe to my newsletter
Read articles from ANSAR SHAIK directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

ANSAR SHAIK
ANSAR SHAIK
AWS DevOps Engineer