AWS OpenVPN: SSL and hostname configuration
 Rahul wath
Rahul wath
If you have OpenVPN AS running in Production, For now – need to configure SSL to avoid alerts in clients browsers.
Contents
Let’s Encrypt
Install Let’s Encrypt client:
git clone https://github.com/letsencrypt/letsencrypt /opt/letsencrypt
Open port 80 in your AWS Security Group – it’s safe as OpenVPN AS listen on the 443 for clients and 943 for the admin page access.
Obtain a new certificate:
/opt/letsencrypt/letsencrypt-auto certonly -d vpn.example.com
SSL in OpenVPN AS
You can change certificates using Admin UI in the Web Server Configuration, or using CLI.
On the first run OpenVPN AS generates self-signed certificates stored in the /usr/local/openvpn_as/etc/web-ssl/ directory:
ls -l /usr/local/openvpn_as/etc/web-ssl/
They are kind of failover-certificates in case if others will be broken.
To configure SSL we need to have three files, in case of using Let’s Encrypt we will use next files to create them:
*.crt– it’s ourfullchain.pemfile*.key–privkey.pemfile*.bundle– will be created fromfullchain.pemandprivkey.pem
Install private key to OpenVPN server:
/usr/local/openvpn_as/scripts/sacli --key "cs.priv_key" --value_file "privkey.pem" ConfigPut
Install its public cert:
/usr/local/openvpn_as/scripts/sacli --key "cs.cert" --value_file "fullchain.pem" ConfigPut
“Generate” bundle – just by using cat for the fullchain.pem and privkey.pem:
cd /etc/letsencrypt/live/vpn.example.com
cat fullchain.pem privkey.pem > bundle.pem
Add it to the OpenVPN AS:
/usr/local/openvpn_as/scripts/sacli --key "cs.ca_bundle" --value_file "bundle.pem" ConfigPut
Restart service:
/usr/local/openvpn_as/scripts/sacli start
Check UI now:
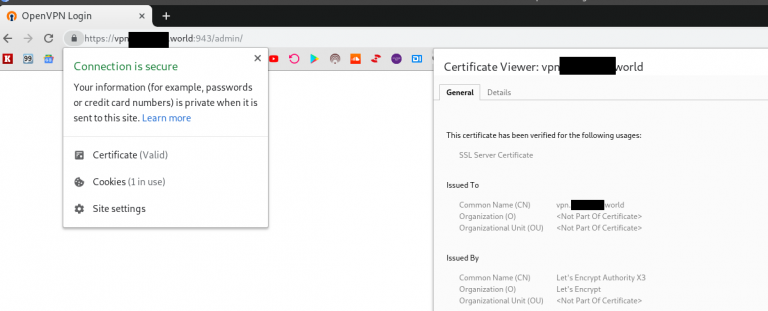
OpenVPN AS hostname
And the last step here will be to configure server’s hostname if this wasn’t made during initial setup.
Go to the Admin UI => Network Settings:

AUTOMATE EVERYTHING!
Lets Encrypt certificates expire every 3 months. To save us from having to renew & reinstall them manual we can create a simple bash script and schedule it using cron which is a time-based job scheduler
1. Copy the code below using a text editor of your choice into /usr/local/sbin/certrenewal.sh:
#!/bin/bash
certbot renew — standalone
sleep 1m
cat /etc/letsencrypt/live/vpn.kreditz.com/fullchain.pem /etc/letsencrypt/live/vpn.example.com/privkey.pem > /etc/letsencrypt/live/vpn.example.com/bundle.pem
/usr/local/openvpn_as/scripts/sacli --key "cs.priv_key" --value_file "/etc/letsencrypt/live/vpn.example.com/privkey.pem" ConfigPut
/usr/local/openvpn_as/scripts/sacli --key "cs.cert" --value_file "/etc/letsencrypt/live/vpn.example.com/fullchain.pem" ConfigPut
/usr/local/openvpn_as/scripts/sacli --key "cs.ca_bundle" --value_file "/etc/letsencrypt/live/vpn.example.com/bundle.pem" ConfigPut
/usr/local/openvpn_as/scripts/sacli start
2. Make the script Executable:
sudo chown +x /usr/local/sbin/certrenewal.sh
3. Enter Cron editor as root:
sudo crontab -e
#Add the following line
0 0 1 */2 * /usr/local/sbin/certrenewal.sh
This will schedule the script to run 'At 00:00 on day-of-month 1 in every 2nd month.
Subscribe to my newsletter
Read articles from Rahul wath directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rahul wath
Rahul wath
An experienced DevOps Engineer understands the integration of operations and development in order to deliver code to customers quickly. Has Cloud and monitoring process experience, as well as DevOps development in Windows, Mac, and Linux systems.