Navigating Cross-Origin Resource Sharing (CORS) Errors: A Comprehensive Guide for Developers
 Nishant Tomer
Nishant Tomer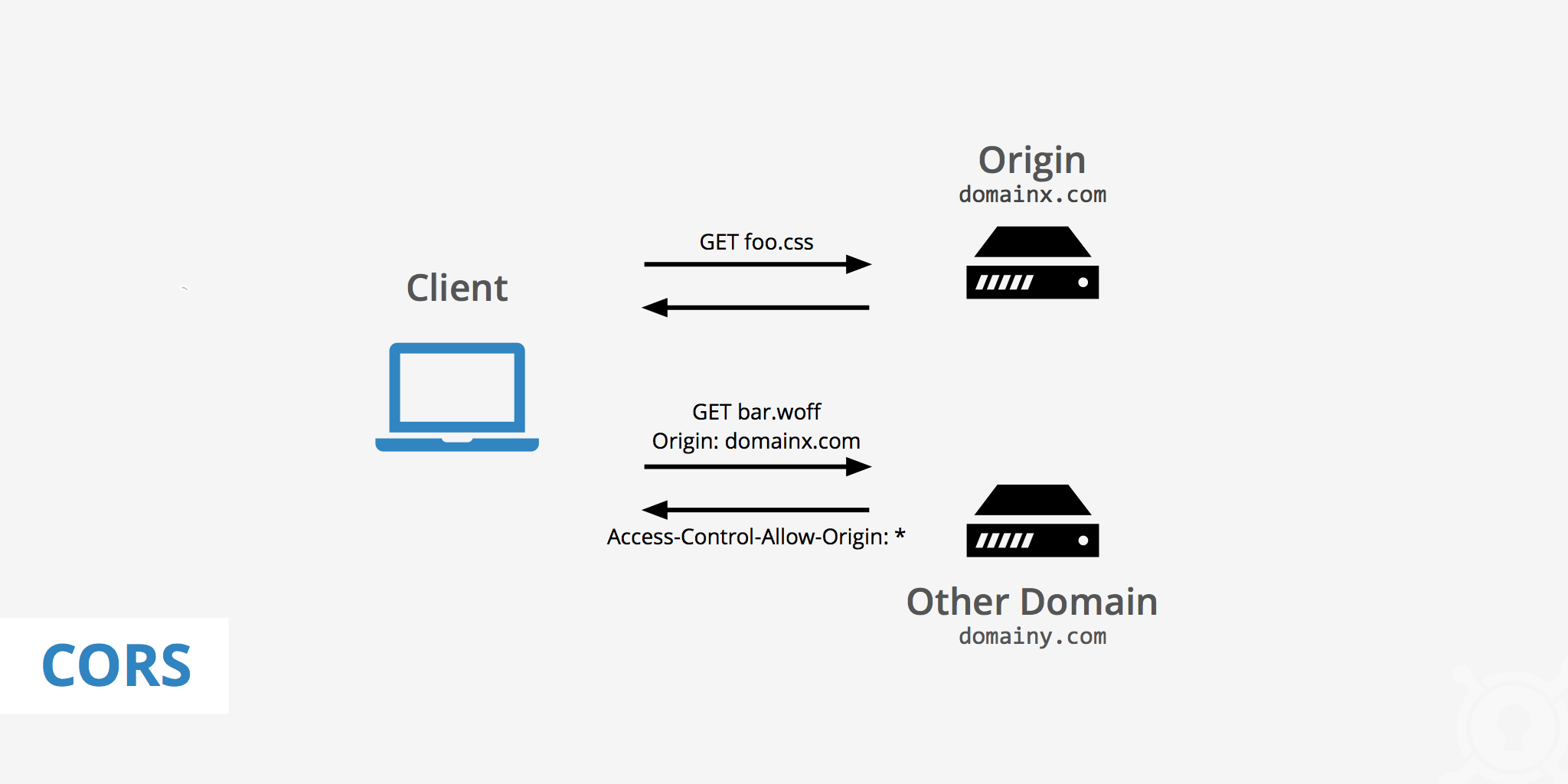
Introduction:
Cross-Origin Resource Sharing (CORS) is a security feature implemented in web browsers to control and restrict resource access across different origins. While essential for web security, CORS errors can be a common stumbling block for developers. This comprehensive guide aims to provide an in-depth understanding of CORS errors, their causes, and effective strategies for resolution.
Understanding CORS:
Definition and Purpose:
- CORS is a security feature implemented by web browsers to prevent unauthorized cross-origin requests. It ensures that a web page or web application can only request resources from the same origin by default.
Same-Origin Policy:
- The Same-Origin Policy is a fundamental security measure where web pages can only make requests to a different domain if both the protocol (HTTP/HTTPS), domain, and port match.
Causes of CORS Errors:
Cross-Origin Requests:
- When a web page hosted on one domain makes a request to a server on a different domain, it triggers a CORS error if the server doesn't explicitly allow such requests.
Unauthorized Headers:
- Including unauthorized headers in a cross-origin request, such as custom headers not whitelisted by the server, can lead to CORS errors.
Cookie and Credentials Issues:
- Requests with credentials (like cookies or HTTP authentication) from a different origin may trigger CORS errors unless the server explicitly allows such requests.

Resolving CORS Errors:
Server-Side Solutions:
- Configure the server to include appropriate CORS headers in responses. This involves setting
Access-Control-Allow-Origin,Access-Control-Allow-Methods,Access-Control-Allow-Headers, and other related headers.
- Configure the server to include appropriate CORS headers in responses. This involves setting
Wildcard Origins and Specific Allowances:
- Servers can be configured to allow requests from specific origins or to use wildcard (
*) to allow any origin. However, wildcard usage has implications for credentials and requires careful consideration.
- Servers can be configured to allow requests from specific origins or to use wildcard (
Preflight Requests:
- For requests with certain characteristics (e.g., using certain methods or custom headers), browsers send a preflight request (OPTIONS) to check if the server permits the actual request. Handling preflight requests correctly is crucial.
Credentials and Cookies:
- If the client sends credentials with a cross-origin request, the server must respond with
Access-Control-Allow-Credentials: trueand specific origin allowances. The client-side must also setwithCredentialstotrue.
- If the client sends credentials with a cross-origin request, the server must respond with
Common Scenarios and Practical Examples:
AJAX Requests:
- Handling CORS errors in AJAX requests, including setting up the appropriate headers and understanding the impact on different HTTP methods.
Font, Image, and Resource Loading:
- CORS implications for loading external resources such as fonts and images and strategies to resolve related issues.
CORS in Different Contexts:
Single Page Applications (SPAs):
- How SPAs interact with APIs and handle CORS, including considerations for routing and client-side navigation.
Serverless Architectures:
- CORS considerations in serverless architectures, where functions are deployed as individual endpoints and may have unique CORS requirements.
Tools and Debugging:
Browser Developer Tools:
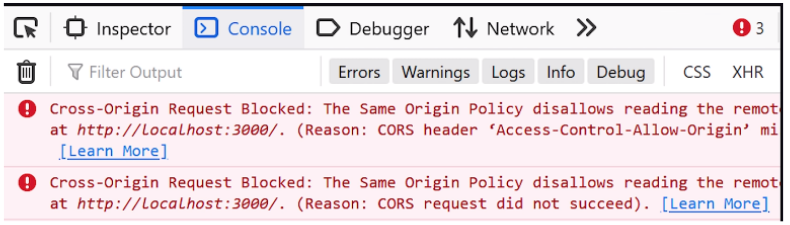
- Leveraging browser developer tools to identify and diagnose CORS issues, inspecting network requests, and analyzing headers.
Proxy Servers:
- Using proxy servers to circumvent CORS restrictions during development or testing phases.
Security Implications and Best Practices:
Security Risks:
- Understanding potential security risks associated with relaxed CORS policies and ensuring configurations are secure against cross-origin attacks.
Granular Permissions:
- Implementing granular permissions for specific origins rather than using wildcard allowances to minimize security risks.
Conclusion:
CORS errors are an integral aspect of web development, requiring a nuanced understanding to build secure and interoperable applications. This comprehensive guide has covered the fundamental concepts, causes, resolution strategies, and practical examples associated with CORS errors. Armed with this knowledge, developers can navigate CORS-related challenges, ensure proper server configurations, and build web applications that seamlessly interact across different origins while maintaining robust security practices.
Thank you for your time. See you in the next article.
Subscribe to my newsletter
Read articles from Nishant Tomer directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nishant Tomer
Nishant Tomer
I'm a seasoned backend web developer with a passion for crafting robust and scalable solutions. With expertise in languages such as C/C++, JavaScript, and Node.js and a keen eye for optimizing database performance, I specialize in building the backbone of web applications. I've successfully implemented and maintained various backend systems, ensuring seamless functionality and a positive user experience. I'm excited about the prospect of collaborating on impactful projects and contributing my skills to innovative solutions.