Analysing the Gootloader infection Palo-Alto threat intelligence using wireshark and performing dynamic analysis
 Mohamed Kourouma
Mohamed Kouroumasource: https://www.malware-traffic-analysis.net/2024/01/08/index.html
In this analysis I will start with investigating the packet with wireshark and perform code analysis.
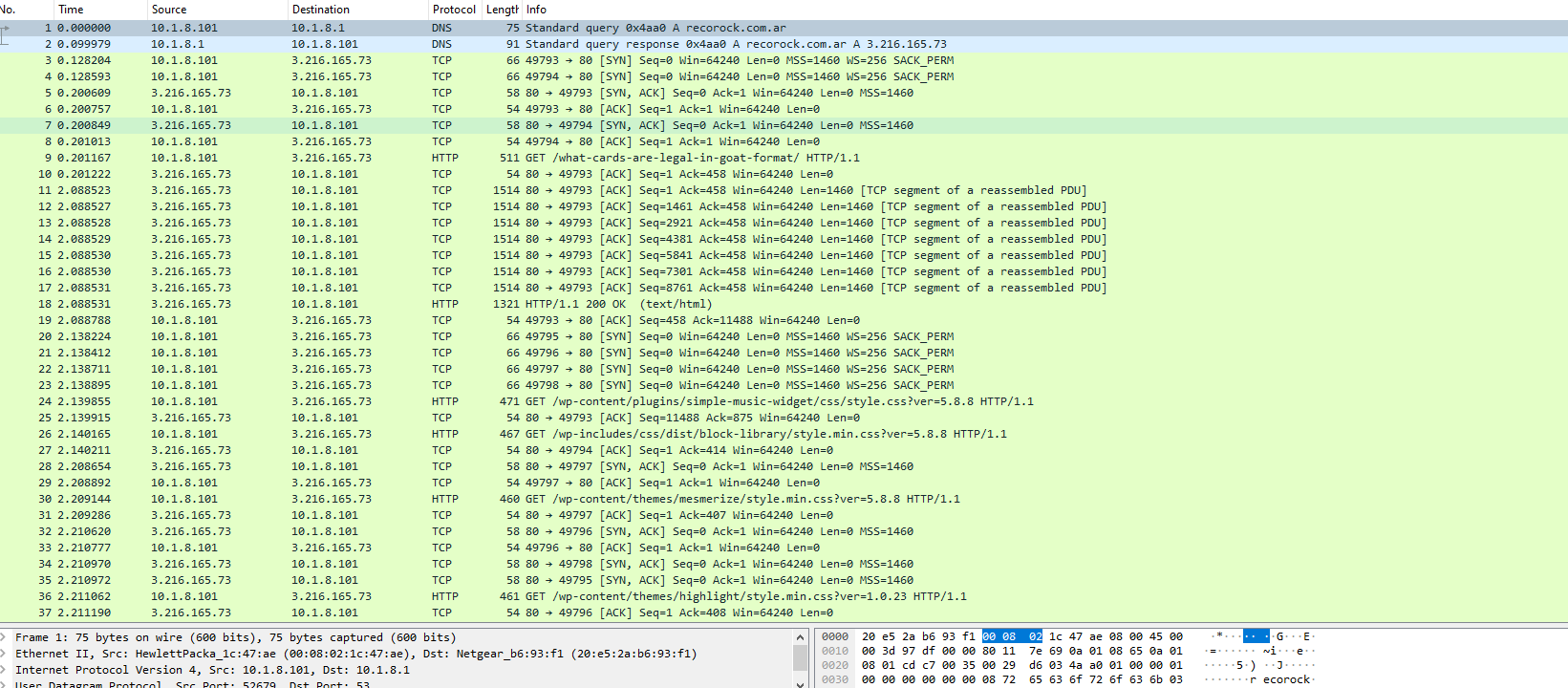
Using some filters to make analysis much easier and efficient, individual packet analysis is time consuming and not all traffic are related to malicious activities some traffic are normal network traffics. To narrow down the packets we shall focus on protocols related to malicious activities such as DNS HTTP,HTTPs and SMB these protocols are not the only related to malicious activities but the concern of this specific anlaysis shall be limited to protocols mentioned above.
The first protocol of focus is the DNS protocol, we shall verify all the addresses making DNS queries and verify the domain they connect to .
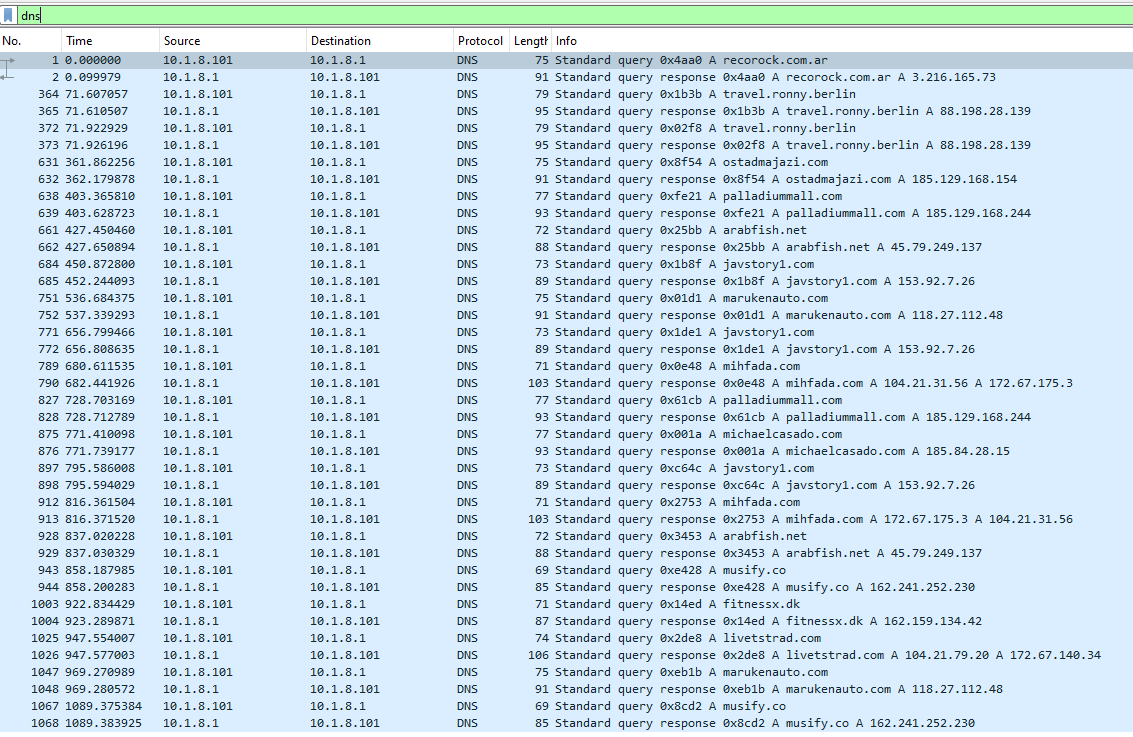
The above screenshot shows all the addresses that are performing DNS queries, as can be observe only two ip addresses are involve, it becomes obvious that the client making the queries is at 10.1.8.101 and the DNS server that performs the resolution is at 10.1.8.1.
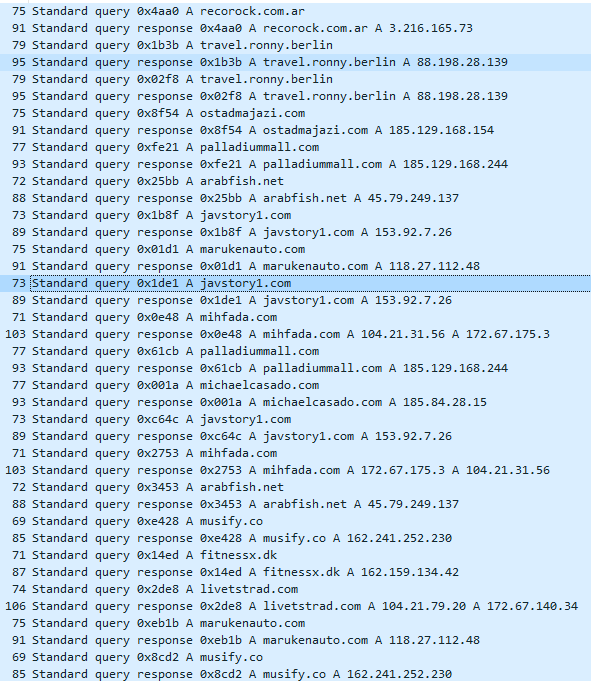
The above DNS queries and responses show all the related domain names and IP addresses , we can go deeper to verify the ASN , countries, and reputation of these domains/IP.
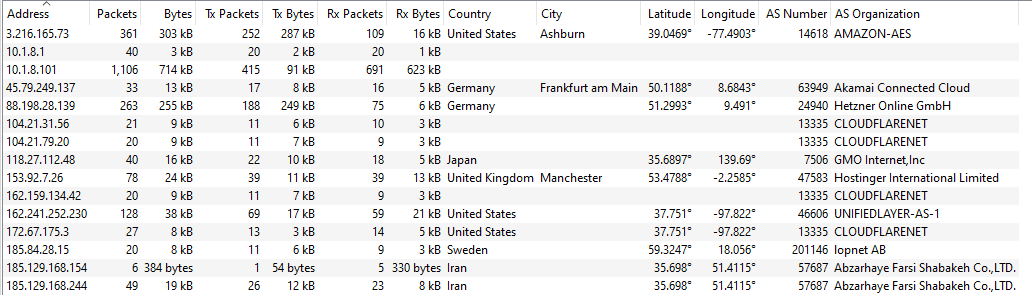
Two domain names shall be verify against virustotal.
1- recorock.com.ar --> 3.216.165.73 2
2- travel.ronny.berlin --> 88.198.28.139
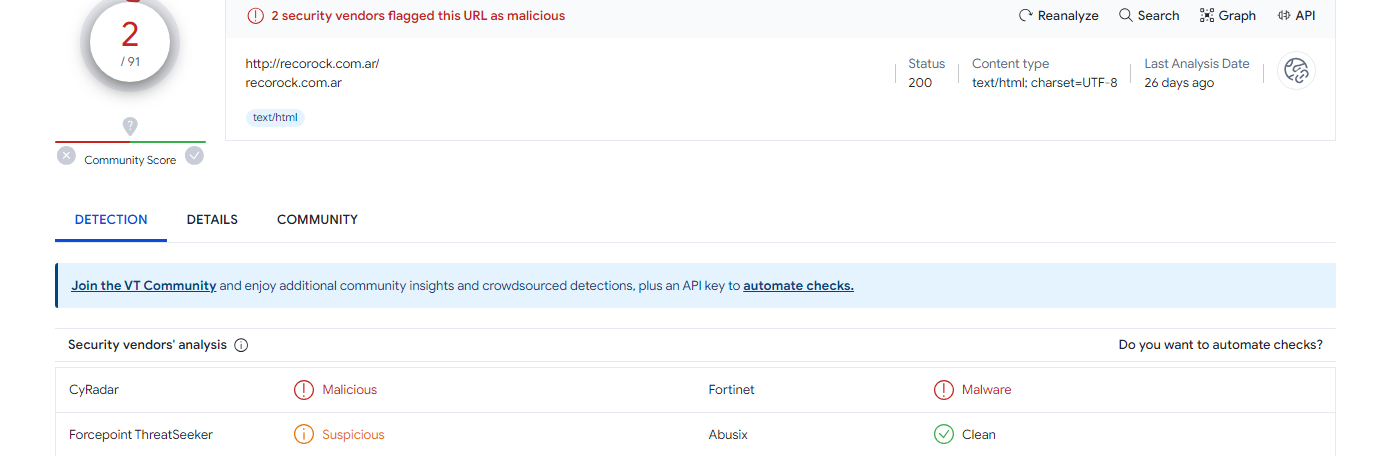
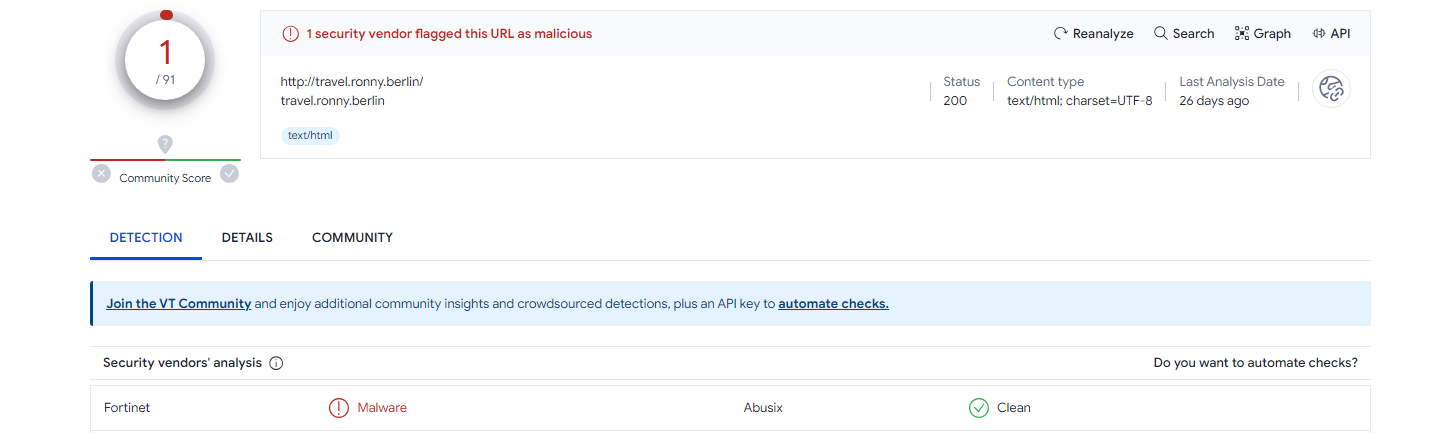
We can repeat the same procedure for all the other domains, but to make it short these two domains are used as sample. The next prorocol to be analyse is the HTTP requests , HTTPS packets will not be analyse because we cannot decrypt it to see the content, it is being analyse as a middle man. Sometimes it's important to verify the version of the TLS protocol in use some malware actors forces a server to use a less secure version of TLS to perform TLS downgrade attacks.
The HTTP requests
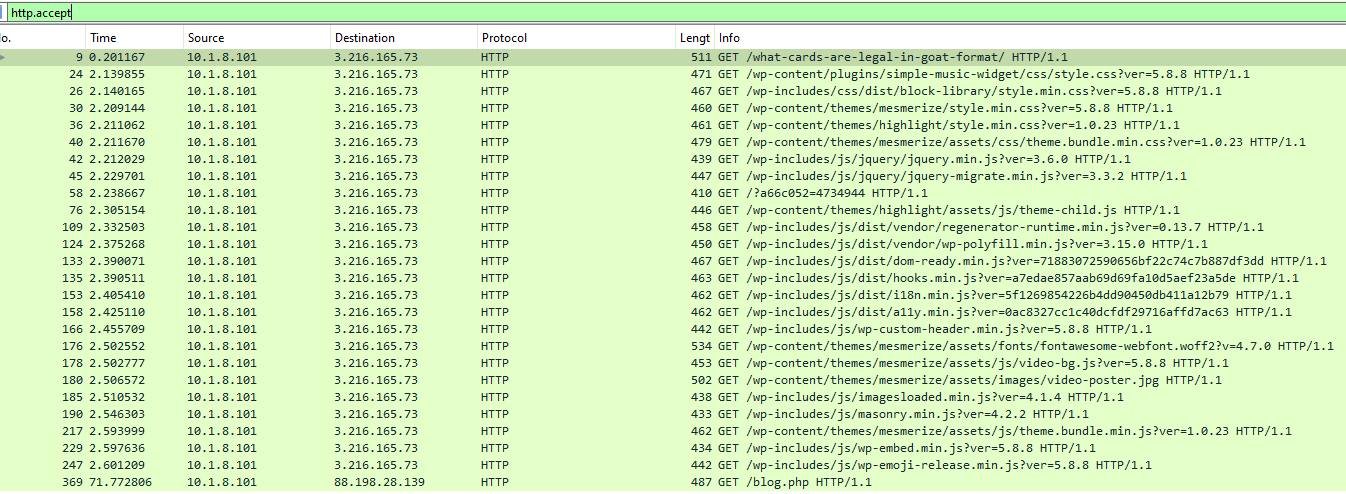
We can see that the host at 10.1.8.101 is getting alot of javascript,php,perl and css contents , all those contents will be downloaded and perform code analysis. some file won't be analyse because they are compiled CSS files,only files with interest shall be further analyze. To perform code analysis we shall make use of Vscode , and vscodeextensions to enable easy code reading.
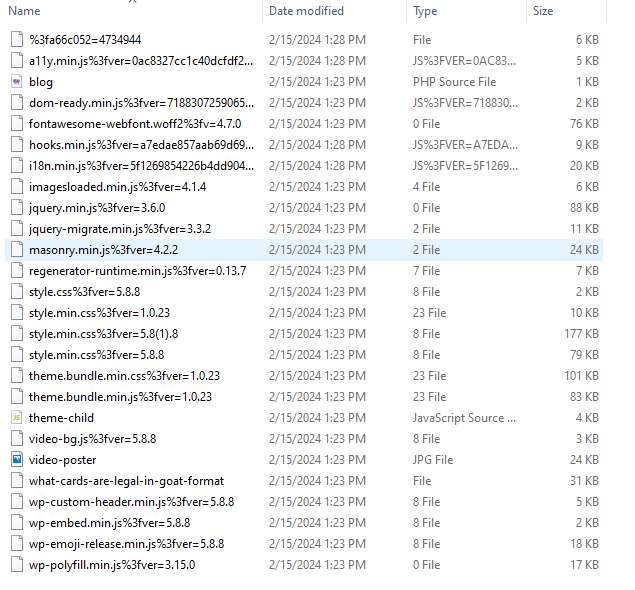
These are the files associated to this packet, two files are of interest the blog.php and what-cards-are-legal-in-goat-format. The content of these two files will be analyse.
blog.php
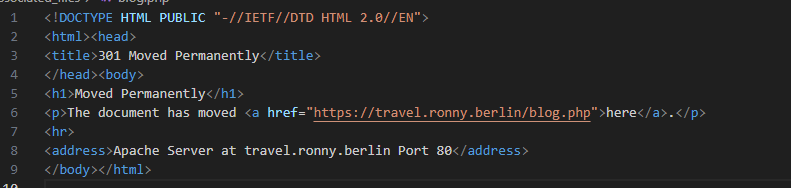
What-cards.....
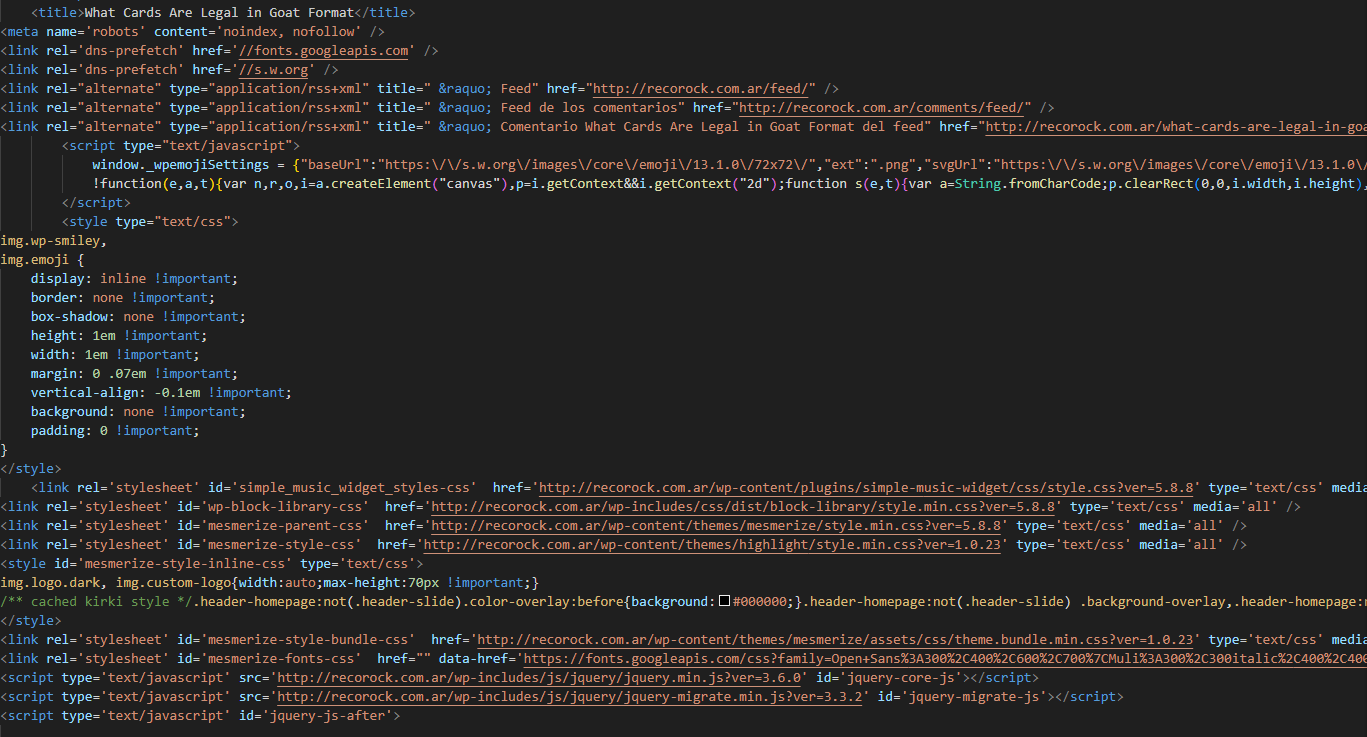
Not all the code will be displayed only sections of the code that are suspicious, from the above code all the resources related to this particular webpage is fetched from the malicious domain name we analysed with virustotal. But something needs to be noted this particular file doesnot contain all the IOCs. From the source of this packet mentioned above, it contains a zip file called gootloader-malware-and-artifacts, files in that zipped file are different from what I obtained, from my personal assumption either we missed out some parts of the traffic or some code modification happened. The files I obtained and the files provided with the traffic are compared.

Meld is use to compare the two javascript codes. There is a big difference between the two codes, just a snippet of the code.
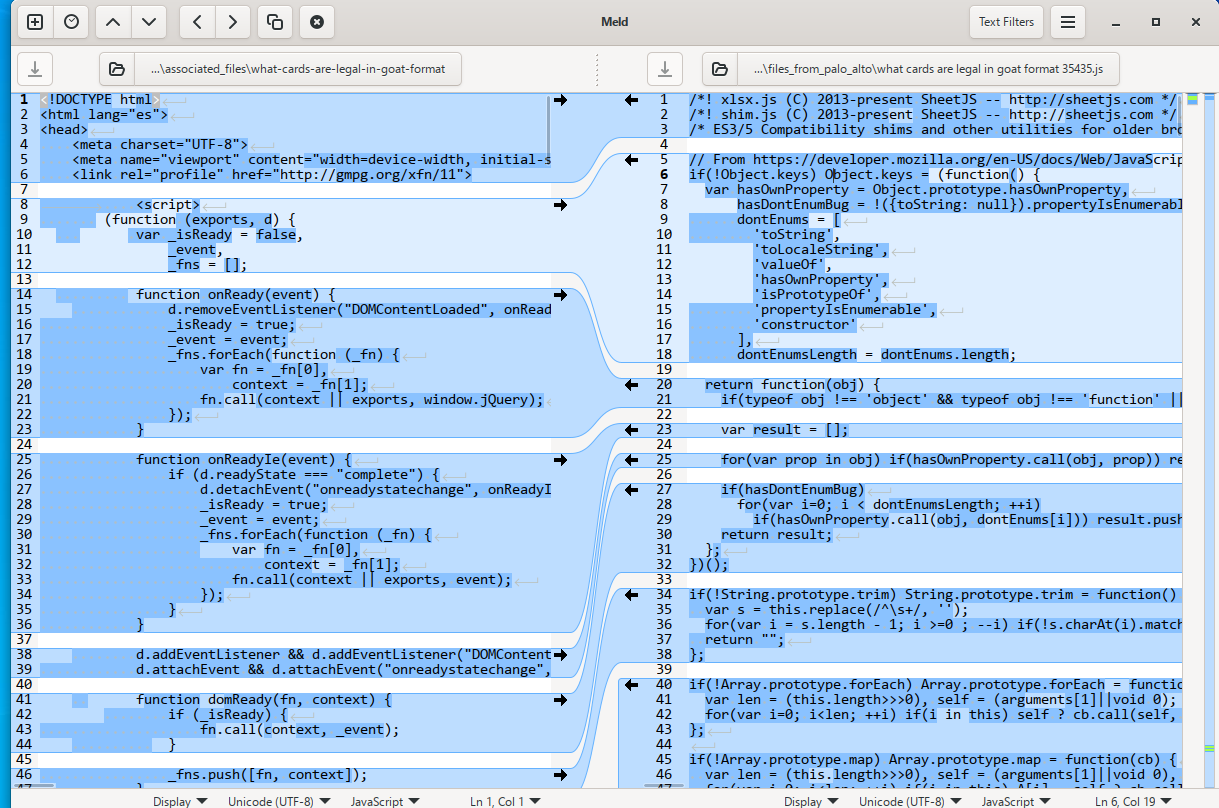
These are some of contents of the two codes only parts of interest will be screenshot , it is a very long code line by line code analysis will be time consuming.
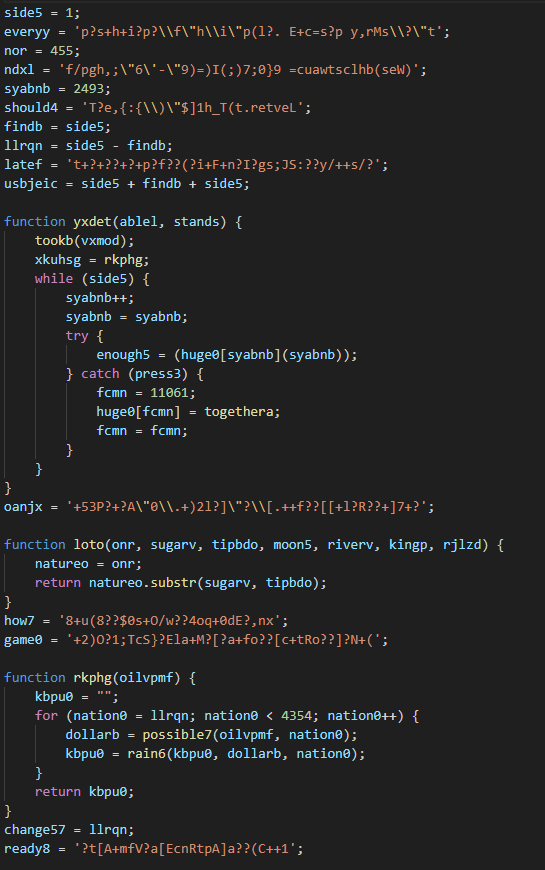
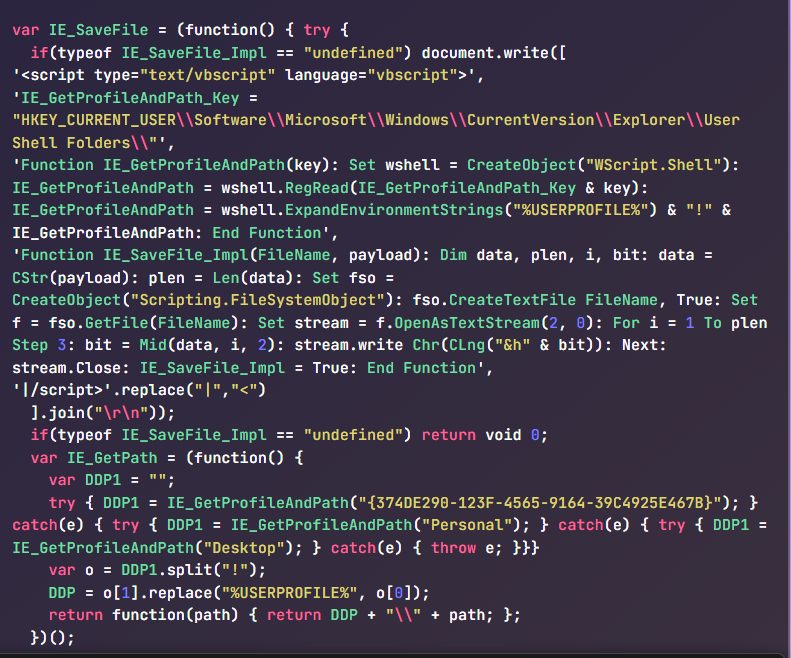
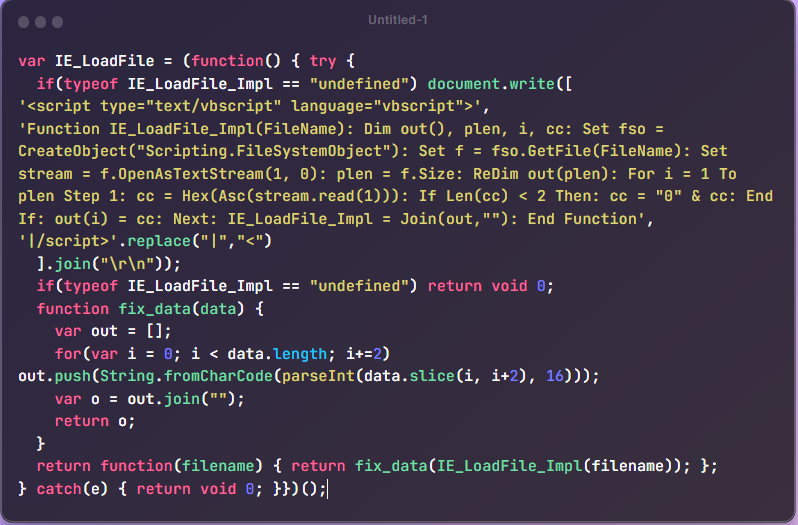
We can come to a conclusion that these two javascript code are malicious, we can see strange variable names and values , vbscript which is a high identification of a malicious activity that manipulates the registry. It is a very long code deeper code investigation can be done by testing every function of the code to identify the specific task it performs. This is just a brief view we can go deeper by verifying the partern each domain the host connected to and how it got infected. It also becomes evident that these code perform some form of data exfiltration.
Subscribe to my newsletter
Read articles from Mohamed Kourouma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
