RBAC in Kubernetes
 Abinash Mishra
Abinash Mishra1 min read
RBAC stands for Role Based Access Control
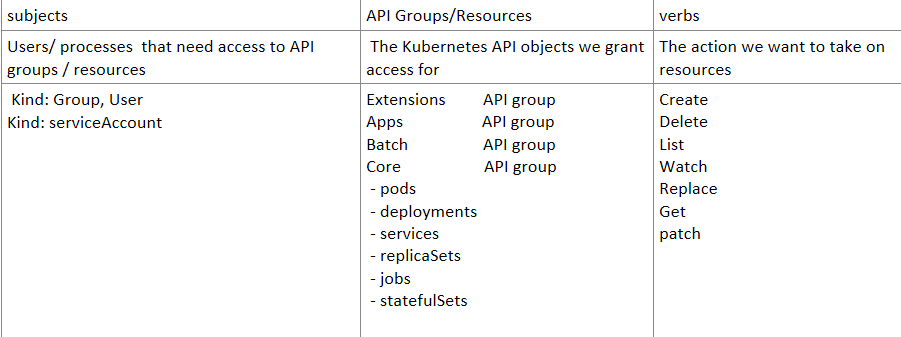
Under core api groups we have all objects: pods, deployments, Services, ReplicaSets, Statefulsets, jobs
Role: A role can be used to grant access to resources in a namespace.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: developer
namespace: dev
rules:
- apiGroups: ["","Extensions", "apps"] # "" indicates the core API group
resources: ["*"]
verbs: ["get", "list", "create", "delete", "watch"]
- apiGroups: ["batch"]
resources:
- job
- cronjobs
verbs: ["*"]
RoleBinding: A RoleBinding binds subjects[users, groups] with the roles.
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metedata:
name: dev-user-rolebinding
namespace: dev
subjects:
kind: user
name: dev
apiGroup: rbac.authorization.k8s.io/v1
roleRef:
kind: role
name: developer
apiGroup: rbac.authorization.k8s.io/v1
imperative command to create Roles and RoleBindings
kubectl create role developer --namespace=default --verb=list,create,delete --resource=pods
kubectl create rolebinding dev-user-rolebinding --namespace=default --role=developer --user=dev-user
kubectl auth can-i list nodes --as dev # to check access
clusterrole & clusterrolebinding :
# create cluster role
kubectl create clusterrole abi-clustaer-role \
--namespace=dev --verb=list --resource=persistentvolumes
# create cluster rolebinding with a user
kubectl create rolebinding abi-cluster-rolebinding \
--namespace= dev --clusterrole=abi-cluster-role --user=dev-user
# create cluster rolebinding with a service account
kubectl create rolebinding abi-cluster-rolebinding \
--namespace= dev --clusterrole=abi-cluster-role --serviceaccount-abi-serv-acnt
0
Subscribe to my newsletter
Read articles from Abinash Mishra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
