1.6 Deep Dive into Ethernet and MAC Addresses
 Vijay Kumar Singh
Vijay Kumar Singh
Introduction
Understanding the fundamentals of computer networking can often seem like deciphering a foreign language. However, at the heart of these complex systems lie a few critical components that enable seamless communication between millions of devices. Among these are Ethernet and MAC addresses. This article will offer a comprehensive exploration of these two crucial aspects of networking and their roles in ensuring smooth data transmission.
Ethernet: The Foundation of Data Communication
Ethernet is the protocol that underpins the vast majority of local area network (LAN) architectures. It's akin to a common language that all devices on a network understand and use for sending and receiving data across network links.
Ethernet operates at the data link layer of the OSI (Open Systems Interconnection) model, a conceptual framework that describes how information from a software application in one computer moves through a network medium to a software application in another computer. The data link layer, Layer 2 in the OSI model, handles the physical and logical connections to the packet's destination.
In essence, Ethernet abstracts the complexities of the physical layer, translating raw bits of data into a form that higher-level software can understand. This abstraction allows software to send and receive data without worrying about the specifics of the physical transmission medium, be it copper wire, fiber optic cable, or wireless radio wave.
MAC Addresses: The Unique Identifier in a Network
Every device that connects to an Ethernet network, such as computers, servers, or printers, has a unique identifier called a Media Access Control (MAC) address. This identifier is hardwired into the network interface card (NIC) and is used to identify the device on the network reliably.
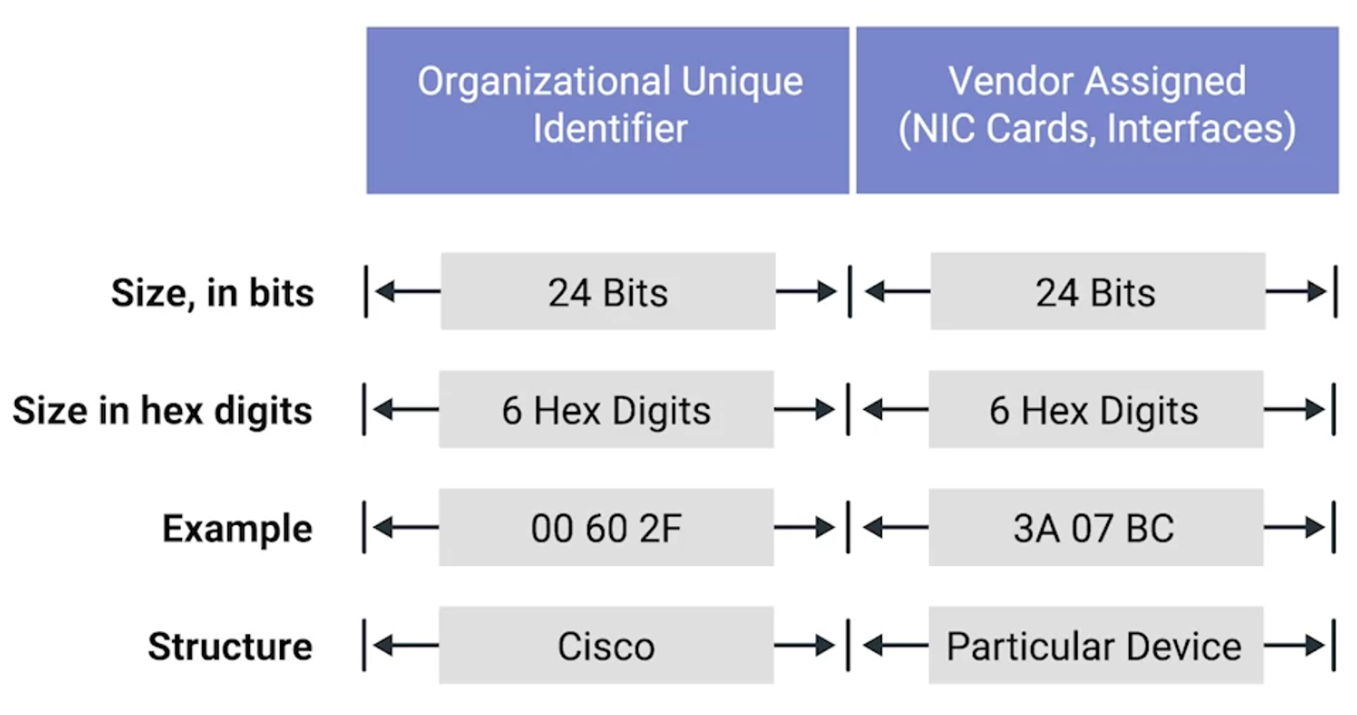
A MAC address is 48 bits long and is usually represented as six groups of two hexadecimal numbers. The first half, or three octets of the MAC address, known as the Organizationally Unique Identifier (OUI), identifies the manufacturer of the NIC. The second half is serialized and assigned by the manufacturer, ensuring a globally unique identifier for every device.
MAC addresses are integral to the operation of Ethernet. When data is to be sent from one device to another over an Ethernet network, it is packaged into an Ethernet frame. This frame includes the MAC address of the source and the destination, ensuring that the data reaches the correct device.
CSMA CD: An Effective Collision Prevention Mechanism
Carrier Sense Multiple Access with Collision Detection (CSMA CD) is a network protocol used in Ethernet to ensure that no two devices try to transmit data at the exact same time, which could lead to a collision.
In essence, CSMA CD allows each device on an Ethernet network to sense whether the transmission medium is currently being used. If the medium is free, the device begins transmitting data. If a collision is detected - that is, if another device transmits data at the same time - all devices stop transmitting and wait for a random period before attempting to transmit again. This randomization helps to minimize the chance of repeated collisions.
Wrapping Up
Ethernet, MAC addresses, and CSMA CD are fundamental to the operation of computer networks. They form the backbone of how data is transmitted and received across networks, ensuring that our digital communications run smoothly. As we continue to expand our reliance on digital technologies, understanding these foundational networking concepts becomes increasingly vital.
Whether you are a network professional troubleshooting complex network issues or an enthusiast seeking to understand how our interconnected world works, a solid grasp of Ethernet and MAC addresses is invaluable. So the next time you're browsing the web, streaming a video, or sending an email, spare a thought for the sophisticated systems working behind the scenes to make it all possible.
Subscribe to my newsletter
Read articles from Vijay Kumar Singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vijay Kumar Singh
Vijay Kumar Singh
I'm Vijay Kumar Singh, a Linux, DevOps, Cloud enthusiast learner and contributor in shell scripting, Python, networking, Kubernetes, Terraform, Ansible, Jenkins, and cloud (Azure, GCP, AWS) and basics of IT world. 💻✨ Constantly exploring innovative IT technologies, sharing insights, and learning from the incredible Hashnode community. 🌟 On a mission to build robust solutions and make a positive impact in the tech world. 🚀 Let's connect and grow together! #PowerToCloud