Cloning a Repository via SSH Authentication: Unveiling the Secure Gateway
 Temitayo Daisi-Oso
Temitayo Daisi-Oso
Introduction
In the realm of secure code management, the process of cloning a repository stands as a pivotal step. GitHub offers two primary avenues for cloning: via HTTPS and via SSH. In this guide, we'll delve into the latter, exploring the intricacies of SSH authentication and understanding why it's the go-to choice for secure connections.
Understanding SSH - The Secure Shell
SSH, or Secure Shell, stands as a cryptographic network protocol, providing a secure conduit for managing network devices and servers across unsecured networks. It ensures data confidentiality and integrity during transmission, offering a fortified alternative to less secure remote access methods.
Demystifying SSH Jargon
Let's demystify the tech lingo. A cryptographic network may sound complex, but in simple terms, it's your devices—laptops, phones, servers—talking to each other securely over a network using "secret codes" known as encryption keys.
Confidentiality and Integrity - The SSH Seal:
SSH connections play guardian to your data, ensuring both its confidentiality and integrity. Picture this: it's like sealing a letter in an envelope. Only the intended recipient (the "server") can open it. The encryption acts as the seal, verifying data integrity like ensuring the contents of a sealed envelope remain unchanged during transmission.
Now, in the world of SSH, you wear two hats: the sender of data, a.k.a. the "client," and the recipient of data, the "server." It's standardized lingo. Even your PC can play the role of a server when receiving data. Flexibility at its finest!
SSH: Fortifying Remote Access:
SSH isn't just a protocol; it's a powerhouse addressing security concerns in remote access and data transmission. This robust and versatile solution brings encryption, authentication, and more to the table, ensuring communication between clients and servers is nothing short of a secure tech performance.
Advantages of SSH Authentication
Encryption: SSH employs robust encryption methods to secure data during transmission, thwarting unauthorized access and eavesdropping. This stringent safeguard guarantees the confidentiality of sensitive information.
Authentication: SSH employs powerful authentication methods, such as passphrases, public key cryptography, and multi-factor authentication. Users enhance security by entering a secret passphrase, adding an extra layer beyond conventional passwords. Public key cryptography involves users generating a pair of cryptographic keys—a public key (shared openly) and a private key (kept confidential). Access is verified by matching the public key with the private key on both the client and server devices. Multi-factor authentication fortifies the process by requiring users to provide multiple forms of identification, such as a combination of passwords, temporary codes, or biometrics.
Key-Based Authentication: SSH introduces a more secure alternative to password-based authentication through the use of public and private key pairs. This eliminates the need to transmit passwords over the network, significantly enhancing security.
Secure File Transfer: SCP (Secure Copy) and SFTP (Secure File Transfer Protocol) utilize the core aspects of SSH to ensure secure file transfer capabilities, establishing a trustworthy environment for exchanging files between systems.
Tunnelling: SSH supports tunnelling, creating secure communication channels for various network services like HTTP, VNC, or database connections. The encryption of public keys ensures that only the recipient device, equipped with the private key, can decrypt the data—akin to protecting data transfer through a tunnel with decryption only occurring at the tunnel's end, specifically at the intended recipient's machine. This meticulous process significantly heightens the overall security of network communications and excels at preventing middleman attacks.
Cross-Platform Compatibility: SSH boasts wide-ranging support across diverse operating systems, positioning itself as a versatile and interoperable solution for secure remote access and management. Its compatibility ensures a seamless and secure experience across different platforms.
Step-by-Step Guide: Generating SSH Key Pair and Cloning
1. Generate an SSH Key Pair:
To expedite the SSH key generation process while maintaining a clutter-free filesystem, utilize the provided script here. This script streamlines the complexities of key generation, ensuring perpetual use even after device shutdowns—assuming the key file remains intact. Proceed to step 5 after copying the generated SSH public key.
Alternatively, run the following commands to generate an SSH key pair linked to your GitHub account via your email address.
ssh-keygen -t rsa -b 4096 -C "your-github-email"
2. Set Proper Permissions for Your Private Key:
Avoid permission denial errors by setting the correct permissions for the private key file.
chmod 600 ~/.ssh/id_rsa
3. Configure Environment Variables for SSH Agent:
Enable communication with the SSH agent, a program managing private keys for public key authentication. This background process stores decrypted private keys in memory, allowing programs such as
sshto authenticate without constant password prompts or permission denials. This step sets the necessary environment variables, such asSSH_AUTH_SOCK.eval $(ssh-agent)ssh-add ~/.ssh/id_rsa
4. Display and Copy Your SSH Public Key:
Print your SSH public key to the screen.
cat ~/.ssh/id_rsa.pub
5. Add SSH Key to GitHub:
Visit your GitHub account settings by clicking on your
profile imageand selectingSettings
On the left sidebar, choose
SSH and GPG Keys.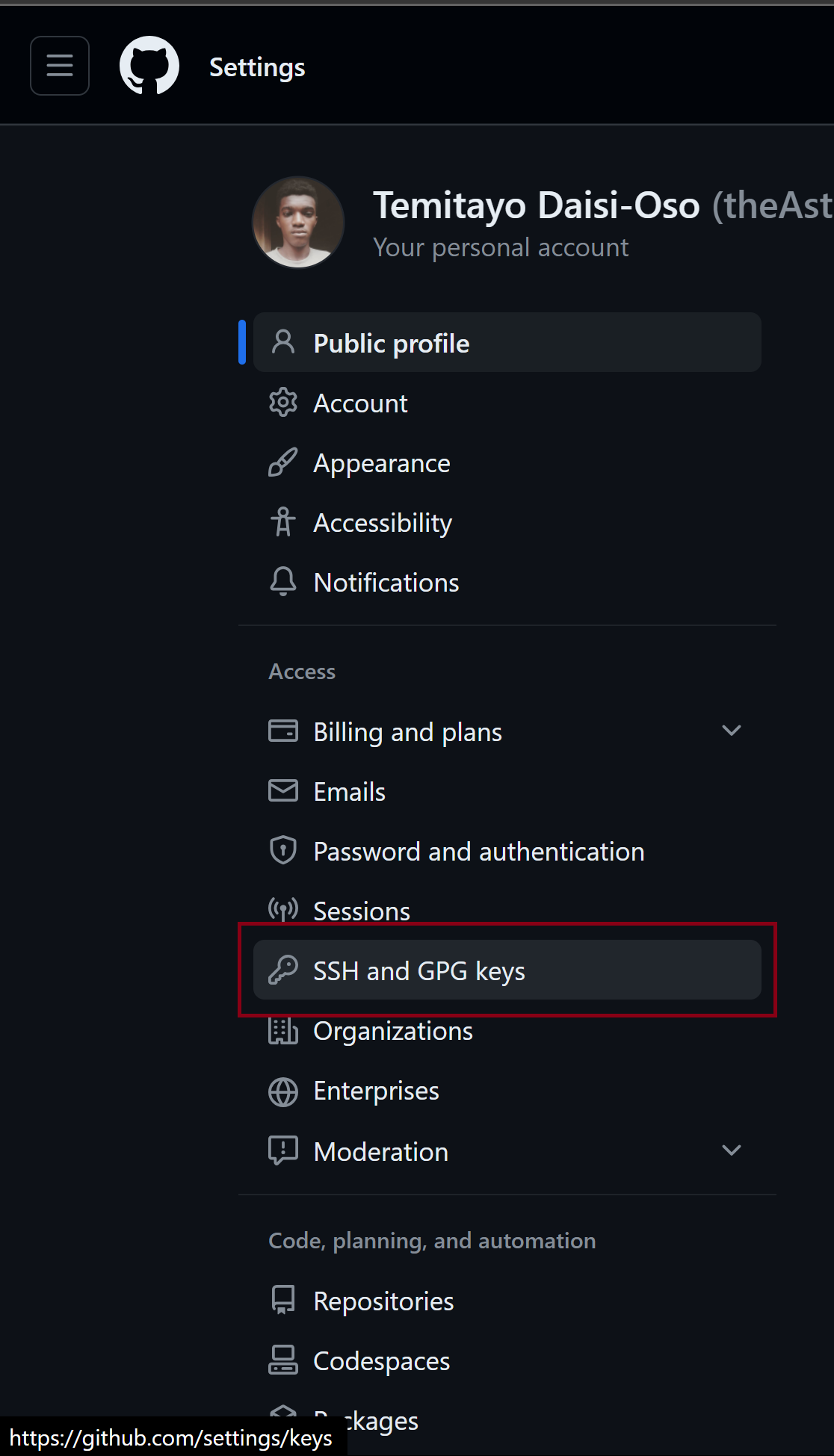
Click
New SSH key.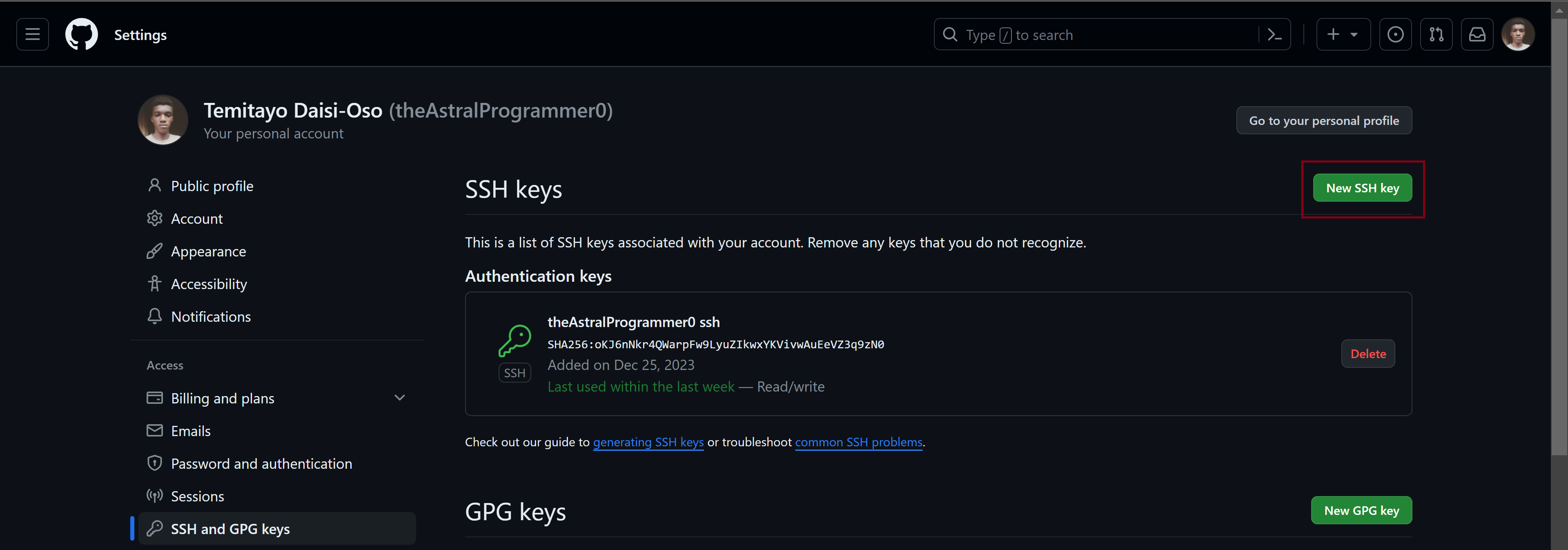
Provide a relevant
Title, paste the copied SSH public key into theKeysection, and clickAdd SSH key.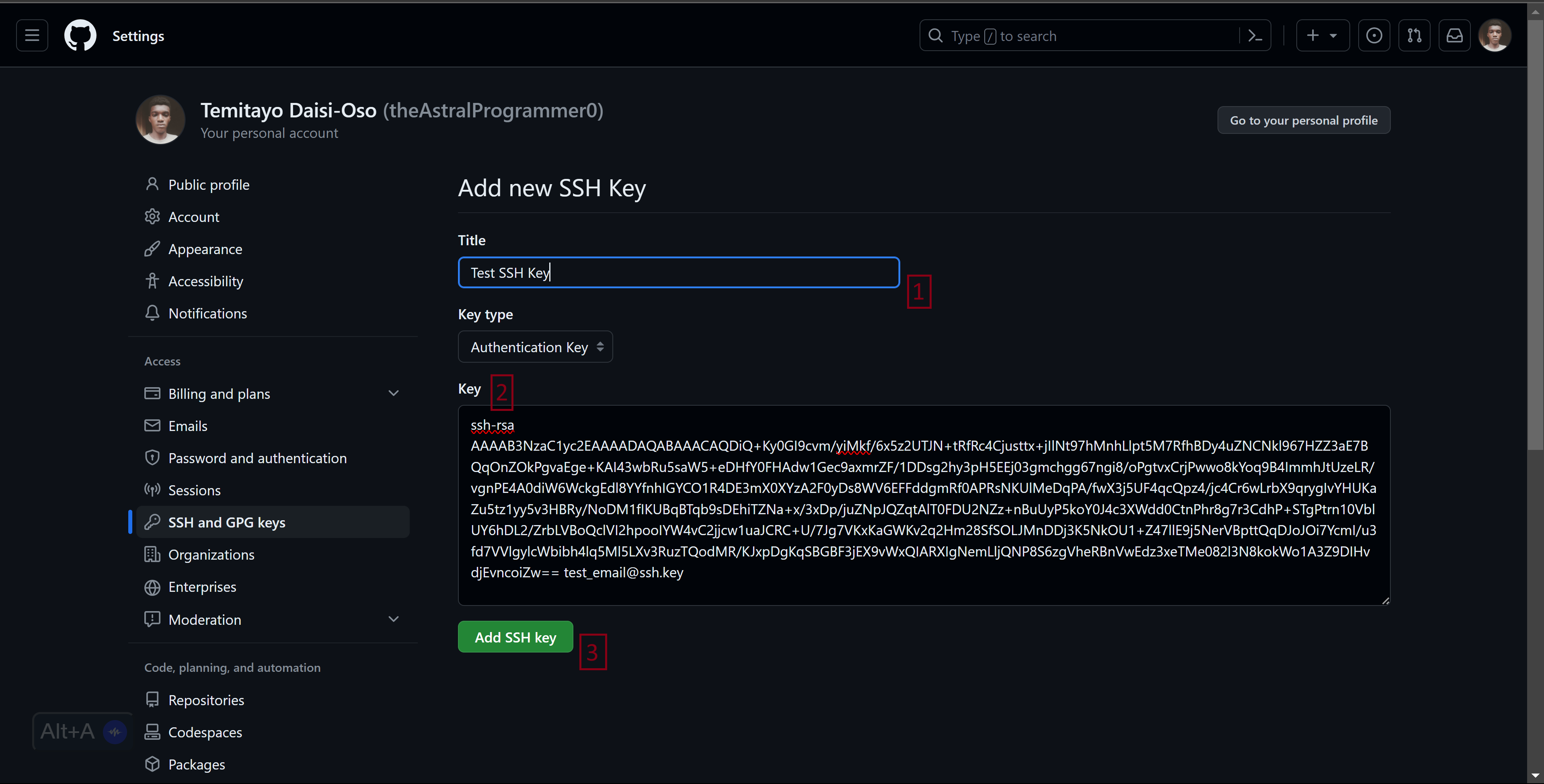
6. Clone Your GitHub Repository:
Navigate to the repository you wish to clone.
Click on the
Codedropdown on the repository page.Select the
SSHTab and copy the URL.Open your terminal, type
git clone, and paste the URL.
7. Test Your SSH Connection:
Ensure a successful SSH connection to GitHub by running the following command:
ssh -Tgit@github.comYou should receive a confirmation message indicating a successful connection. Your SSH key is now set up, and you're ready to securely interact with your GitHub repositories.
Subscribe to my newsletter
Read articles from Temitayo Daisi-Oso directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Temitayo Daisi-Oso
Temitayo Daisi-Oso
Meet Temitayo, a coding virtuoso and a cool visionary with an unquenchable thirst for innovation. Focused on joining the Mars exploration team, he dreams of propelling humanity to new heights. At the same time, Temitayo aspires to make a mark in Meta, developing cutting-edge software for Mixed Reality. With each line of code, he's shaping a future where technology not only reaches the stars but also transforms our daily reality.