Journey through Cybersecurity: Mastering Fundamental Network Tools for Troubleshooting Reconnaissance and Attack!
 Adrian
Adrian
Do you also know people who are fascinated by technical innovations and the latest gadgets, but...? There are IT specialists who know the latest tools, but do not know or do not remember the basic ones. To use these advanced super gadgets, you need to know the basic tools. The ones I am writing about today are the basis of the IT world. Every network specialist and cybersecurity specialist must know them and know when and how to use them! Only then should they start using the rest of the super advanced gadgets and tricks!
Ping
Do you know what the acronym PING stands for?|
Ping may evoke different associations for everyone. Maybe Ping-Pong? Or maybe a submarine or a bat?
The full name of the tool is Packet InterNet Groper.
This tool is used to verify a point in the network. Ping checks whether a device is alive and responds to IP messages. Ping sends an ICMP echo request to the point. If the tested node responds, you will see a summary of the measured waiting times and the number of packets lost. Receiving a response after a long time with a large number of lost packets suggests communication problems. If the tested node is not working, an ICMP error will be returned stating that the request has expired/timed out.
In addition to the target address, we can provide other parameters, there are several of them and they are very useful. Let's check what's hidden in the ping options!
ping /? # Displays a description of the ping command syntax
-t # Ping will continue to send packets to the node until ctrl+c is pressed
-l packet_size # You can set the size of the sent packet in bytes
-a # Ping will try to translate the provided IP address into a computer name/symbolic name
-n number # Specifies the number of packets sent
-i TTL # You can specify the value of the time-to-live parameter in the header of the sent packet, i.e. the maximum number of allowed intermediary nodes on the way to the destination address. The maximum value is 255
PoD attack
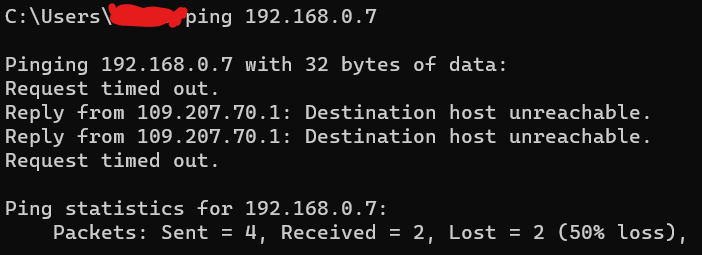
Ping Of Death, It's a type of attack on a computer that uses specially formatted ping packets, i.e. ICMP (Internet Control Message Protocol) packets, to cause the target system to crash, restart or freeze. This attack exploits the fact that the length of an ICMP packet can be larger than the maximum allowed packet size (standard 65535 bytes for an IP packet). Back when the PoD attack was more popular, many systems were unable to properly handle such a large packet, leading to buffer overflows and system failures .
ping -t -l 65535 192.168.0.7
Ping flood
Ping flood is a type of network attack that uses the "ping" tool, i.e. the ICMP (Internet Control Message Protocol) Echo Request command, to overload a network or a specific system with a large number of ping packets. This attack is a type of DoS (Denial of Service) attack, where the goal is to bombard the target system with so many ping requests that it is unable to respond to legitimate traffic or stops functioning altogether.
See also:
https://www.kali.org/tools/hping3/
https://fping.org/
https://www.darknet.org.uk/2017/07/t50-fastest-mixed-packet-injector-tool/
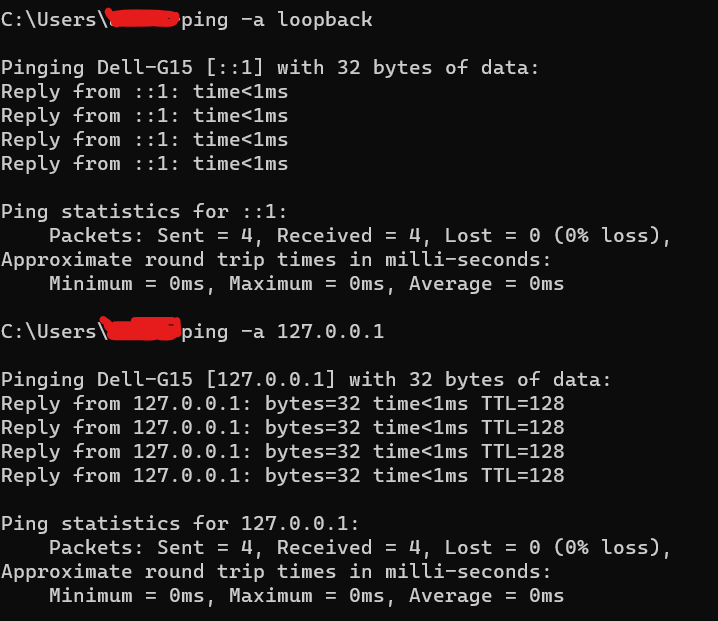
Loopback 127.0.0.1
By checking the connection to this address, you will check the operation of your computer bypassing external network connections/nodes. If the ping command does not get the expected responses, know that the problem is with your computer and not with the network or Internet provider.
If you are experiencing network connectivity, you should first use ping. Thanks to this, you can quickly check whether everything is working properly.
IPConfig
This tool, along with ping, is the basis of the basics! It is used as often as a toothbrush. You can use it to obtain a lot of valuable information. The IP protocol allows data packets to be sent from a source to the correct destination based solely on the IP address. The packet contains information that we send to the destination.
ipconfig /all # You can, among other things, check until when the IP address assignment (DHCP) is valid.
ifconfig -a
# These commands (1. windows), (2. linux) are used to display detailed information about the network configuration of your computer.
After entering the command at the command line, you have a wealth of information available to you. You can start verifying your network settings and your assumptions about the nature of the problems encountered! The command will display information about IP addresses and network gateways for each network adapter running on the tested computer. The default gateway address is the private address of your router. It is literally a gateway to access the Internet or other networks.
ipconfig /release # All assigned IPv4 addresses on a given computer are forgotten and returned to the DHCP server
ipconfig /renew # New IP address values are downloaded from the DHCP server along with the subnet mask, DNS addresses, and default gateway address
ipconfig /displaydns # Displays all domain names and their associated IP addresses
ipconfig /flushdns # Clearing the DNS cache
DNS Poisoning / DNS Spoofing
This attack is based on the adversary deliberately spoofing the DNS cache, as a result of which the domain name is associated with the wrong IP address and network traffic is redirected to the wrong destination!
See also:
https://www.okta.com/identity-101/dns-poisoning/
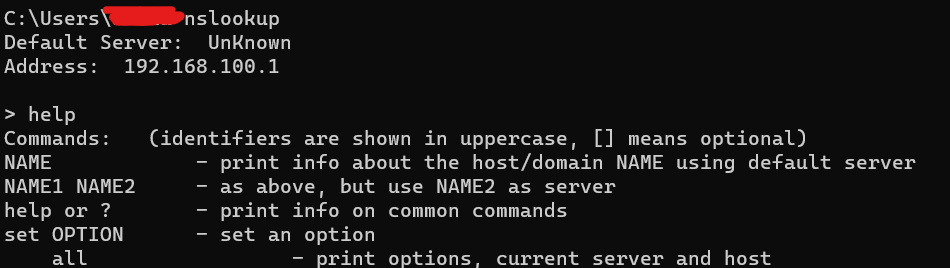
NSlookup
Name server lookup - as the name suggests, it will be useful primarily when you encounter problems with DNS operations. Thanks to this, you can determine the numeric IP address knowing its domain name and vice versa - find the domain name for the given IP address. You can also find the name of the mail server for a given domain. NSlookup can be use in interactive and non-interactive mode.
To run the tool in interactive mode, type nslookup and press enter ( type exit or ctrl + c to go back to cmd )
To run the program in non-interactive mode, enter nslookup ajcyb3r.com
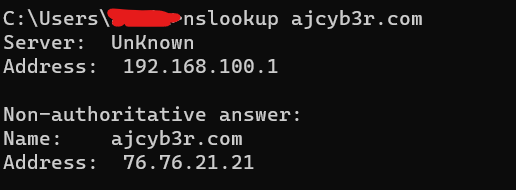
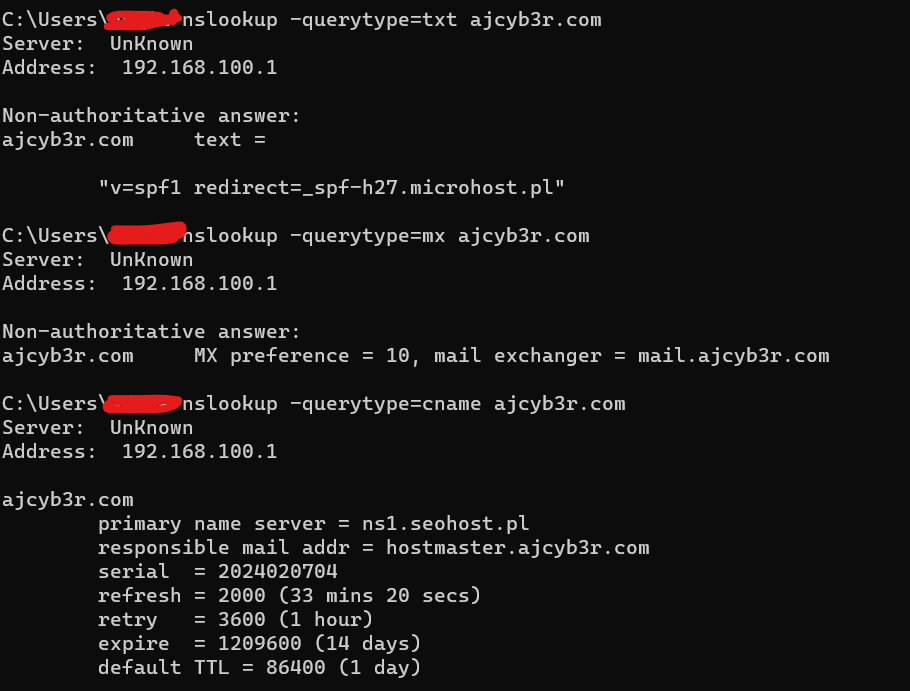
You can use the -querytype argument to read other information about the domain and server, not just the address. You can check the domain's DNS records. You can use it to check the DNS records of a given host or domain, which is a basic step in network reconnaissance.
See also:
https://www.ibm.com/docs/en/om-nm/5.6.0?topic=pstac-nslookup-command
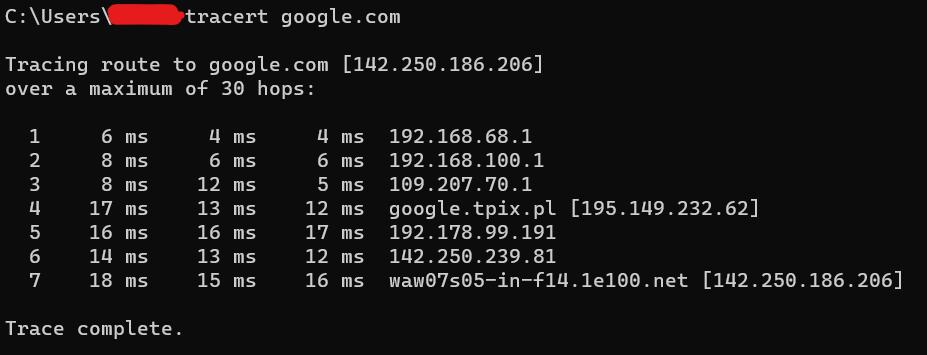
Tracert
This program is a very useful diagnostic tool. It allows you to determine the route that the package must take from London to Barcelona, from your home to Hong Kong, etc. This program is a very useful diagnostic tool. It uses ICMP request messages for this purpose. The tracert command displays the route taken by a packet. The list of intermediary routers and processing time are also saved.
Why is this so important?
Because thanks to this tool you can find out where packets are delayed or blocked.
! NOTE !
Here I am describing tracert, I am not focusing on Linux (we will get to that). However, the traceroute tool sends packets using UDP protocol and the Windows tracert tool sends ICMP protocol echoes.
PathPing
After tools like ping and tracert, it would be nice to have both, wouldn't it?
It would be nice to be able to diagnose intermediate points on the route to the destination. And there is such a tool! Running this command examines the connection to each of the intermediate nodes on the route to the destination node, just as if you had used the ping command for each one. Best of all, as a result of executing this command, not only the entire route between computers is examined, but also the connection test result for each intermediate point.
pathping /? # Displays options that are explained, so I do not expand on them further
It is important to emphasize that pathping information cannot be fully relied on, primarily because public network nodes are involved in communication. Because they are publicly available, they may be overloaded or may be protected by ICMP messages sent by pathping. This is where mechanisms such as control plane policing come into play (CoPP).
See also:
https://study-ccnp.com/cisco-copp-control-plane-policing-configuration/
Pathping is particularly useful in diagnosing network problems, such as high latency or packet loss, that can affect the quality of your Internet connection. With detailed information about each node along the route, users can identify which segment of the network is causing the problem, which is especially useful in large networks and when troubleshooting Internet connections.
In the context of cybersecurity, pathping is a diagnostic tool that can provide valuable insights into the operation of network infrastructure, helping to identify, diagnose, and mitigate risks associated with various network threats.
Address Resolution Protocol - ARP
The ARP table is a key method of storing information obtained using the ARP protocol, which plays an important role in the network communication process. This protocol enables the identification and recording of MAC and IP address pairs of devices connected to the network, ensuring efficient data exchange. Each network device has its own ARP table, which contains information about the addresses with which it communicates.
Thanks to the ARP protocol, there is no need to constantly discover MAC and IP address pairs with each data transmission. Once an address pair is identified, this information is written to the ARP table and stored for a set period of time. If there is no information about the IP address of the target device in the ARP table, the protocol initiates sending a broadcast message to all devices in the given subnet to determine the MAC address of the recipient. This procedure ensures smooth and efficient communication between network devices. It is worth noting that ARP is used for IPv4. In IPv6 NDP (Neighbor Discovery Protocol) is used.
The ARP table is crucial in communication! Without it, each host would have to ask for the MAC address of the destination, which would slow down network performance tremendously!
arp -g / arp -a # Shows the ARP Table
arp -d ip_address # Deletes an entry from ARP Table
arp -s # Adds static entry
If necessary, a single entry can also be removed from the ARP table. To delete an ARP entry via the command line, most systems offer a command similar to arp -d ip_address to eliminate a specific entry.
Following this, you have the option to manually replace the deleted entry or wait for it to be automatically repopulated during the next ARP request, ensuring the ARP table remains up-to-date and accurate.
After deleting, you may want to add an entry. We can do it manually or wait until the ARP Table updates itself automatically when the connection between network points is made.
arp -s ip_address mac_addres
arp -s 192.168.68.110 00-aa-11-bb-33-cc
Delete an entire ARP Table
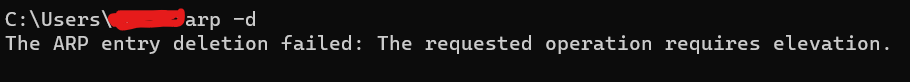
Experiencing issues with a malfunctioning ARP table can disrupt network communication, rendering a device unable to connect with others on the network. Despite the potential severity of this problem, rectifying it by purging the ARP cache is a relatively simple and harmless procedure.
The device's ARP table will naturally reconstruct itself via new ARP requests. Clearing the ARP table to facilitate its reconstruction is a straightforward remedy for any ARP-related problems.
Knowing some basics, we can look at ARP Poisoning
ARP Poisoning, also known as ARP spoofing, occurs when an attacker sends forged ARP messages across a Local Area Network (LAN). This is done to associate the attacker's MAC address with the IP address of a legitimate computer or server within the network. Once the attacker's MAC address is linked with an authentic IP address, they can intercept messages intended for the legitimate MAC address. As a result, the attacker can capture, modify, or block communications meant for the legitimate device. The term address resolution refers to the process of finding the MAC address that corresponds to a given IP address of a computer on the network.
What is an ARP Attack on a Router?
An ARP attack can target to deceive a host computer or network router. If a router is tricked into associating the wrong MAC address with a given IP address, all communication is misdirected to the incorrect host.
What is ARP Cache Poisoning?
In the ARP protocol, hosts on a network automatically cache all received ARP responses, regardless of whether they requested them and without authenticating their source. This vulnerability in the protocol allows for ARP spoofing by altering entries in the ARP cache, creating an opportunity for attackers to manipulate or disrupt network communications.
See also:
https://kalilinuxtutorials.com/macof/
https://charlesreid1.com/wiki/MITM/Wired/ARP_Poisoning_with_Ettercap
How to detect ARP attack?
Numerous tools, both commercial and open-source, can detect ARP cache poisoning. Yet, you can simply inspect your computer's ARP tables without any installations. By executing the arp -a command in the terminal you can view the current IP-to-MAC address associations.
For ongoing network surveillance, applications such as arpwatch and X-ARP are valuable, notifying administrators of potential ARP Cache Poisoning Attacks. Nevertheless, the issue of false positives may lead to a high volume of unnecessary alerts.
See also:
https://www.kali.org/tools/arpwatch/
Netstat
The network statistics command displays the number of incoming and outgoing network connections, routing tables, and other details, depending on the parameters used. This information allows you to assess network traffic and detect slow connections. Sounds simple, doesn't it?
From the point of view of cybersecurity, it is important to be able to check which ports enable opening incoming connections, which ports are currently used for transmission and what is the status of existing connections. In the netstat output, the status of all currently existing network connections is shown. This knowledge is useful for configuration and for diagnosing errors.
netstat /? # Displays help and a list of available options
netsta -a # Displays all connections and listening ports
When you run the command you will see 127.0.0.1 or 0.0.0.0. Loopback address and zeros? This value should be understood as "no specific address" - it means that the connection has not been established yet, but some process on the local machine is waiting for incoming connections. The number written next to the address, separated by a colon, is the port number. Here I could expand and describe the ports, Well-Known Ports, Registered Ports, Dynamic Ports. However, I am focusing here on the netstat tool.
netstat -p IP # Detailed information about packets transmitted and received by network interfaces based on the IP
When you use this command, netstat will provide detailed information about packets transmitted and received by network interfaces based on the IP protocol. This includes data such as the number of packets received and sent, errors, packets discarded, etc.
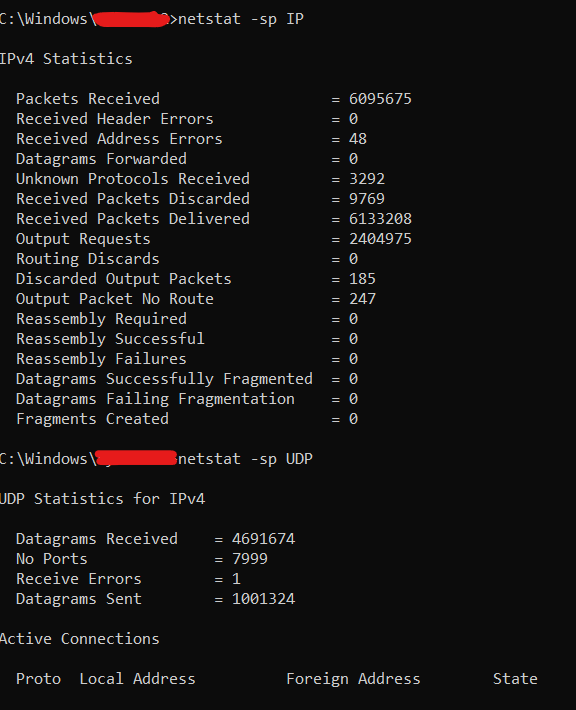
Netstat offers useful information about local network connections and configurations that can be used in the following scenarios:
Identification of active connections,
Detection of unauthorized connections,
Understanding network configuration,
Diagnose network problems.
Save netstat output to a file
When working with netstat, there is often a need to save the output for a given command with parameters. To do this, simply use the '>' operator followed by the file name.
netstat -nao > my_connections.txt
-n # Displays addresses in numerical form instead of trying to resolve domain names
-a # By default, netstat only shows active socket connections, adding -a expands the output to include ports that are listening, which is useful for identifying open ports
-o # This is a Windows-specific parameter that adds a "PID" (Process ID) column to the output
There are two port numbers to pay attention to during diagnostics, 4444 and 31337. Port 4444 is used by default by metasploit to listen for incoming connections. Port 31337 can be treated as a record of the word 'eleet' (leet speak).
In such situations, there is nothing left but prayer 😂
But seriously,
Pulling out the network cable may help during an attack, but evidence may be destroyed - for the incident response department.
See also:
https://pl.wikipedia.org/wiki/Leet_speak
https://1337.me/
https://www.metasploit.com/
To sum up
All these tools should be known to every IT specialist, especially a network specialist and a cybersecurity engineer.
These are basic, but invaluable tools that, as seen above, can provide a lot of information and output. The only thing left is learning through practice.
This is the only way to remember these useful and useful tools and their parameters! They seem like simple tools, but it took me a lot of time to describe and organize this knowledge.
I did not delve into everything, because many of the topics discussed would need to be developed in separate entries - the ports and protocols themselves would be a topic for several or a dozen blog posts ( if not a book or books 😯 ).
My main goal was to remind myself of these tools, and this post was also created for others who like to learn and repeat materials.
I noticed that thanks to repetitions and returning to the basics, I remember these tools much better and use these tools at work more often. It's great that several tools allowed me to describe attacks and link several tools useful in work and study.
I will definitely come back to these tools again and then I will remember them even better!
Subscribe to my newsletter
Read articles from Adrian directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Adrian
Adrian
IT Engineer who loves to create something out of nothing. I write, I create, I educate! Social Engineering enthusiast! Python, Wireshark, Kali, RHEL