Day 1 : Understanding the ABCs of Security Testing: SAST, DAST, IAST, IAC, and API Security
 Suresh Kumar S
Suresh Kumar S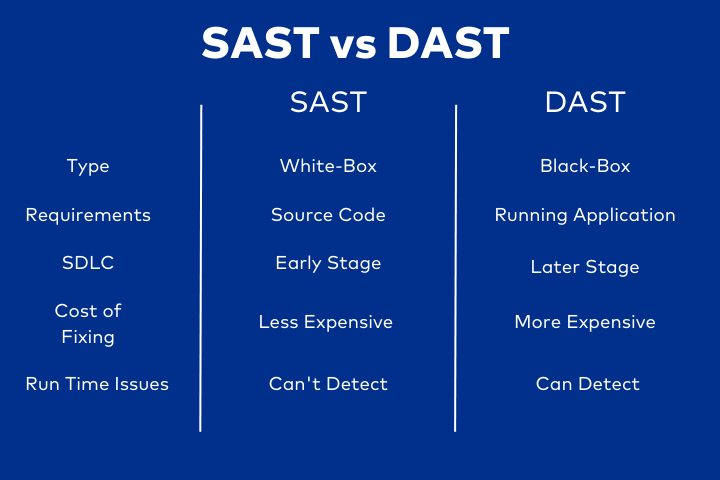
In today's interconnected digital landscape, ensuring robust security measures is non-negotiable. But what exactly are the different types of security testing, and how do they safeguard our systems? Let's delve into the alphabet soup of security testing:
SAST (Static Application Security Testing): SAST involves analyzing source code to identify potential security vulnerabilities early in the development process. It's like having a vigilant guardian scrutinizing every line of code for weaknesses before deployment.
DAST (Dynamic Application Security Testing): DAST, on the other hand, simulates attacks on a running application to detect vulnerabilities from an external perspective. It's akin to stress-testing your application's defenses against real-world threats.
IAST (Interactive Application Security Testing): Combining the best of both worlds, IAST operates within the application runtime environment, providing real-time feedback on vulnerabilities while the application is running. It's like having an embedded security advisor guiding you through potential risks in real-time.
IAC (Infrastructure as Code) Security: With the rise of DevOps and cloud-native architectures, securing infrastructure code becomes paramount. IAC security ensures that the code used to provision and manage infrastructure is free from vulnerabilities, reducing the attack surface and bolstering overall resilience.
API Security: As APIs become the backbone of modern software development, safeguarding them is critical. API security focuses on protecting APIs from threats such as unauthorized access, injection attacks, and data breaches, ensuring secure data exchange between applications.
Understanding these different types of security testing is crucial for building resilient software systems in today's threat landscape. Embracing a holistic approach that encompasses SAST, DAST, IAST, IAC, and API security empowers organizations to stay ahead of potential threats and safeguard their digital assets effectively.
🔔 Stay updated with the latest tech tutorials and insights! Follow my blog:
https://imsuresh.hashnode.dev/
🔔)Let's expand our professional network on LinkedIn! Connect with me here:
https://www.linkedin.com/in/suresh-kumar-s-profile/
However, if you have any more questions or need assistance with anything else, feel free to ask!
~ Suresh Kumar
Subscribe to my newsletter
Read articles from Suresh Kumar S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suresh Kumar S
Suresh Kumar S
Experienced AWS DevOps Engineer with 9+ years in IT, specializing in AWS for over 5 years. Holder of 5 AWS certifications, adept at optimizing infrastructure and driving efficiency.