Day3: Exploring the STRIDE Concept
 Suresh Kumar S
Suresh Kumar S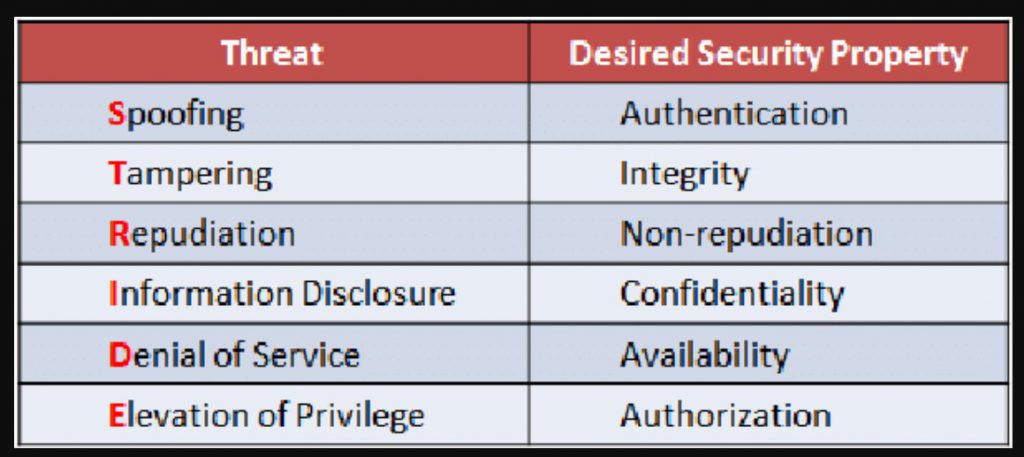
In the vast landscape of cybersecurity, understanding potential threats is paramount. With the proliferation of digital systems and the increasing reliance on interconnected networks, it’s crucial to identify and mitigate potential risks effectively. One valuable framework in this endeavor is the STRIDE concept.
What is STRIDE?
STRIDE is an acronym representing six different types of security threats that can compromise the integrity, availability, and confidentiality of information within a system. Each letter in the acronym corresponds to a distinct threat category:
S - Spoofing: This threat involves masquerading as someone else to gain unauthorized access. It includes various forms of identity deception, such as IP spoofing, email spoofing, or DNS spoofing.
T - Tampering: Tampering refers to unauthorized modification of data, either in transit or at rest. This can include altering the content of messages, files, or configuration settings to manipulate the behavior of a system or application.
R - Repudiation: Repudiation threats involve denying an action or event that has taken place. In the context of cybersecurity, this could mean a user denying that they performed a particular action, such as sending a message or making a transaction.
I - Information Disclosure (or Information Disclosure): Information disclosure threats involve the unauthorized exposure of sensitive data. This could include confidential documents, personal information, or cryptographic keys being accessed by unauthorized parties.
D - Denial of Service (DoS): Denial of Service attacks aim to disrupt the normal functioning of a system or network, making services unavailable to legitimate users. This can be achieved through various means, such as overwhelming a server with traffic or exploiting vulnerabilities to crash a system.
E - Elevation of Privilege: Elevation of Privilege threats involve gaining unauthorized access to resources or functionality beyond what is typically allowed for a user or application. This could involve exploiting vulnerabilities to escalate privileges or bypassing access controls to gain administrative rights.
Applying STRIDE in Practice
Understanding the various threat categories outlined by STRIDE is essential for building robust cybersecurity defenses. By analyzing potential vulnerabilities through the lens of these six threat types, organizations can develop more comprehensive risk mitigation strategies.
For example, when designing a new software application, developers can conduct a STRIDE analysis to identify potential security weaknesses. This may involve assessing how the application handles user authentication (Spoofing), data validation (Tampering), audit logging (Repudiation), sensitive data storage (Information Disclosure), resource utilization (Denial of Service), and access control (Elevation of Privilege).
By systematically addressing each of these threat categories during the design and implementation phases, developers can implement appropriate safeguards to mitigate the risks effectively. This might include implementing encryption protocols to protect sensitive data, enforcing strict access controls, implementing intrusion detection systems to detect and respond to anomalous activity, and regularly updating software to patch known vulnerabilities.
Conclusion
The STRIDE concept provides a valuable framework for understanding and addressing cybersecurity threats effectively. By systematically analyzing potential risks across six distinct threat categories, organizations can develop more robust security strategies to protect their systems and data from unauthorized access, manipulation, and disruption.
In an ever-evolving threat landscape, proactive measures are essential to stay ahead of malicious actors. By integrating STRIDE analysis into their cybersecurity practices, organizations can enhance their resilience to emerging threats and safeguard their digital assets effectively.
🔔 Stay updated with the latest tech tutorials and insights! Follow my blog:
https://imsuresh.hashnode.dev/
🔔)Let's expand our professional network on LinkedIn! Connect with me here:
linkedin.com/in/suresh-kumar-s-profile
However, if you have any more questions or need assistance with anything else, feel free to ask!
~ Suresh Kumar
Subscribe to my newsletter
Read articles from Suresh Kumar S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suresh Kumar S
Suresh Kumar S
Experienced AWS DevOps Engineer with 9+ years in IT, specializing in AWS for over 5 years. Holder of 5 AWS certifications, adept at optimizing infrastructure and driving efficiency.