Computer Networking Course: How does the internet work?
 Suraj
SurajTable of contents
- How did it all start?
- WWW came into the picture:
- Client-Server Architecture:
- How is data Transferred?
- What is a network?
- Modem/Router:
- Topologies:
- Structure of the Network:
- OSI (Open System Interconnection) Layer:
- TCP/IP Model(5 Layers):
- Peep-to-Peer Architecture:
- Networking Devices:
- Protocols:
- Sockets:
- Ports:
- 3-Way Handshake:
- MAC Addresses:
- VPN tunneling
- TLS and SSL

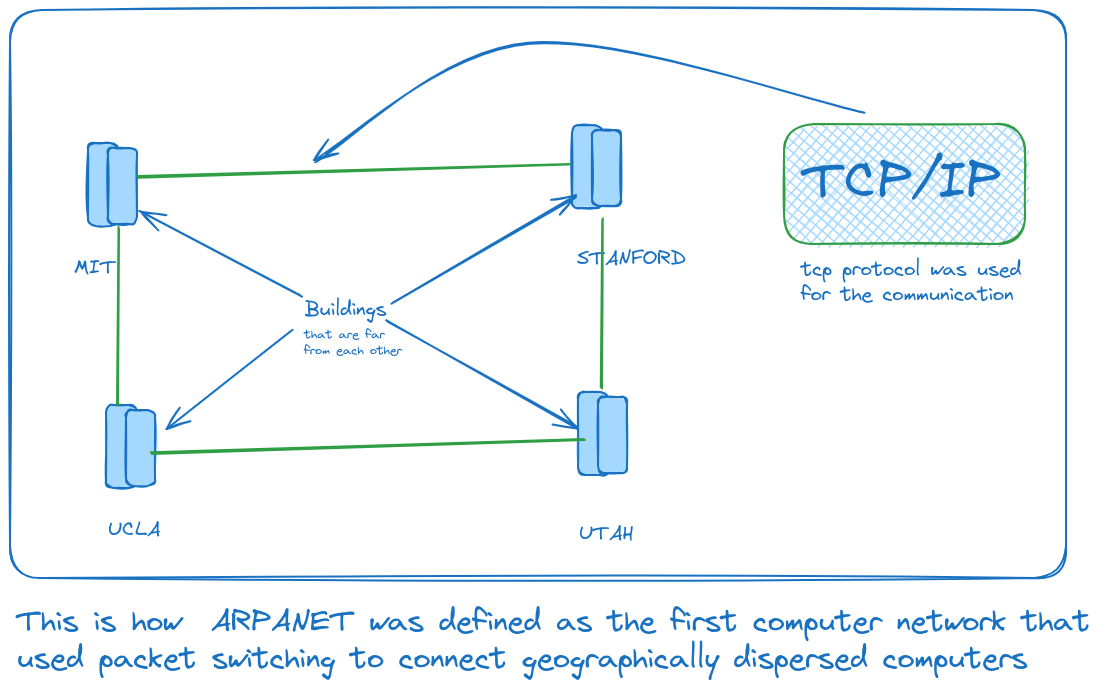
How did it all start?
During the Cold War, the United States and the Soviet Union competed to be the best.
In 1957, the Soviet Union surprised everyone by launching Sputnik 1, the first man-made satellite.
To keep up, the U.S. created ARPA (Advanced Research Project Agency) to stay ahead in science.
ARPA made ARPANET, the first big computer network using packet switching.
ARPANET laid the foundation for the internet we use today, changing how we connect and work together.
The U.S. Advanced Research Projects Agency Network (ARPANET) was the first big computer network. It started in 1969 and stopped in 1989. ARPANET was mainly for academics and research.
WWW came into the picture:
We wanted to easily share research papers, but couldn't because there was no automatic way to do it.
Then, Mr. Tim Berners-Lee created the World Wide Web (www). It lets us store and access documents online. However, back then, we couldn't search for things on the website.
This is the world's first website
- The World Wide Web, also called the Web, is a place on the Internet where we find documents and other stuff. Each thing has its special address called a URL, like
https://example.com/.These things can link to each other, and we can access them through the internet.
Who is responsible for managing all this stuff:
The Internet Society is responsible for all the rules and regulations that we have to send our data over the Internet.
Client-Server Architecture:
This is the typical client-server model:
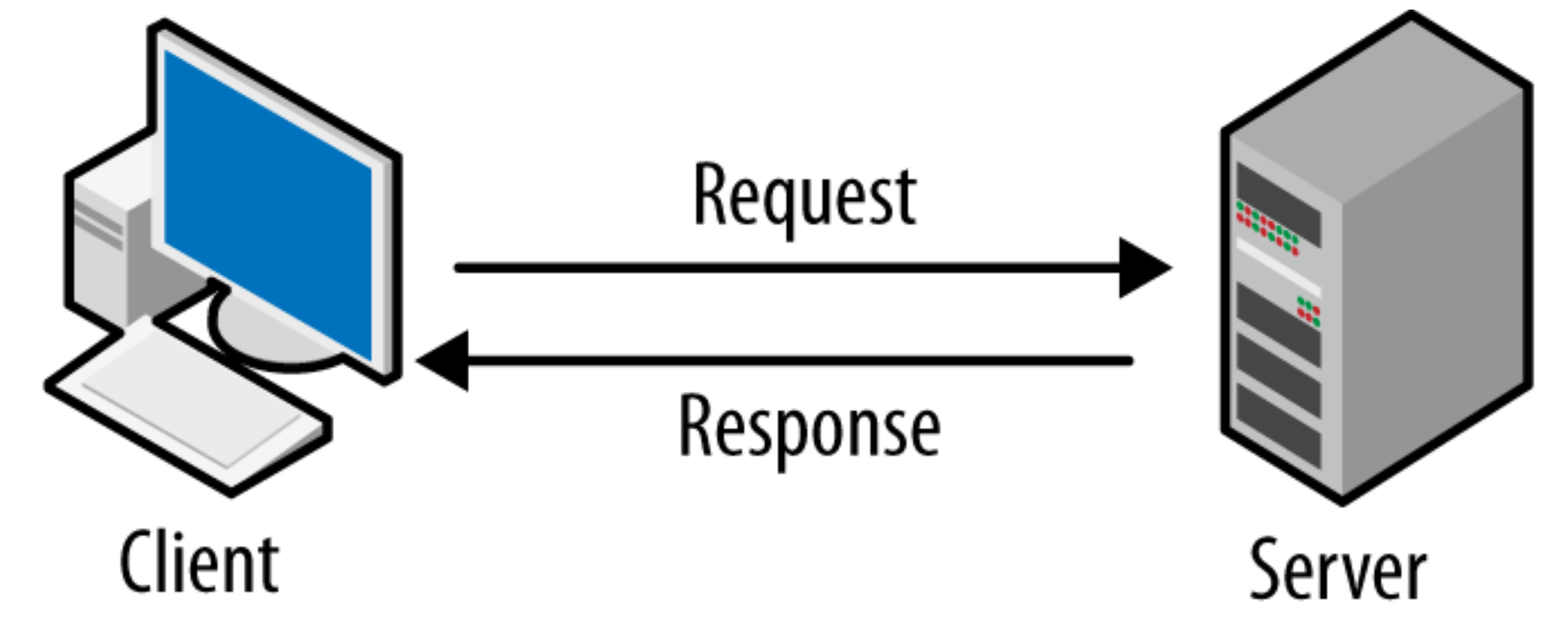
Your computer/laptop can work as a client and server.
The client-server model is a way computers communicate over networks.
In this model, one computer acts as a client, requesting services or resources.
Another computer acts as a server, providing those services or resources.
These computers can be anywhere in the world, connected by wires laid under oceans.
Your computer or laptop can act as both a client, requesting information, and a server, providing information, depending on the situation.
Submarine cables map (Optical Fibre Cable)
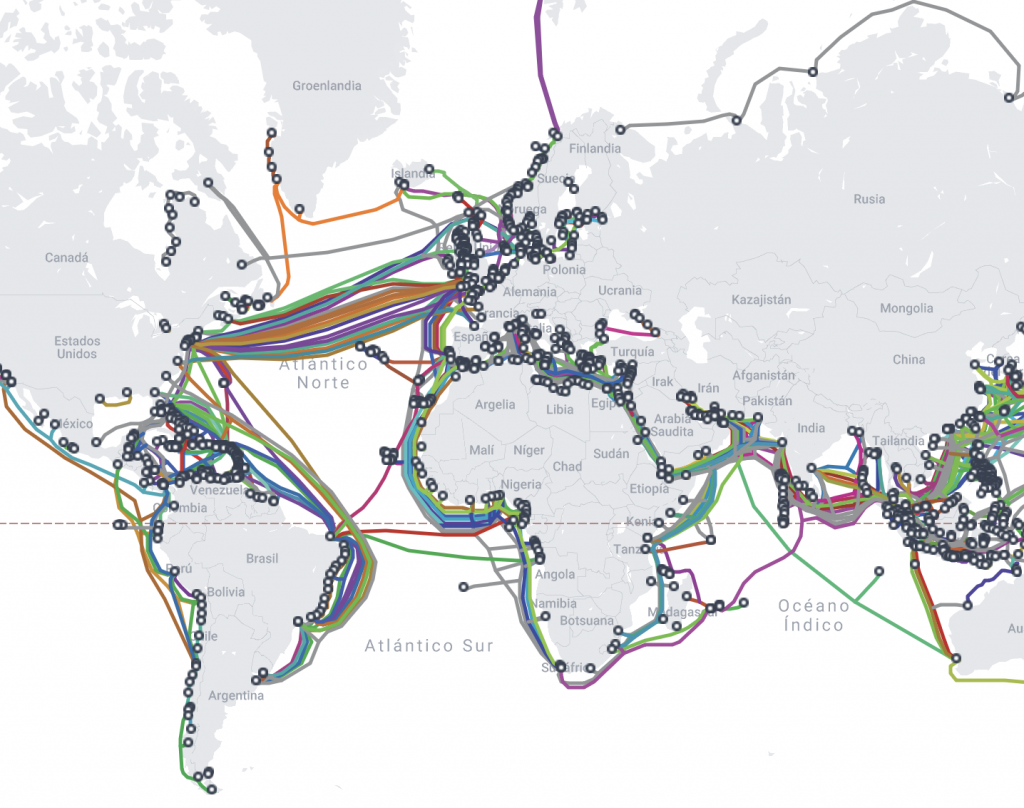
”So the internet is not like in the clouds but it’s under the sea”
How is data Transferred?
Packets: Packets are small chunks of data that travel across networks like digital envelopes. They have destination addresses and come together to deliver messages or files.
This is how the data is transferred:
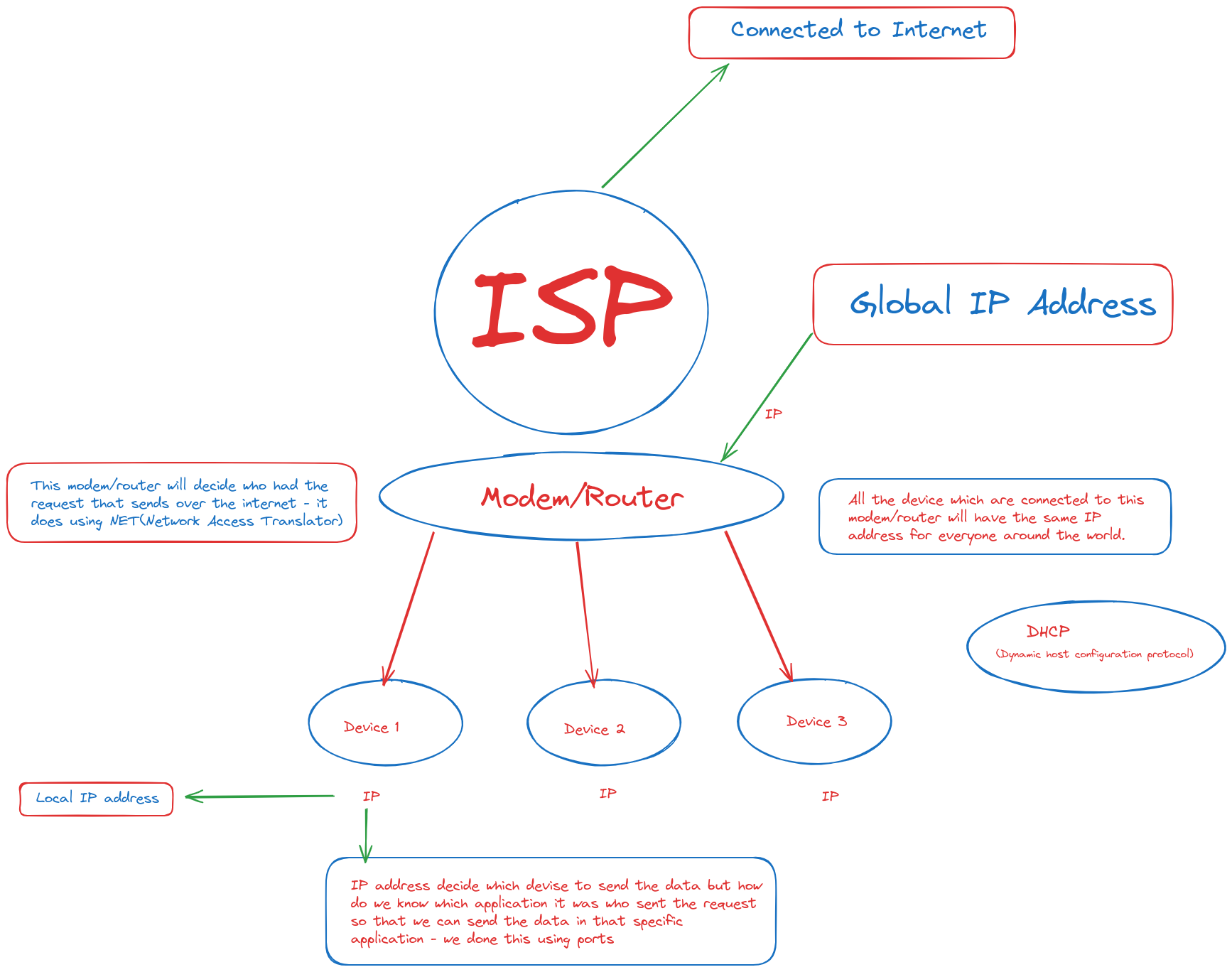
Connected to the Internet: Devices connect via Wi-Fi, Ethernet, or mobile data.
ISP (Internet Service Provider): Provides internet access.
Modem/Router: Provided by the ISP, assigns global IP addresses.
Device1,2,3: Receives local IP addresses via DHCP for communication within the network.
IP (Internet Protocol): Global IP identifies devices on the internet; local IP identifies devices within a network.
Data Transfer: Devices package data into packets with destination IP addresses. Modem/router routes packets based on global IP. Destination devices receive and reconstruct data using local IP.
Finally, if we talk:
Devices connect to the internet through an ISP, which assigns a global IP via a modem/router; data is then packaged into packets with destination IP addresses, routed based on global IP, and received using local IP addresses on destination devices for reconstruction.
IP address determines which device you are using and
The Port Number will determine which application you are using to communicate
Tata Communications is the tier 1 ‘ISP’ provided in India
Tier 2 ‘ISPs’ are like Airtel or others…
What is a network?
A network is a collection of network-enabled devices, typically made up of computers, switches, routers, printers, and servers.
PAN(Personal area network):
PAN connects devices within a small area, like a room or an individual.
e.g. include Bluetooth connections between devices or wireless connections within a home.
LAN(Local area network):
LAN is used in small-scale settings such as homes, offices, or schools.
Provides networking capabilities for devices within a limited geographic area.
Typically connected via Ethernet cables or Wi-Fi routers.
MAN(Metropolitan area network):
MAN covers a larger geographical area, such as a city or town.
Used to interconnect various LANs within the same metropolitan region.
Utilizes technologies like fiber optics or wireless connections.
WAN(Wide area network):
WAN spans large distances, connecting networks across cities, countries, or even continents.
Enables communication between LANs and MANs over extensive geographical areas.
Relies on high-speed data transmission technologies like optical fiber cables for long-distance connections.
SONET( Synchronous optical networking): So it carries the data using an optical fiber cable, hence it covers a larger distance.
Frame relay: It is a way to connect your local area network to the wider area network like the Internet.
Modem/Router:
Modem:
A modem is used to convert the digital signal into an analog signal and vice-versa.
Converts digital signals from your devices into signals that can travel over phone lines or cables, and vice versa.
Links your home network to your internet service provider (ISP).
Router:
Directs internet traffic between devices in your home network and the internet.
Uses IP addresses to send data packets to their intended destinations.
Provides features like Wi-Fi, firewall protection, and network management.
Work on the network layer.
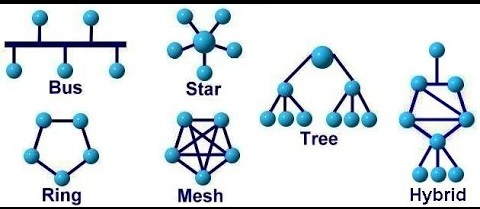
Topologies:
Bus: A network topology where all devices are connected to a single communication line.
Ring: A network topology where devices are connected in a circular manner, forming a closed loop.
Mesh: A network topology where devices are interconnected with multiple redundant paths between them.
Star: A network topology where all devices are connected to a central hub or switch.
Ethernet: Widely used networking standard for LAN, MAN, and WAN networks.
Fast Ethernet: Developed to support data transmission speeds of up to 100 Mbps.
Gigabit Ethernet: Developed to support faster communication networks, reaching speeds of 1 Gbps.
10 Gigabit Ethernet: Standardized with a nominal data transfer speed of 10 Gbps.
Terabit Ethernet: Offers data transfer speeds of 200 Gbps and 400 Gbps.
Structure of the Network:
Let’s understand it by a real-world scenario:
That's how the Internet works
OSI (Open System Interconnection) Layer:
1. Application Layer:
Facilitates communication between applications and users, providing services like email and web browsing.
Example: Sending an email using Outlook.
Protocol: HTTP/HTTPS for web browsing, SMTP for email.
2. Presentation Layer:
Handles data translation, encryption, and compression, ensuring compatibility between different systems.
Example: Viewing an image on a website.
Protocol: SSL/TLS for secure data transmission, JPEG for image compression.
3. Session Layer:
Manages communication sessions between devices, establishing, maintaining, and terminating connections.
Example: Video conferencing with Skype.
Protocol: SSH for secure remote login, NetBIOS for session control.
4. Transport Layer:
Provides reliable end-to-end data delivery, error-checking, and flow control.
Example: Downloading a file using FTP.
Protocol: TCP for reliable transmission, UDP for faster but less reliable transmission.
checksum:
- Data will travel in order and the receiver get in the order.
Times (Retransmission timer):
- The timer starts when you send the data and it’ll expire when the receiver gets the data
UDP (User Datagram Protocol):
Data may or may not be delivered
Data may be corrupted/change
Data may not be in order
UDP uses checksum
UDP Packet:
| Source Port No. (2 bytes) | Length of datagram (2bytes) | | --- | --- | | Destination port No.(2bytes) | Checksum (2bytes) | | Data | |
Use Cases:
It’s very fast
video conferencing apps
DNS also uses UDP
Gaming
sudo tcpdump -c5
TCP (Transmission Control Protocol):
Transport layer protocol
congestion control
The application layer sends lots of raw data, and TCP segments this data → divides it into chunks, and adds headers. It may also collect data from the network layer( data in the form of packets)
Takes care of :
when data does not arrive.
Maintains the order of data using sequence numbers.
Features:
Connection-oriented( means first the connection must be established)
Error-control
Congestion control
Full-Duplex (two-way communication)
5. Network Layer:
Handles routing and forwarding of data packets across networks, enabling inter-network communication.
Example: Sending data between two computers on different networks.
Protocol: IP for addressing and routing packets, ICMP for network diagnostics.
Control place:
Routers are responsible for managing nodes within a network.
Links establish connections between nodes and are referred to as edges.
Static Routing:
- Implemented manually by configuring routing tables on routers.
Dynamic Routing:
- Utilizes algorithms to automatically adjust routing tables based on network conditions.
6. Data Link Layer:
Organizes data into frames and manages access to the physical transmission medium.
Example: Transferring data between a computer and a printer.
Protocol: Ethernet for LAN communication, Wi-Fi for wireless LAN.
ARP (Address Resolution Protocol): The Address Resolution Protocol (ARP) is a communications protocol within the Internet Protocol suite. It's a request-response protocol used to resolve the media access control (MAC) address for a given IP address.
Framing: ARP is a protocol used to map IP addresses to MAC addresses on a local network.
Error Detection: It helps devices find the MAC address corresponding to an IP address within the same network segment.
7. Physical Layer:
Deals with the physical connection between devices, including transmission of raw data bits.
Example: Connecting a computer to a router via Ethernet cable.
Protocol: IEEE 802.3 for Ethernet, IEEE 802.11 for Wi-Fi.
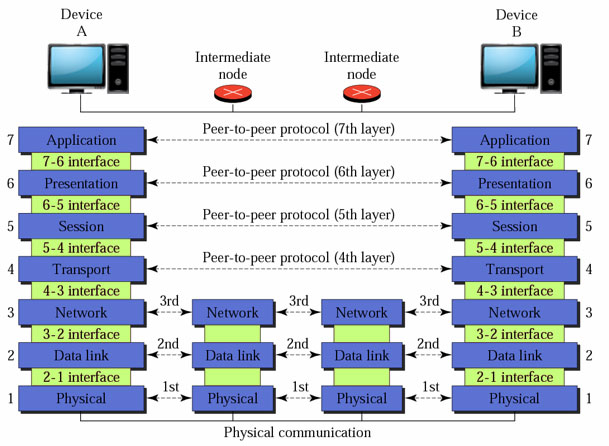
The OSI model is more theoratical approch or concept based.
TCP/IP Model(5 Layers):
Application Layer: Users interact with applications running on their devices.
Transport Layer: Ensures reliable data delivery between devices.
Internet Layer: Manages addressing and routing across networks.
Data Link Layer: Handles communication within a network segment.
Physical Layer: Deals with the physical transmission of data over the network medium.
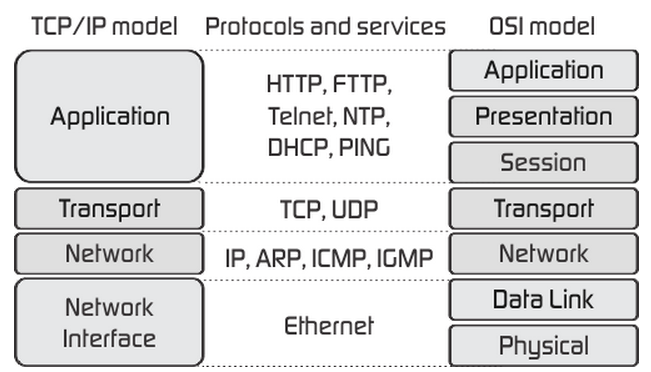
The TCP/IP Model is more practical approch
Peep-to-Peer Architecture:
Peer-to-peer (P2P) architecture distributes tasks or workloads among peers without the need for a central server, enabling decentralized communication and resource sharing.
Rapid Scalability:
- Allows for quick expansion as more participants join.
Decentralization:
- Operates without a central authority or server control.
Example: BitTorrent:
- Users share files directly, enabling efficient distribution without a central server.
Networking Devices:
Repeater:
A two-port device that repeats network signals without modifying data packets.
Regenerates data packets at original strength for devices located at a distance.
Bridge:
Divides network into segments and forwards data packets based on MAC addresses.
Reduces unnecessary traffic by filtering data between segments.
Hub:
A multiport repeater that connects multiple devices in a network.
Operates at the speed of the slowest device and sends copies of data packets to all devices.
Types of Hub:
Active Hub: Requires external power and regenerates signals.
Passive Hub: This does not require external power and does not regenerate signals.
Switch:
Combines bridge and hub functionalities, segmenting networks and filtering packet data.
Uses MAC addresses to direct data packets and operates in full-duplex mode.
Types of Ethernet Switch:
Unmanaged: No configuration capability, suitable for small-office/home-office environments.
Managed: Offers extensive configuration options via CLI or web interface, including QoS, VLANs, STP, port mirroring, etc.
Smart: Limited configuration options through a web-based interface, a midpoint between unmanaged and managed switches.
Enterprise: Fully managed switches with comprehensive configuration capabilities for enterprise networks.
Bridge:
- Connects multiple network segments, forwarding data packets based on MAC addresses.
Types of Bridge:
- Transparent Bridge, Source Route Bridge, and Translational Bridge.
Routers:
- Direct network traffic between different networks based on IP addresses.z
Gateway:
- Acts as an entry or exit point between networks, often performing protocol translation.
Brouter:
- Combines the functionalities of a bridge and a router, forwarding packets between networks based on both MAC and IP addresses.
Protocols:
Web Protocols:
TCP/IP: Suite of protocols governing internet communication.
HTTP: Hypertext Transfer Protocol for web browsing.
DHCP: Dynamic Host Configuration Protocol for automatic IP address assignment.
FTP: File Transfer Protocol for transferring files between computers.
SMTP: Simple Mail Transfer Protocol for sending email.
POP3 & IMAP: Post Office Protocol and Internet Message Access Protocol for email retrieval.
SSH (Secure Shell): Secure remote login and file transfer protocol.
VNC (Virtual Network Computing): Remote desktop access protocol.
Telnet (Terminal Emulation): Protocol for remote access to command-line interfaces, typically on port 23.
UDP (User Datagram Protocol): Connectionless protocol for data transmission without error checking or correction.
Sockets:
Software endpoints facilitate communication between processes over a network.
They enable data exchange between applications running on different devices.
Let's Understand with example:
Two computers running chat applications establish a socket connection.
This connection allows the applications to send and receive messages in real time.
Ports:
Ports identify which application we're using with a 16-bit number.
There are about 65,000 port numbers available.
Common ports include HTTP (80), MongoDB (27017), and SQL (1433).
Ports 0-1023 are reserved, while 1024-19152 are typically used for applications.
Ephemeral ports are dynamic and used to differentiate between instances or processes within an application.
They exist on the client side and must be known on the server side for data routing.
1 kbps (kilobit per second) = 1,000 bits/s
1 Mbps (megabit per second) = 1,000,000 bits/s
1 Gbps (gigabit per second) = 1,000,000,000 bits/s
The following table lists some of the more common well-known port numbers.
| Port number | Assignment |
| 20 | File Transfer Protocol for data transfer |
| 21 | File Transfer Protocol for command control |
| 22 | Secure Shell for secure authentication |
| 23 | Telnet remote authentication service for unencrypted text messages |
| 25 | Simple Mail Transfer Protocol for email routing |
| 53 | Domain Name System service |
| 80 | Hypertext Transfer Protocol for use in the web |
| 110 | Post Office Protocol |
| 119 | Network News Transfer Protocol (NNTP) |
| 123 | Network Time Protocol (NTP) |
| 143 | Internet Message Access Protocol for management of digital mail |
| 161 | Simple Network Management Protocol |
| 194 | Internet Relay Chat (IRC) |
| 443 | HTTP Secure HTTP over TLS/SSL |
HTTP (Hypertext transfer protocol):
HTTP( Application layer ) used TCP ( transport layer )
Stateless protocol, the server did not store any information about the client by default.
HTTP Methods(GET, POST ,PUT ,DELETE):
- What is a method: A method is something that tells the server what to do.
GET:
You are requesting some data.
Example: Retrieve information from a website by entering its URL in a browser's address bar.
POST:
Like I'm a client and I'm giving something to the server, like when you register somewhere, username, password, etc.
Example: Submitting a form with user information to create a new account on a website.
PUT/PATCH:
Put the data at a specific location.
Patch usually is for partial updates.
Example: Updating a specific user's profile information on a website.
DELETE:
When you want to delete any data.
Example: Removing a post or comment from a social media platform.
Error/Status Codes:
100: Informational codes
200: Success codes
300: redirecting
400: client error
500: server error
Response status codes
The HTTP 200 OK success status response code indicates that the request has succeeded
Status codes have conventions. For example, any status code starting with a "2xx" (a "200-level response") represents a successful call. Get familiar with other status code categories:
| Code range | Meaning | Example |
| 2xx | Success | 200 - OK201 - Created204 - No content (silent OK) |
| 3xx | Redirection | 301 - Moved (path changed) |
| 4xx | Client error | 400 - Bad request401 - Unauthorized403 - Not Permitted404 - Not Found |
| 5xx | Server error | 500 - Internal server error502 - Bad gateway504 - Gateway timeout |
Cookies:
Unique string
Stored in browser
Small data pieces
Used for session management, personalization, and tracking
Maintain user sessions and preferences
Track user behavior
Third-Party Cookies
Cookies set by domains other than the one the user is currently visiting
Often used for tracking and advertising purposes
Enable cross-site tracking
Can be used by advertisers to gather information about user browsing habits
Controversial due to privacy concerns
Subject to regulation and browser restrictions
Cache:
Temporary storage location
Used to store frequently accessed data
Improves website performance by reducing load times
Can be browser cache or server cache
Stores copies of web pages, images, and other resources
Helps minimize server load and network traffic
How does email work?
Email works by composing messages in an email client, which are then sent to an outgoing mail server using SMTP. The recipient's mail server receives the email and stores it until the recipient's email client retrieves it using POP3 or IMAP. The recipient accesses the email through their email client or webmail interface for reading, replying, and managing messages.
Email operates through a series of protocols and standards to facilitate communication and message retrieval:
SMTP (Simple Mail Transfer Protocol): This protocol is employed to send emails over the Internet. It operates on top of the TCP (Transmission Control Protocol) to ensure reliable data delivery.
POP3 (Post Office Protocol, Port No. 110): Used for retrieving emails from a mail server to a client device. POP3 allows users to download their emails to their local devices for offline access.
IMAP (Internet Message Access Protocol): Unlike POP3, IMAP permits users to access their emails from multiple devices while keeping them synchronized with the server. This protocol allows for managing emails across various devices without the need to download them locally.
-type=mx gmail.com
DNS (Domain Name System):
So basically when you enter google.com it’ll use DNS to find the IP address of Google’s server.
You can't buy a domain name but you can rent it. For example, you rent the .org domain name which top-level domain name to GoDaddy for example and then you have to pay GoDaddy and GoDaddy will pay the Internet Corporation for Assigned Names and Numbers (ICANN)
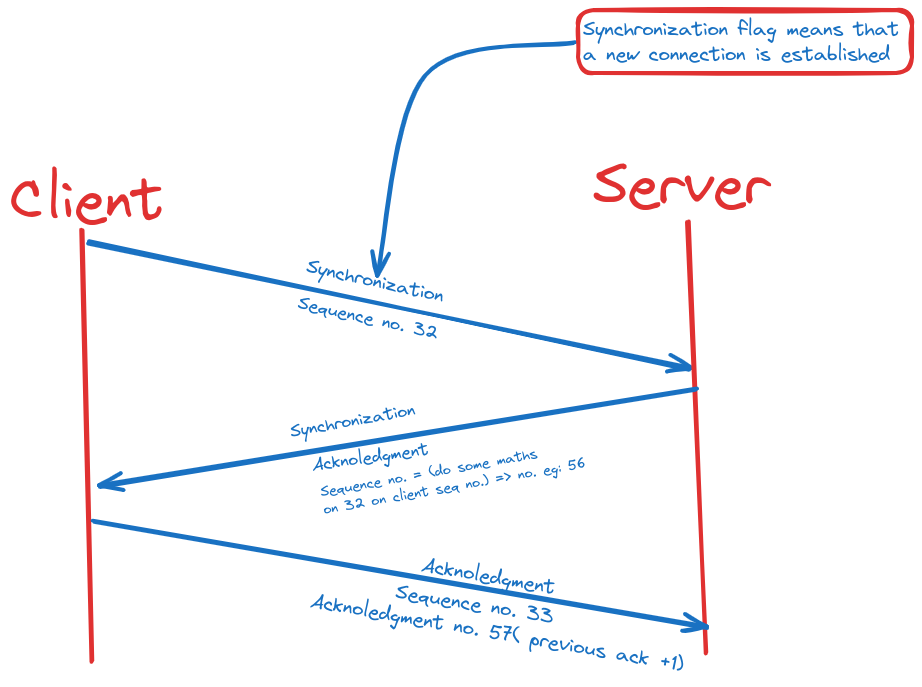
3-Way Handshake:
Initiation (First handshake):
The client sends a synchronization (SYN) packet to the server, indicating its intent to establish a connection and specifying initial sequence numbers.
This packet contains TCP header flags indicating the SYN flag is set, along with other connection-related information.
Agreement (Second handshake):
Upon receiving the SYN packet, the server responds with a SYN-ACK packet.
The server acknowledges the client's SYN packet (SYN-ACK), indicating its readiness to establish the connection.
The SYN-ACK packet contains its own initial sequence number, as well as TCP header flags indicating both the SYN and ACK flags are set.
Communication (Third handshake):
Finally, the client sends an acknowledgment (ACK) packet to the server.
This packet acknowledges the server's SYN-ACK packet and confirms the connection establishment.
The ACK packet contains an incremented acknowledgment number, confirming receipt of the server's SYN-ACK packet.
Established Connection:
With the three-way handshake completed, a reliable, bidirectional communication channel is established between the client and server.
Subsequent data exchange can occur over this established connection, with both parties synchronized and ready to transmit and receive data packets.
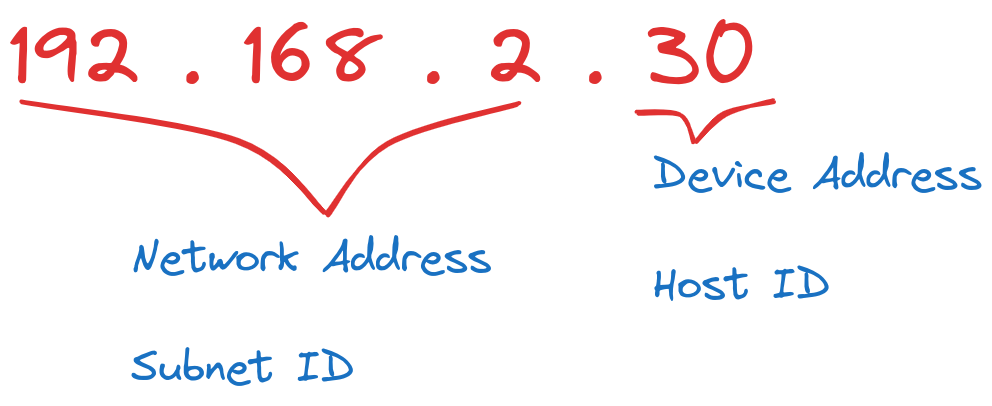
IP ( Internet Protocol ) Address:
IP addresses tell us which device we are working with.
IP addresses uniquely identify devices connected to a network.
They consist of a series of numbers separated by dots, like 192.168.2.30
Each device, such as a computer or smartphone, has its own IP address.
IP addresses help devices communicate with each other over the internet.
They play a crucial role in directing data packets to their intended destinations.
curl ifconfig.me -s
The command curl ifconfig.me -s is used to retrieve your public IP address from the ifconfig.me service using the cURL command-line tool. The -s flag is used to suppress the progress meter and other unnecessary output.
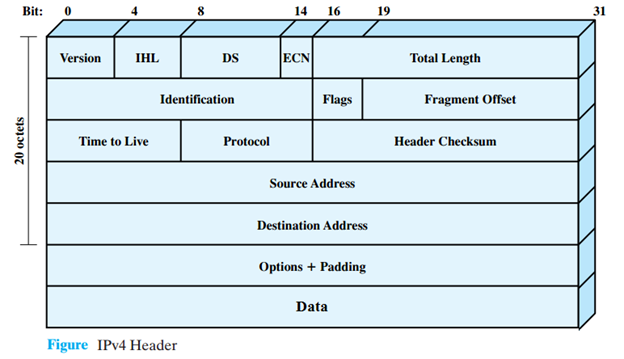
IPv4:
32-bit address space, expressed in four decimal numbers.
Limited to approximately 4.3 billion unique addresses.
Uses NAT for address conservation.
Limited support for security features.
An example of an IPv4 address is: 192.168.0.1
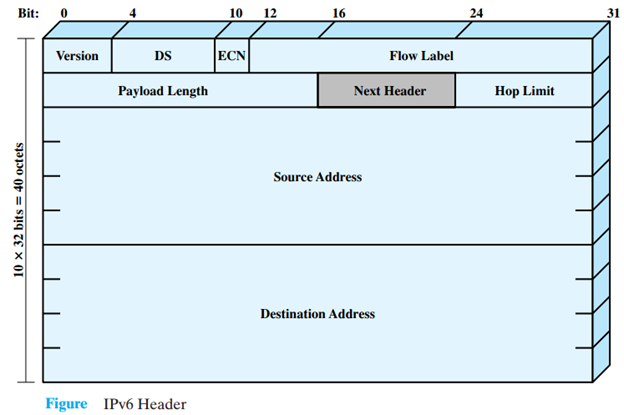
IPv6:
128-bit address space, expressed in hexadecimal notation.
Offers an extremely large number of unique addresses.
Simplifies address assignment and configuration.
Supports built-in security features like IPsec.
Facilitates efficient routing and packet processing.
Transition mechanisms ensure compatibility during the transition from IPv4.
An example of an IPv6 address is: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
IPv4 Vs IPv6
| Feature | IPv4 | IPv6 |
| Address Space | 32-bit, limited (approx. 4.3 billion) | 128-bit, vast (approx. 3.4 x 10^38) |
| Address Format | Decimal (e.g., 192.168.1.1) | Hexadecimal (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334) |
| Address Configuration | Manual or DHCP | Stateless Address Autoconfiguration (SLAAC) |
| Security Features | Limited | Built-in support for IPsec |
| Routing Efficiency | Less efficient | More efficient due to simplified headers |
| Transition Mechanisms | Requires transition mechanisms | Transition mechanisms for coexistence |
Classes of IP Addresses:
Classification system dividing IP addresses into Class A, B, C, D, and E based on their leading bits, determining network size and address allocation.
Class A:
First bit is always fixed to 0.
Allows for a very large number of hosts (over 16 million).
Primarily used by large organizations or internet service providers.
Class B:
First two bits are fixed to 10.
Suitable for medium-sized networks with moderate numbers of hosts (up to 65,534).
Provides a balance between network and host addresses.
Class C:
First three bits are fixed to 110.
Designed for small networks with a limited number of hosts (up to 254).
Commonly used for small businesses or home networks.
Class D:
First four bits are fixed to 1110.
Reserved for multicast addressing, used for one-to-many communication.
Not used for traditional unicast communication between hosts.
Class E:
First four bits are fixed to 1111.
Reserved for experimental or research purposes.
Not intended for general use in production networks.
What is a subnet?
A subnet defines one or more logical networks within the class A, B, or C network. Without subnets, you're restricted to a single network in each of the class A, B, or C networks.
Middle Boxes:
A middlebox is a network device or appliance that provides specific services such as firewalling or NAT (Network Address Translation) between different network segments.
Firewall:
Monitors and controls network traffic based on security rules.
Acts as a barrier between trusted internal and untrusted external networks.
Can be hardware or software-based, analyzing data packets to determine passage.
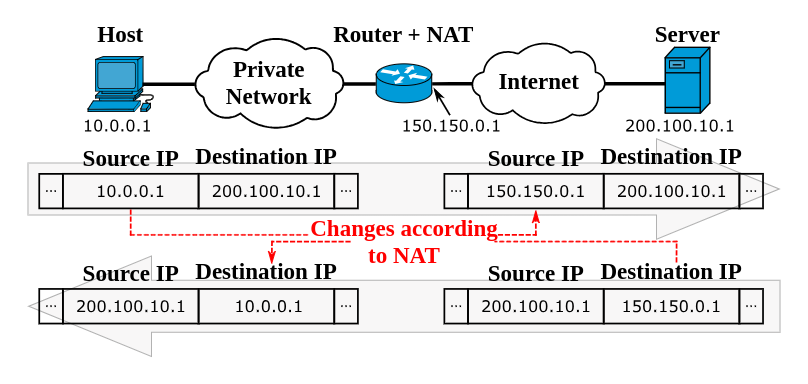
NAT (Network Address Translation):
Modifies network address information in packet headers.
Allows multiple devices to share a single public IP address.
Translates private IP addresses to a single public IP address, facilitating communication between local devices and the internet.
MAC Addresses:
The media access control (MAC) address is a unique identifier assigned to every network-enabled device at the time of manufacture. It's sometimes referred to as the burned-in address, the Ethernet hardware address, or a physical address.
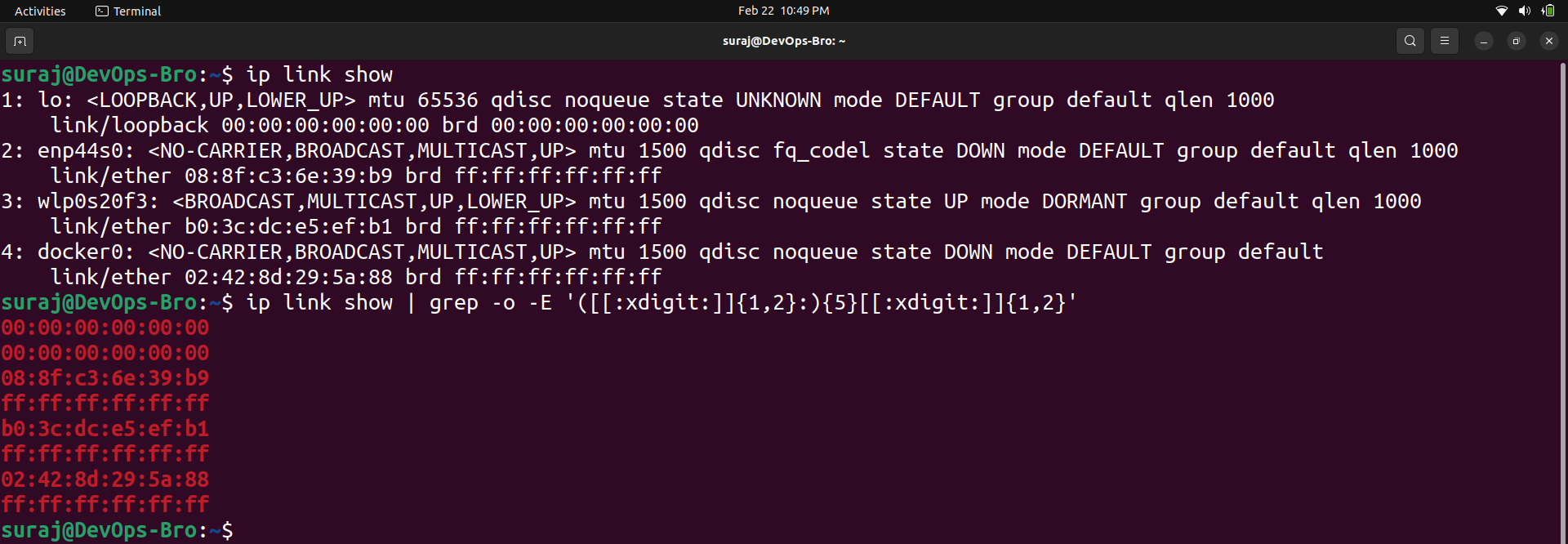
The MAC address has a standard composition of six hexadecimal numbers separated by a colon or dash. The first three numbers of the MAC address define the manufacturer's organizationally unique identifier (OUI), and the remaining three numbers uniquely identify the device. For example, if the MAC address is ff:ff:ff:ff:ff:ff then the OUI is ff:ff:ff and ff:ff:ff is the device ID.
VPN tunneling
VPN tunneling is the process of encrypting data packets sent over a public network, creating a secure "tunnel" between the user's device and the VPN server.
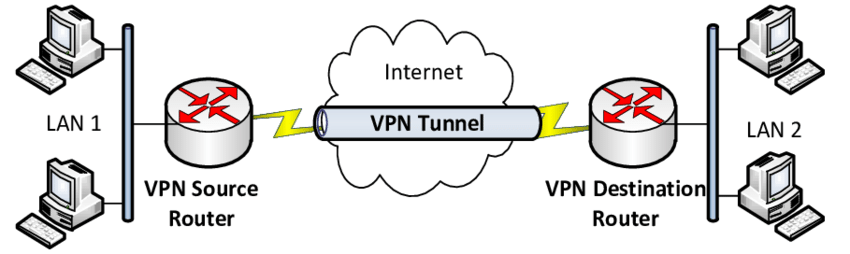
VPN tunneling encrypts data packets for secure transmission over a public network.
It establishes a virtual encrypted connection between the user's device and the VPN server.
This process ensures data confidentiality, integrity, and privacy.
Example: User data is encrypted at their device, transmitted securely to the VPN server through an encrypted tunnel, decrypted at the server, and then forwarded to the intended destination.
TLS and SSL
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols.
They provide secure communication over a network by encrypting data transmitted between clients and servers.
TLS is the successor of SSL and offers improved security features.
Example: TLS/SSL encrypts data exchanged between a web browser (client) and a web server, ensuring confidentiality and integrity of information such as login credentials or financial transactions.
Ofcourse this blog does not consists all about computer networking and if you want to learn more reger this structure learning path by microsoft learn.
Subscribe to my newsletter
Read articles from Suraj directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suraj
Suraj
I'm a Developer from India with a passion for DevOps ♾️ and open-source 🧑🏻💻. I'm always striving for the best code quality and seamless workflows. Currently, I'm exploring AI/ML and blockchain technologies. Alongside coding, I write Technical blogs at Hashnode, Dev.to & Medium 📝. In my free time, I love traveling, reading books