Day4: OWASP Top Ten Vulnerabilities
 Suresh Kumar S
Suresh Kumar S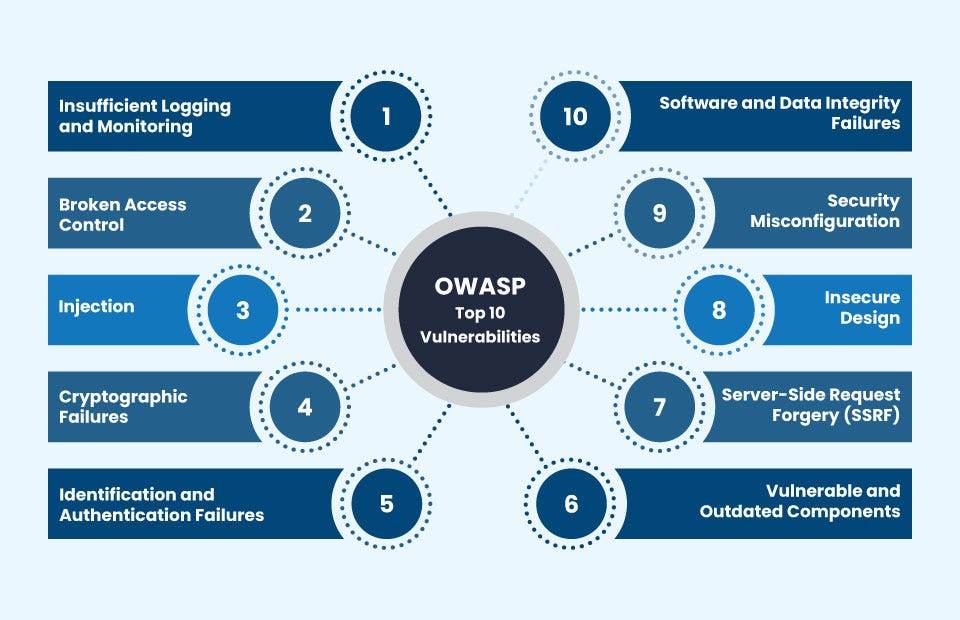
Introduction: In today's interconnected world, web applications are integral to businesses, providing essential services and interactions with users. However, this increased connectivity also brings heightened security risks. The Open Web Application Security Project (OWASP) identifies and ranks the top ten most critical web application security risks, offering guidance on how to mitigate these vulnerabilities effectively. In this blog post, we'll explore each of these OWASP Top Ten vulnerabilities and discuss best practices for securing your web applications.
Injection: Injection flaws, such as SQL injection or NoSQL injection, occur when untrusted data is sent to an interpreter as part of a command or query. Attackers exploit these vulnerabilities to execute arbitrary code or access unauthorized data. Mitigate this risk by using parameterized queries, input validation, and ORM frameworks that handle input sanitization.
Broken Authentication: Weak authentication mechanisms, such as ineffective password management or session management, can lead to unauthorized access to user accounts. Enforce strong password policies, implement multi-factor authentication, and use secure session management techniques to mitigate this risk.
Sensitive Data Exposure: Failure to adequately protect sensitive data, such as passwords or credit card numbers, can result in data breaches and compromise user privacy. Encrypt sensitive data both at rest and in transit, avoid storing unnecessary data, and regularly audit access controls to prevent unauthorized access.
XML External Entities (XXE): XML processors that parse external entities without proper validation can be exploited to read sensitive files or execute remote code. Prevent XXE attacks by disabling external entity processing, using safe XML parsing libraries, and implementing input validation.
Broken Access Control: Inadequate access control mechanisms allow unauthorized users to access privileged functionalities or sensitive data. Follow the least privilege principle, enforce access controls at both the server and client sides, and regularly review access control policies to prevent unauthorized actions.
Security Misconfiguration: Improperly configured security settings expose web applications to various security risks. Follow secure configuration guides, disable unnecessary services, and regularly audit systems for security misconfigurations.
Cross-Site Scripting (XSS): XSS vulnerabilities enable attackers to inject malicious scripts into web pages, leading to data theft or website defacement. Encode user input, use content security policy (CSP), and conduct regular code audits to identify and remediate XSS vulnerabilities.
Insecure Deserialization: Insecure deserialization vulnerabilities can be exploited to execute arbitrary code or tamper with application logic. Use secure serialization formats, implement integrity checks, and restrict deserialization to minimize this risk.
Using Components with Known Vulnerabilities: Failure to update third-party components exposes web applications to known security vulnerabilities. Monitor security advisories, establish a patch management process, and use dependency checkers to identify and remediate vulnerable components.
Insufficient Logging and Monitoring: Inadequate logging and monitoring capabilities hinder the detection and response to security incidents. Implement comprehensive logging, use centralized logging solutions, and establish incident response procedures to mitigate this risk effectively.
Conclusion: By understanding and addressing the OWASP Top Ten vulnerabilities, organizations can enhance the security of their web applications and protect sensitive data from unauthorized access and exploitation. By implementing robust security measures, staying vigilant against emerging threats, and fostering a culture of security awareness, businesses can mitigate risks and build trust with their users in an increasingly interconnected digital landscape.
🔔 Stay updated with the latest tech tutorials and insights! Follow my blog:
🔔 Let's expand our professional network on LinkedIn! Connect with me here:
linkedin.com/in/suresh-kumar-s-profile
However, if you have any more questions or need assistance with anything else, feel free to ask!
~ Suresh Kumar
Subscribe to my newsletter
Read articles from Suresh Kumar S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suresh Kumar S
Suresh Kumar S
Experienced AWS DevOps Engineer with 9+ years in IT, specializing in AWS for over 5 years. Holder of 5 AWS certifications, adept at optimizing infrastructure and driving efficiency.