Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
Lab Scenario: Our objective is to understand and exploit a SQL injection vulnerability in the WHERE clause of a web application's stock check feature. By carefully probing and bypassing security measures, we aim to retrieve hidden data and ultimately solve the lab. Let's embark on this journey using Burp Suite:
Identifying the Vulnerability:
Observe that the stock check feature sends the
productIdandstoreIdto the application in XML format.Send the
POST /product/stockrequest to Burp Repeater.
Probing for Injection Points:
In Burp Repeater, probe the
storeIdto see if your input is evaluated. Try replacing the ID with mathematical expressions to evaluate other potential IDs:xmlCopy code<storeId>1+1</storeId>Observe that your input appears to be evaluated, returning stock information for different stores.
Bypassing the Web Application Firewall (WAF):
Attempt to determine the number of columns returned by the original query using a UNION SELECT statement. Note that your request may be blocked.
xmlCopy code<storeId>1 UNION SELECT NULL</storeId>Bypass the WAF by obfuscating your payload using XML entities. Utilize tools like Hackvertor extension to encode entities.
Resend the request and confirm that you receive a normal response, indicating successful WAF bypass.
Crafting the Exploit:
Deduce that the query returns a single column. Attempting to return more than one column results in an error.
Concatenate the returned usernames and passwords using SQL injection:
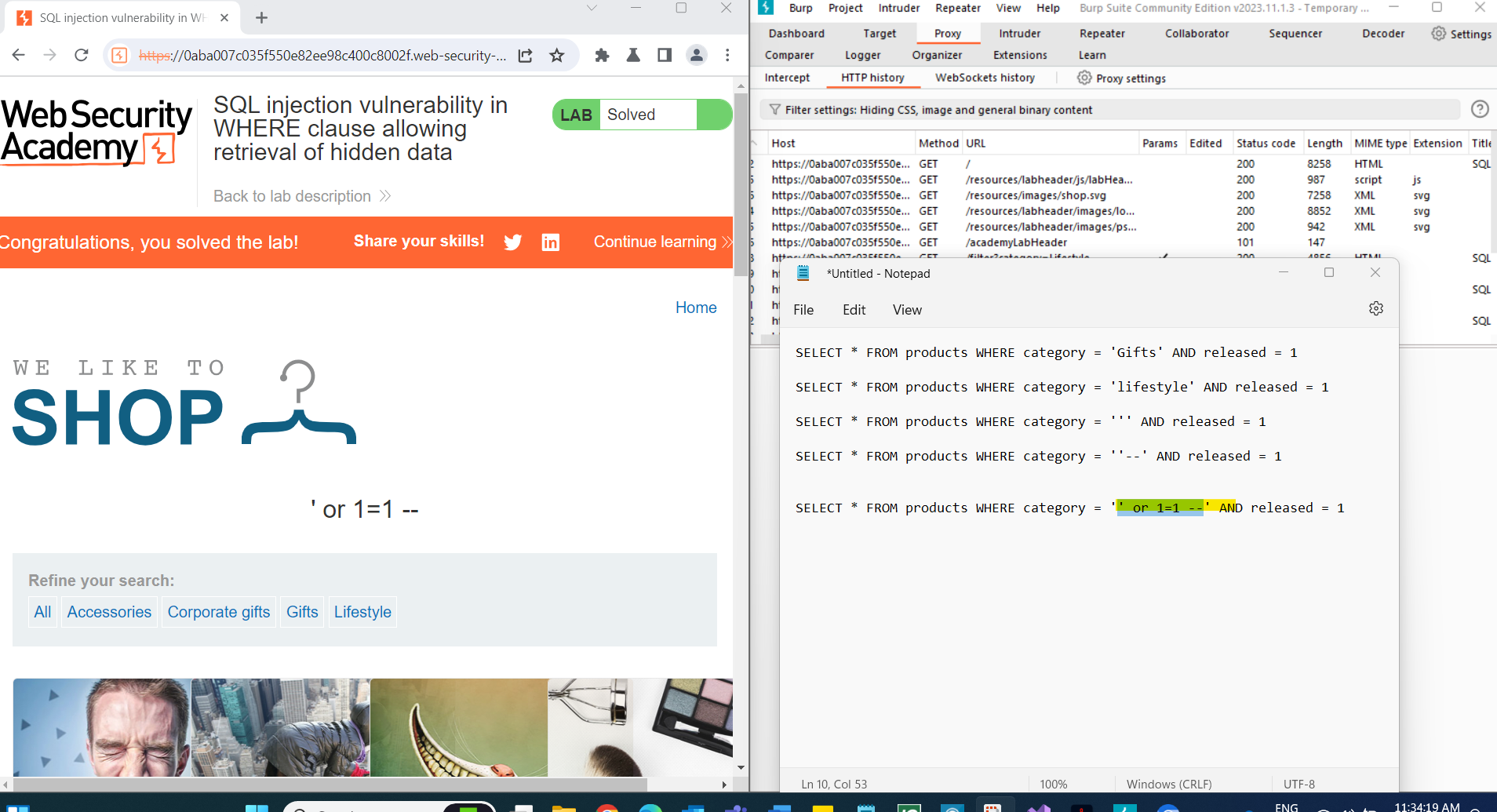
xmlCopy code<storeId><@hex_entities>1 UNION SELECT username || '~' || password FROM users<@/hex_entities></storeId>Observe that you've successfully fetched usernames and passwords from the database, separated by a ~ character.
Solving the Lab:
- Use the administrator's credentials obtained from the exploit to log in and solve the lab.
Conclusion
This hands-on lab provides practical insights into exploiting SQL injection vulnerabilities in the WHERE clause, showcasing the potential risks associated with inadequate security measures. By following this step-by-step guide, users can enhance their skills in identifying, exploiting, and mitigating SQL injection flaws. Stay informed, keep learning, and continue exploring the dynamic field of cybersecurity to contribute to a more secure online environment.
Reference:
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.