What is Hacking?
 Aniket Nayan Verma
Aniket Nayan Verma
In the realm of cybersecurity, hacking refers to the deliberate and unauthorized manipulation of digital devices, networks, and systems. Let’s delve into the details:
Definition of Hacking:
Hacking involves compromising digital systems through unauthorized access to accounts or computer networks.
While hacking isn’t always malicious, it is most commonly associated with illegal activities and data theft by cybercriminals.
In the context of cybersecurity, hacking encompasses various actions:
Causing damage to or corrupting systems.
Gathering information on users.
Stealing data and documents.
Disrupting data-related activity.
Evolution and Sophistication:
The traditional image of a hacker as a lone rogue programmer is outdated.
Modern hackers are highly skilled and sophisticated:
They use stealthy attack methods that evade detection by cybersecurity software and IT teams.
Social engineering techniques trick users into revealing sensitive personal data.
Hacking has become a multibillion-dollar industry with successful and intricate methods.
History of Hacking:

The term “hacking” emerged in the 1970s but gained prominence in the following decade.
Movies like “Tron” and “WarGames” introduced hacking to a wider audience, portraying characters breaking into computer systems.
High-profile attacks on organizations followed, leading to the negative connotation associated with hackers.
Types of Hacking:
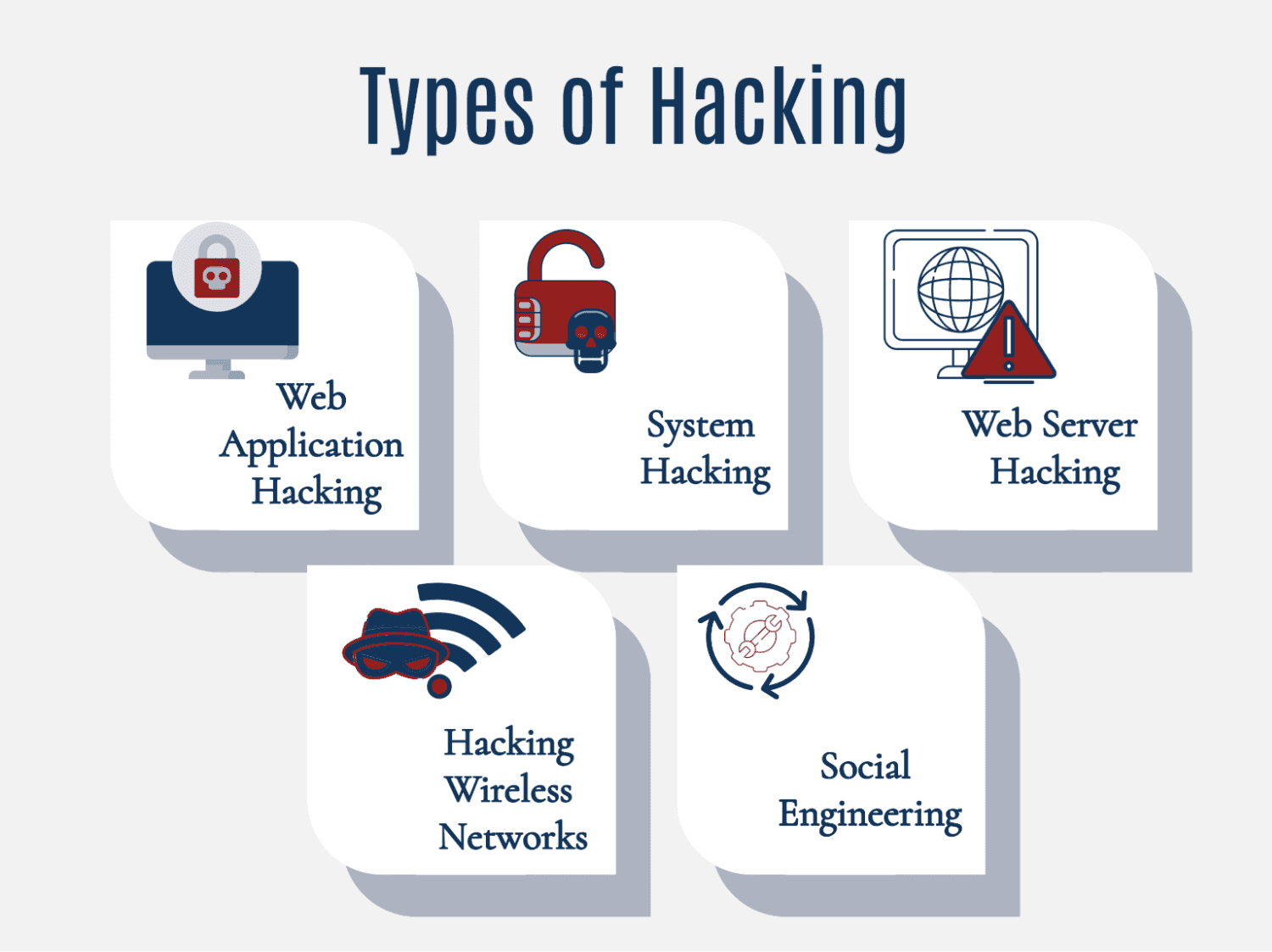
Phishing Attacks:
Phishing involves tricking users into revealing sensitive information (such as login credentials or credit card details) by posing as a trustworthy entity.
Attackers send deceptive emails, messages, or create fake websites to lure victims.
Malware Attacks:
Malware refers to malicious software designed to harm systems or steal data.
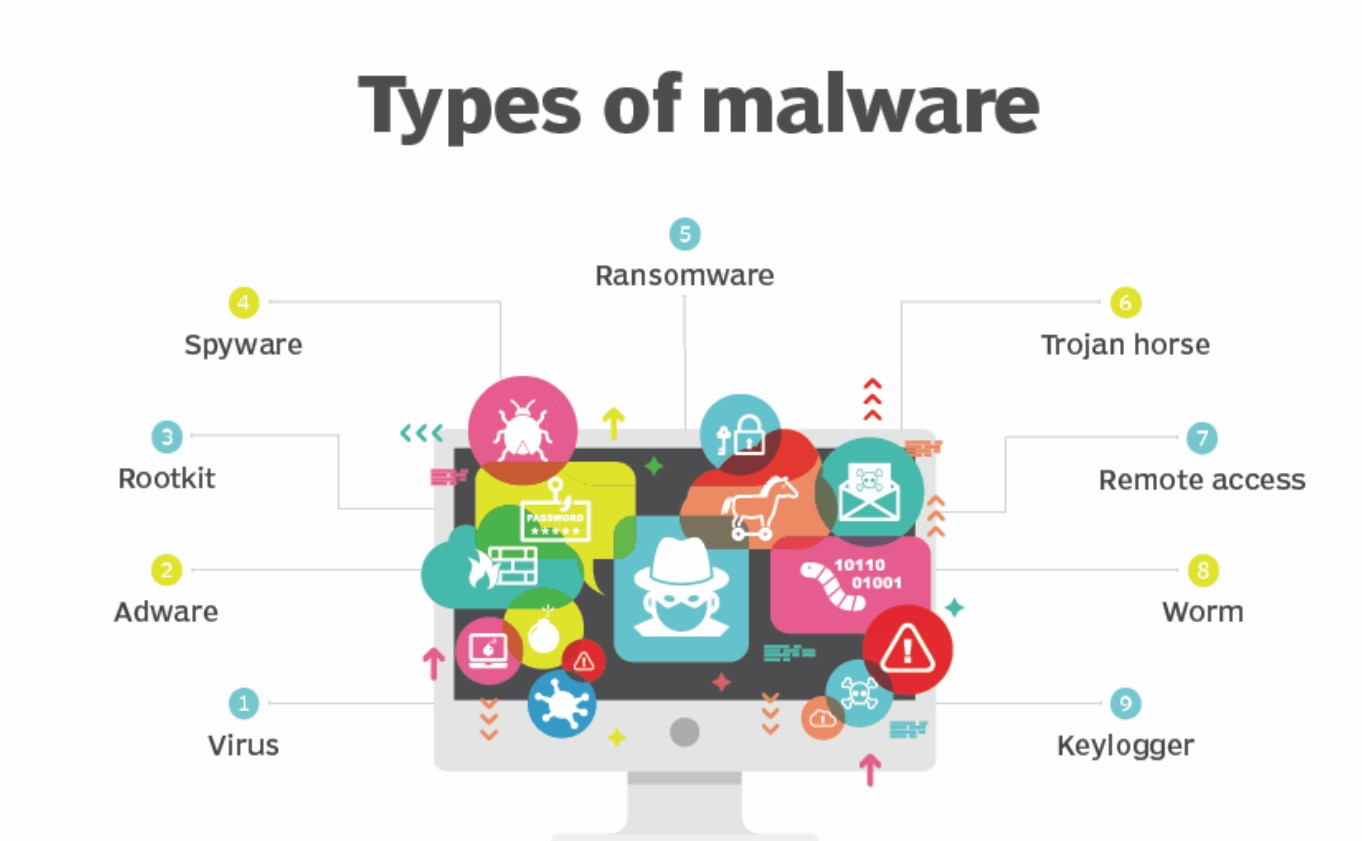
Types of malware include:
Viruses: Self-replicating programs that attach to legitimate files.
Trojans: Disguised as legitimate software but perform harmful actions.
Ransomware: Encrypts files and demands payment for decryption.
Worms: Self-propagating programs that spread across networks.
SQL Injection:
Exploiting vulnerabilities in web applications by injecting malicious SQL queries.
Attackers gain unauthorized access to databases.

Cross-Site Scripting (XSS):
Injecting malicious scripts into web pages viewed by other users.
Can lead to data theft or session hijacking.
Distributed Denial of Service (DDoS):
Overwhelming a server or network with excessive traffic.
Renders the service unavailable to legitimate users.
Social Engineering:
Manipulating human psychology to gain unauthorized access.
Techniques include impersonation, pretexting, and tailgating.
Zero-Day Exploits:
Targeting vulnerabilities in software before they are patched.
Attackers exploit flaws unknown to developers.
Wireless Hacking:
Attacking Wi-Fi networks or Bluetooth devices.
Examples include cracking Wi-Fi passwords or intercepting Bluetooth communication.
Insider Threats:
Malicious actions by employees, contractors, or business partners.
Can involve data theft, sabotage, or unauthorized access.
Ethical Hacking (White Hat):
Authorized hacking to identify and fix vulnerabilities.
Ethical hackers help organizations secure their systems.
Subscribe to my newsletter
Read articles from Aniket Nayan Verma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

