Multi-Cloud Red Team Analyst (MCRTA) Review
 Abhijeet Kumar
Abhijeet Kumar
Disclaimer
At the time of writing this blog, I am employed by the CyberWarFare Labs (the creator of this course), however, the thoughts and experiences shared are my own and does not reflect those of my employer.
Overview
Although cloud has been here for a very long time, since the past decade or so, the usage of cloud services (SaaS. PaaS, IaaS, etc) has seen an exponential spike in terms of adoption by the MNCs as well as SMEs. This essentially means a lot of opportunities for individuals to dive into the world of cloud technologies and learn new skills. CyberWarFare Lab's latest course Multi-Cloud Red Team Analyst [MCRTA], is created for such individuals who are interested in hacking & securing the cloud services and ready to take the first step. Furthermore, no prior cloud knowledge is required for taking this course as TTPs (Tactics, Techniques, and Procedures) are taught from the very grounds up. That said, I would recommend some prior experience with command-line interfaces (Bash, Command Prompt, PowerShell) along with the zeal to learn.
Course Architecture
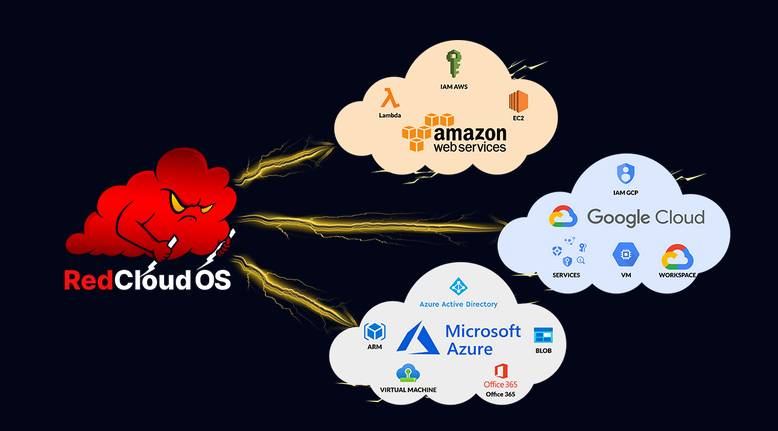
MCRTA features a multi-cloud lab setup which spans across three major Cloud Service Providers (CSPs), i.e, AWS, Azure, and GCP. This journey starts from the external recon of a fictional organization with OSINT and ends with accessing sensitive information from inside the cloud infrastructure. The lab has fun challenges which are interesting to research and boost one’s knowledge.
Course Highlights
Introduction to Multi-Cloud (AWS, Azure, and GCP) Red Teaming
Multi-Cloud Architecture & Authentication Mechanisms
Exploiting Multi-Cloud Mis-configurations
Red Team Ops in Multi-Cloud Environment
Red Teaming in AWS
AWS Core Services Enumeration
CLI Authentication & Configuration
Abuse mis-configured EC2, S3 & IAM ACLs
Exploit Vulnerable Apps hosted in Cloud
Practically perform Red Team Ops in AWS Cloud
Red Teaming in Azure
Understand Entra ID(aka Azure AD), O365, ARM
CLI & Powershell based authentication
Exploit Vulnerable Apps hosted in Cloud
Abuse mis-configured Entra ID, VMs etc
Practically perform Red Team Ops in Azure Cloud
Red Teaming in GCP
Understand Google Workspace & GCP Architecture
CLI Authentication & Configuration
Enumerate mis-configured GCP Storage, VMs etc
Exploit Vulnerable Apps hosted in Cloud
Practically perform Red Team Ops in GCP
My Experience
MCRTA turned out to be top-notch with the content broken down in neat chunks. I really like how concepts are explained in a beginner-friendly manner with focus on practical usability. Before taking the course, I had some prior experience with cloud security (mostly defensive side) as a side effect of securing my own cloud infrastructure (homelab + personal projects). Having said that, the course proved to be an excellent intro to red teaming in the cloud environments and taught me cool new tricks which am pretty eager to replicate in my own environment. Similarly, the process for earning the associated certification has quite interesting challenges (OSINT + enumeration) spread across 3 CSPs (10 challenges each). I took a quick jab at some of the challenges and managed to accquire few flags (hoping to finish the remaining ones coming weekend) with some OSINT.
Apart from the course itself, another fun part for me was the research where I spent quite some time reading through the CSP documentations and blogs in order to better understand the internal workings of the cloud services. For people taking MCRTA/serious about learning cloud security, I strongly recommend going through the CSP documentations. While the documentations might seem like bit too much at first glance, having the knowledge and proper understanding will surely go a long way towards building solid skill-sets in the cloud security (be it offensive/defensive).
That's it for this review, next I'll be sharing the review of a course sitting in my course backlog for almost 2 years.
Subscribe to my newsletter
Read articles from Abhijeet Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
