OAuth2 and OpenID Connect with WSO2 IS - Part 14
 Nipuna Upeksha
Nipuna Upeksha
🧬 Introduction
We have already discussed how you can gain access via the Authorization Code Grant flow. In this article, we will look at an extension of that, how to use Authorization Code Grant flow with PKCE.
PKCE is an acronym for Proof Key for Code Exchange. It is there to ensure more security for Authorization Code Grant Type for advanced use cases. Those who know the flow of the Authorization Code Grant type know that the first call(authorization request) is made through a browser(user-agent) to obtain the Authorization Code. This makes the Authorization Code susceptible to Authorization Code Interception Attacks*.* The idea behind PKCE is proof of possession. The client application should provide proof to the Authorization Server that the Authorization Code belongs to the Client application for the Authorization Server to issue an Access Token.
PKCE introduces a few new things to the Authorization Code Grant flow, a code verifier, a code challenge, and a code challenge method.
Code Verifier
↳ A random code that meets the requirements.
Code Challenge
↳ A transformation of the code verifier.
Code Challenge Method
↳ An optional method used to transform the code verifier into the code challenge. If you don't use it the Authorization Server will assume the code challenge and the code verifier are the same.
Now let's check how you can use the PKCE with Authorization Code Grant flow in WSO2 IS.
🧪 Testing PKCE with Authorization Code Grant Flow in WSO2 IS
First, you need to create a Service Provider(SP) in WSO2 IS and use the Apache-Tomcat server to configure it. We have discussed how to create Service Providers thoroughly in this series, so I am not going to repeat the same. You can check the series to learn how to create SPs in WSO2 IS. After creating the SP, make sure to check on the following checkboxes.
PKCE Mandatory
Support PKCE "Plain" Transform Algorithm
↳ This enables the Code Challenge Method as plain and supports the S256 algorithm by default.

Next, generate a Code Verifier and Code Challenge using this online tool, https://tonyxu-io.github.io/pkce-generator/
Make sure to store them and the Client ID and Client Secret of your application for future reference. In my case,
Client ID
↳
provided_client_id0001Client Secret
↳
provided_client_secret0001Code Challenge
↳
_YIAvfU2J2CZXjvV2ksYkvvXMZKskBEAjp5po37KKgQCode Verifier
↳
hdcbbxygd39fajdfdh45dvs37sjdgdskbslkdguskm4sdfcvvcgsffg355ddgdf2
Now, you can paste the following URL in the browser to get the Authorization Code.
URL format
↳
https://<IS_HOST>:<IS_PORT>/oauth2/authorize?scope=openid&response_type=code &redirect_uri=<REDIRECT_URI>&client_id=<CLIENT_ID>&code_challenge=<PKCE_CODE_CHALLENGE> &code_challenge_method=<PKCE_CODE_CHALLENGE_METHOD>Sample URL
↳
https://localhost:9443/oauth2/authorize?scope=openid&response_type=code&redirect_uri=http://localhost:8080/playground2/oauth2client&client_id=provided_client_id0001&code_challenge=_YIAvfU2J2CZXjvV2ksYkvvXMZKskBEAjp5po37KKgQ&code_challenge_method=S256
After typing the above URL, you will be prompted to authenticate. Provide the default username(admin) and password(admin) for that.
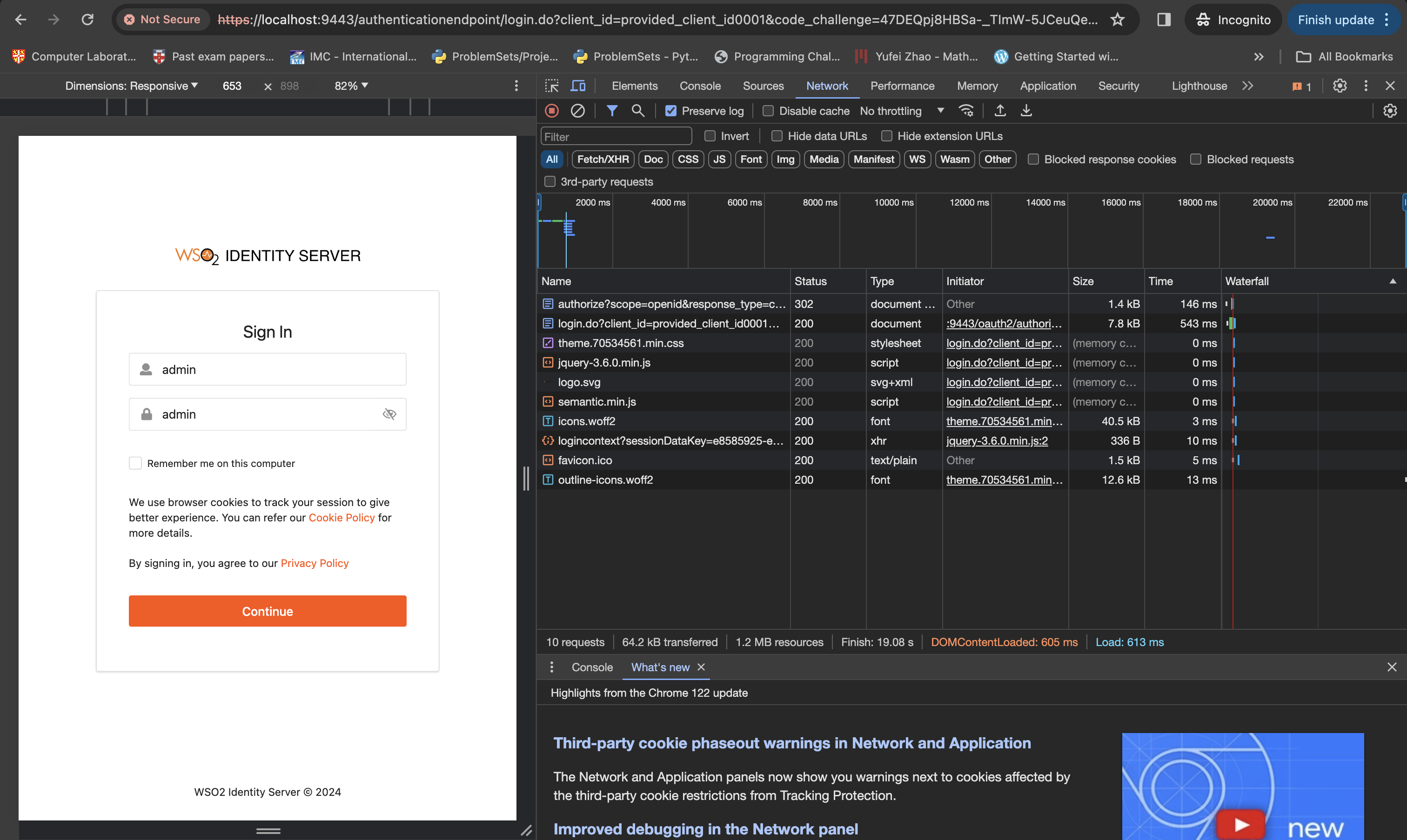
After that, you will get the Authorization Code with the query parameter code. It will be something like this.
http://localhost:8080/playground2/oauth2client?code=92594593-cc9a-3b55-bf1b-1f1e551777f5&session_state=bc1da3e9742680bd951abb669d8a30e72a0f3e4c9e978087562e56ecbf1fe0ab.zuoRyKMbq33PcCztN0IwgQ
Then you can use the following cURL command to get an Access Token.
cURL format
↳
curl -k --user "<CLIENT_ID>:<CLIENT_SECRET>" -d "code=<AUTH_CODE>&grant_type=authorization_code&client_id=<CLIENT_ID>&redirect_uri=<REDIRECT_URI>&code_verifier=<CODE_VERIFIER>" https://localhost:9443/oauth2/tokenSample cURL
↳
curl -k --user "provided_client_id0001:provided_client_secret0001" -d "code=92594593-cc9a-3b55-bf1b-1f1e551777f5&grant_type=authorization_code&client_id=provided_client_id0001&redirect_uri=http://localhost:8080/playground2/oauth2client&code_verifier=hdcbbxygd39fajdfdh45dvs37sjdgdskbslkdguskm4sdfcvvcgsffg355ddgdf2" https://localhost:9443/oauth2/token
After that, you will get an Access Token and an ID Token.
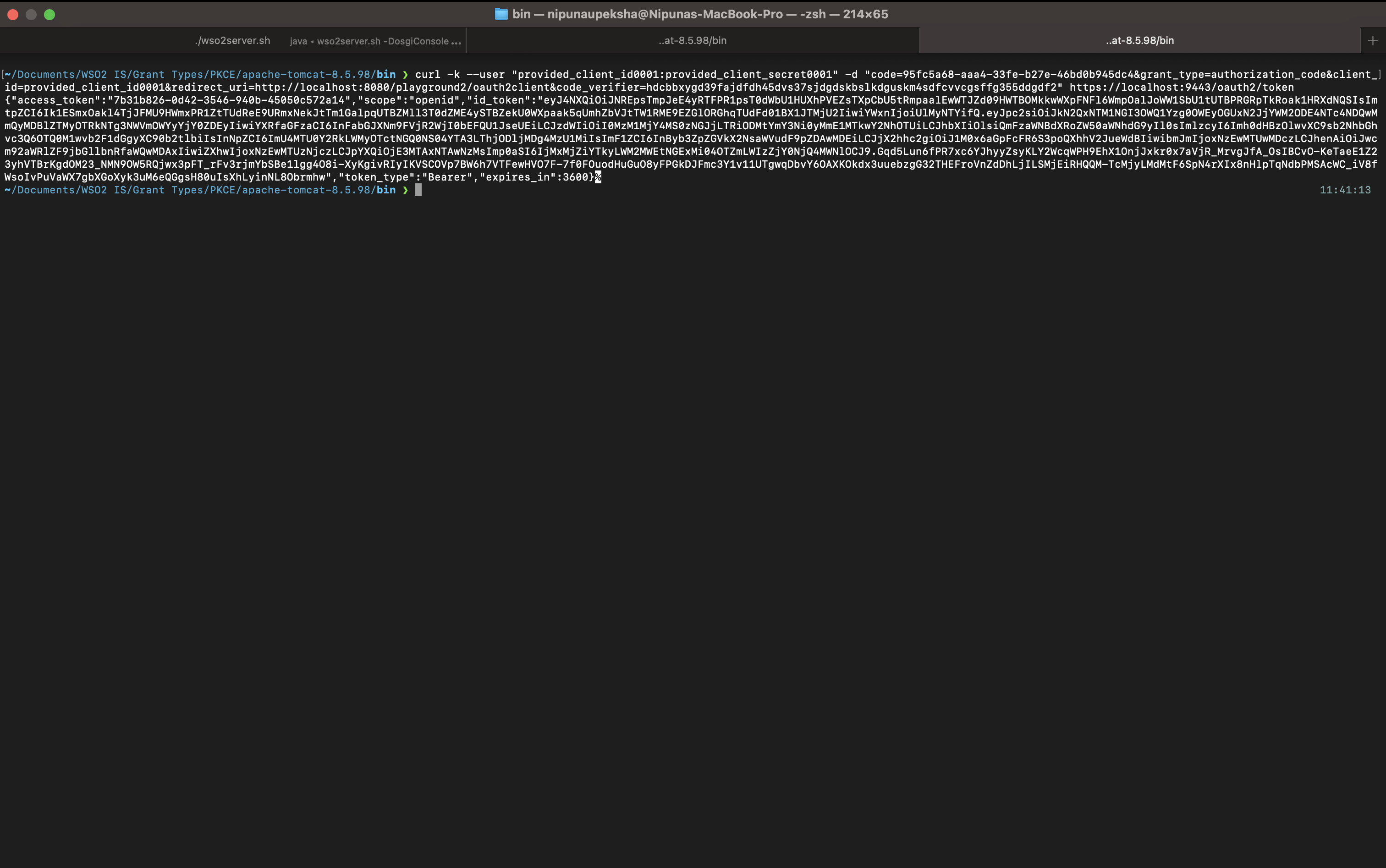
Using that you can access the resources as we have seen in the article where we discussed the Authorization Code Grant type.
📚 Reference
Subscribe to my newsletter
Read articles from Nipuna Upeksha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nipuna Upeksha
Nipuna Upeksha
Software Engineer | MSc. in Big Data Analytics | Java | Spring | IAM Expert | AWS SAA | AWS DVA