AWS Virtual Private Cloud (VPC) Explained Simply
 Trinaya Kantevari
Trinaya KantevariWhen one server is used by AWS to provide instances to different organizations, if one of the instances is hacked, all the other instances of that server would be affected by the hack. This security breach is unacceptable, prompting AWS to introduce the concept of Virtual Private Cloud (VPC) as a solution.
VPC is a private, secure, and isolated area in the cloud where you can run your applications and store your data.
A VPC is a virtual network that you create in the cloud. It allows you to have your own private section of the internet, just like having your own network within a larger network. Within this VPC, you can create and manage various resources, such as servers, databases, and storage.
Think of it as having your own little "internet" within the bigger internet. This virtual network is completely isolated from other users' networks, so your data and applications are secure and protected.
In a VPC, a DevOps engineer is responsible for building, maintaining, and configuring everything within the VPC, following the provided documentation. The size of a VPC is determined by its IP address range, which is divided into smaller subnets.
These subnets help you organize your resources and control how they communicate with each other. Each project within the company is assigned a subnet, and each application within a project is deployed onto an instance, which is assigned a specific IP address.
By implementing AWS VPC, the company can ensure the security of its multiple projects and their respective applications. Each project is allocated a subnet within the VPC, and each application within a project is deployed on a dedicated instance with its own IP address.
To access the VPC, the DevOps engineer creates a gateway, which serves as the entry point. The subnets within the VPC are private and do not have direct access to the internet.
Inside the VPC, there is a public subnet that acts as the initial point of access for users. This public subnet is connected to the internet through an Internet Gateway.
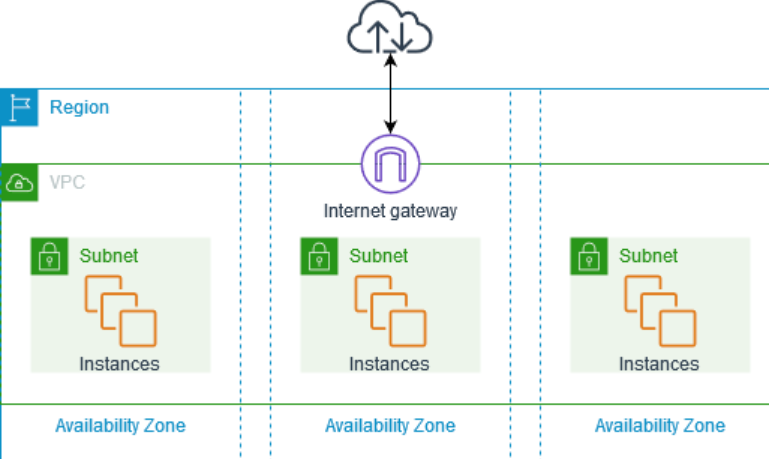
Users enter the VPC through the public subnet, which is equipped with a load balancer responsible for distributing incoming requests based on the current load. The load balancer forwards requests to the appropriate target group.
The route table defines the path from the load balancer to the desired subnet within the VPC.
Once a request reaches the subnet, it encounters a security group that acts as a protective barrier. The security group examines the IP address of the request and either allows or rejects it based on its defined rules.
Hence to connect your VPC to the internet or other networks, you can set up gateways or routers. These act as entry and exit points for traffic going in and out of your VPC. You can control the flow of traffic and set up security measures to protect your resources from unauthorized access.
With a VPC, you have control over your network environment. You can define access rules, set up firewalls, and configure security groups to regulate who can access your resources and how they can communicate.
By default, when you create an AWS account, AWS will create a default VPC for you but this default VPC is just to get started with AWS. You should create VPCs for applications or projects.
NAT Gateway
NAT gateway is used to allow instances within a subnet to access the internet without exposing their IP addresses. The NAT gateway masks the IP address and replaces it with either the public address of the load balancer or the router, depending on the path. If the traffic goes through the load balancer, it is referred to as SNAT (Source Network Address Translation). If it goes through the router, it is known as a NAT gateway.
The NAT gateway plays a crucial role in enabling instances to download and access resources from the internet while keeping their IP addresses hidden. It is created within the public subnet.
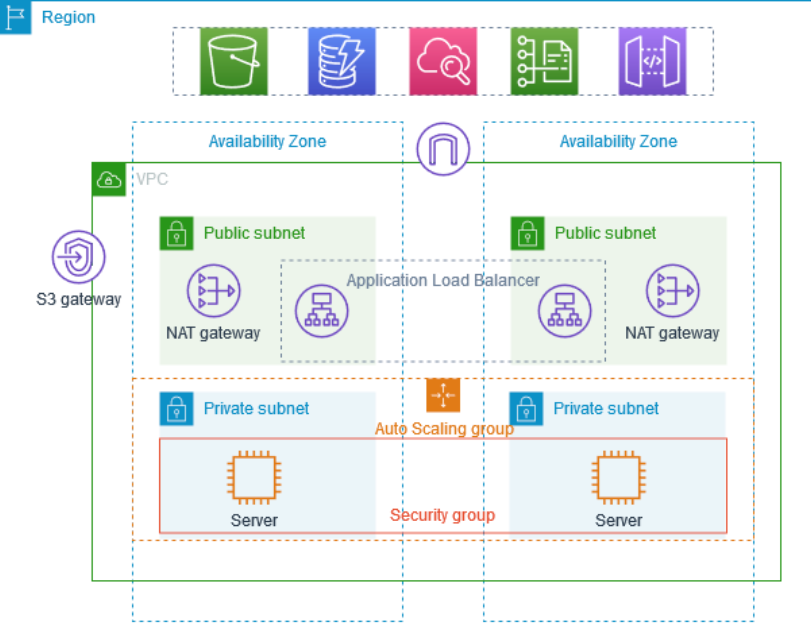
VPC components
The following features help you configure a VPC to provide the connectivity that your applications need:
Virtual private clouds (VPC) : A VPC is a virtual network that closely resembles a traditional network that you'd operate in your own data center. After you create a VPC, you can add subnets.
Subnets : A subnet is a range of IP addresses in your VPC. A subnet must reside in a single Availability Zone. After you add subnets, you can deploy AWS resources in your VPC.
IP addressing : You can assign IP addresses, both IPv4 and IPv6, to your VPCs and subnets. You can also bring your public IPv4 and IPv6 GUA addresses to AWS and allocate them to resources in your VPC, such as EC2 instances, NAT gateways, and Network Load Balancers.
Network Access Control List (NACL) : A Network Access Control List is a stateless firewall that controls inbound and outbound traffic at the subnet level. It operates at the IP address level and can allow or deny traffic based on rules that you define. NACLs provide an additional layer of network security for your VPC.
Security Group : A security group acts as a virtual firewall for instances (EC2 instances or other resources) within a VPC. It controls inbound and outbound traffic at the instance level. Security groups allow you to define rules that permit or restrict traffic based on protocols, ports, and IP addresses.
Routing : Use route tables to determine where network traffic from your subnet or gateway is directed.
Gateways and endpoints : A gateway connects your VPC to another network. For example, use an internet gateway to connect your VPC to the internet. Use a VPC endpoint to connect to AWS services privately, without the use of an internet gateway or NAT device.
Peering connections : Use a VPC peering connection to route traffic between the resources in two VPCs.
Traffic Mirroring : Copy network traffic from network interfaces and send it to security and monitoring appliances for deep packet inspection.
Transit gateways : Use a transit gateway, which acts as a central hub, to route traffic between your VPCs, VPN connections, and AWS Direct Connect connections.
VPC Flow Logs : A flow log captures information about the IP traffic going to and from network interfaces in your VPC.
VPN connections : A flow log captures information about the IP traffic going to and from network interfaces in your VPC.
Subscribe to my newsletter
Read articles from Trinaya Kantevari directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by