AWS IAM (Identity and Access Management)
 Divya Mahajan
Divya Mahajan
Link to exam: https://aws.amazon.com/certification/certified-cloud-practitioner/
1. Understanding IAM Basics:
What is IAM?
IAM is a framework of policies and technologies designed to manage digital identities and control access to resources securely. It involves processes and tools aimed at ensuring authorized access while maintaining security.
Key Objectives of IAM
Identity Management: Manages the lifecycle of digital identities, including user account creation, management, and deletion to ensure only authorized individuals access resources.
Access Management: Controls and monitors resource access based on user identities and permissions, utilizing authentication and authorization mechanisms.
Security and Compliance: Enforces security policies and regulatory compliance through measures like multi-factor authentication and access controls.
Efficiency and Productivity: Streamlines identity and access management processes, centralizing user provisioning and deprovisioning to enhance operational efficiency.
Role of IAM in AWS
In AWS, IAM is a crucial component for secure access control to AWS resources. It allows management of users, groups, roles, and permissions, ensuring only authorized entities interact with resources. IAM serves as the foundation for security in AWS environments, providing granular control over resource access and actions.
Components of IAM:
Users: Individuals or services needing access to AWS resources within an account. Each user has unique security credentials for authentication, like usernames, passwords, access keys, or temporary tokens.
Groups: Collections of IAM users for streamlined access management. Permissions are assigned to groups rather than individuals, simplifying administration and scalability. Users can belong to multiple groups, inheriting permissions from each group they're a part of.
Roles: Entities with temporary permissions for specific tasks or applications. Commonly used to delegate access to AWS resources to applications or services like EC2 instances or Lambda functions.
Policies: JSON documents defining permissions attached to IAM identities. In AWS IAM, policies define access rights by combining multiple permissions. Policies can be attached to users, groups, roles, or even AWS resources, governing their access and actions within the AWS environment.
Managed policies offer predefined permission sets for common use cases,
Inline policies allow for custom permissions tailored to specific requirements.
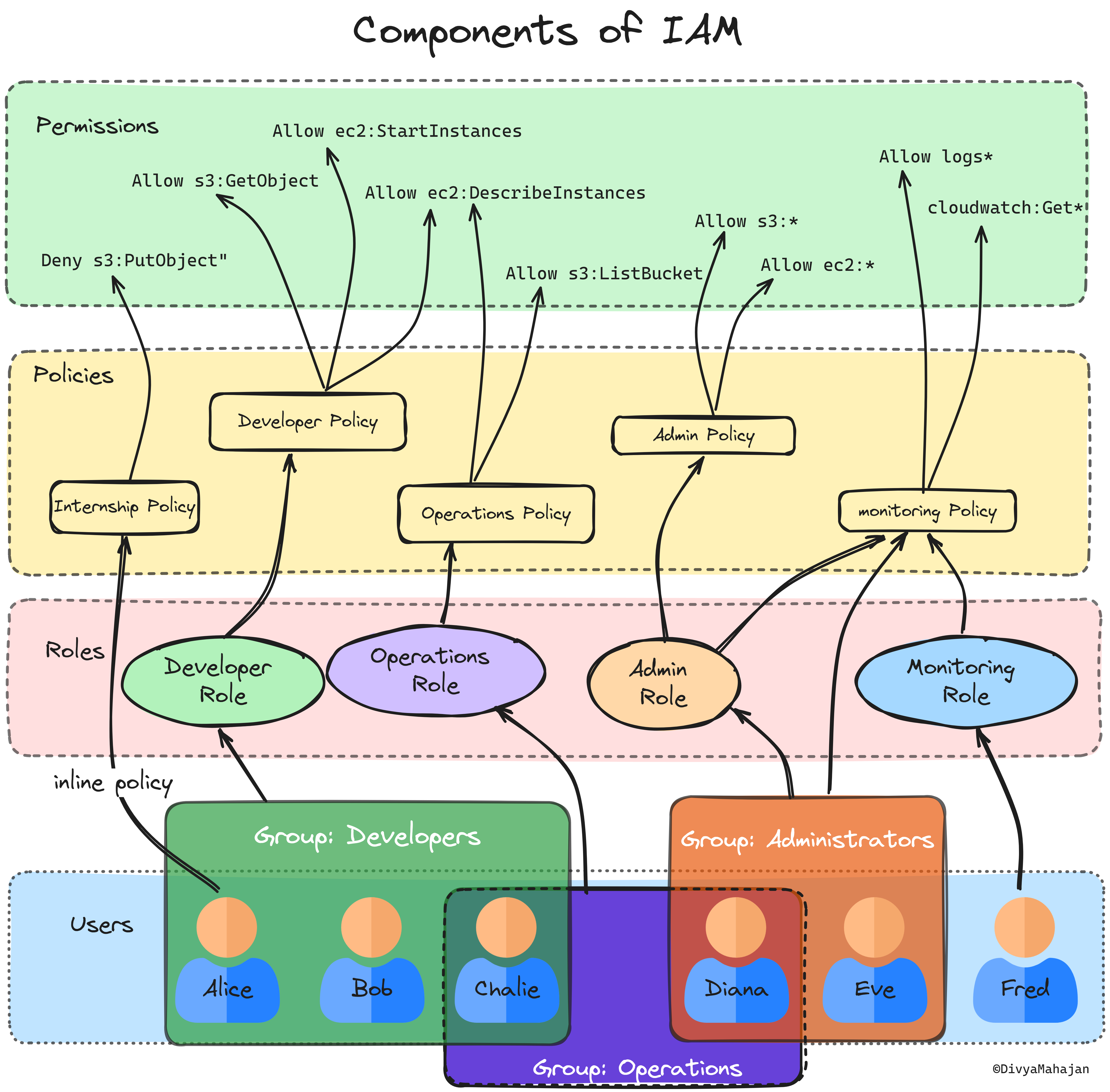
Key Notes:
Root Account Precautions: The default root account should be avoided for regular use or sharing due to its elevated privileges and security risks.
User and Group Flexibility: Users can operate independently without belonging to a group, and they can belong to multiple groups for enhanced access management.
Group Composition: Groups exclusively consist of users; they cannot contain other groups, only individuals.
Role Flexibility in Groups: Each group can be associated with multiple roles, and the same role can be assigned to multiple groups, offering versatility in access control.
Policy and Permissions: While it's possible to assign permissions individually, it's more practical to assign policies than individual permissions as they streamline management and updates.
Policy Assignment in Roles: Roles can be equipped with multiple policies, and multiple roles can be endowed with the same policy, providing granular control over permissions.
Inline Policy Option: Users can have policies directly assigned to them without inheriting through roles, known as inline policies, offering additional customization options for specific user needs.
2. IAM Authentication and Authorization:
Authentication
Authentication in IAM involves verifying the identity of users or services attempting to access AWS resources. IAM supports various authentication methods, including:
Username and password: Standard authentication mechanism for IAM users.
Access keys: Long-term credentials used by applications or AWS services to make programmatic requests to AWS APIs.
Temporary security tokens: Generated dynamically and used for short-term access to AWS resources, typically obtained through the AWS Security Token Service (STS).
Multi-factor authentication (MFA): Adds an extra layer of security by requiring users to provide a second form of verification, such as a time-based one-time password (TOTP) generated by a hardware or software token.
Authorization
Authorization in IAM determines what actions users or services are allowed to perform within AWS. Permissions are granted through policies attached to IAM identities. Key concepts related to authorization include:
Managed Policies: Predefined sets of permissions provided by AWS for common use cases, such as read-only access to S3 buckets or full administrative access to an AWS account.
Inline Policies: Custom policies that you create and attach directly to IAM identities, allowing for more granular control over permissions.
Permission Boundaries: Limits the maximum permissions an IAM identity can have, providing an additional layer of control to prevent unintended access.
3. IAM Best Practices:
Principle of Least Privilege: Grant users only the minimum permissions necessary for their tasks to minimize the risk of unauthorized access and security breaches.
Multi-Factor Authentication (MFA): Enable MFA to add an extra layer of security, requiring users to provide a second form of verification beyond passwords, reducing the risk of compromised credentials.
Use of Access Keys for Programmatic Access: Utilize Access Keys for programmatic access, allowing users and applications to interact with AWS services via the Command Line Interface (CLI) or Software Development Kits (SDKs) while maintaining security.
IAM Roles for EC2 Instances: Securely delegate permissions to applications running on EC2 instances by assigning IAM roles, reducing the exposure of long-term credentials and simplifying credential management.
IAM Policies Conditions: Enhance access control by using IAM policies with conditions, specifying additional constraints such as time of day, source IP address, or resource tags to tailor permissions to specific scenarios.
Strong Password Policy: Implement a robust password policy to ensure that passwords used for accessing AWS accounts are sufficiently complex and resistant to brute force attacks.
Regular Review and Monitoring: Conduct regular audits of IAM permissions using tools like IAM Credentials Report and IAM Access Advisor to ensure alignment with business needs, security standards, and compliance requirements. Identify and rectify any excessive permissions or unauthorized access, maintaining a secure and compliant AWS environment.
Avoid Sharing IAM Users & Access Keys: Strictly prohibit the sharing of IAM users and Access Keys, ensuring that each user has their own set of credentials to prevent unauthorized access and maintain accountability.
4. IAM Security Features:
IAM Access Analyzer: Analyze resource policies to detect unintended access, providing insights into resource access and granting alerts for potential issues, ensuring a secure and compliant AWS environment.
IAM Policy Simulator: Test IAM policies' effects before application, verifying alignment with access control policies and identifying conflicts, offering a risk-free method for policy evaluation and refinement.
AWS Organizations: Centrally manage multiple AWS accounts, applying policies and controls across member accounts, simplifying governance, compliance, and security management, ensuring consistency and reducing administrative overhead.
IAM Roles for Service Accounts (IRSA): Securely grant Kubernetes workloads access to AWS services by associating IAM roles with Kubernetes service accounts, enforcing the principle of least privilege, and ensuring authorized access to AWS resources.
IAM Access Control Lists (ACLs): Control network-level access to AWS resources by defining rules for allowed or denied IP addresses or ranges, adding an extra layer of protection against unauthorized network traffic and enhancing overall AWS environment security.
5. IAM Integration with Other AWS Services:
Amazon S3 Bucket Policies: Define granular access permissions for S3 buckets, controlling data access based on factors like IP address or IAM identity, ensuring secure and controlled access to S3 data.
AWS Lambda Function Policies: Specify permissions for Lambda function invocation, controlling access based on event sources, caller identities, or conditions, ensuring precise control over function access and actions.
AWS IAM Roles for AWS Services: Grant permissions to AWS services to access other resources securely, enforcing the principle of least privilege, and limiting access to only necessary resources, enhancing security and control over AWS services.
AWS IAM Access Advisor: Gain insights into IAM usage by analyzing last accessed time and credential age, identifying unused permissions and potential security risks, optimizing IAM permissions, and improving overall security posture in your AWS environment.
6. IAM Compliance and Governance:
Compliance with Regulatory Standards: IAM ensures compliance with GDPR, HIPAA, PCI DSS, SOC 2, and other regulatory standards by implementing best practices, enforcing least privilege, and auditing permissions, safeguarding sensitive data from unauthorized access.
IAM Access Reports: Gain visibility into IAM usage and permissions with access reports, monitoring activity, identifying security incidents or policy violations, and tracking IAM permission changes over time, facilitating compliance audits and security incident investigations.
AWS CloudTrail Integration: CloudTrail logs IAM actions, recording who did what, when, and from where in your AWS environment, enabling IAM activity audits, policy change tracking, and security incident investigations, maintaining an audit trail for compliance, governance, and security purposes.
AWS Config Rules: Automate IAM compliance assessments with Config Rules, evaluating IAM configurations against predefined rules, detecting deviations, and alerting on non-compliant resources, providing continuous monitoring and proactive remediation for a secure and compliant AWS environment
7. Hands-On AWS IAM: A Step-by-Step Guide
Explore a comprehensive walkthrough for mastering user management, configuring security settings, and enabling programmatic access in AWS IAM.
For hands-on practice, delve into the detailed article "AWS IAM: Hands-On | A Step-by-Step Guide" at the provided link: AWS IAM: Hands-On | A Step-by-Step Guide.
References:
AWS Identity and Access Management (IAM) Documentation: https://docs.aws.amazon.com/iam/index.html
AWS Certified Cloud Practitioner Exam Guide: https://aws.amazon.com/certification/certified-cloud-practitioner/
AWS IAM Best Practices: https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
AWS Security Best Practices: https://aws.amazon.com/whitepapers/aws-security-best-practices/
Subscribe to my newsletter
Read articles from Divya Mahajan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Divya Mahajan
Divya Mahajan
Experienced Technical developer with 6+ years' global collaboration. Proficient in Python, Go, React, Next.js, Django, various databases, Cloud & DevOps (AWS EC2, Docker, Kubernetes), and Big Data tools. Skilled in data structures and algorithm, API development, and end-to-end software engineering. Excels in back-end development, front-end design, Root Cause Analysis, and product management to deliver superior user experiences. Holds a master’s degree in computer engineering.