The Ultimate Guide to Securing Your X/Twitter Account
 Rivanorth
Rivanorth
Following the SEC's X account compromise earlier this year and the fact that 5 out of the 10 top blockchain hacks of 2023 were not directly related to smart contract vulnerabilities but rather operational security, bringing awareness to a few key steps that can greatly increase your X account's security becomes a no brainer.
How can your X account get compromised?
There are basically two main avenues attackers can use to take over your X account:
Password compromise
SIM swapping
Let's explore them.
Password Compromise
It is very unlikely that an attacker can successfully execute a bruteforce password attack i.e. try lots of password combinations to gain access to your account, as X will likely block the IP of the attacker and make it very slow to try lots of password combinations, think months/years, making this attack vector unfeasible.
An easier avenue becomes available if you've been reusing the same password and email address/phone number across multiple platforms. Once that very passwords gets leaked, the attacker can simply log in using that password. This is where MFA comes in to play, with that additional code, the attacker won't be able to take over your account. So let's look into how a few steps can skyrocket your account's security.
Implementing MFA
Go into settings
Select security
And tick authenticator app
Authenticator app is the most user friendly option, and ultimately the most secure one. Security keys are a great option but it creates the risk of loosing the key which could mean getting locked out of your account and is only advisable for very risk adverse users that are willing to build in redundancy in case that was to occur. For the general public we recommend the authentication app which provides great security and a good balance of usability and security.
Below we'll explore why using the text message option is not the best way to go.
SIM Swapping
SIM swapping is a type of identity theft where a criminal tricks a mobile phone provider into transferring a victim's phone number to a SIM card controlled by the criminal. This is often achieved by the criminal impersonating the victim and providing fake credentials to the mobile provider, convincing them to switch the phone number to a new SIM card. Once the number is transferred, the criminal can receive all the victim's calls and text messages, including those containing one-time passwords and verification codes. And this is how the attack works on X.
Select forgot password
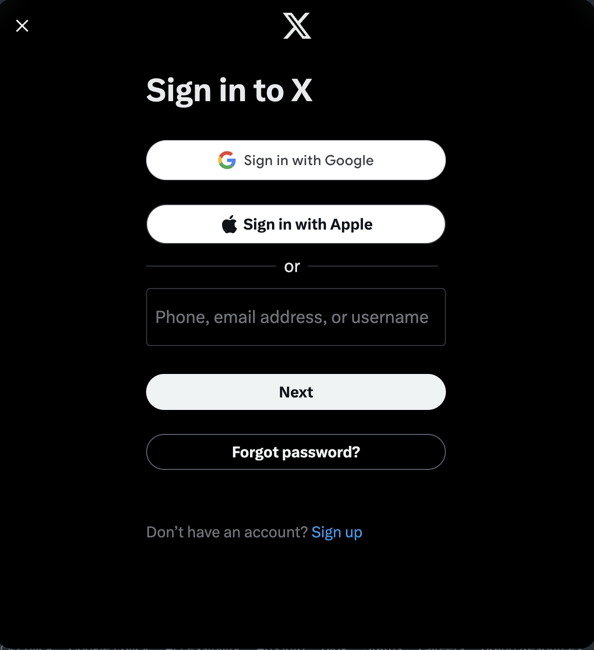
We get presented with a window where we can search for the account that we want to compromise, we have already successfully executed a SIM swap and have access to their mobile number.
We insert the user handle (this is public information)
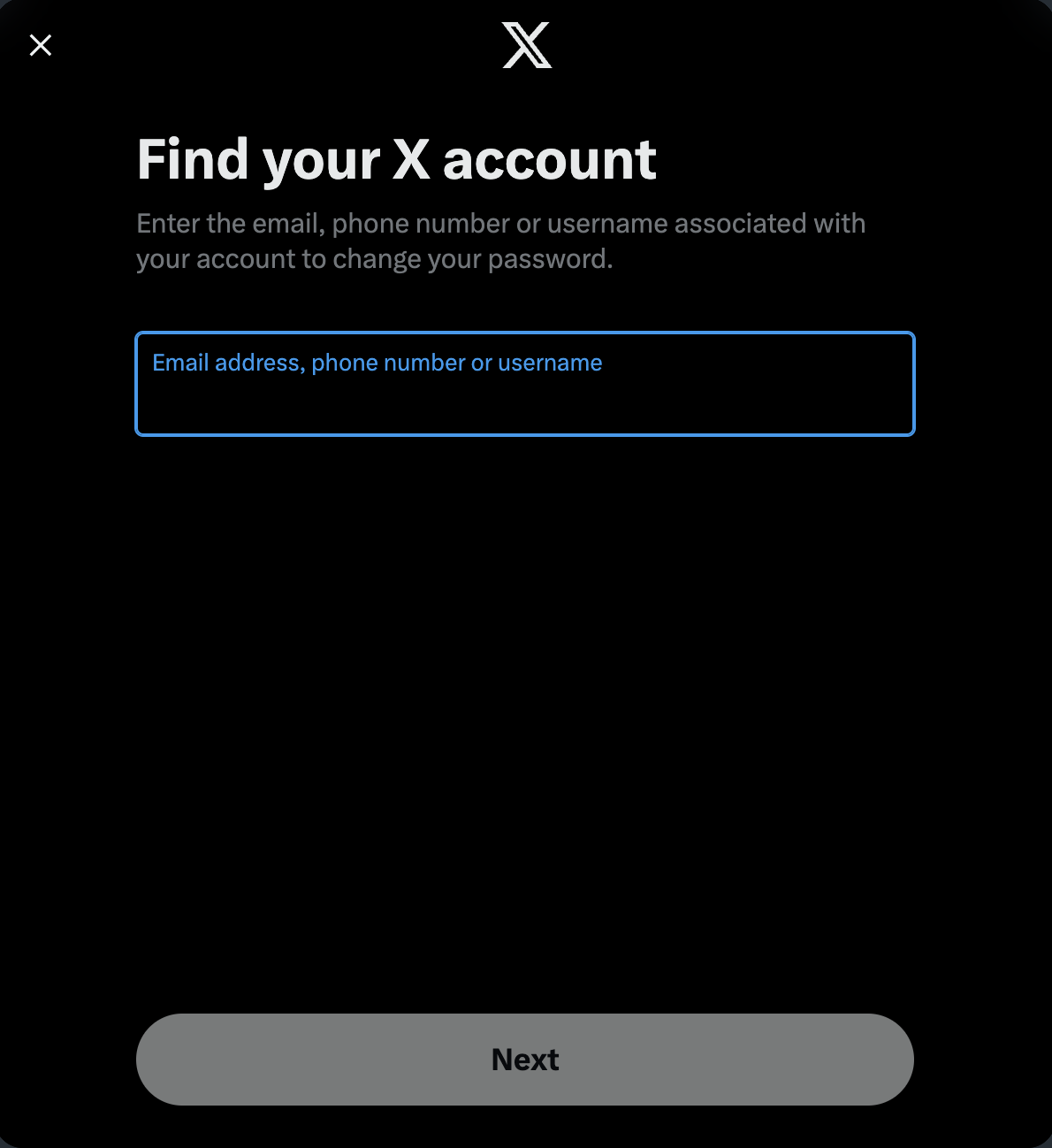
Now we enter the email address, this is not hard to find as ofter users expose this on other social media platforms
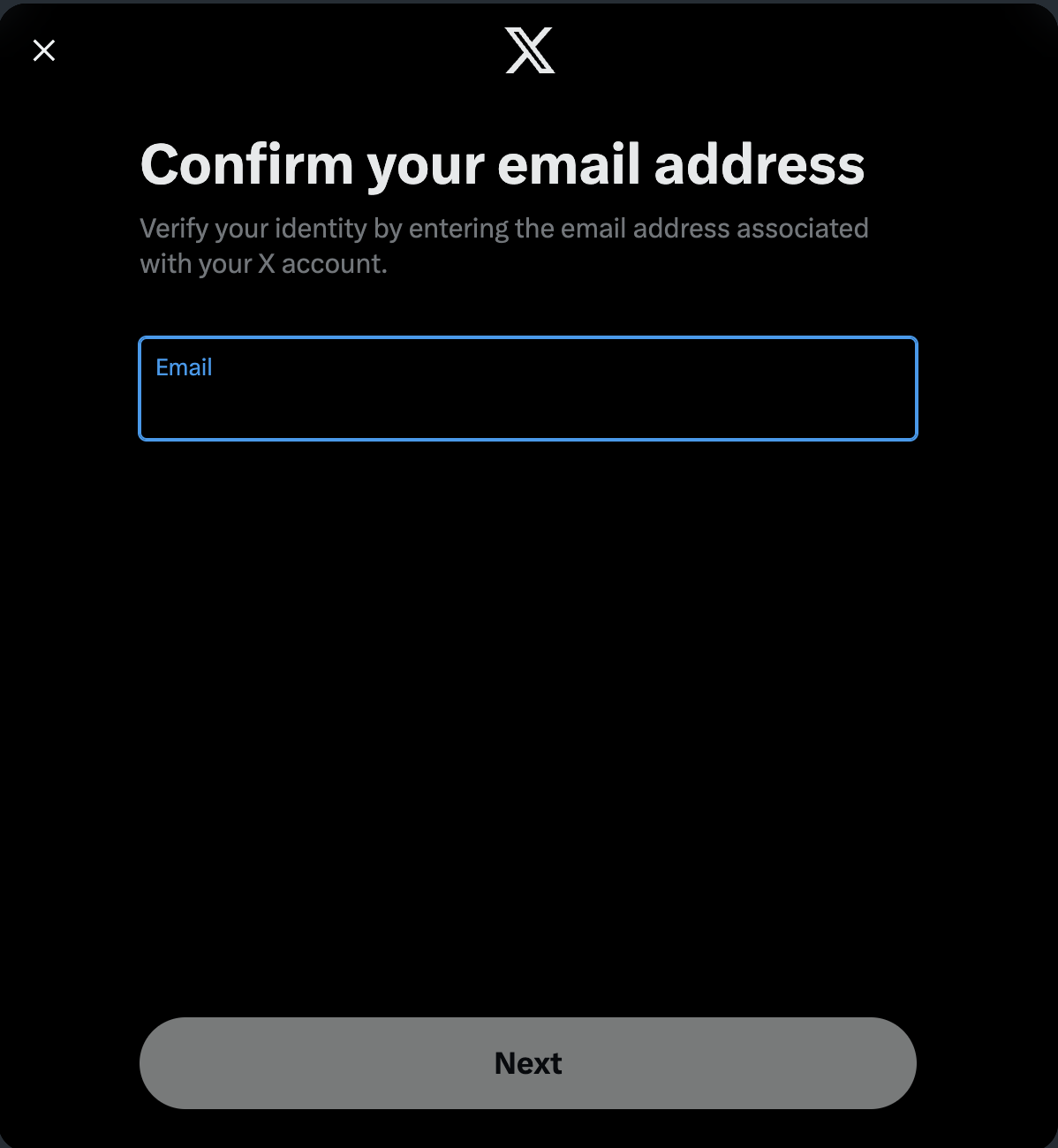
Final step, insert the compromised phone number
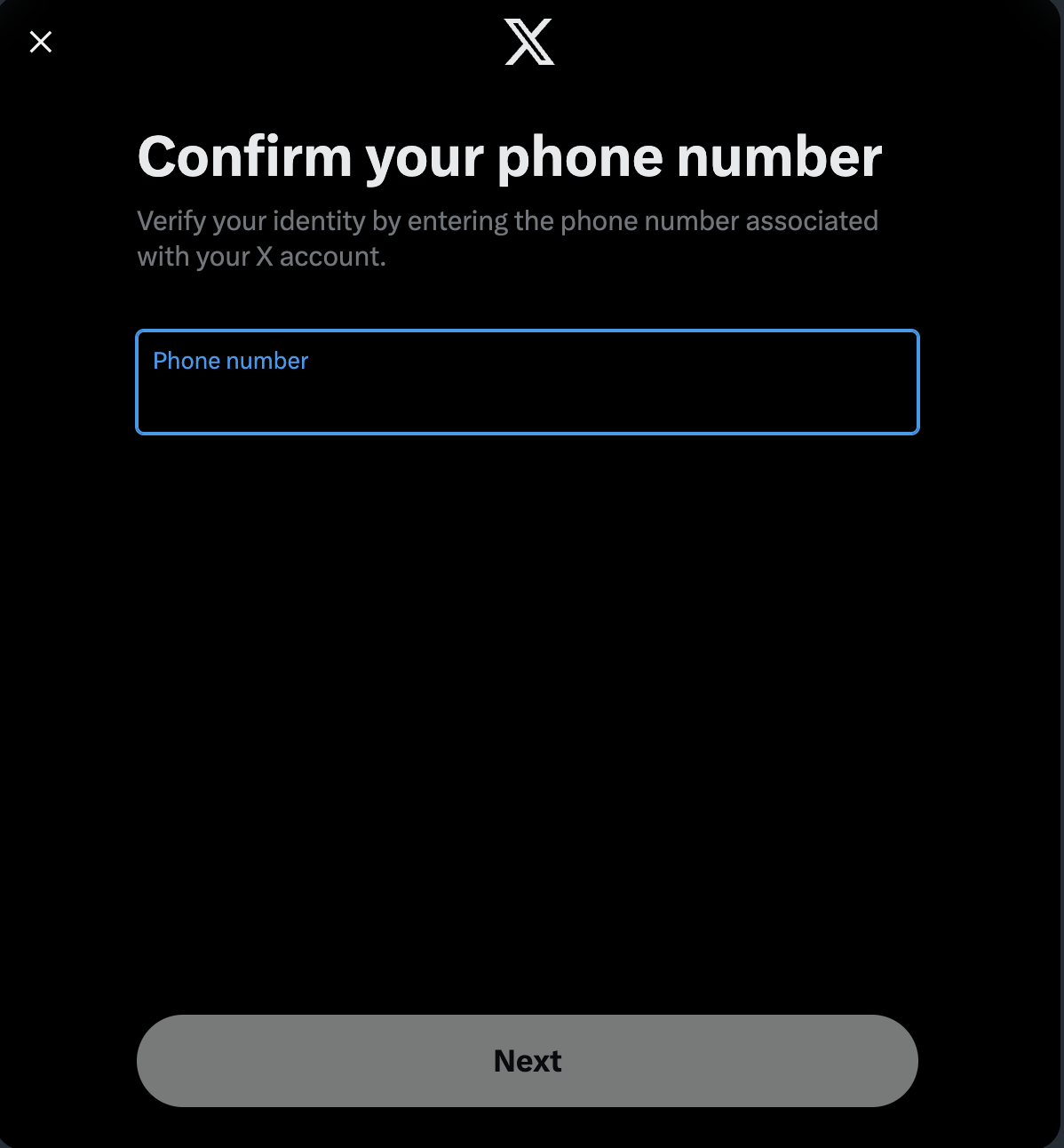
And we can request a text message to reset the password
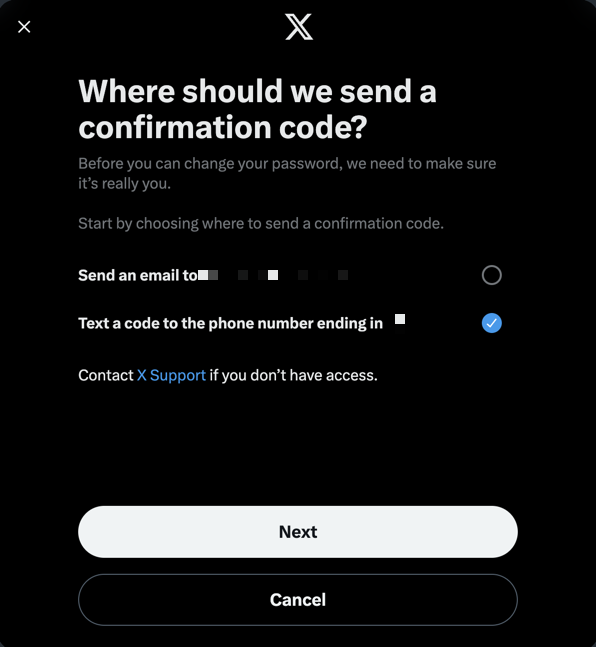
Once the account is compromised it can be very hard, if not impossible to get it back. This is what you can do to protect yourself from SIM swap attacks.
Locking down your account
To create a new X account you are required to authenticate it with a phone number, but beyond the initial account creation this is not required later on. These are the steps to remove your phone number and make this type of attack impossible.
Visit settings/your account/account information
Select phone
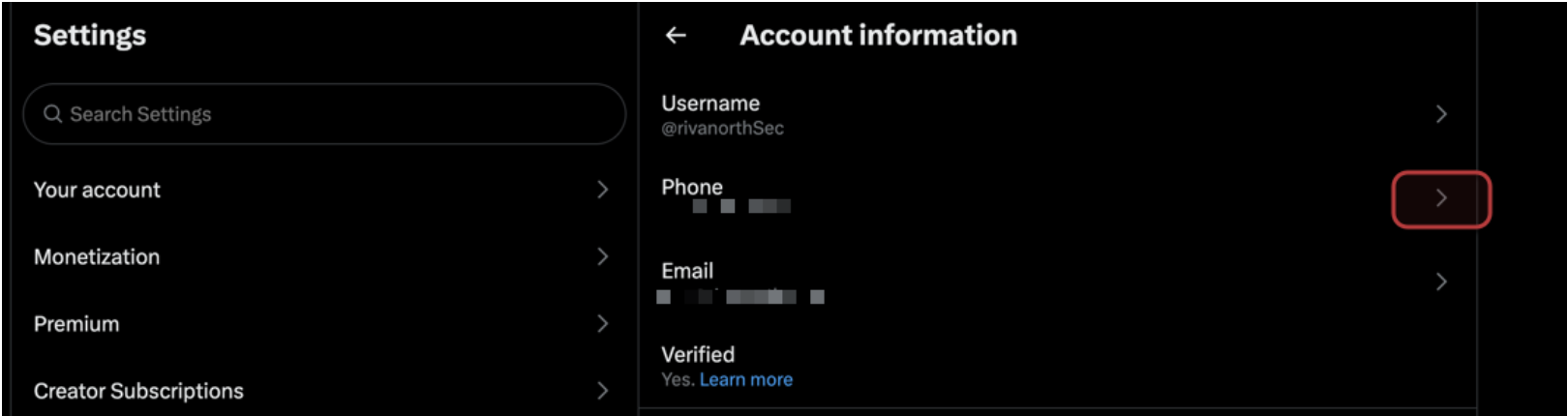
and remove the phone number. That's it.
Conclusion
Securing your X account is not hard but admittedly X hasn't made it straight forward, removing the phone number and enabling MFA, not only on X but on all your accounts will greatly increase your general security making it much harder for attackers.
Subscribe to my newsletter
Read articles from Rivanorth directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rivanorth
Rivanorth
State of the art Cybersecurity services, always a step ahead. You build the future. We help you secure it.