HTTP vs HTTPS Understanding the Difference and what is TLS?
 Nikhil Pandey
Nikhil Pandey
Have you ever noticed a little lock icon in the address bar of your browser while browsing the web? This seemingly simple icon signifies a crucial difference in how your data travels online. In this blog post, we'll embark on a journey to understand HTTP & HTTPS protocols, delve into the workings of TLS encryption, and discover why HTTPS is the undisputed champion of secure browsing.
Part 1: Understanding HTTP
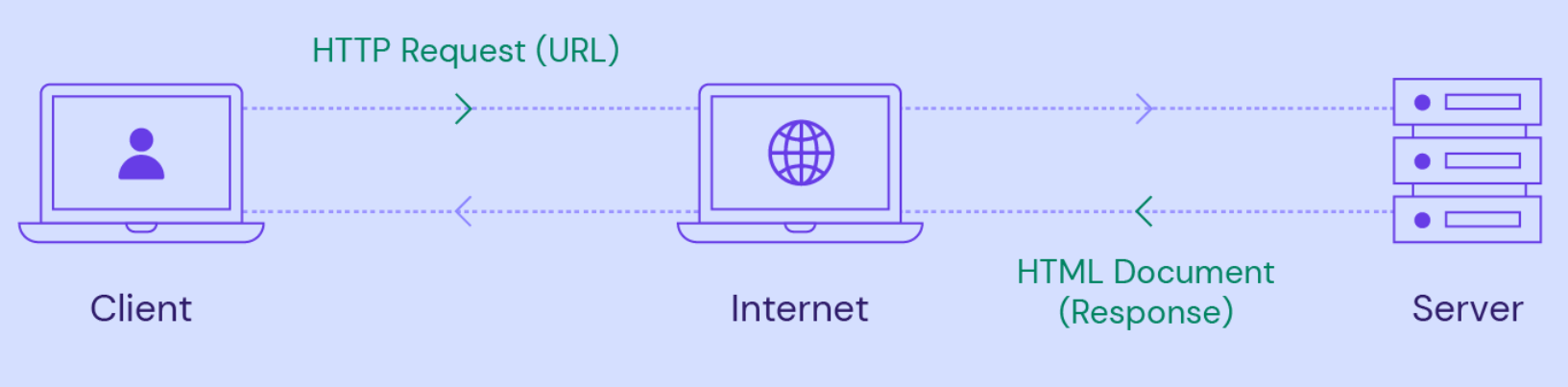
HTTP stands for Hypertext Transfer Protocol. It is the set of rules that sets the foundation of communication on the World Wide Web. It enables the transfer of hypertext documents, such as web pages, between clients (e.g. web browsers) and servers (e.g. web servers). When you type a URL into your web browser and hit enter, your browser sends an HTTP request to the server hosting the requested web page. The server then responds with an HTTP response containing the requested content.
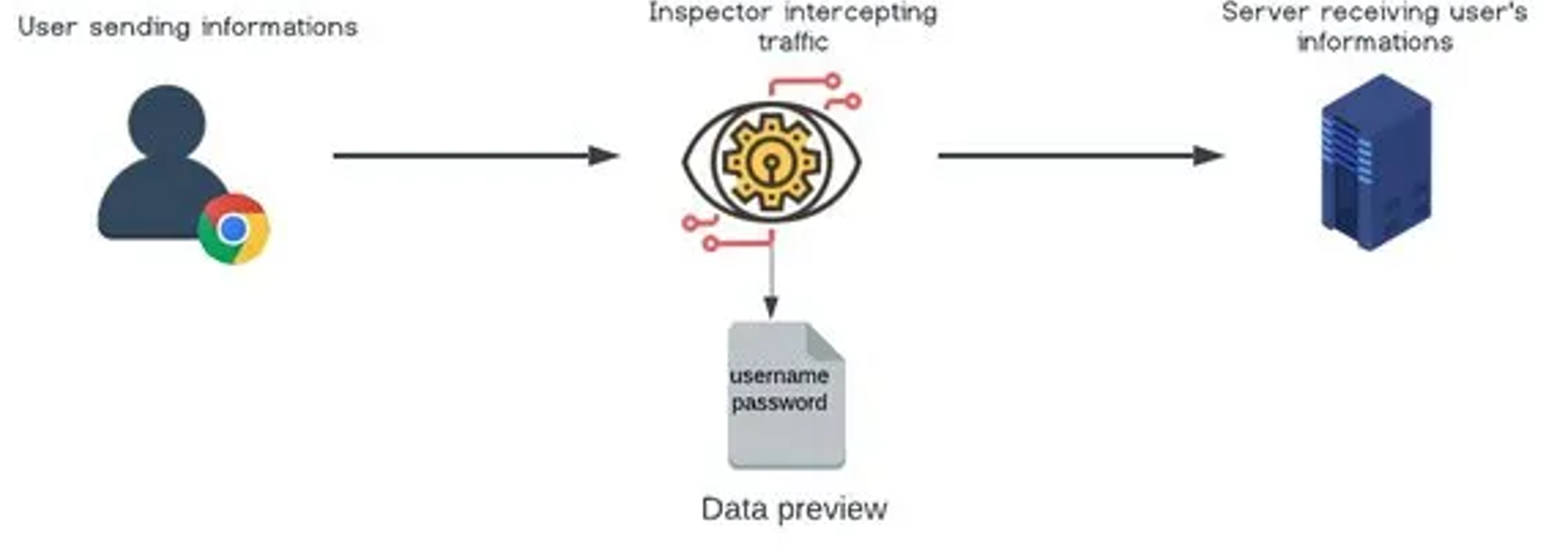
HTTP operates over TCP (Transmission Control Protocol), which is a connection-oriented protocol that ensures the reliable delivery of data packets over the Internet. But, HTTP is not secure by default. Data transmitted over HTTP is sent in plain text, which means that it can be intercepted and read by anyone with the technical know-how to do so. This lack of encryption makes HTTP vulnerable to various security threats, such as eavesdropping, data tampering, and man-in-the-middle attacks.
Part 2: Understanding HTTPS

After learning about HTTP, we learned that it governs how data is transmitted over the internet b/w client and server. But it is not secure, To solve this security issue HTTPS comes into the picture.
HTTPS, or Hypertext Transfer Protocol Secure, is an extension of HTTP that adds a layer of security to web communication. It uses a combination of HTTP and TLS (Transport Layer Security) to encrypt data exchanged between clients and servers, thereby protecting it from interception and tampering.
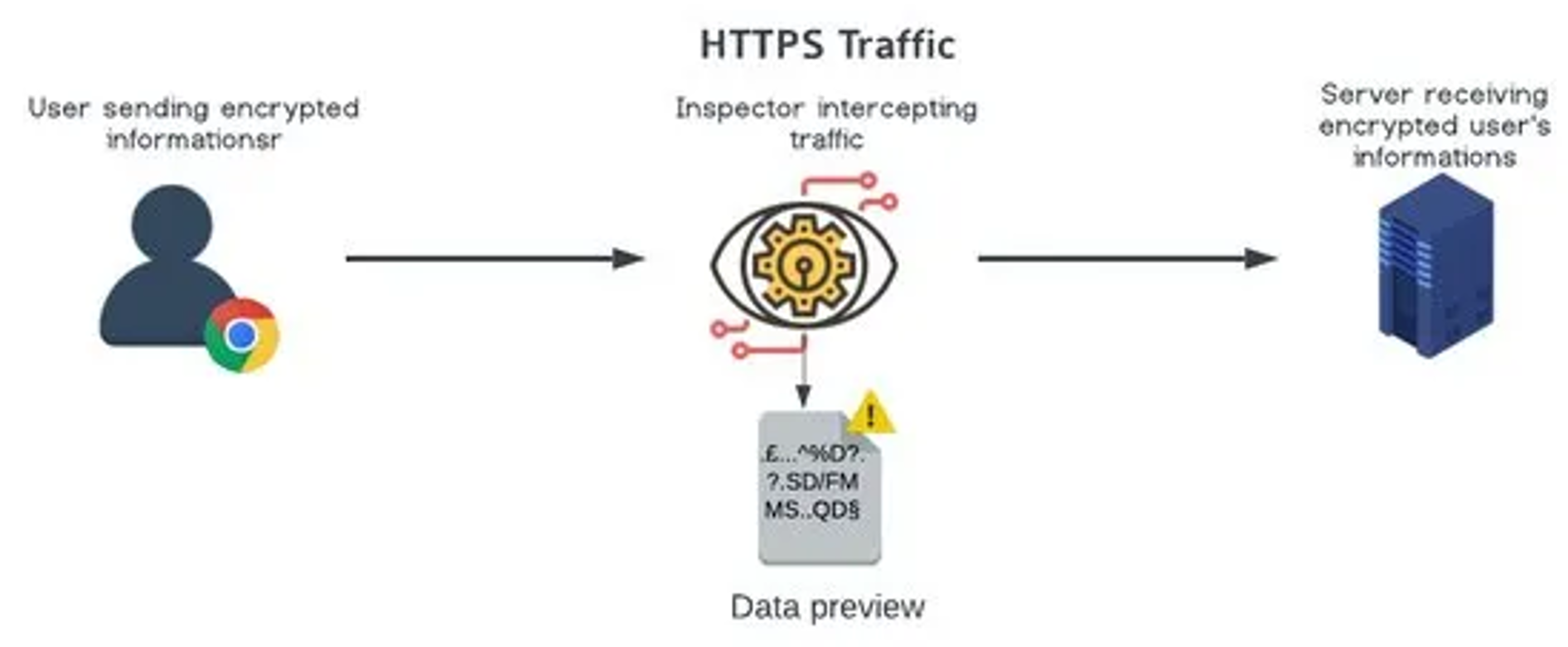
When you visit a website using HTTPS, your web browser establishes a secure connection with the server using TLS encryption. This encryption ensures that any data transmitted between your browser and the server is encrypted and cannot be deciphered by unauthorized parties. This is particularly important when transmitting sensitive information such as passwords, credit card numbers, and personal data.
In addition to encryption, HTTPS also provides authentication, ensuring that you are connected to the legitimate website and not a malicious imposter. Websites using HTTPS are issued digital certificates by trusted Certificate Authorities (CAs), which serve as proof of their identity. Your web browser verifies these certificates to ensure the authenticity of the website you are visiting.
Can you now guess what that lock icon on your search bar signifies?
I hope you were able to guess it. Anyway, It signifies that your browser is using HTTPS for secure Communication.
Part 3: The Difference b/w HTTP vs HTTPS
After understanding Http and Https individually. let's compare them in detail
| HTTP | HTTPS |
| Sends plain text data | Transmit data using encryption |
| Receive unencrypted data | Digitally sign requests and responses |
| Not Secure | Highly Secure due SSL/TLS encryption |
| Send requests and responses without owner and intent verification | Verify ownership and intent of online requests and responses |
| HTTP works at the application layer. | HTTPS works at the transport layer. |
| The default port number is 80, for communication. | Here the default port number is 443 |
| It is lightweight, considering no additional security headers | It is Heavier than HTTP, considering additional security headers |
| Not SEO friendly | SEO friendly, all search engines prefer HTTPS-enabled websites/web applications |
Part 4: What is TLS and How it works?
TLS stands for Transport Layer Security, which is an advanced version of SSL (Secure Sockets Layer) for more detail check this
It is a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP)
we have already discussed that HTTPS is the combination of HTTP and TLS (Transport Layer Security) to encrypt the data exchanged between clients and servers.
This is achieved by the process of TLS handshaking b/w client and server.
Before understanding TLS handshaking we need to know two concepts
Asymmetric encryption:
It is an encryption technique that uses 2 keys, public & private keys
Public key is shared with the public and the data that is being encrypted by the public key can only be decrypted with its corresponding private key.
for more details check this
Symmetric encryption :
It is an encryption technique that uses only 1 key for encryption & decryption
data that is encrypted with the key can only be decrypted with the same key
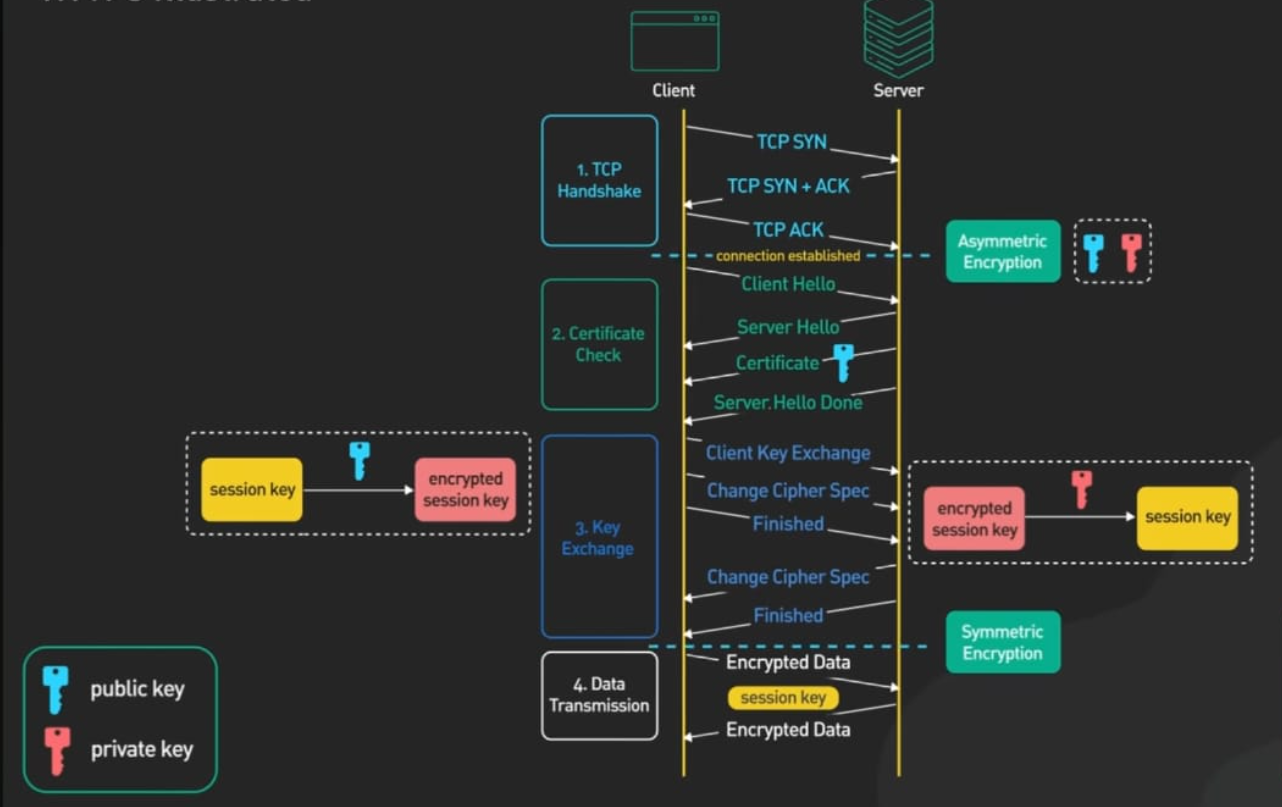
now let us understand in detail how TLS Handshaking happens
Step 1: TCP handshake
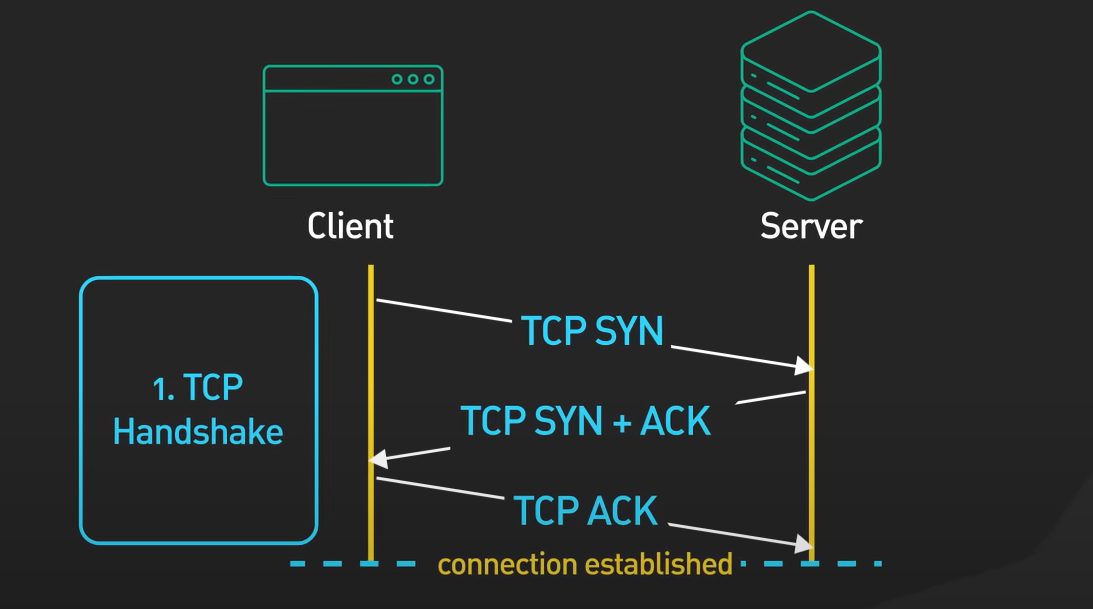
The first step is to establish a connection b/w client and server by the process of TCP Handshaking. To learn about TCP Handshaking check this
After a secure connection is established b/w client and server. actual TLS handshaking process begins.
Step 2: Certificate Check
During this phase server's certificate & public key are sent to the client & communication parameters are configured.
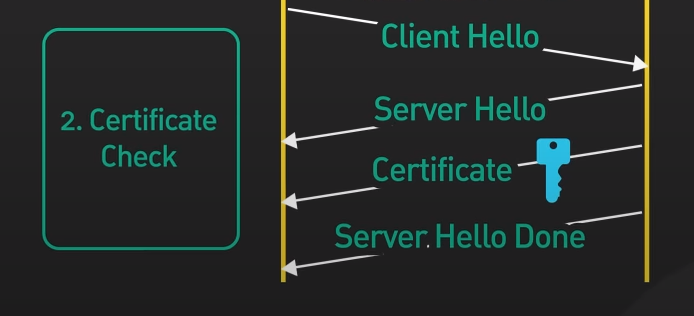
Client Hello: the client sends a Client Hello request to the server that specifies which TLS version(1.2, 1.3 etc) and cyber suites (encryption algorithms) that are supported by the client.
Server Hello: the server receives the Client Hello request and configures & sends its Server Hello response by agreeing on the TLS version & cyber suites (encryption algorithms) to be used during communication, based on the Client Hello request.
The server also sends its public key along with its Certificate (which is issued by trusted Certificate Authorities (CAs)) to the client for authentication purpose, so that the client can uniquely identify & verify the server that it is interacting with.
At this point, the client has the server's certificate and its public key and they both have agreed upon which TLS version & encryption algorithm to use for secure communication.
Step 3: Key Exchange
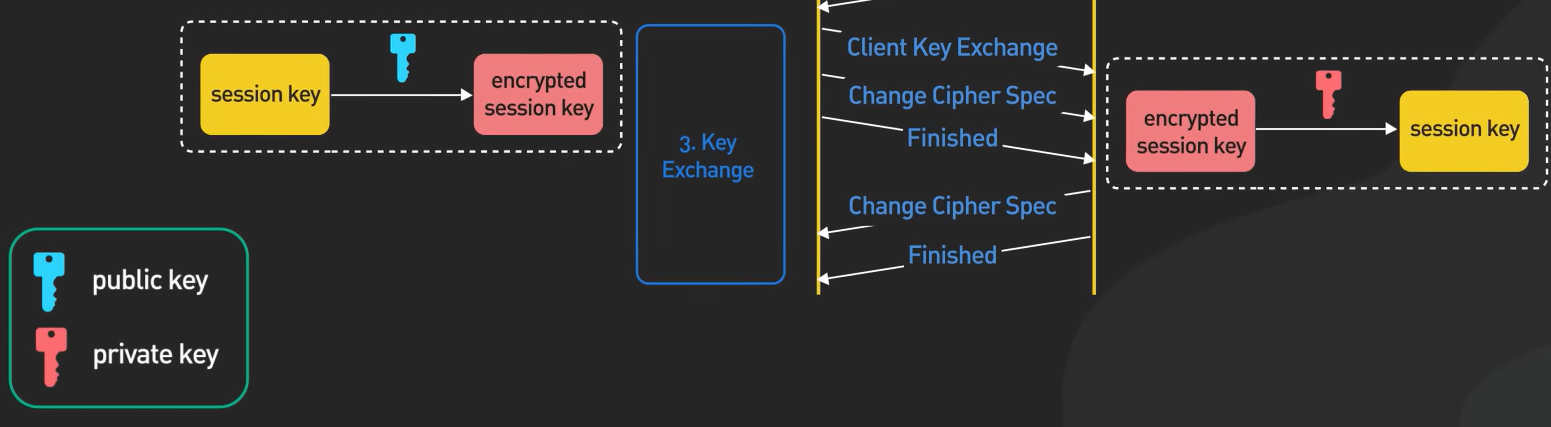
Now, the client generates a session key using an encryption algorithm such as Diffie–Hellman (DH), RSA, etc. This session key is then encrypted using the server's public key and transmitted to the server over an open network. Upon receiving the encrypted session key, the server decrypts it using its private key.
and by this way using the Asymmetric encryption Technique, both client and server have securely shared the session key.
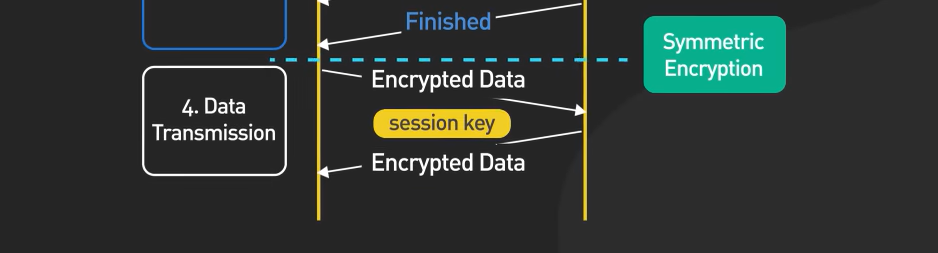
Step 4: Data Transmission
In this step, the exchange of data b/w client and server begins, which is encrypted & decrypted using the shared session key. This employs a Symmetric encryption Technique.
Q: why are we using both Symmetric & Asymmetric encryption Technique ? why not only use the Asymmetric encryption Technique?
Ans: Asymmetric encryption Technique is computationally expensive that's why we only use it once to share the session key b/w client & server and from there we use the symmetric encryption Technique which is less computationally expensive.
Note: This description is for TLS v1.2, TLS v1.3 is an optimized version of TLS v1.2, which uses a single encryption Technique and single network round trip to complete the TLS Handshaking process.
and in this way, TLS Handshaking is successfully done.
Please Note that :
A session key is only valid for a single session. i.e. if the client closes its connection(closes the tab or the browser or shuts down the computer), a new session key needs to be generated for the communication by repeating all the above steps.
we have discussed TLS version 1.2 here, not TLS Version 1.3 which is an optimized version of TLS 1.2. because the core fundamentals of TLS handshaking are best understood with a simpler version 1.2.
TLS 1.3 uses an advanced mathematical technique involving large prime numbers to reduce the network round trip from 2 to 1 during TLS handshaking. and generates a shared session key without transmitting the public key over the network.
TLS 1.3 doesn't support the RSA encryption algorithm.
And that's a wrap!
I hope you enjoyed this article and learned in detail about HTTP, HTTPS,TLS etc
We’ve come a long way from finding that little lock icon on your browser to learning behind the scenes of secure browsing. Who would have thought that a little icon could make such a huge impact on our online security?
So the Next time you when see that little lock icon, thank it for keeping your online world safe.
Subscribe to my newsletter
Read articles from Nikhil Pandey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nikhil Pandey
Nikhil Pandey
hie👋 I am Nikhil, I am a problem solver & software developer , I am interested in web development, web 3.0, productivity, entrepreneurship, self-help, people skills, and mental health. I am here to share all the learnings which I will be learning on the way.