API Security Risks and Best Practices to Mitigate Them
 Narola Infotech
Narola Infotech
APIs require robust security measures. Weaknesses in API security can expose sensitive data to theft, disrupt critical services, and tarnish a company's reputation.
In 2022, US companies collectively suffered losses ranging from $12 billion to $23 billion due to compromises associated with web application programming interfaces (APIs).
The protection of APIs is paramount for today's entrepreneurs to protect against possible breaches. The purpose of this blog is to guide you through the most common API security risks and how to implement practical best practices to safeguard your applications and data.
What is API Security?
In light of the fact that businesses are becoming more and more dependent on APIs for digital operations, API security is concerned with securing APIs from attacks and threats. Securing Application Programming Interfaces (APIs) is essential in order to prevent breaches in API security and to protect digital assets.
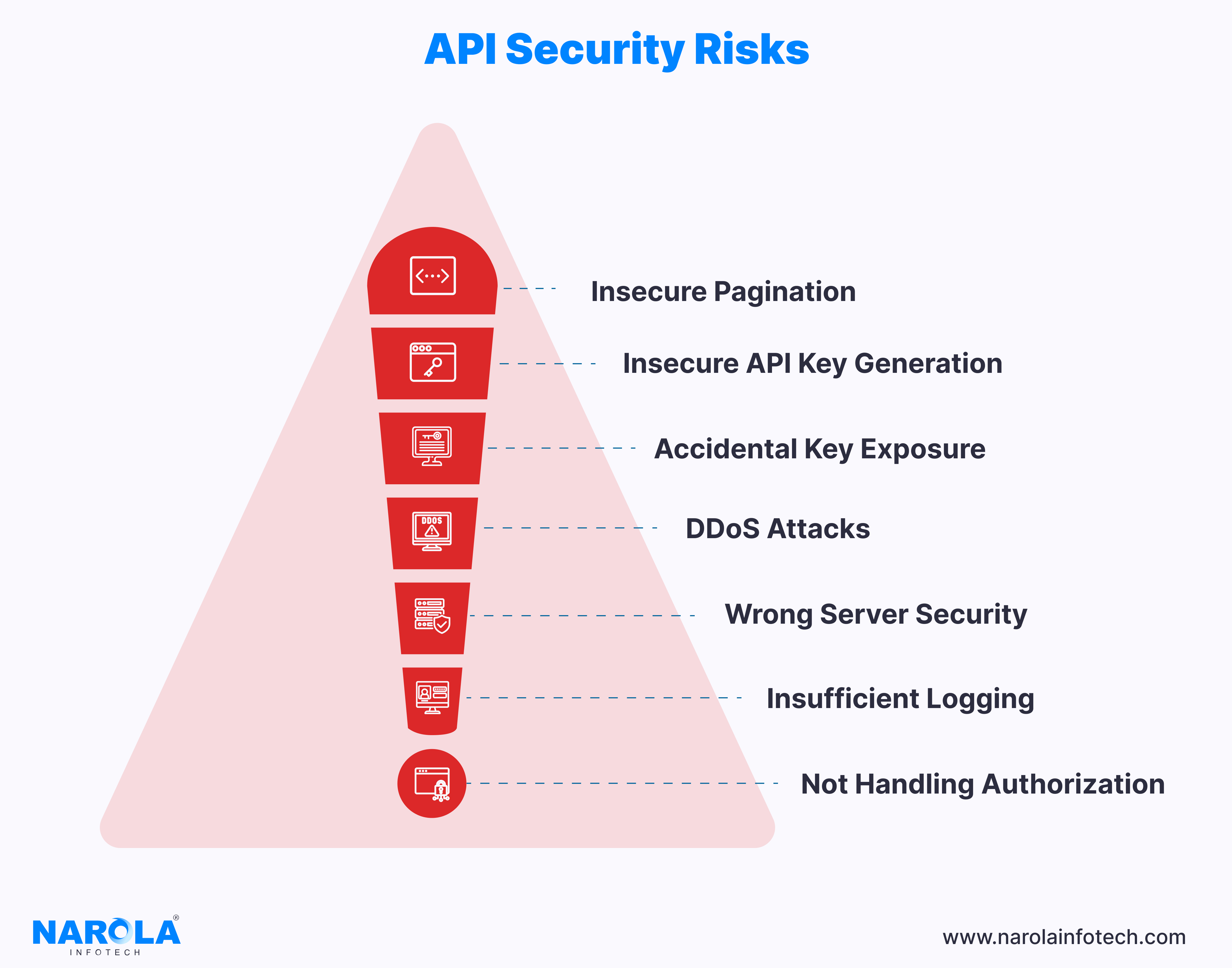
7 Key API Security Risks and Solutions
1. Insecure Pagination
Risk: Sensitive data may be exposed by insecure pagination in APIs beyond defined limitations, which may result in data leaks or illegal access to information.
Mitigation Strategy: Limit the number of entries delivered per page and validate pagination parameters to prevent manipulation. These are two examples of appropriate pagination controls that should be implemented in API responses. Make sure that cursors or pagination tokens are generated securely and are difficult to guess or tamper with.
2. Insecure API Key Generation
Risk: Poorly constructed API keys can make the API and the data it controls less secure by opening it up to brute force attacks or illegal access.
Mitigation Strategy: Use a secure technique to generate API keys, such as random number generators that are cryptographically secure. Strictly enforce the length and complexity criteria for keys. Rotate your API keys frequently, and quickly revoke access to any unused or compromised keys.
3. Accidental Key Exposure
Risk: Unauthorized access and possible data breaches may result from API keys that are inadvertently made public, such as when they are stored in publicly available repositories or included in client-side code.
Mitigation Strategy: Preferably, keep your API keys safe in environment variables or other secure storage options. Tokenization and OAuth are useful technologies to use instead of directly disclosing raw API keys. Teach developers how to handle API keys properly, and conduct routine code repositories audits to check for unintentional disclosure.
4. DDoS Attacks
Risk: Attacks such as Distributed Denial of Service (DDoS) have the ability to overload malicious traffic on API servers, resulting in downtime and service interruptions.
Mitigation Strategy: Put in place DDoS defenses including distributed traffic management systems, rate limitation, and traffic filtering. Use content delivery networks (CDNs) to counteract and absorb denial-of-service (DDoS) assaults. Track the patterns of API activity and use anomaly detection to find and stop such attacks before they happen.
5. Wrong Server Security
Risk: APIs may be vulnerable to a number of security flaws and attacks due to inadequate server security procedures, such as using antiquated software, improperly configured permissions, or insufficient authentication methods.
Mitigation Strategy: Update and patch server software on a regular basis to fix known vulnerabilities. Adhere to security best practices, which include putting in place robust access restrictions, enforcing secure coding standards, and using encryption for data that is both in transit and at rest. To find and fix security flaws, do routine penetration tests and security assessments.
6. Insufficient Logging
Risk: It can be difficult to notice and investigate security incidents due to inadequate logging of API activity, which makes it difficult to identify malicious conduct or unauthorized access.
Mitigation Strategy: Enable thorough recording of all API queries and answers, including with essential metadata such IP addresses, timestamps, and user IDs. Logs should be kept safely in unchangeable locations and should be periodically checked for questionable activity. Install alerting systems to instantly inform security professionals of possible security incidents.
7. Not Handling Authorization
Risk: When authorization measures in APIs are not handled correctly, sensitive data or functionality may be accessed by unauthorized parties, which may result in data breaches or misuse.
Mitigation Strategy: Control access to APIs and resources by putting strong authentication and authorization mechanisms in place, such as JWT, OAuth, or API tokens. To guarantee compliance and security, implement appropriate access controls based on user roles and permissions. You should also monitor and review authorization policies on a regular basis.
Best Practices for API Security to Avoid Data Compromise
1. Always Use a Gateway
A gateway is essential for API security. A gateway centralizes API requests, enforcing security policies like authentication, authorization, rate limitation, and traffic encryption.
By routing all API traffic through a gateway, companies may better monitor and regulate API access, ensuring only authorized clients and users can use the services.
2. Always Use a Central OAuth Server
Centralizing authentication and authorization with an OAuth server improves security. Clients receive access tokens from OAuth to access protected resources on behalf of users.
A centralized OAuth server can standardize API authentication, enforce access control regulations, and reduce security risks associated with decentralized authentication.
3. Only Use JSON Web Tokens Internally
Party claims can be represented securely using JSON Web Tokens (JWT). Internally using JWTs for authentication and authorization improves security by validating token integrity and claim authenticity.
JWTs should not be exposed directly to clients to avoid security risks. Install token validation and verification in your API architecture.
4. Use Scopes for Coarse-Grained Access Control
Scopes define coarse-grained API access control policies. Organizations can restrict resource and function access by allocating scopes to users or client apps based on roles and permissions.
This ensures that only authorized parties may access sensitive data or conduct privileged API functions, improving security. Scopes allow enterprises to establish a more granular access control approach, decreasing illegal access and data breaches.
5. Trust No One
To reduce insider and external threats, zero-trust security is important. In zero-trust environments, all requests—internal or external—are considered malicious.
Organizations use strict access restrictions, encryption, and authentication to verify parties' identities and integrity before providing resources or services. Organizations can better protect APIs from unauthorized access and exploitation by adopting a mistrustful posture and employing strong security measures.
6. Do Not Mix Authentication Methods
A safe API ecosystem requires authentication consistency. Using multiple authentication methods in the same environment can create security risks.
Instead, enterprises should use a solid authentication method like OAuth 2.0 and enforce it across all APIs and services. By simplifying authentication processes, companies can decrease authentication-related security risks and improve security.
Get Rid of Security Flaws and Make Your APIs Secure
Every firm should ensure that its APIs are as safe as feasible. It necessitates a proactive approach and a complete API security plan that includes technological solutions, training, collaboration, and ongoing audits. Fraudsters do not manually target your APIs; they use automation to carry out their harmful operations.
Subscribe to my newsletter
Read articles from Narola Infotech directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Narola Infotech
Narola Infotech
Narola Infotech is an IT Staff Augmentation services company in the USA. We deliver innovative software solutions that help thousands of entrepreneurs convert their vision into reality.