Building a CI/CD Pipeline for a Python Flask Quiz App on AWS with Terraform
 Rajeev Mishra
Rajeev MishraIntroduction
In this project, I'll walk you through the process of building a Continuous Integration and Continuous Deployment (CI/CD) pipeline for a Python Flask Quiz App hosted on AWS using Terraform. I'll cover containerizing the application, setting up secure infrastructure on AWS, implementing CI/CD with AWS CodePipeline, and incorporating monitoring and logging using AWS CloudWatch.
Synopsis
I chose to develop a Python Flask Quiz App and containerize it using Docker. The application is then hosted on AWS Elastic Container Service (ECS) behind an Application Load Balancer (ALB). I have utilized Terraform to create the necessary infrastructure, including VPC, subnets, security groups, ECS cluster, and ALB. The CI/CD pipeline is automated with AWS CodePipeline, triggering builds on code pushes and deploying updates to the ECS cluster. The CICD pipeline is also written using Terraform. I have written terraform scripts to create S3 bucket for CodePipeline artifacts, SNS topic for CodePipeline and CloudWatch Alarms notifications. CloudWatch Alarms, Dashboard and logs are also created using Terraform.
How Teams Will Work?
The DevOps engineers team will handle infrastructure provisioning using Terraform and set up the CI/CD pipeline with AWS services. The developers focus on coding the Flask app and writing Dockerfiles and pushing code changes to Application Code GitHub repo.
Prerequisites
Before we begin, make sure you have the following:
AWS Account
GitHub Account
Time to invest in learning
Basic Linux Knowledge
Basic Docker Knowledge
Knowledge of Terraform
Knowledge of Python Flask
Basic DevOps Knowledge including CI/CD process
Description About Tools Used
We utilized:
Python Flask for building the Quiz App.
Docker for containerization.
buildspec.yml file for the CodeBuild Project.
GitHub to host Application code and Terraform Scripts
Terraform for infrastructure as code, and AWS services including ECS, CodePipeline, and CodeBuild for CI/CD automation, SNS for pipeline and metric alarms notifications, CloudWatch for logging, monitoring, and visualization using CloudWatch Logs, CloudWatch Alarms, and CloudWatch Dashboard, ALB in front of ECS Cluster for serving the application.
Microsoft PowerPoint to create the Architecture Diagram.
Architecture Diagram
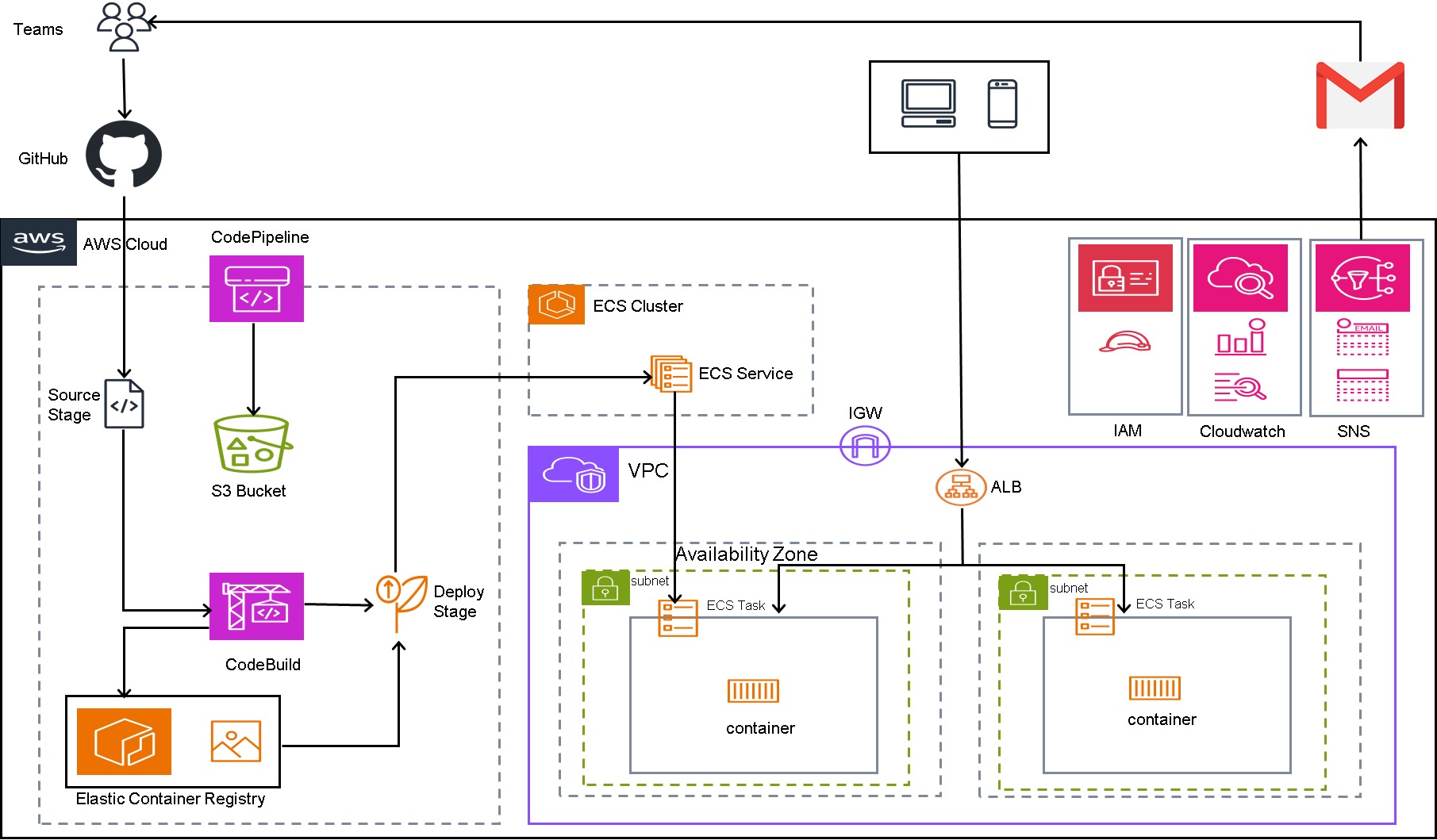
Step-by-Step Guide
Now, it's time to get our hands dirty with hands-on experience. As I mentioned before we are going to utilize the power of Infrastructure as code(IAC) using Terraform and Ansible. and you can access those repositories using the below link.
Application code: GitHub Repo
Terraform code: GitHub Repo
Steps:
Application Development: Develop the Python Flask Quiz App.
Containerization: Write Dockerfile to containerize the app.
Infrastructure Provisioning: Use Terraform to create VPC, subnets, security groups, ECS Cluster including Cluster, Task Definition and ECS Service, and ALB. Write scripts for SNS, CodePipeline, CodeBuild, IAM Roles, ECR , CloudWatch including CloudWatch Logs, CloudWatch Alarms, CloudWatch Dashboard.
a. Clone the Terraform GitHub Repo
b. Run terraform init
c. Run terraform plan -out=plan-name.tfplan
d. Run terraform apply --auto-approve
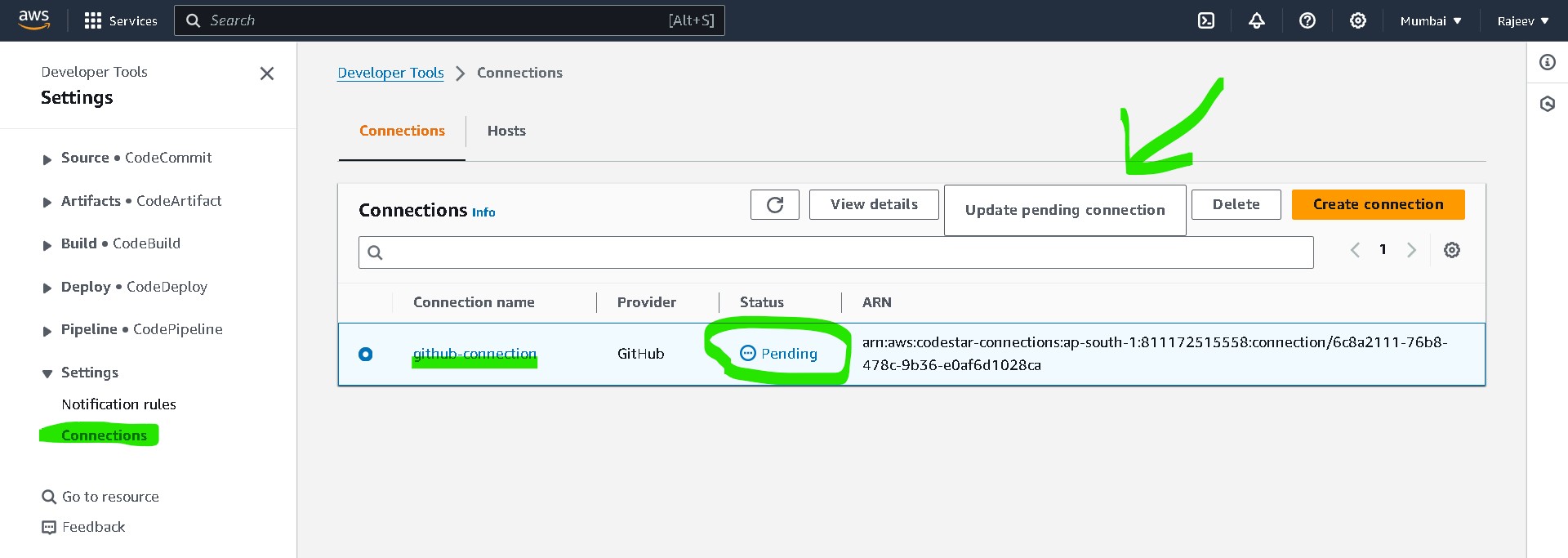
e. Once the Infrastructure Creation begins, you will have to update pending
connection between AWS CodePipeline and GitHub for the first time for
CodePipeline to be able to pull code from GitHub Repo.
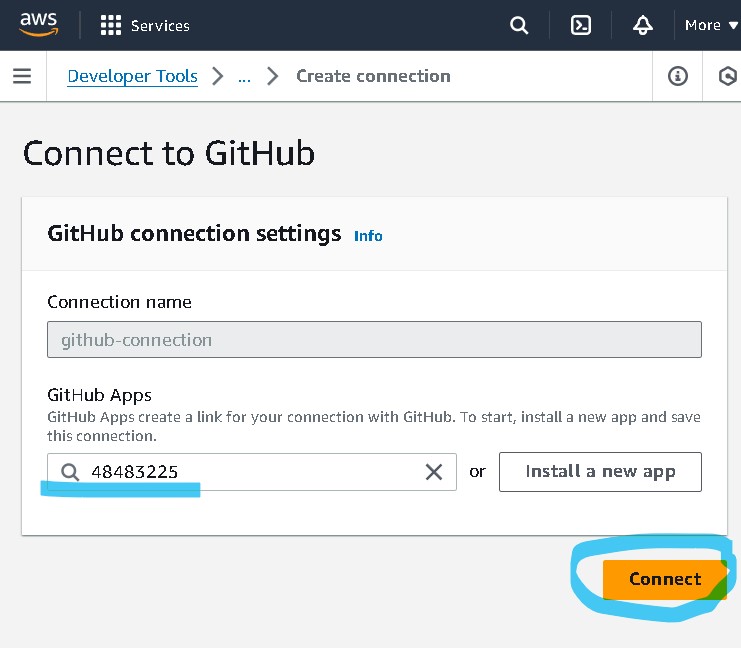
f. Go to AWS Console -> Developer Tools -> Settings -> Connections and update
the pending connection
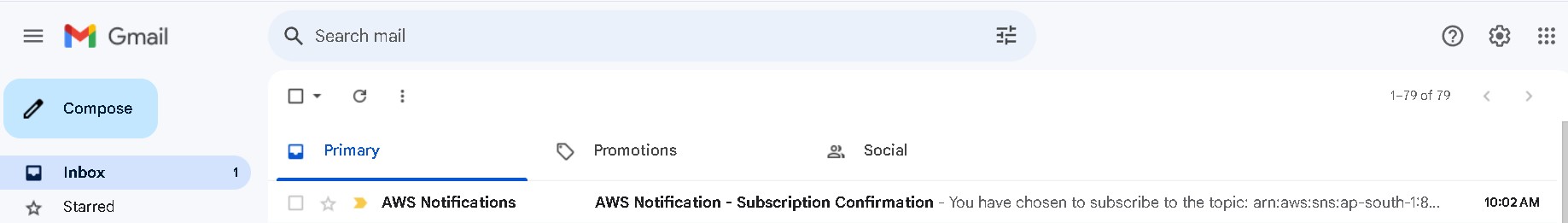
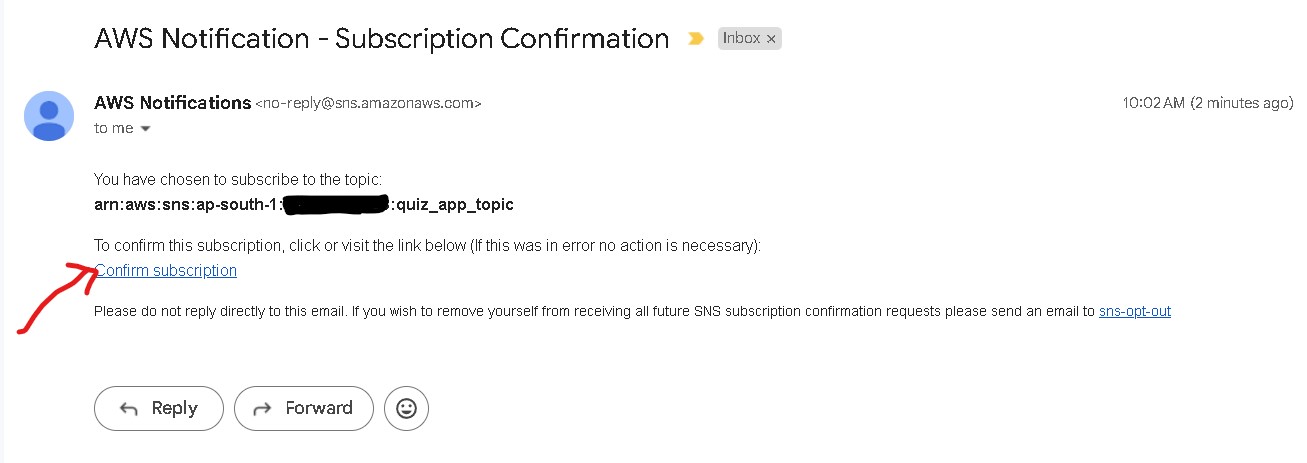
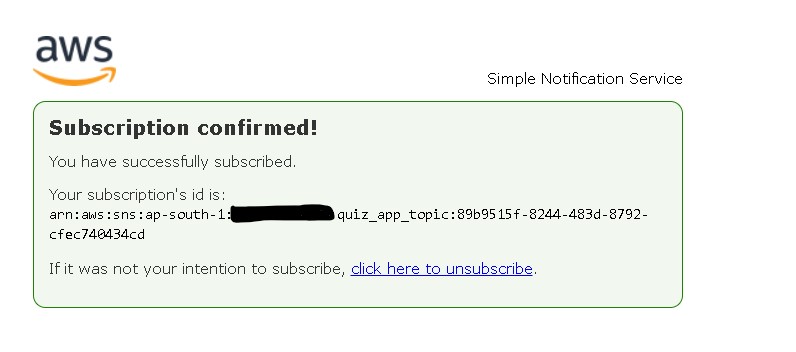
g. Go to your SNS topic subscription email and conform subscription.
Monitoring and Logging: Go to CloudWatch Dashboard to view the application metrics and CloudWatch logs to view logging for ECS cluster and CodeBuild project.
CICD Pipeline Verification: Push changes to Application code GitHub repo and check the CICD pipeline running.
Testing
After deployment, test the application using the ALB URL to ensure it's accessible and functioning as expected.
Resource Cleanup
Don't forget to clean up AWS resources to avoid unnecessary charges after completing the project. Use Terraform to destroy infrastructure resources created during the project.
Run terraform destroy
Future Improvements
While the current setup provides a solid foundation for deploying and managing the quiz application, there are several areas where enhancements and optimizations can be made:
Auto Scaling: Implement auto-scaling policies for the ECS cluster to dynamically adjust the number of running tasks based on traffic patterns. This ensures optimal resource utilization and better handling of fluctuating loads.
Container Orchestration: Consider using Amazon EKS (Elastic Kubernetes Service) for container orchestration. These managed services offer additional features and scalability options compared to ECS.
Enhanced Monitoring and Logging: Integrate additional monitoring tools like Prometheus and Grafana for advanced metrics visualization and alerting. Implement centralized logging solutions such as ELK stack (Elasticsearch, Logstash, Kibana) for comprehensive log management.
Security Enhancements: Consider implementing the following security features in future versions:
Secrets Management: Leverage AWS Secrets Manager to securely store and manage sensitive information such as database credentials, API keys, and encryption keys. Use Secrets Manager to rotate secrets automatically, reducing the risk of exposure due to stale credentials.
Key Management Service (KMS): Utilize AWS Key Management Service (KMS) to manage encryption keys for protecting data at rest and in transit. Implement encryption using KMS-managed keys for Amazon EBS volumes, Amazon S3 buckets, and AWS RDS databases to ensure data confidentiality and integrity.
Vulnerability Scanning: Integrate AWS Inspector into the CI/CD pipeline to perform automated security assessments and vulnerability scanning of the application and underlying infrastructure. Leverage Inspector's findings to identify and remediate security vulnerabilities proactively.
Container Image Security: Implement container image scanning using Amazon ECR (Elastic Container Registry) to detect and remediate security vulnerabilities and malware in Docker images. Utilize ECR's integration with third-party scanning tools or AWS-native solutions for continuous image scanning and monitoring.
Web Application Firewall (WAF): Deploy AWS WAF to protect the application against common web-based attacks such as SQL injection, cross-site scripting (XSS), and HTTP flood attacks. Configure WAF rules to filter and block malicious traffic, enhancing the security posture of the application.
DDoS Protection: Enable AWS Shield, a managed Distributed Denial of Service (DDoS) protection service, to safeguard the application from volumetric and application-layer DDoS attacks. Utilize AWS Shield Standard or AWS Shield Advanced depending on the level of protection and mitigation capabilities required.
Cost Optimization: Analyse resource usage and optimize costs by leveraging AWS Cost Explorer and Trusted Advisor. Utilize spot instances or reserved instances for cost-effective compute resources.
Automated Testing: Implement automated testing pipelines using tools like AWS CodeBuild and Jenkins to ensure code quality and application functionality before deployment.
Infrastructure as Code (IaC) Refinement: Refactor Terraform scripts to improve modularity, readability, and maintainability. Utilize Terraform modules for reusable infrastructure components.
Disaster Recovery: Develop and test disaster recovery strategies to recover data and services in case of outages or failures. Implement cross-region replication and backup solutions for data redundancy.
Continuous Improvement: Establish a feedback loop and regular review process to identify areas for improvement and optimization. Encourage collaboration between development, operations, and security teams to drive continuous improvement initiatives.
Conclusion
Building a CI/CD pipeline for my Python Flask Quiz App on AWS was an enlightening journey. I learned how to automate the deployment process, increase development speed, and ensure the reliability of our application. By leveraging tools like Terraform and AWS services, we've streamlined our development workflow and set a solid foundation for future projects.
Subscribe to my newsletter
Read articles from Rajeev Mishra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
