The zrok SOCKS Backend
 Michael Quigley
Michael Quigley
zrok provides a number of powerful tools for sharing private resources. In addition to our multiple flavors of proxy support, web hosting, low level TCP and UDP sharing, and network drives support, zrok now includes the ability to hide or alter your IP address.
zrok facilitates this type of privacy by layering on another type of tunneling callled SOCKS. SOCKS is a protocol that was developed in the mid-1990's, and according to Wikipedia "is a de facto standard for circuit-level gateways (level 5 gateways)."
The circuit/session level nature of SOCKS make it a versatile tool in forwarding any TCP (or UDP since SOCKS5) traffic, creating an interface for all types of routing tools. It can be used as:
A circumvention tool, allowing traffic to bypass Internet filtering to access content otherwise blocked, e.g., by governments, workplaces, schools, and country-specific web services.[13] Since SOCKS is very detectable, a common approach is to present a SOCKS interface for more sophisticated protocols:
Providing similar functionality to a virtual private network, allowing connections to be forwarded to a server's "local" network:
The zrok implementation of SOCKS (v5) allows you to split the sharing and access portions of the SOCKS tunnel between two different zrok environments. This means you can run a zrok share on a host in the cloud, or in some other location on the planet, and then use that share as a secure tunnel, allowing you to access the internet from that location.
In practice, it looks like this:
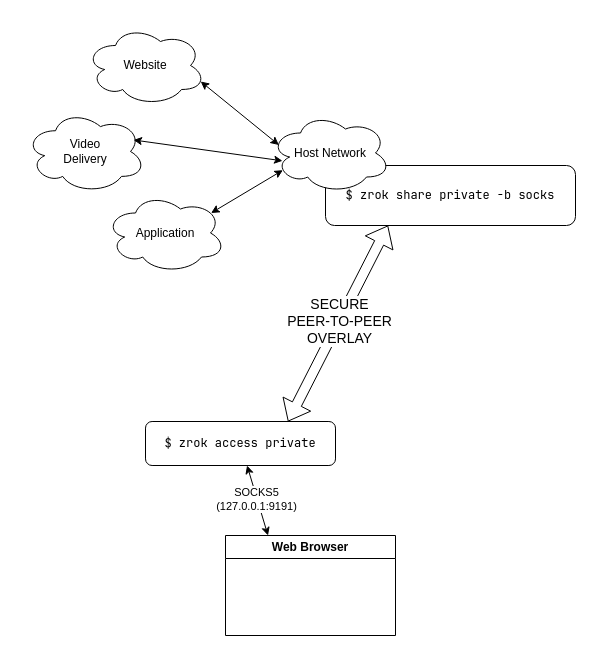
If the environment running the zrok share private -b socks were running on a host in Japan, and the zrok access private was running on a host in the United States, and the user's web browser (in the United States) is configured to use the local SOCKS access (on 127.0.0.1), then the end user will appear to be browsing from the host in Japan.
Like all zrok shares, the SOCKS share can be set up in seconds and removed just as easily when it is no longer needed.
All modern web browsers support SOCKS. There is tooling available for all modern operating systems that allow most applications to be "wrapped" with SOCKS, such that all of their network traffic can be intercepted and re-routed through the SOCKS proxy.
Here is a recent zrok Office Hours video that illustrates the socks backend in action:
Be aware that fully securing your traffic using SOCKS can be tricky in some cases. Modern web browsers allow you to configure a SOCKS host and also allow you to configure whether or not DNS resolution is also routed through SOCKS:
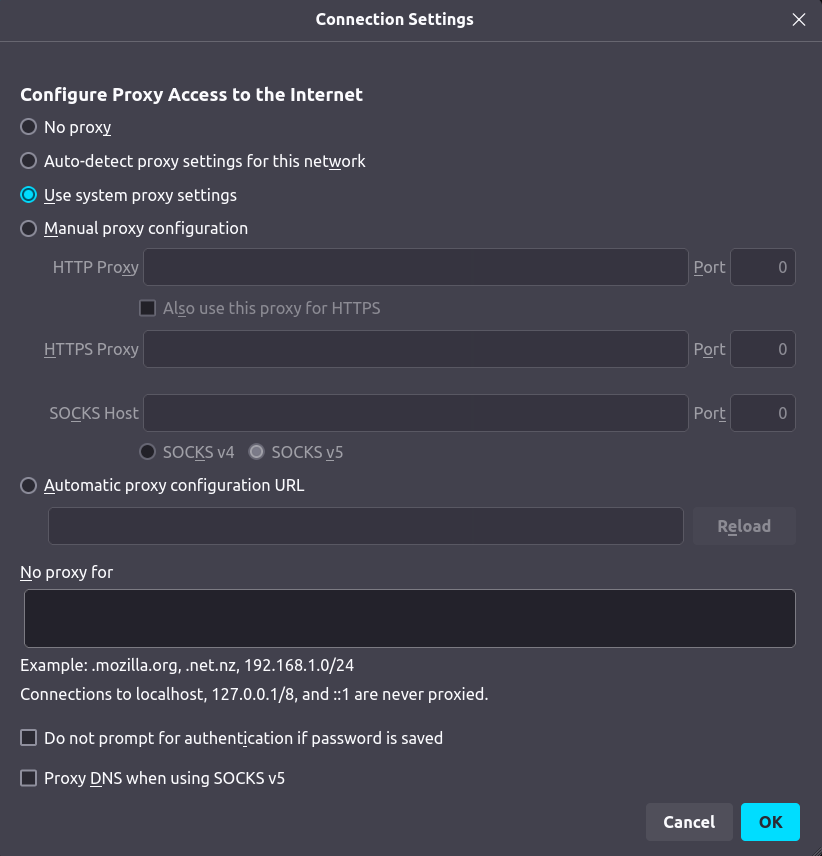
Notice that Firefox includes a checkbox to enable "Proxy DNS when using SOCKS v5". Like any security or tunneling solution, you'll want to be sure that you understand the implications of various configuration options and audit that they're working correctly in your environment.
This is the basic approach for creating and using the socks backend:
Create a zrok environment (using
zrok enable) on a host with network locality that you would like to share (in a foreign country, for example)In the environment with the remote network locality, run
zrok share private --backend-mode socks(consider adding--closed) to share that network locality as a SOCKS shareEnsure that your local environment (where you want to access the remote network locality) is enabled using
zrok enableRun
zrok access private <token>in your local environment.<token>is given to you from thezrok share privatecommand above and can also be retrieved from the zrok web consoleBy default, the
zrok accesscommand above will create a SOCKS listener at the address127.0.0.1:9191. Use that address to configure your web browser (ortsocks, or SocksCap) to enable to SOCKS-based connectivity
There are numerous inexpensive VPS and VM solutions that would be very effective for siting a zrok share private -b socks SOCKS share. This is a simple way to locate your network access on a different host on the internet. A lot of VPS and VM providers allow you to allocate a host for a short period of time, and then dispose of it when you no longer need it. Kind of a "burner phone" for the internet.
The shared zrok infrastructure in your self-hosted environment, or on zrok.io has no way to observe your actual traffic. That traffic is all end-to-end encrypted through the OpenZiti overlay. zrok is just acting as a secure transport.
If you run into any issues or need assistance, feel free to reach out on the the OpenZiti Discourse. There's a great community there to help you.
It always means a lot to the folks working on zrok when you're take a minute to drop a star on the zrok's GitHub repository. It helps us to know that the work we're doing on zrok is important to you.
Subscribe to my newsletter
Read articles from Michael Quigley directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
