Cybersecurity in Centralized Vs. Decentralized Computing
 Spheron Network
Spheron Network
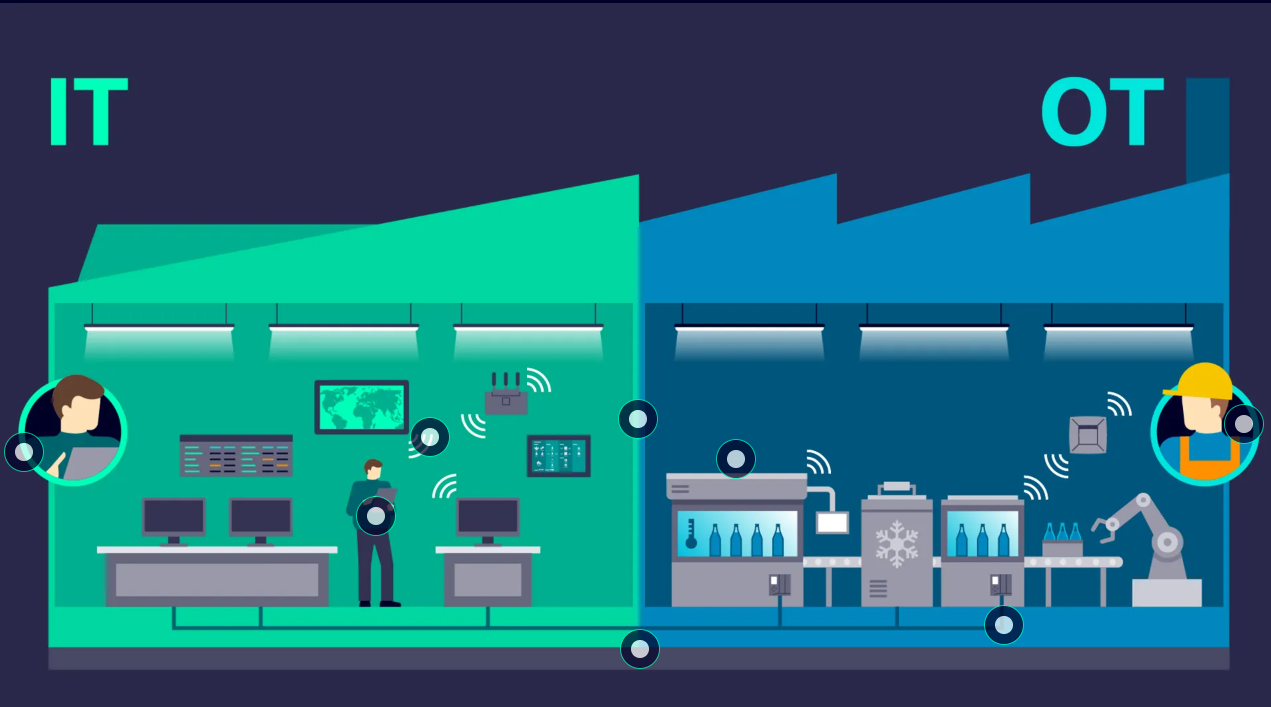
In the early stages of using computers in industrial settings, their requirements were minimal. However, today, data generation has increased exponentially with the widespread use of IoT devices in numerous industries. Such an abundance of data requires massive computing power, which can only be achieved by deploying large central or multiple distributed systems. However, these systems come with significant cybersecurity implications. Before delving into the cybersecurity implications associated with various computing systems, it is crucial to understand the fundamental difference between operational technology (OT) and information technology (IT) in the IoT realm.
Operational Technology vs. Informational Technology (OT vs. IT)
The distinction between Operational Technology (OT) and Information Technology (IT) is clear and crucial for the proper functioning of a manufacturing plant. OT pertains to the operational side of a facility, which includes hardware and software used to control and monitor processes. It includes devices such as SCADA, PLCs, sensors, and other equipment that perform pre-programmed actions to achieve desired outcomes in plant operations.
In contrast, IT manages data and information flow and provides supporting technology for industrial operations. This involves a range of hardware and software, from email services to manufacturing execution systems (MES). Although not always critical to plant operations, IT systems can significantly enhance plant operations by improving efficiency.
Centralized vs. Decentralized Computing
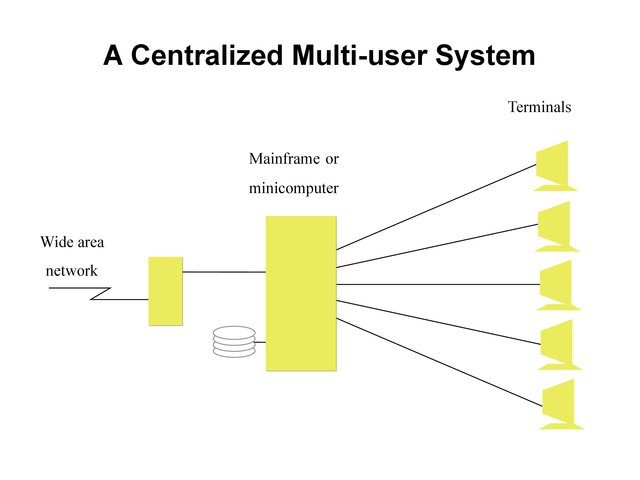
The world's network systems have traditionally been centralized, with a single server acting as the central node for storing, processing, and routing information across the entire network. This model allowed authorized users and devices to access data from the central server. However, this outdated model has now been replaced by decentralized computing systems.
In decentralized computing systems, there is no central server; instead, there are interconnected clusters with a node at their centers. These nodes are connected, and computing power is spread across multiple nodes, making it a more efficient operation model. Furthermore, the possibility of a fault taking down the entire system is minimal.
Distributed computing is an extension of decentralized computing, where all devices have computing capabilities and are connected through a mesh network. This architecture offers a more resilient computing system but comes at a higher cost.
| Feature | Centralized Computing | Decentralized Computing |
| Control | A single entity controls all resources and data | No single entity controls all resources and data |
| Data Storage | Data is stored in a central location | Data is distributed across multiple locations |
| Security | Security is the responsibility of the central authority | Security is distributed among participants |
| Scalability | Scales well for large amounts of data and users | Scales better for small to medium amounts of data and users |
| Cost | Higher cost due to centralized infrastructure and maintenance | Lower cost due to lack of centralized infrastructure |
| Fault Tolerance | A single point of failure can bring down the entire system | Redundancy and distribution reduce the risk of single points of failure |
| Privacy | A single entity controls user data | User data is encrypted and distributed, reducing exposure |
| Accessibility | Users must access the central server to use the network | The network can be accessed from anywhere with an internet connection |
| Censorship Resistance | Easier for governments or other entities to censor or shut down | More difficult for governments or other entities to censor or shut down |
| Consensus Algorithm | Not necessary for centralized systems | Required for decentralized systems to ensure consistency and security |
| Smart Contracts | This is not possible without a decentralized architecture | Possible with a decentralized architecture |
Cybersecurity Challenges in Computing
Industrial systems face an alarming increase in cybersecurity threats, as evidenced by recent attacks on critical national infrastructure. Hackers have shown their capability to hold entire pipelines at ransom. It is imperative to consider protection against cyberattacks for every computing system used with automation and IoT.
In a centralized computing model, the central server is the primary vulnerability. If it is compromised, the entire system goes offline, and operations can halt. A single point of attack can bring down the entire system. Therefore, it is crucial to prioritize protecting the central server.
On the other hand, in a decentralized and distributed model, the attack vector is much wider. Even if one of the nodes or devices is compromised, the rest of the system can remain operational. However, if a security breach goes undetected, malware can spread across the network and infect all nodes and devices.
IoT has also transformed the cybersecurity landscape for industrial systems. The centralized model in IoT architecture uses central servers, and the distributed model relies on edge computing. All devices are connected to the Internet and have some data processing capabilities, increasing hackers' potential attack vectors. Therefore, following the best cybersecurity practices is crucial to safeguarding critical infrastructure in every architecture.
Cybersecurity Best Practices
Industrial systems are increasingly at risk from attacks by sovereign opponents and malicious hackers. Implementing strong defense systems is the only way to protect against such attacks effectively. Fortunately, the National Institute of Standards and Technology (NIST) and the International Society of Automation (ISA) have established comprehensive guidelines and standards for cybersecurity in the industrial sector. To build a truly resilient ICS, companies must follow these best practices.
Enhancing Industrial Cybersecurity: Focus on Firewalls, Encryption, and Redundancy
Industrial networks face continual threats from cyberattacks, making robust security measures imperative. Firewalls, comprising hardware and software components, form the primary defense line, monitoring and regulating data flow based on predefined rules. Trusted vendors' proven firewall implementations are essential for any Industrial Control System (ICS) deployment.
Encryption is pivotal in safeguarding data integrity, particularly against data exfiltration attempts. By encrypting all network communications, sensitive information remains protected even if intercepted. This additional layer of security is crucial for thwarting cyber threats.
Integrating redundancy into systems bolsters resilience, ensuring uninterrupted operations. Regular backups, stored centrally and replicated across diverse locations, mitigate the impact of cyberattacks by facilitating swift data restoration.
Emphasizing Passwords, Authentication, and Security Maintenance
Weak passwords pose a significant vulnerability, often exploited by hackers. Eliminating default passwords and adopting strong, corporate password management solutions is essential. Implementing two-factor or multi-factor authentication further fortifies network security.
Cybersecurity is an evolving landscape, necessitating prompt application of software updates and patches from device manufacturers. Selecting vendors committed to regular updates is paramount for maintaining up-to-date protection.
Security audits conducted by external agencies offer insights into a company's cybersecurity posture. Through techniques like penetration testing, these audits identify vulnerabilities, allowing for targeted improvements and enhancing overall cyber resilience.
Cybersecurity measures must continuously adapt to evolving threats, reflecting the ongoing efforts of industries to mitigate emerging attack vectors.
Subscribe to my newsletter
Read articles from Spheron Network directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Spheron Network
Spheron Network
On-demand DePIN for GPU Compute