The Ultimate Guide to AWS Global Infrastructure and IAM: Everything You Need to Know
 Gopinath J
Gopinath J
Global Infrastructure:*
AWS (Amazon Web Services) has a global infrastructure across multiple geographical locations around the world. Each region is a separate area, and each region has multiple Availability Zones (AZs).*
Region:
A region is a large geographic area that has multiple Availability Zones.
Availability Zones:
An AWS region consists of many Availability Zones (AZs), each of which contains a collection of data centers. Each Availability Zone has its own cooling, power, and network infrastructure.
Edge Locations:
Edge locations are places used by the CloudFront Content Delivery Network (CDN) to cache content closer to user locations, reducing latency and improving performance.
Identity and Access Management
IAM — Identity and Access Management is used to control access to AWS resources.
IAM uses the following to manage AWS resources:
Policy: Policies are permissions for the resources that individuals or groups have access to. IAM policies are JSON documents used to define permissions.
Users: Users are individuals or employees who need access to AWS resources.The root user creates separate users and assigns them policies (permissions). Policies specify the resources that users have access to. Users have their security credentials, which allow them to log in to their AWS console. These security credentials are created by the root user.
For example*, when a user is assigned a policy (e.g., s3FullAccess), the user can create, list, and delete the S3 bucket. However, the user cannot create an EC2 instance as they do not have access to it.*
Role: An IAM role is similar to an IAM user, but with permission policies that determine what an identity can and cannot do in AWS. Users use long-term credentials like passwords or access keys, but roles are short-term. When a role is assumed (temporarily taking permissions), it provides temporary security credentials to access resources.
For example*, suppose you have an EC2 instance that does not have access to a particular S3 bucket. In that case, you can define the EC2 to access S3 by setting the role to it, allowing the EC2 to access the S3 bucket.*
Group: Groups are collections of users with specific policies (permissions).
For example*, when the root user wants to create 50 users with the same policy, it is time-consuming to create each user and allocate their policies. Instead, the root user can create a group and assign the policies to that group. Then, the root user can add users with the same policies to the group. If the root user wants to create a group for developers and assign them permission to create two EC2 instances, they can create a group and add all the developers to it.*
Create Policy :
1. Go to aws console → search IAM
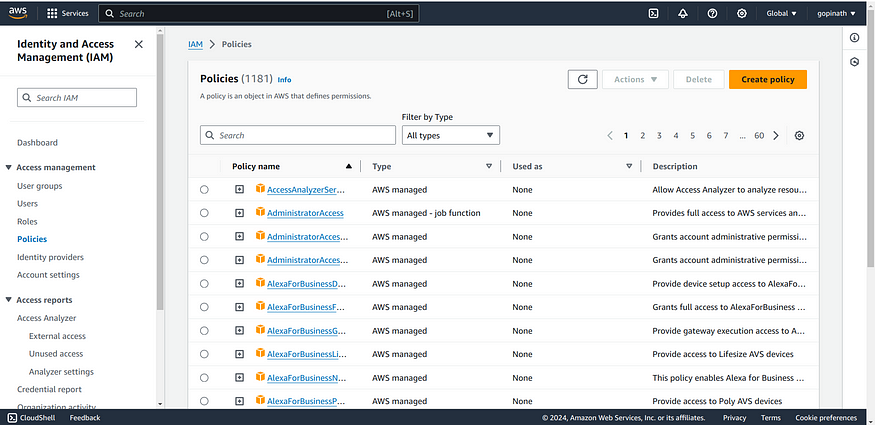
2. Click create Policy
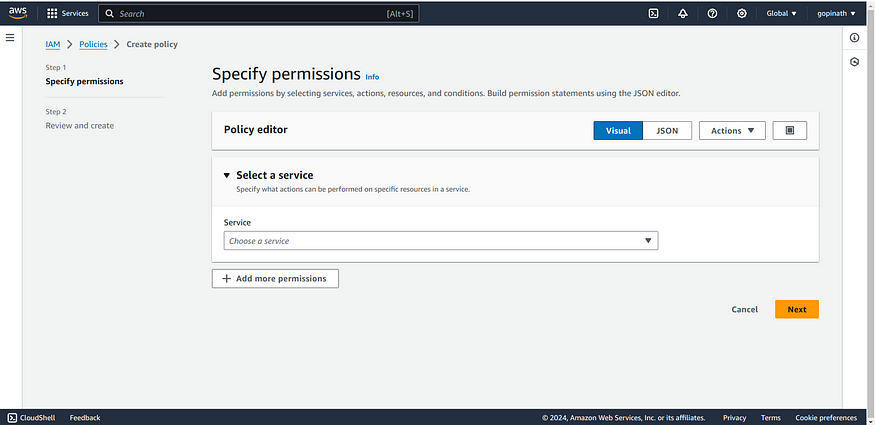
Choose the service to which you want to define the permission
3. In my case , I have selected s3.
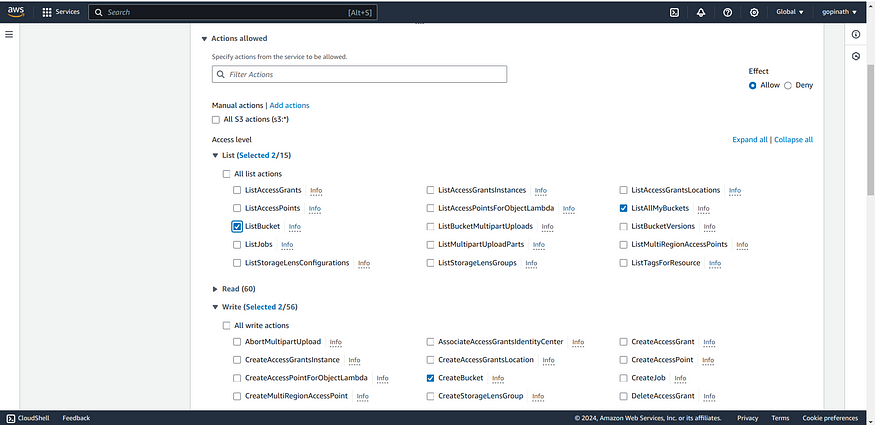
Choose the access level for the service. In my case , I have selected listBucket,Create and Delete Bucket.
4. Specify Resources and Request conditions
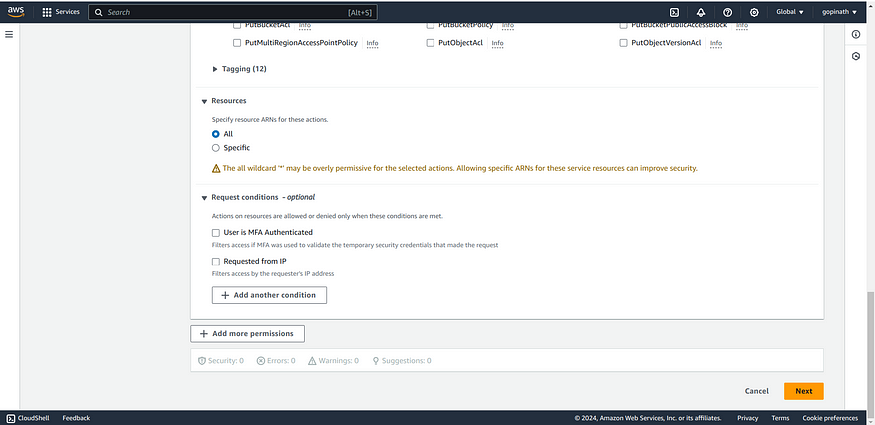
Resources — The Resource element defines the AWS resources to which the policy applies.
For example*, you can choose a specific S3 bucket and apply the policy to that bucket*
Request Conditions — Allows to access resources only if the conditions are met.
User is MFA Authenticated — Allows only if the user complete Multi Factor Authentication.
Requested from IP — Allows only if the request is from specified IP.
Now, Click on Next.
5. Give a proper name for the policy and the description if needed.
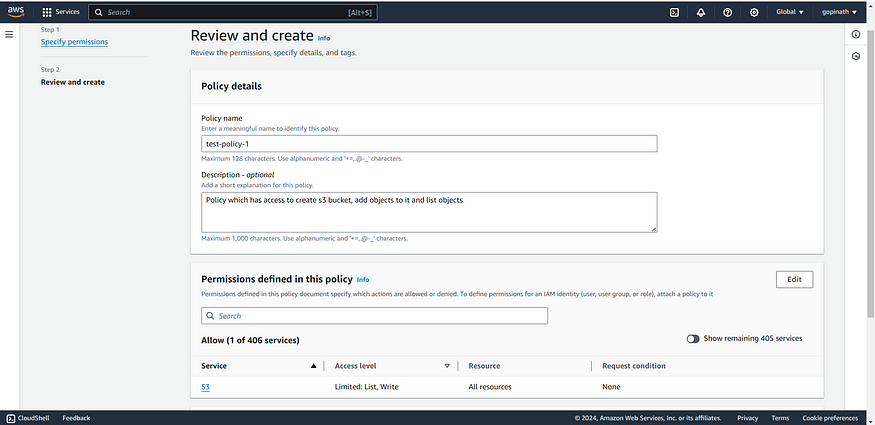
6. Click create policy and the policy will be created.You can see the policy in policy tab of IAM.
Create Group:
- Go to IAM -> User Groups
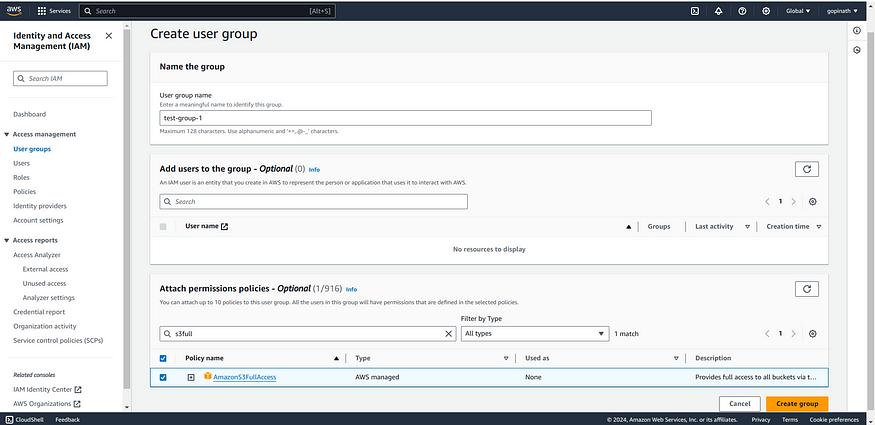
create user group
i) Give the group name and add users if already present.
ii) Selected the policy we have created
iii) Finally click the create group.
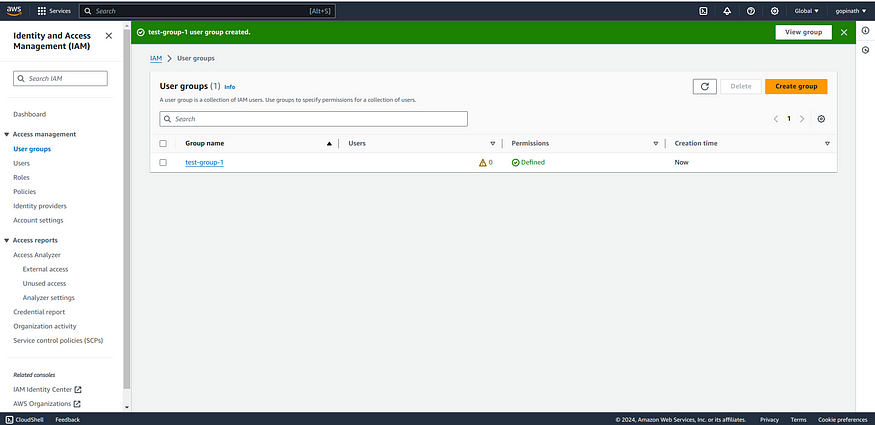
2. View the created group in User groups section
Create Users :
Go to IAM -> Users
Give user name and click
I want to create an IAM user.
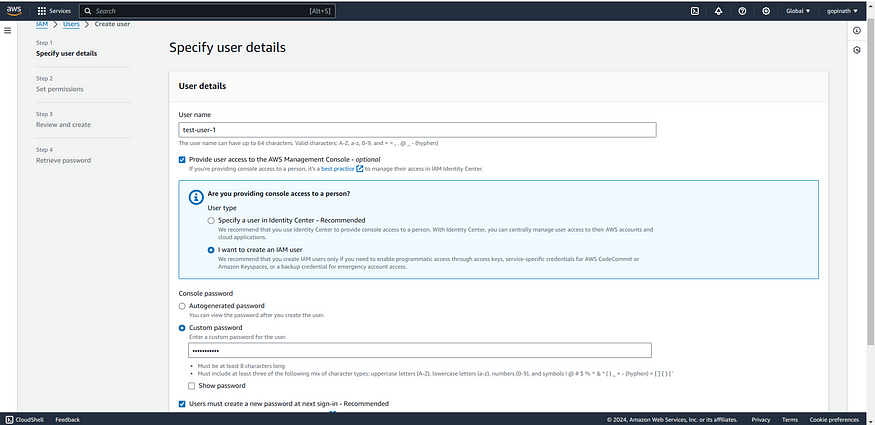
3. You can shoose auto generate password or can give custom password.
4. Click the checkbox of user to create new password so when the user sign in for the first time it asks to create new Password.
5. Select the permission (policy) for th group

Permission can be set in three ways :
i) Add user to group — Creating a group and adding policy to it (Like we have done now)
ii) Copy Permission — Copy permissions from already created policies
iii) Attach Policies Directly — Policies can also be attached directly to the user.
In out case, We have added the user to the group that we created.
6. Review the User Details and Permissions.
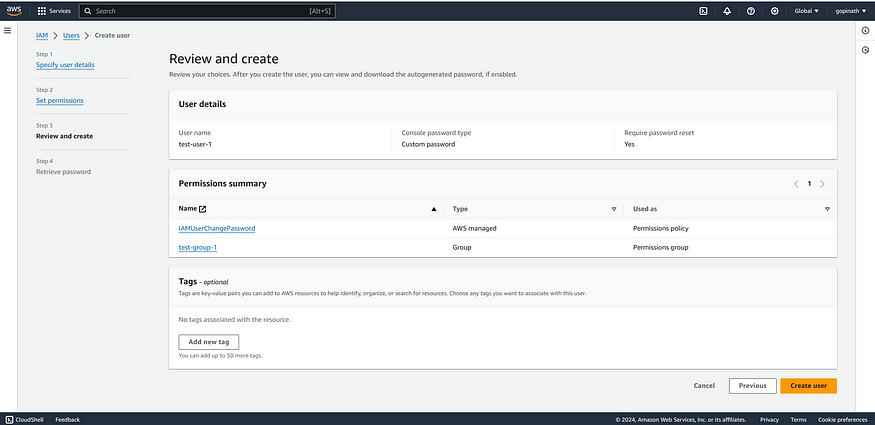
Tags — Tags can be used for organising and managing users based on specific criteria.
7. You can download the csv file. It has all the informations for signing in IAM user.
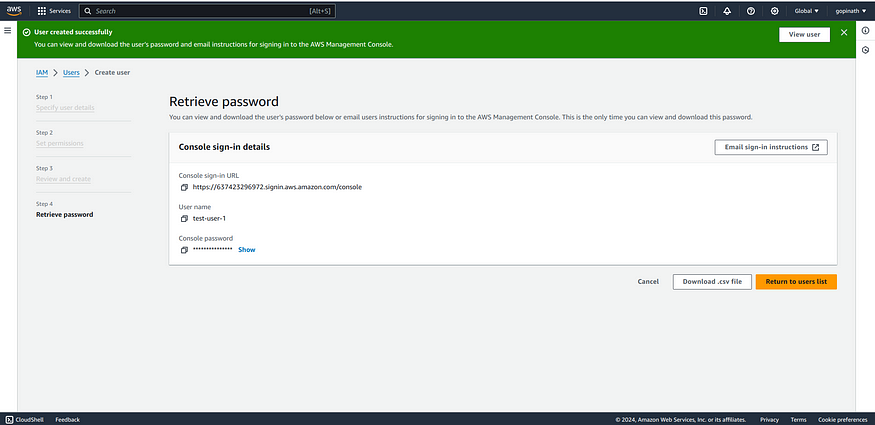
Login using Created User :
- Go to aws login → Click IAM user -> Enter the 12 digit code present int the console sign-in URL.
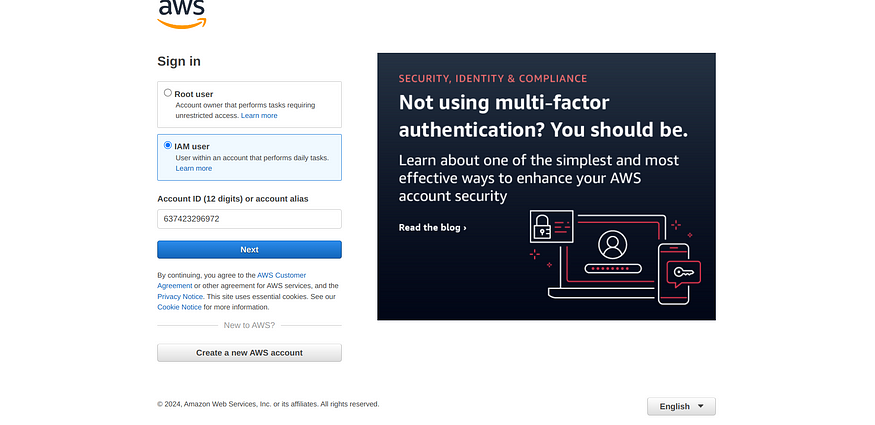
2. Click Next,
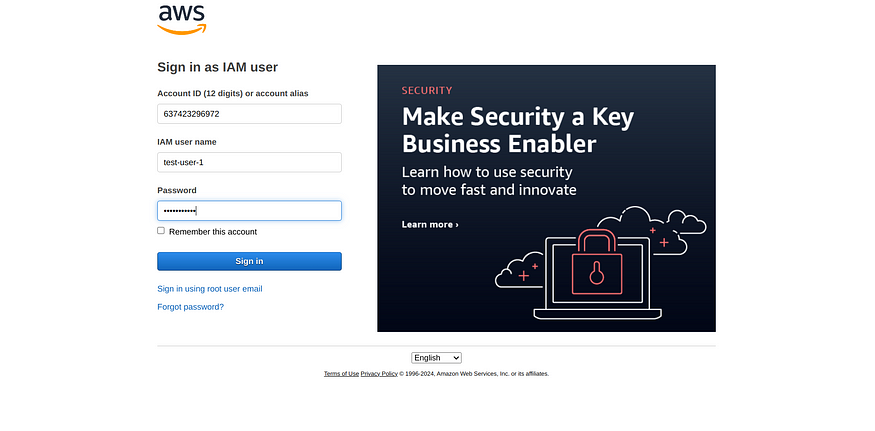
2.1) Enter the IAM username and Password.
3. It will ask for new Password as we clicked the check box of ask new Password for the first time while creating the user.
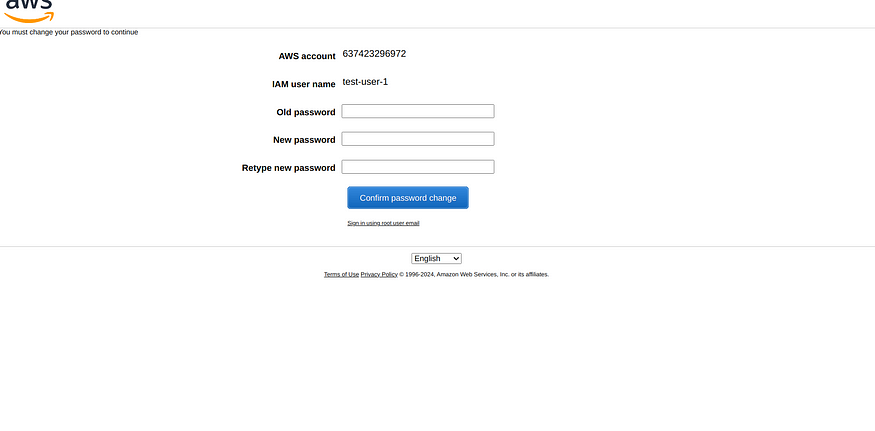
4. Now the User can access the aws console.
5. The User can access the resources for which the permissions are granted.
Conclusion :
In conclusion, AWS Global Infrastructure ensures high availability and low latency for all the applications through regions, availability zones, and edge locations.AWS IAM enables the least privilege, which ensures that users and applications have permissions to access only specific resources.
Subscribe to my newsletter
Read articles from Gopinath J directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
