Deciphering Access Tokens and Refresh Tokens: A Developer's Guide
 Firoj K. Timalsina
Firoj K. Timalsina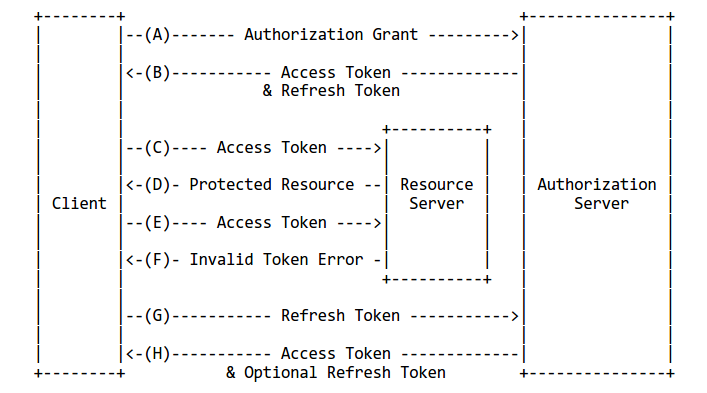
In the world of web development and API authentication, access tokens and refresh tokens play a crucial role in ensuring secure and seamless interactions between clients and servers. Understanding how these tokens work and their significance is essential for developers building modern web applications. Let's dive into the realm of access tokens and refresh tokens to demystify their purpose and functionality.
What are Access Tokens ?
Access tokens are like golden tickets that grand permission to access protected or secured resources on a server. They are typically short-lived and are issued by an authentication server after successful user authentication. These tokes carry information about the user and their permissions, allowing clients to make authorized requests to protected APIs or resources.
How Do Access Tokens Work?
When a user logs into an application, the authentication server verifies their credentials and generates an access token. This token is then sent to the client, usually in the form of JSON Web Token(JWT). The client includes the access token in suceeding requests to the server, typically in the Authorization header or cookies. The server validates the access token and grants access to the requrested resources if the token is valid and the user has the necessary permissions.
The Role of Refresh Tokens
While access tokens provide short-term access to resources, they have a limited lifespan for security reasons. Refresh tokens come to the rescue by providing a means to obtain new access tokens without the hassle of logging in again. When an access token expires, the client can use a refresh token to obtain a fresh access token from the authentication server. This process helps maintain the user's session without the hassle of frequent logins.
Best Practices for Handling Tokens
To ensure the security of your application, it's essential to follow best practices when handling access tokens and refresh tokens:
Use HTTPS*:* Always transmit tokens over secure HTTPS connections to prevent interception by malicious actors.
Keep Tokens Secure: Store tokens securely on the client-side and avoid exposing them in URLs or logs.
Implement Token Expiry: Set approximate expiration times for access tokens and refresh tokens to minimize the window of opportunity for unauthorized access.
Roate Refresh Tokens: Periodically rotate refresh tokens to mitigate the risk of token theft and unauthorized access.
Access tokens and refresh tokens are indispensable tools in the realm of modern web development, enabling secure authentication and authorization mechanisms. By understanding how these tokens work and following best practices for their usage, developers can build robust and secure applications that protect user data and privacy. So, embrace the power of tokens, and unlock a world of secure possibilities in your web development journey.
Subscribe to my newsletter
Read articles from Firoj K. Timalsina directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Firoj K. Timalsina
Firoj K. Timalsina
Self taught developer based in Hetauda, Nepal.