Phishing attack imitates US Department of Labor
 The Watcher
The Watcher
In January 2022, an advanced phishing scheme was reported aimed at obtaining Office 365 credentials by impersonating the US Department of Labor. This incident highlights the increasing sophistication of phishing efforts.
The attack used two methods to impersonate the DoL’s email address—spoofing the actual DoL email domain (reply@dol[.]gov) and buying up look-a-like domains, including:
dol-gov[.]com
dol-gov[.]us
Using these domains, the phishing emails sailed through the target organizations’ security gateways.
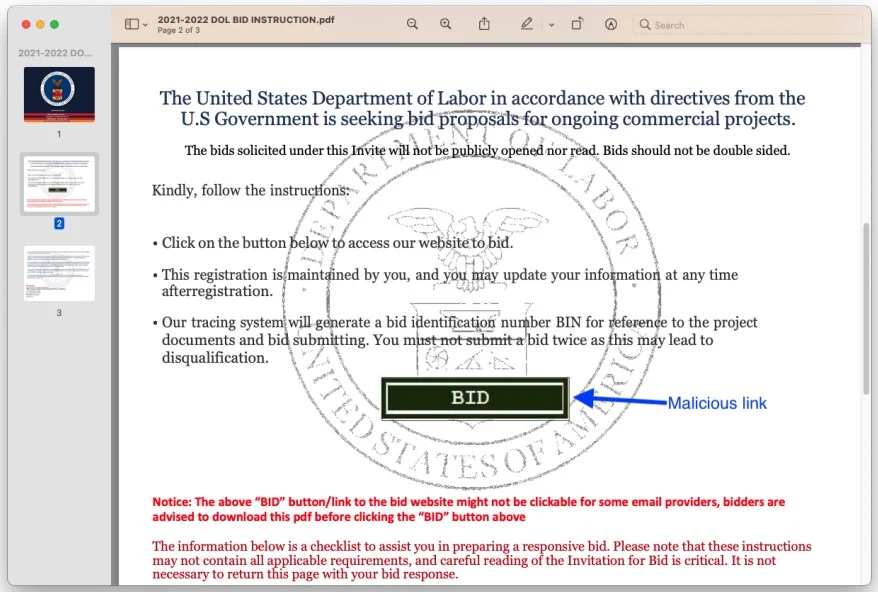
The emails, featuring official Department of Labor branding and professionally crafted content, invited recipients to submit bids for a government project. Detailed bidding instructions were provided within a three-page PDF document, which included an embedded "Bid Now" button.
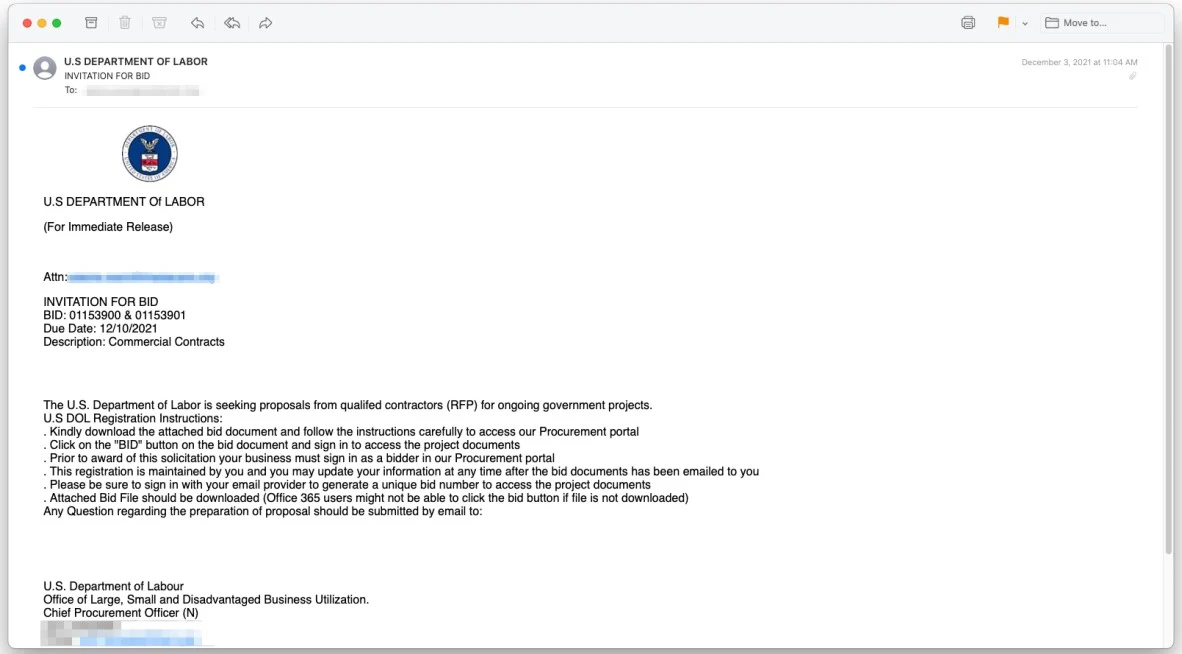
The emails contain a valid letterhead, professionally-arranged content, and a three-page PDF attachment of a seemingly legitimate form.
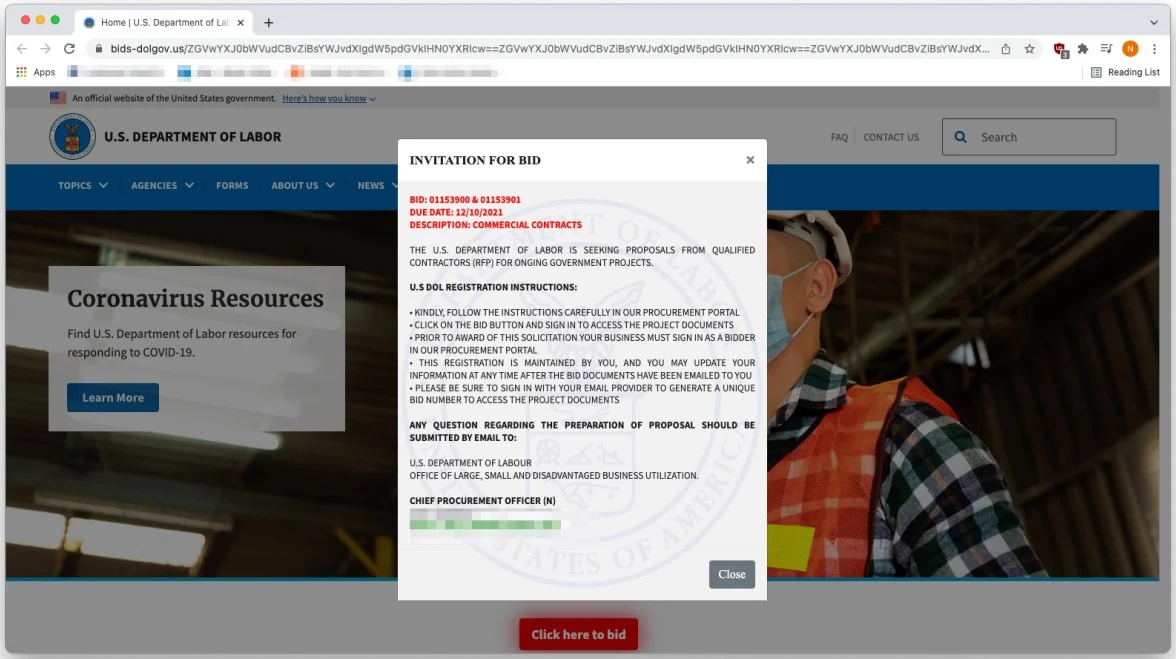
Upon clicking the link, individuals were taken to a phishing website that closely mimicked the real Department of Labor site, located at a deceptive URL like bid-dolgov[.]us. This counterfeit site prompted users to input their Office 365 login details. Furthermore, an "error" notification was shown after the initial entry, prompting users to input their credentials a second time, thereby minimizing the chances of errors in typing.
Individuals attempting to bid on a project will be directed to a form designed to collect their Microsoft Office 365 email address and password.
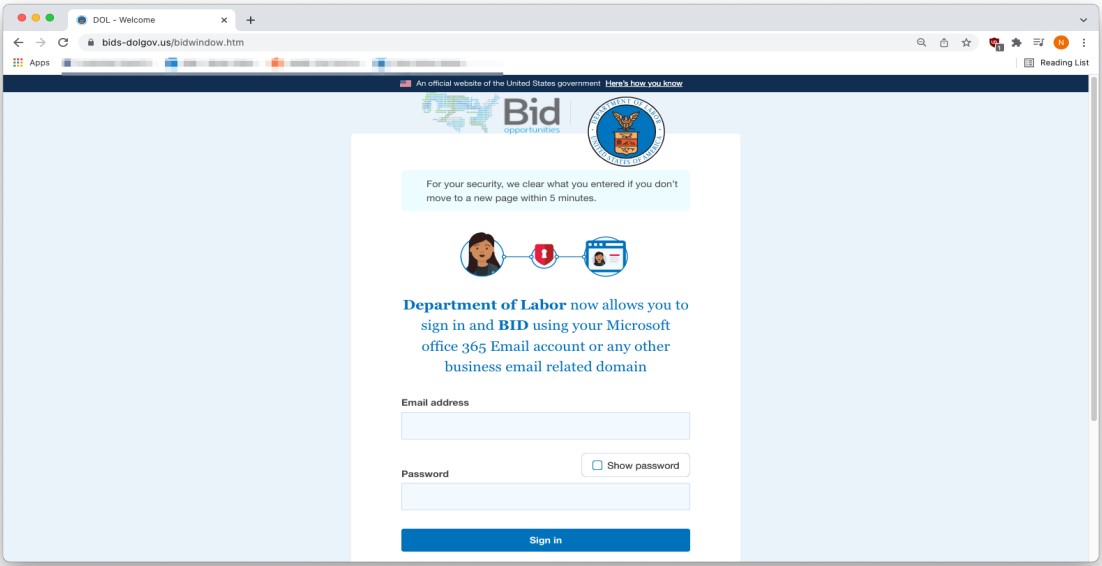
Regardless of the information entered, the site displays a fake error message to deceive the victim into submitting their credentials again, thereby lowering the risk of capturing incorrectly typed information.
Should the victim be deceived a second time, they are subsequently redirected to the legitimate Department of Labor website, leaving them with minimal clues about the incident that transpired.
Subscribe to my newsletter
Read articles from The Watcher directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
