Address Resolution Protocol (ARP) Explained
 Maxat Akbanov
Maxat Akbanov
The Address Resolution Protocol (ARP) is a communication protocol used for discovering the link layer address, such as a MAC (Media Access Control) address, associated with a given internet layer address, typically an IPv4 address. This protocol operates between the network layer and the data link layer in the OSI model, enabling devices on a local network to communicate with each other.
How ARP Works:
ARP Request: When a device (let's say, Device A) wants to communicate with another device on the same local network (Device B) but only knows Device B's IP address, it broadcasts an ARP request onto the network. This request essentially asks, "Who has IP address X? Please send your MAC address to me."
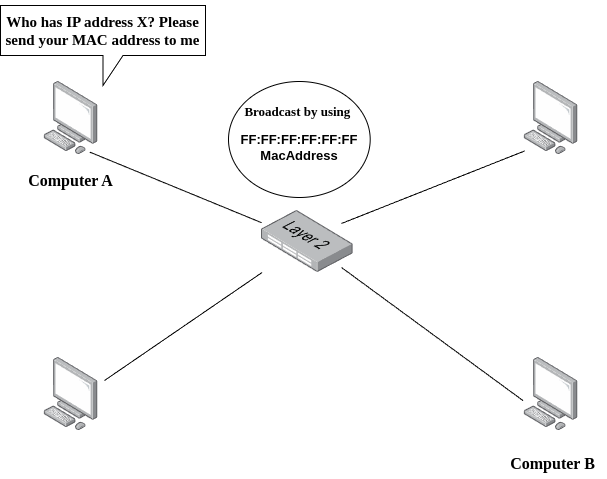
Broadcasting: The ARP request is broadcast to all devices on the local network because Device A does not know the MAC address of Device B. It uses a special MAC address (FF:FF:FF:FF:FF:FF) that prompts all devices on the network to process the ARP request.
ARP Reply: If a device on the network (in this case, Device B) recognizes its IP address in the ARP request, it sends back an ARP reply. This reply contains Device B's MAC address and is sent directly to Device A using Device A's MAC address, which was part of the ARP request.
Updating ARP Cache: Once Device A receives the ARP reply from Device B, it updates its ARP cache, a table where IP-to-MAC address mappings are stored for quick reference. This cache reduces the need to broadcast ARP requests for IP addresses that have already been resolved.
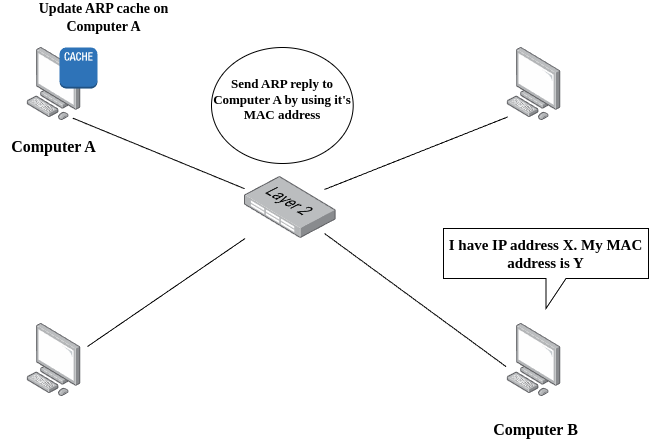
Communication: With the MAC address of Device B known, Device A can now frame packets addressed to Device B's MAC address for direct communication on the local network.
Security Considerations:
ARP does not include any form of authentication, making it susceptible to various attacks, such as ARP spoofing. In an ARP spoofing attack, an attacker sends fake ARP messages onto the network, linking their MAC address with the IP address of another device on the network (often the default gateway). This can lead to the interception of data.
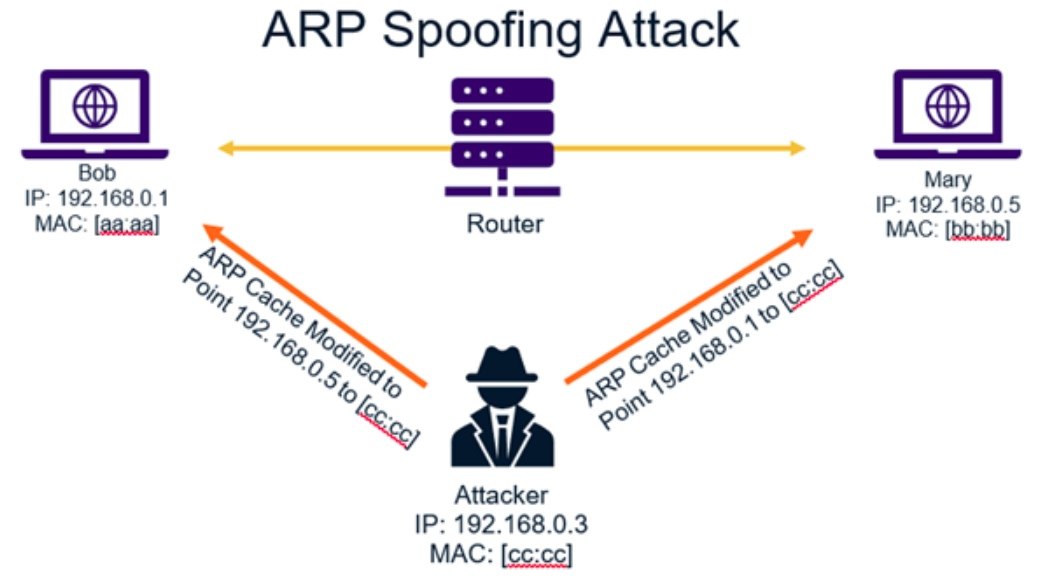
Image source: Thesslstore.com
Command Line Usage:
The arp command is used to view and manipulate the ARP table on a system. This table holds the IP address to MAC address mappings for hosts that have been communicated with.
Linux:
View the ARP Table:
arporarp -a- This command displays the ARP table. The
-aoption is often used for a more readable format.
- This command displays the ARP table. The
Add a Static ARP Entry:
sudo arp -s <IPAddress> <MACAddress>- Adds a permanent entry to the ARP cache. You usually need superuser permissions to add an ARP entry.
Delete an ARP Entry:
sudo arp -d <IPAddress>- Deletes an ARP entry. Like adding an entry, this usually requires superuser permissions.
Additional Options
-n: Displays ARP entries without resolving addresses to hostnames. This can speed up the command if reverse DNS lookups are slow or unnecessary.-v: Verbose mode. Provides more detailed output, which can be helpful for troubleshooting.
Usage Notes
Superuser Access: Modifying the ARP table typically requires superuser (administrator/root) permissions because of the potential for misuse, such as ARP spoofing attacks.
Temporary vs. Permanent Entries: Entries added manually are often permanent (persistent across reboots), especially on Windows, unless explicitly removed. On Linux and macOS, the behavior can depend on the system configuration and version.
Security: Because ARP does not include authentication mechanisms, it's advisable to use ARP commands with an understanding of the potential security implications, especially on networks susceptible to ARP spoofing or poisoning attacks.
Remember, the availability and syntax of these commands can vary depending on the operating system and its version, so it's a good idea to check the man pages (man arp on Linux and macOS) or use arp /? on Windows for the most accurate information.
References:
Subscribe to my newsletter
Read articles from Maxat Akbanov directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Maxat Akbanov
Maxat Akbanov
Hey, I'm a postgraduate in Cyber Security with practical experience in Software Engineering and DevOps Operations. The top player on TryHackMe platform, multilingual speaker (Kazakh, Russian, English, Spanish, and Turkish), curios person, bookworm, geek, sports lover, and just a good guy to speak with!