Exploring Rancher: A Comprehensive Kubernetes Management Tool
 Bruno Gatete
Bruno Gatete
Rancher is a comprehensive Kubernetes management tool that simplifies the deployment and operation of clusters across various environments and providers. It facilitates cluster provisioning, centralizes authentication and access control, offers monitoring and alerting capabilities, integrates with Helm for application deployment, and includes features like Fleet for workload automation. In essence, Rancher serves as a complete container management platform for Kubernetes, empowering organizations to efficiently run their applications anywhere.
How to Install Rancher
Pre-requisites
Kubernetes Cluster V>1.9
Helm Installed on the Cluster
kato@master1:~$ kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
master1 Ready control-plane,master 5m27s v1.23.10 192.168.1.60 <none> Ubuntu 20.04.5 LTS 5.4.0-169-generic docker://20.10.8
node1 Ready worker 5m v1.23.10 192.168.1.61 <none> Ubuntu 20.04.5 LTS 5.4.0-169-generic docker://20.10.8
node2 Ready worker 5m v1.23.10 192.168.1.62 <none> Ubuntu 20.04.5 LTS 5.4.0-169-generic docker://20.10.8
kato@master1:~$ helm version
version.BuildInfo{Version:"v3.9.0", GitCommit:"7ceeda6c585217a19a1131663d8cd1f7d641b2a7", GitTreeState:"clean", GoVersion:"go1.17.5"}
Add the Helm Chart Repository
Use helm repo add command to add the Helm chart repository that contains charts to install Rancher.
helm repo add rancher-latest https://releases.rancher.com/server-charts/latest
Stable: Recommended for production environments
helm repo add rancher-stable https://releases.rancher.com/server-charts/stable
Create a Namespace for Rancher
kubectl create namespace cattle-system
Install cert-manager
You should skip this step if you are bringing your own certificate files (option
ingress.tls.source=secret), or if you use TLS termination on an external load balancer.
# If you have installed the CRDs manually instead of with the `--set installCRDs=true` option added to your Helm install command, you should upgrade your CRD resources before upgrading the Helm chart:
kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/<VERSION>/cert-manager.crds.yaml
# Add the Jetstack Helm repository
helm repo add jetstack https://charts.jetstack.io
# Update your local Helm chart repository cache
helm repo update
# Install the cert-manager Helm chart
helm install cert-manager jetstack/cert-manager \
--namespace cert-manager \
--create-namespace \
--set installCRDs=true
Once you’ve installed cert-manager, you can verify it is deployed correctly by checking the cert-manager namespace for running pods:
kubectl get pods --namespace cert-manager
NAME READY STATUS RESTARTS AGE
cert-manager-5c6866597-zw7kh 1/1 Running 0 2m
cert-manager-cainjector-577f6d9fd7-tr77l 1/1 Running 0 2m
cert-manager-webhook-787858fcdb-nlzsq 1/1 Running 0 2m
Install Rancher with Helm and Your Chosen Certificate Option
helm install rancher rancher-stable/rancher \
> --namespace cattle-system \
> --set hostname=rancher.my.org \
> --set bootstrapPassword=admin
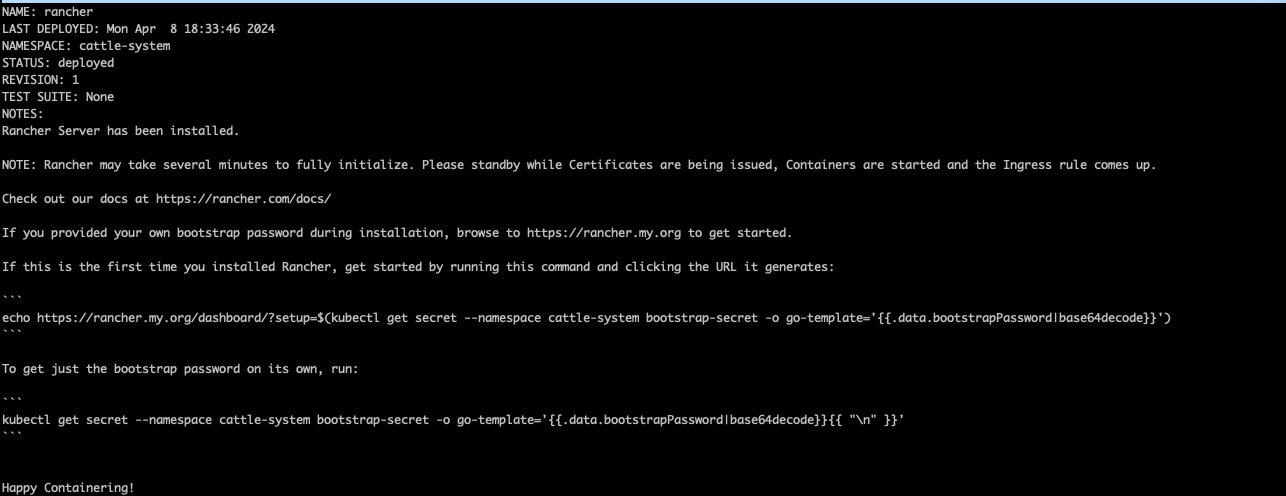
Wait for Rancher to be rolled out:
kubectl -n cattle-system rollout status deploy/rancher
Waiting for deployment "rancher" rollout to finish: 0 of 3 updated replicas are available...
deployment "rancher" successfully rolled out
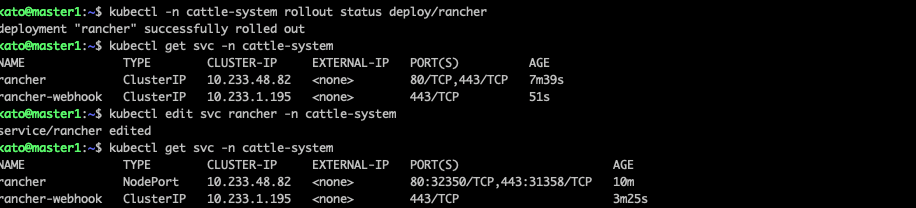
Once you create your password and login
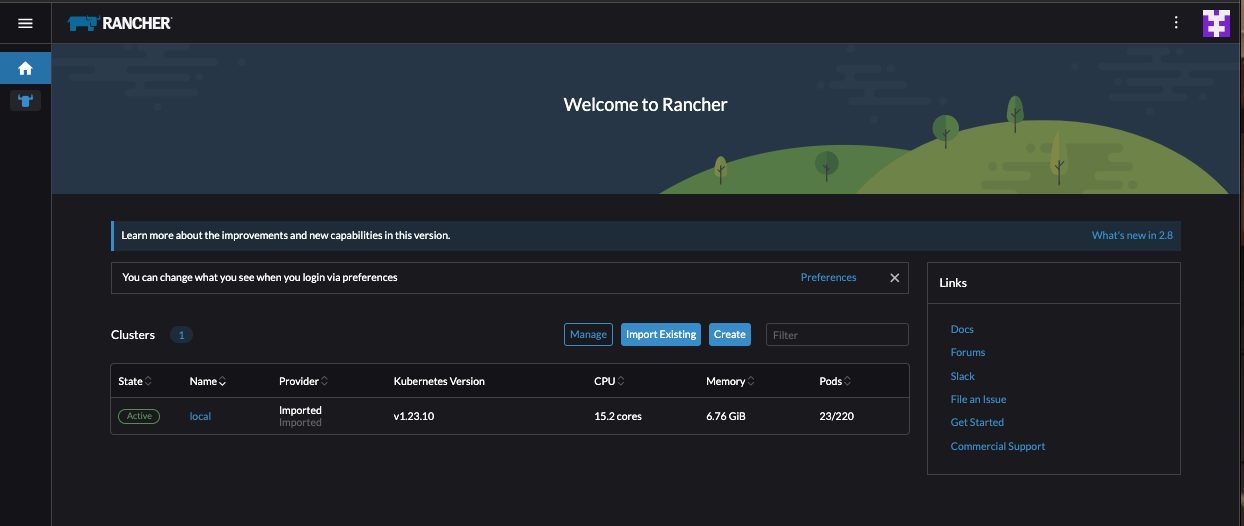
Let Us deploy an application and see how rancher interpretes everything on Kubernetes
kato@master1:~$ git clone https://github.com/Gatete-Bruno/rancher-101.git
Cloning into 'rancher-101'...
remote: Enumerating objects: 24, done.
remote: Counting objects: 100% (24/24), done.
remote: Compressing objects: 100% (19/19), done.
remote: Total 24 (delta 3), reused 23 (delta 2), pack-reused 0
Unpacking objects: 100% (24/24), 11.27 KiB | 288.00 KiB/s, done.
kato@master1:~$ cd rancher-101/
kato@master1:~/rancher-101$ ls
K8s-Microservices-Fleetman README.md
kato@master1:~/rancher-101$ cd K8s-Microservices-Fleetman/
kato@master1:~/rancher-101/K8s-Microservices-Fleetman$ ls
AWS Intro-Phase-1 'Logging ELK' 'Microservice Architecture '
kato@master1:~/rancher-101/K8s-Microservices-Fleetman$ cd Microservice\ Architecture\ /
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ ls
mongo-stack.yaml services.yaml storage.yaml workloads.yaml
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ kubectl apply -f storage.yaml
persistentvolumeclaim/mongo-pvc created
persistentvolume/local-storage created
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ kubectl apply -f workloads.yaml
deployment.apps/queue created
deployment.apps/position-simulator created
deployment.apps/position-tracker created
deployment.apps/api-gateway created
deployment.apps/webapp created
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ kubectl apply -f services.yaml
service/fleetman-webapp created
service/fleetman-queue created
service/fleetman-position-tracker created
service/fleetman-api-gateway created
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ kubectl apply -f mongo-stack.yaml
deployment.apps/mongodb created
service/fleetman-mongodb created
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $ kubectl get all
NAME READY STATUS RESTARTS AGE
pod/api-gateway-6778674ddc-6d8sx 0/1 ContainerCreating 0 23s
pod/mongodb-bb6879545-kkhzs 0/1 ContainerCreating 0 7s
pod/position-simulator-75dddbb5b4-n5zf9 0/1 ContainerCreating 0 23s
pod/position-tracker-556974ff57-n8xgq 0/1 ContainerCreating 0 23s
pod/queue-bf8d54985-6twgx 0/1 ContainerCreating 0 23s
pod/webapp-5cbfb64494-94f6j 1/1 Running 0 23s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/fleetman-api-gateway NodePort 10.233.22.98 <none> 8080:30020/TCP 14s
service/fleetman-mongodb ClusterIP 10.233.40.102 <none> 27017/TCP 7s
service/fleetman-position-tracker ClusterIP 10.233.32.7 <none> 8080/TCP 14s
service/fleetman-queue NodePort 10.233.31.177 <none> 8161:30010/TCP,61616:32320/TCP 14s
service/fleetman-webapp NodePort 10.233.16.54 <none> 80:30080/TCP 14s
service/kubernetes ClusterIP 10.233.0.1 <none> 443/TCP 102m
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/api-gateway 0/1 1 0 23s
deployment.apps/mongodb 0/1 1 0 7s
deployment.apps/position-simulator 0/1 1 0 23s
deployment.apps/position-tracker 0/1 1 0 23s
deployment.apps/queue 0/1 1 0 23s
deployment.apps/webapp 1/1 1 1 23s
NAME DESIRED CURRENT READY AGE
replicaset.apps/api-gateway-6778674ddc 1 1 0 23s
replicaset.apps/mongodb-bb6879545 1 1 0 7s
replicaset.apps/position-simulator-75dddbb5b4 1 1 0 23s
replicaset.apps/position-tracker-556974ff57 1 1 0 23s
replicaset.apps/queue-bf8d54985 1 1 0 23s
replicaset.apps/webapp-5cbfb64494 1 1 1 23s
kato@master1:~/rancher-101/K8s-Microservices-Fleetman/Microservice Architecture $
Subscribe to my newsletter
Read articles from Bruno Gatete directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Bruno Gatete
Bruno Gatete
DevOps and Cloud Engineer Focused on optimizing the software development lifecycle through seamless integration of development and operations, specializing in designing, implementing, and managing scalable cloud infrastructure with a strong emphasis on automation and collaboration. Key Skills: Terraform: Skilled in Infrastructure as Code (IaC) for automating infrastructure deployment and management. Ansible: Proficient in automation tasks, configuration management, and application deployment. AWS: Extensive experience with AWS services like EC2, S3, RDS, and Lambda, designing scalable and cost-effective solutions. Kubernetes: Expert in container orchestration, deploying, scaling, and managing containerized applications. Docker: Proficient in containerization for consistent development, testing, and deployment. Google Cloud Platform: Familiar with GCP services for compute, storage, and machine learning.