Understanding Password Hashing Functions: Secure Storage of Passwords
 Cloud Tuned
Cloud Tuned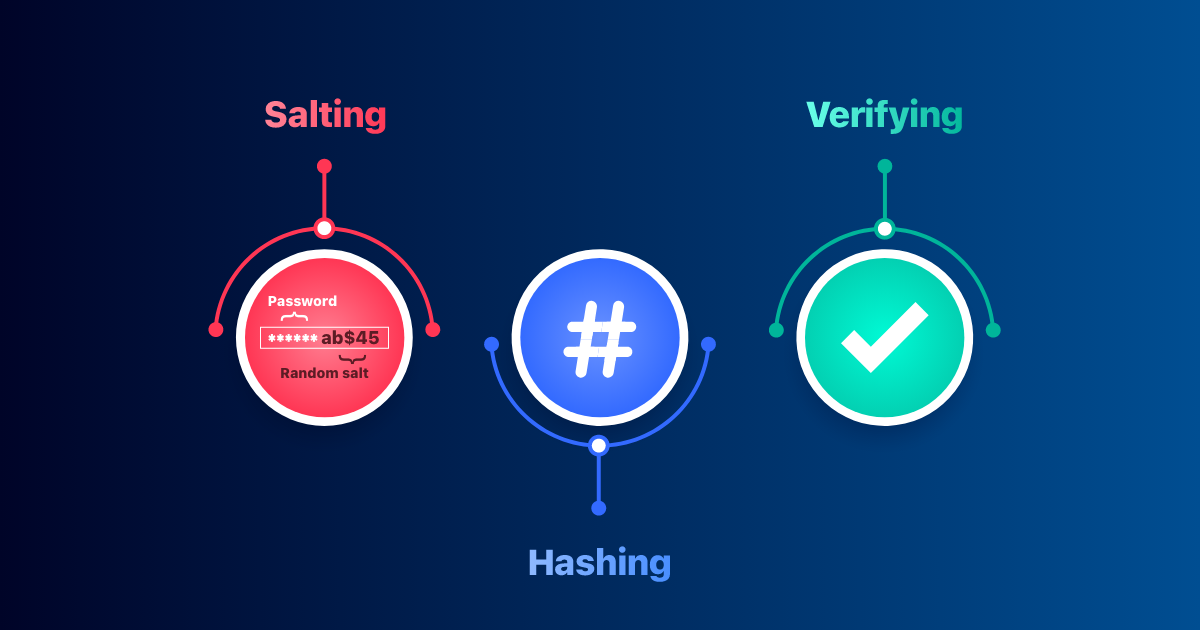
Understanding Password Hashing Functions: Secure Storage of Passwords
In the realm of cybersecurity, protecting user passwords is of utmost importance to prevent unauthorized access and data breaches. Password hashing functions provide a critical layer of security by securely storing passwords in a form that is resistant to reverse engineering and brute-force attacks. In this article, we'll delve into what password hashing functions are, how they work, and best practices for securely storing passwords.
What are Password Hashing Functions?
A password hashing function is a cryptographic algorithm that takes an input (typically a password) and produces a fixed-size string of characters, known as a hash value or digest. Unlike encryption algorithms, which are designed to be reversible, hashing functions are designed to be one-way, meaning it should be computationally infeasible to reverse the process and obtain the original input from the hash value.
How Do Password Hashing Functions Work?
The process of hashing a password using a password hashing function typically involves the following steps:
Input: The user provides a password during the registration or authentication process.
Hashing: The password hashing function takes the input password and applies a mathematical algorithm to generate a hash value.
Salt: A random value, known as a salt, may be added to the password before hashing to add additional randomness and prevent attacks such as rainbow table attacks.
Storage: The resulting hash value is stored in the database along with the user's other account information.
Verification: During the authentication process, when the user attempts to log in, the entered password is hashed using the same hashing function and compared to the stored hash value. If the two hash values match, the authentication is successful.
Benefits of Password Hashing Functions
Password hashing functions offer several benefits for securely storing passwords:
Non-Reversibility: Hashed passwords cannot be reversed to obtain the original plaintext passwords, providing an additional layer of security against data breaches.
Collision Resistance: A good password hashing function minimizes the likelihood of producing the same hash value for different inputs, known as collisions, ensuring uniqueness of hash values.
Salting: The use of salts adds randomness to the hashing process, making it more difficult for attackers to use precomputed tables (e.g., rainbow tables) to crack passwords.
Scalability: Password hashing functions are computationally efficient and scalable, allowing for fast hashing of passwords even in large-scale systems.
Best Practices for Password Hashing
To ensure the security of stored passwords, it's essential to follow best practices for password hashing:
Use a Strong Hashing Algorithm: Choose a secure cryptographic hashing algorithm such as SHA-256 or bcrypt, which are resistant to brute-force attacks and cryptanalytic techniques.
Use Salt: Always use a unique, random salt for each password to prevent rainbow table attacks and ensure the uniqueness of hash values.
Iterative Hashing (Key Stretching): Apply multiple iterations of the hashing algorithm (key stretching) to increase the computational cost of hashing and make brute-force attacks more difficult.
Store Hashed Passwords Securely: Store hashed passwords securely in the database, ensuring that they are adequately protected from unauthorized access and data breaches.
Regularly Update Hashing Algorithms: Stay updated with advancements in cryptography and periodically update password hashing algorithms to use the latest and most secure options available.
Conclusion
Password hashing functions play a crucial role in securely storing passwords and protecting user accounts from unauthorized access and data breaches. By applying cryptographic algorithms, salting, and other security measures, password hashing functions ensure that passwords are stored in a non-reversible and secure manner, safeguarding sensitive user information. As cybersecurity threats continue to evolve, following best practices for password hashing remains essential for maintaining the integrity and confidentiality of user passwords in web applications and systems.
Subscribe to my newsletter
Read articles from Cloud Tuned directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
