The Bug Bounty Chronicles
 Prasun Ray
Prasun Ray
Introduction to web servers, web applications, and their configurations.
What is a "Web Server"
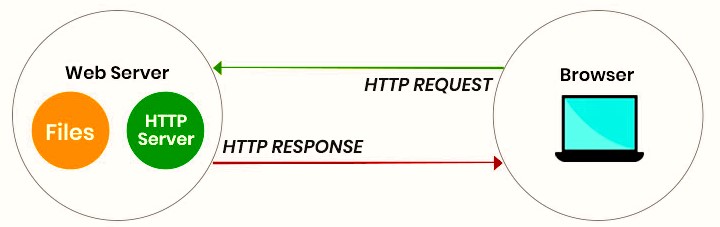 Major web servers: Apache, Nginx, Microsoft IIS, and Google Web Server. Apache is one of the most widely used open-source web servers.
Major web servers: Apache, Nginx, Microsoft IIS, and Google Web Server. Apache is one of the most widely used open-source web servers.
Types of Web Servers
A Web Server Configurations
A Web Application
Web Application Configuration
Explanation of what a bug bounty program is and the popular platforms like HackerOne and Bugcrowd.
What is Bug Bounty
Platforms where you can hunt for the “bugs”:
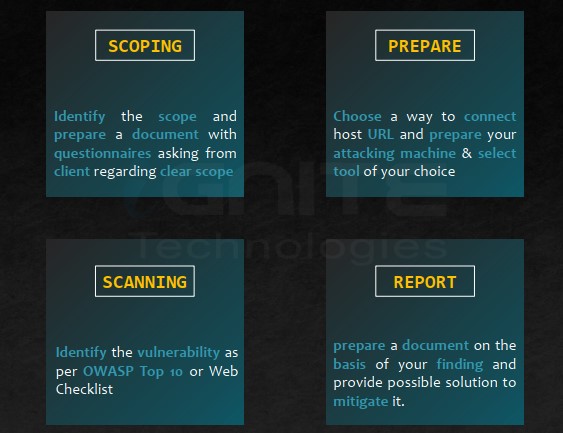
Web Security Assessment(Vulnerability Assessment)
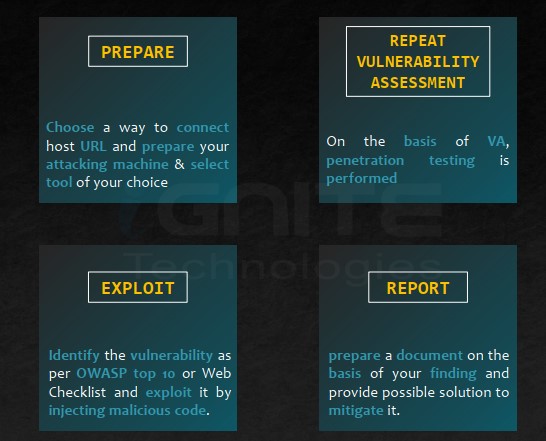
Web Security Assessment(Penetration Testing)
OWASP Top 10 and Common Vulnerabilities
OWASP or the Open Web Application Security Project is an international non-profit organization dedicated to web application security.
The OWASP Top 10 is a regularly updated report outlining security concerns for web application security, focusing on the 10 most critical risks.
OWASP refers to the Top 10 as an ‘awareness document’ and thus all companies incorporate the report into their processes in order to minimize and/or mitigate security risks.
OWASP Top 10
Broken access control
Cryptographic failures
Injection.
Insecure design.
Security misconfiguration.
Vulnerable and outdated components.
Identification and authentication failures.
Software and data integrity failures.
Security logging and monitoring failures.
Server-side request forgery
for more information about the top 10 OWASP visit --> OWASP<2021>
Subscribe to my newsletter
Read articles from Prasun Ray directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
