Part 1 : Cryptography and it's types, Explained!
 Sai Keerthan Kasula
Sai Keerthan Kasula
Have you ever wondered how data is securely transferred from one entity to another and what developers actually do to ensure that the transmitted data is secure? How cryptography is involved in dealing with application or information security? Well, Let's explore in this article.
Allow me to introduce myself, I am Keerthan, working at an esteemed organization as a java developer. I have worked on implementing cryptography into a java application to securely transmit data which ensures data integrity and confidentiality.
So, what is cryptography ?
Cryptography is the study of techniques for ensuring secure communication. It ensures that the data being transmitted is only viewable by the intended recipient. In general terms, it is a way of transforming information in such a way that no third parties or public can read it.
Cryptography uses mathematics, number theory, computer science etc, to design such methods of coding or hiding the information. Cryptography heavily relies on computer science principles, including algorithms, data structures, complexity theory, and computational complexity.
Before deep diving more, let us get familiar with some terms:
Plain text : Plain text is anything that is human-readable and understandable.
Cipher text : Cipher text is the scrambled text, which tough to decode or read.
Cryptographic Algorithm : It is a mathematical equation that transforms the plain text into cipher text.
Encryption : Encryption is the process of transforming plain text into cipher text using the cryptographic algorithm.
Decryption : Decryption is the opposite of encryption, transforming cipher text into plain text.
Cryptographic keys : Cryptographic keys helps the process of encryption and decryption possible.
Types of cryptography
There are several types of cryptography, each serving different purposes and employing distinct techniques, let us explore some of the main types:
Symmetric Cryptography : Symmetric cryptography is the type of encryption technique, in which only a single key is involved to encrypt and decrypt the data. The key is only shared to the intended person through a secured channel who is authorized to decrypt the data.
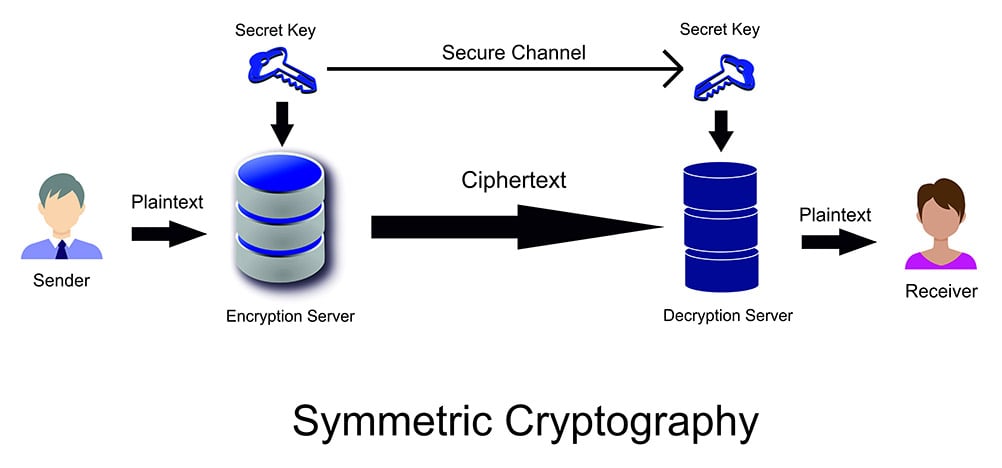
symmetric cryptography algorithms are : Data Encryption Standard (DES), Advanced Encryption Standard (AES), Triple Data Encryption Standard (3DES), Blowfish etc.
Asymmetric Encryption : Asymmetric cryptography is the type of encryption technique, in which two keys, a public key and a private key is involved to encrypt and decrypt the data. The public key is shared to everyone, where as the private key is kept secret.

Asymmetric cryptography algorithms : RSA, Diffie hellman, Elliptic cryptography curve (ECC) etc.
In our next blog, I'll explain how cryptography is actually used in a real time java application, what are the techniques and technologies involved to perform secure transmision using cryptography.
Until then, consider to follow me for such content.
Thanks for reading :-D
Regards,
Sai Keerthan,
Junior Developer.
Subscribe to my newsletter
Read articles from Sai Keerthan Kasula directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sai Keerthan Kasula
Sai Keerthan Kasula
Embracing this journey, eager to confront new challenges daily and strive towards becoming the best version of myself.