VPC ( Virtual Private Cloud )
 Nehal Ingole
Nehal Ingole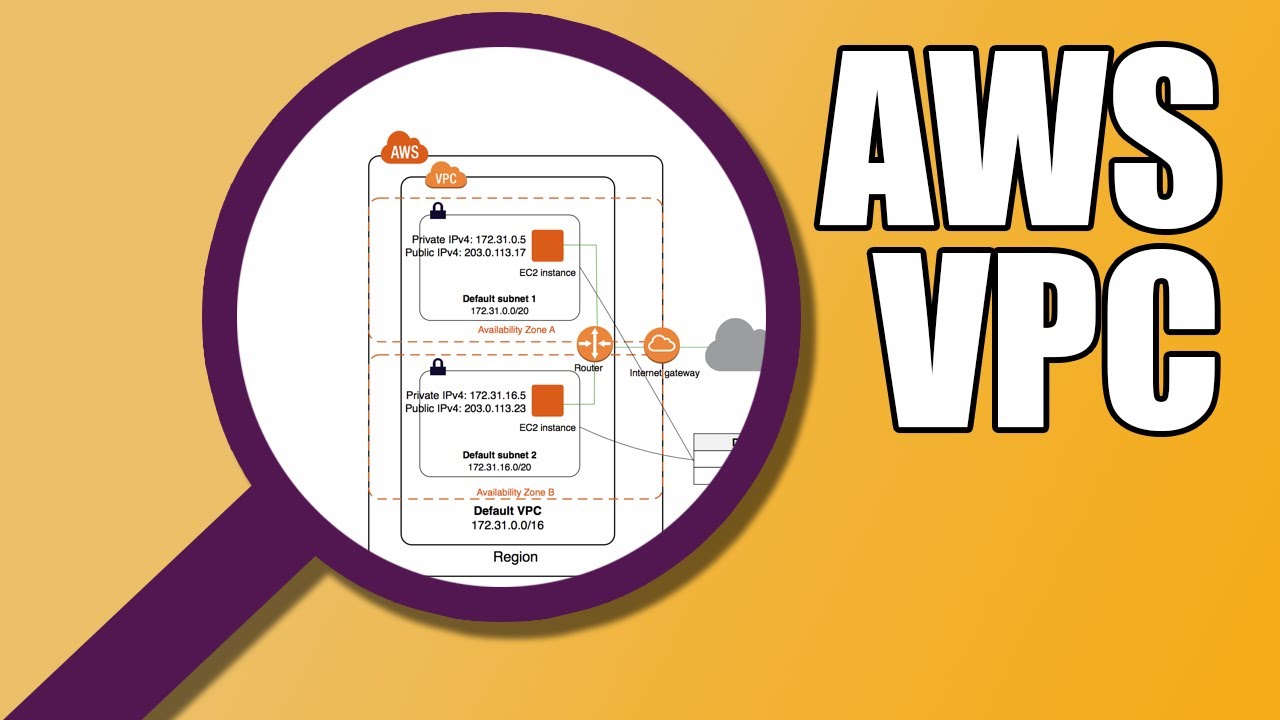
Introduction
Imagine a bustling city with dedicated lanes for public transportation, private residences, and commercial areas. That's essentially what a Virtual Private Cloud (VPC) does in the vast landscape of the AWS cloud. It carves out a secure, isolated network segment for your resources, giving you granular control over traffic flow and security.
This blog dives deep into the world of VPCs, explaining their components, setup process, and benefits, all presented in a clear and comprehensive way.
VPC: Your Private Cloud Getaway
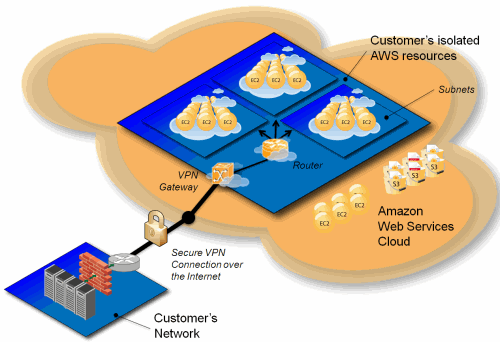
A VPC allows you to create a virtual network within the AWS cloud. Think of it as your own private highway system, separate from the public internet. This virtual network offers several advantages:
Control: You define your IP address range, configure how traffic flows, and set up dedicated subnets for different purposes.
Security: You control who can access your resources by implementing security groups and Network Access Control Lists (NACLs).
Building Blocks of a VPC
Now, let's explore the key components that make your VPC function:
Subnets: These are subdivisions within your VPC, similar to neighborhoods within a city. You can create public subnets for resources accessible from the internet and private subnets for those that should remain hidden.
Route Tables: These act like traffic signals, directing network traffic to its intended destination. You can have separate route tables for public and private subnets, ensuring traffic flows efficiently.
Internet Gateway (IGW): This acts as the on-ramp to the internet for your VPC. If you have resources in a public subnet that need to communicate with the outside world, the IGW provides the connection.
NAT Gateway/NAT Instance: Imagine a one-way bridge. This allows resources in a private subnet to initiate outgoing connections to the internet but prevents incoming traffic from reaching them directly, maintaining security.
Security Groups and NACLs: These are the security guards of your VPC. Security groups control inbound and outbound traffic at the instance level, while NACLs manage traffic flow at the subnet level.
Setting Up Your VPC: A Step-by-Step Guide
Let's follow "Example Corp" as they build their secure network using a VPC:
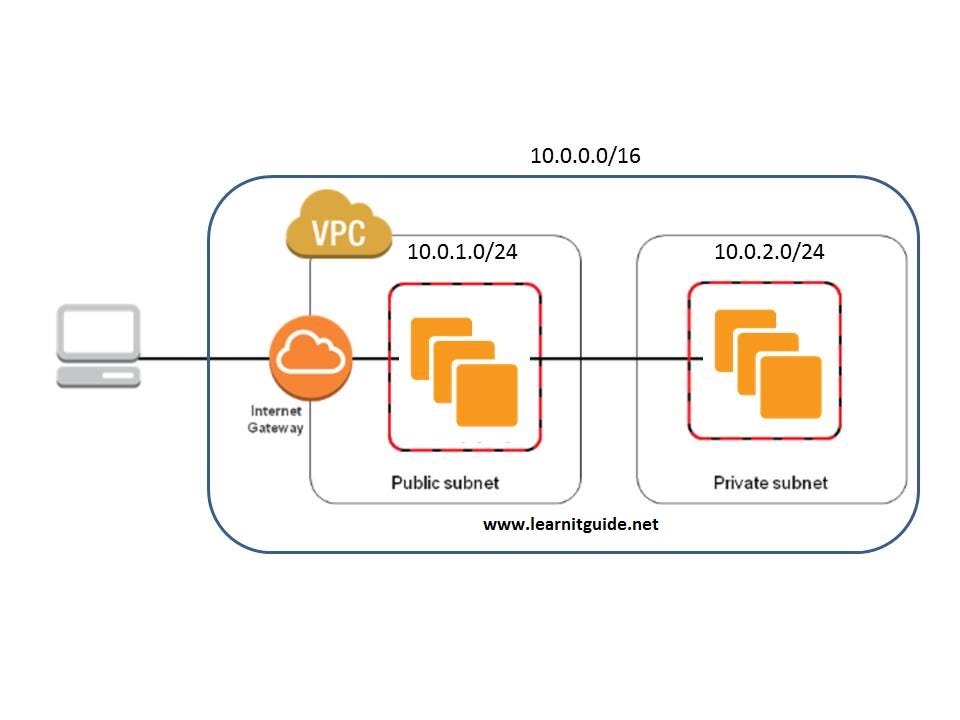
Create the VPC: Example Corp starts by creating a VPC with a CIDR block, which is like their designated address space within the AWS cloud (e.g., 10.0.0.0/16).
Divide and Conquer: Subnets: They create two subnets:
Public Subnet (10.0.1.0/24): This will house their web servers, which need to be accessible from the internet.
Private Subnet (10.0.2.0/24): This is for their application servers and databases that should remain hidden from public view.
Connecting to the World: Internet Gateway: An IGW is attached to the VPC, allowing web servers in the public subnet to access the internet for updates and communication.
Route Management: Route Tables: Two route tables are created:
Public Route Table: This table directs traffic destined for the internet to the IGW, ensuring smooth communication.
Private Route Table: This table routes internet-bound traffic from the private subnet to a NAT Gateway/NAT Instance (explained next). 5. Security Measures: Security Groups and NACLs:
Security Groups: These are configured to allow only HTTP/HTTPS traffic to reach the web servers in the public subnet.
NACLs: These act as an additional security layer, allowing or denying traffic flow at the subnet level.
Deployment: Bringing Your VPC to Life
Now comes the exciting part - deploying your resources within the secure confines of the VPC:
Launching EC2 Instances:
Web Servers: These are launched in the public subnet with security groups configured to allow only authorized traffic (HTTP/HTTPS).
Application Servers and Databases: These reside in the private subnet, with restricted access for enhanced security.
Assigning an Elastic IP (EIP): An EIP is assigned to the NAT Gateway/NAT Instance. This provides a public IP address for outbound connections from the private subnet, allowing them to access the internet while maintaining security.
Traffic Flow: A Behind-the-Scenes Look
Here's how data flows within your VPC:
Incoming Requests: A user from the internet accesses your website. This request is directed to the web servers in the public subnet.
Internal Communication: The web servers might need data from your application servers and databases in the private subnet. They can securely communicate within the VPC.
Conclusion
VPCs offer a robust and secure way to build and manage your network infrastructure within the AWS cloud. By understanding the core components and configuration steps, you can create a customized network environment that meets your specific needs.
Here's a quick recap of the advantages VPCs bring to the table:
Enhanced Security: Isolate your resources and control access with granular security measures.
Improved Scalability: Easily scale your network up or down to accommodate changing demands.
Flexibility and Control: Design complex network architectures tailored to your application requirements.
VPCs empower you to leverage the power of the AWS cloud while maintaining complete control over your network security and configuration. So, take the wheel and navigate your AWS journey with the confidence and flexibility that VPCs provide!
Connect with us:
Hashnode: https://hashnode.com/@Nehal71
Twitter : https://twitter.com/IngoleNehal
Subscribe to my newsletter
Read articles from Nehal Ingole directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nehal Ingole
Nehal Ingole
🚀 Greetings World! 🌐 Meet a dynamic Frontend Developer, UI/UX Designer, and avid explorer of Cloud & DevOps realms! Uncover the journey of a professional deeply passionate about crafting seamless user experiences, designing visually stunning interfaces, and navigating the cloud with a DevOps mindset. 🔧 Skills Snapshot: Frontend Mastery: HTML, CSS, and JavaScript expert, specializing in React, Angular, and Vue.js. Design Wizardry: Proficient in wireframing, prototyping, and Adobe Creative Suite and Figma for captivating designs. Cloud Maestro: Fluent in AWS, Azure, and Google Cloud Platform, adept at architecting scalable solutions. DevOps Guru: Skilled in Docker, Kubernetes, Jenkins, and Git, contributing to efficient development workflows. 🔗 Let's Connect: Open to collaborating on exciting projects and sharing industry insights, I invite connections for networking or discussions. Reach out for potential collaborations. 📧 Contact Me: GitHub: GitHub Profile Email: nehalingole2001@gmail.com Mobile: 7397966719 Figma: Figma Profile Twitter: Twitter Profile HashNode: HashNode Profile LinkedIn : LinkedIn Profile