Securing Information Systems: Integrating Authentication and Authorization into the CIA Triad
 kasinadhsarma
kasinadhsarma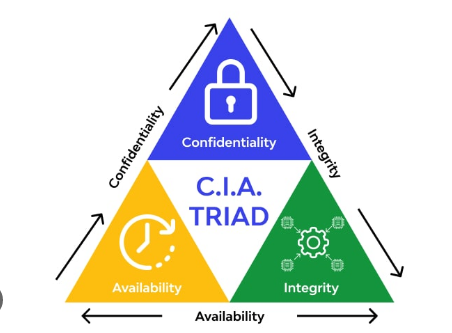
Title: Integrating Authentication, Authorization, and the LAMP Stack into the CIA Triad: A Comprehensive Security Approach
Introduction: Introduce the CIA Triad and its significance in information security. Briefly mention that the focus of this blog post will be on the integration of authentication, authorization, and the LAMP stack within this framework.
1. Understanding Authentication and Authorization: Define authentication and authorization and their importance in securing information systems. Discuss various methods and best practices for implementing robust authentication and authorization mechanisms.
2. Integrating Security into the CIA Triad: Illustrate how the integration of authentication, authorization, and the LAMP stack contributes to the goals of confidentiality, integrity, and availability:
Confidentiality: Secure authentication prevents unauthorized access to sensitive data stored in MySQL databases, preserving confidentiality. Authorization controls restrict user access to specific resources, further protecting confidential information.
Integrity: Implementing secure authentication mechanisms ensures that user interactions with web applications do not compromise the integrity of data. Authorization policies prevent unauthorized modifications to database records, maintaining data integrity.
Availability: Reliable authentication and authorization mechanisms ensure that legitimate users can access web applications hosted on Apache servers, contributing to system availability.
3. Conclusion: Summarize the key points discussed in the blog post and emphasize the importance of integrating authentication and authorization. Encourage readers to explore further and implement these security measures in their web development projects.
4. Notification: Announce the release of another blog post specifically focusing on the LAMP stack and its benefits for web development. Provide a brief teaser or overview to pique readers' interest and encourage them to check out the new post for more details.
This revised outline will help you create a focused blog post that covers the integration of authentication, authorization, and the LAMP stack within the CIA Triad, while also informing readers about the release of the upcoming blog post dedicated to the LAMP stack.
Subscribe to my newsletter
Read articles from kasinadhsarma directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

kasinadhsarma
kasinadhsarma
Hi I am Kasinadhsarma
