⚙Day 4 - Terraform State Management
 Vivek Ashok Moudekar
Vivek Ashok Moudekar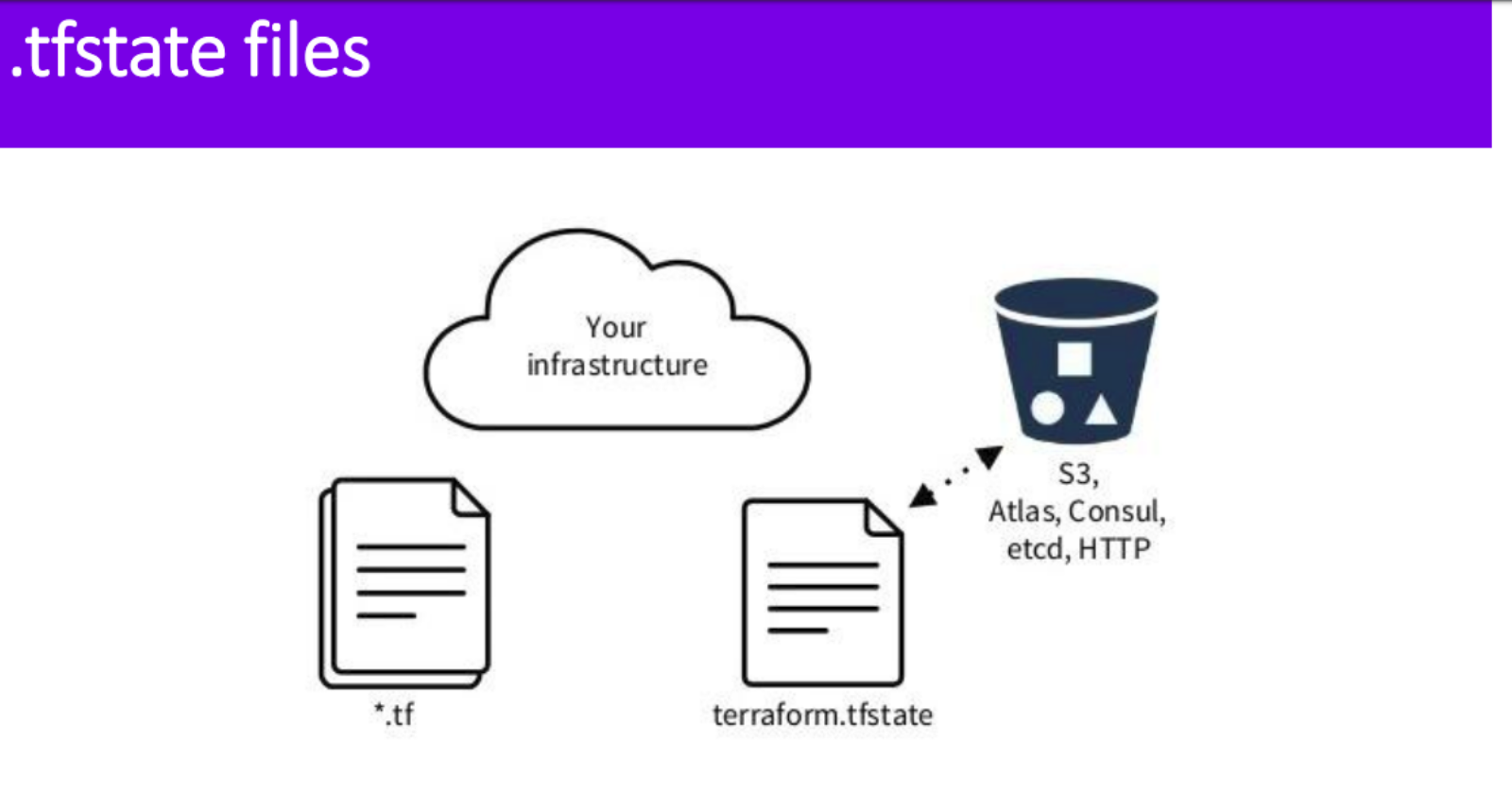
📍Task 1: Importance of Terraform State
Terraform state plays a crucial role in managing infrastructure by tracking the current state of resources, resolving dependencies, enabling concurrency and collaboration, facilitating rollback and recovery, executing plans, and enabling remote state management. It's a fundamental concept in Terraform that ensures smooth and reliable infrastructure provisioning and management.This state file allows Terraform to know which resources are already created, which need to be updated, and which need to be destroyed.Without the state file, Terraform would not be able to manage resources effectively, leading to potential conflicts and inconsistencies in your infrastructure.
📍Task 2: Local State and terraform state Command
To create a local state file, you can use the default behavior of Terraform, which stores the state file in a file named "terraform.tfstate" in the current directory. You can initialize Terraform in a directory containing your configuration files using the following command:
terraform init
Once initialized, you can use the terraform state command to manage your resources. For example, to list all resources in your state file, you can use:
terraform state list
📍Task 3: Remote State Management
Remote state management options like Terraform Cloud, AWS S3, Azure Storage Account, or HashiCorp. Become familiar with the steps required to leverage remote state management in your Terraform workflow. say you choose AWS S3 as your remote state backend. You can configure it by adding the following backend configuration block to your Terraform configuration file:
terraform { #terraform.tf
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.42.0"
}
}
backend "s3" {
bucket = "terra-4-state-bucket"
key = "terrafrom.tfsate"
region = "us-east-2"
dynamodb_table = "terraweek-demo-state-table"
}
}
#Replace placeholders like your-bucket-name, key, your-region, & dynamodb_table name.
#Ensure that the AWS credentials used for this backend configuration have sufficient permissions to access the S3 bucket and, if used, the DynamoDB table for state locking.
Happy Learning 😊
Subscribe to my newsletter
Read articles from Vivek Ashok Moudekar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vivek Ashok Moudekar
Vivek Ashok Moudekar
👋 Hello there! I'm Vivek, a DevOps enthusiast with a keen interest in streamlining software delivery. I hold a Master's degree in Computer Applications and have a solid foundation in key technologies such as Linux, Git, Docker, Kubernetes, and AWS. 💻 My passion lies in automation, ensuring efficient and seamless processes throughout the software development lifecycle. I thrive on creating robust CI/CD pipelines that empower teams to deliver high-quality software with confidence. 🚀 Beyond the code, I enjoy the ever-evolving world of DevOps and the challenges it brings. Join me on this journey as I explore new ways to enhance software delivery and foster a culture of continuous improvement. Let's connect, collaborate, and make the world of DevOps even more exciting together