Unveiling AWS Guard Duty: Your Guardian Angel for Cloud Threat Detection
 Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu Rachapudi
Introduction
Amazon GuardDuty is a security monitoring service provided by AWS. It is designed to safeguard your AWS accounts, workloads, and data by continuously monitoring for potential threats across your AWS environment.
GuardDuty analyzes and processes various data sources, such as AWS CloudTrail management events, VPC flow logs, and DNS logs. It also processes features such as Kubernetes audit logs, RDS login activity, S3 logs, EBS volumes, Runtime monitoring, and Lambda network activity logs.
This service uses threat intelligence feeds, such as lists of malicious IP addresses and domains, and machine learning to identify unexpected, potentially unauthorized, and malicious activity within your AWS environment. This can include issues like escalation of privileges, use of exposed credentials, or communication with malicious IP addresses, domains, and presence of malware on your Amazon EC2 instances and container workloads.
Advantages of AWS Guard Duty
Easy Deployment: GuardDuty can be quickly launched for single or multiple accounts using your AWS’s Management Console.
Easy Integration with Other AWS Tools: Since GuardDuty is an AWS tool, it is closely associated with additional AWS security and logging tools.
Updated Security Intelligence: GuardDuty is continuously updated with the latest threat intelligence.
Near Real-Time Threat Detection: GuardDuty provides almost real-time detection of threats.
Cost-Effectiveness: Compared to other solutions, GuardDuty is cost-effective.
Monitors Outgoing and Incoming Connections: GuardDuty monitors outgoing connections from AWS resources to known malicious hosts and incoming connections to AWS resources from known malicious hosts.
How to Enable the AWS Guard Duty?
Enabling Amazon GuardDuty:
Sign in to your AWS account and go to the AWS Management Console.
Open the GuardDuty console.
Choose 'Get Started’.
Click on ‘Enable GuardDuty’ to begin.
You can also enable GuardDuty through the AWS CLI using the following command:
aws guardduty create-detector --enable --region <your-region>
Replace <your-region> with the AWS region where you want to enable Guard Duty.
Trial Period:
When you enable Guard Duty for the first time in any region, your Amazon account is automatically enrolled in a 30-day free trial for that region. During this trial period, you will have access to the full feature set and detections.
Example:
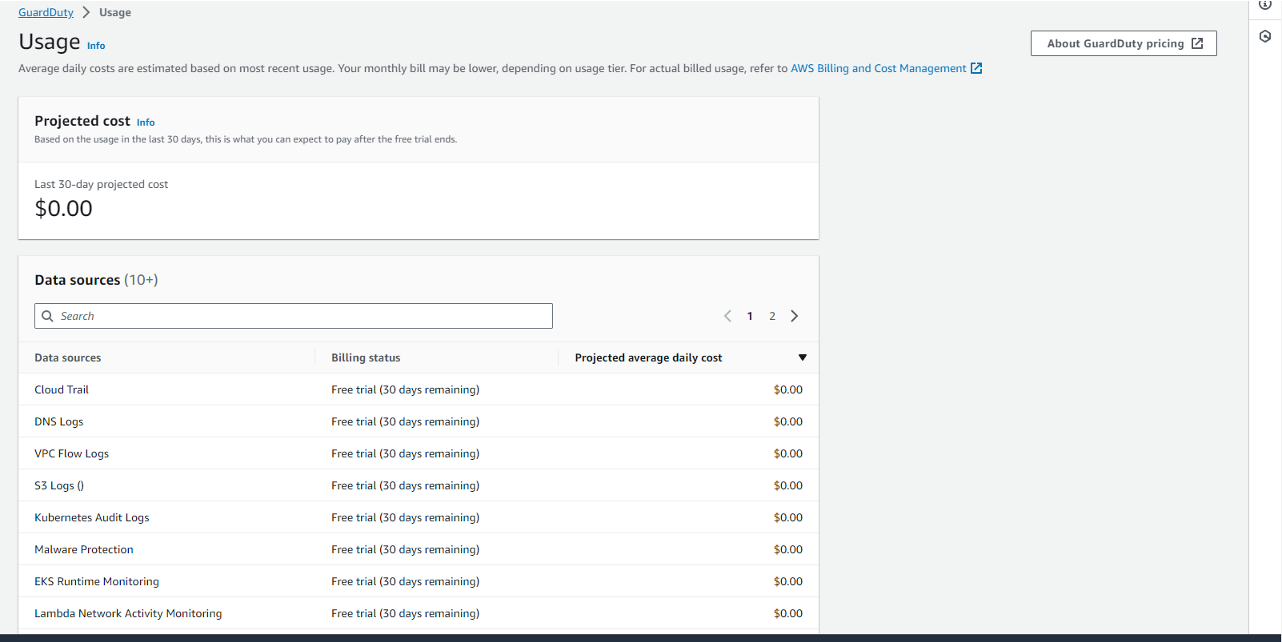
Here I have enabled the Guard Duty Service, and you can see the free trail has begun for few of the sources like Cloud Trail, DNS Logs, S3 Logs, Malware Protection and etc.
For the Demo purpose I have created a S3 Bucket by Disabling the BucketPublicAccess and used Root account to create the above bucket (It is not right practice to do always remember use IAM user instead of root :))
Now Guard Duty Detected 2 potential threats which are low and mentioned from which AWS Account it got detected.
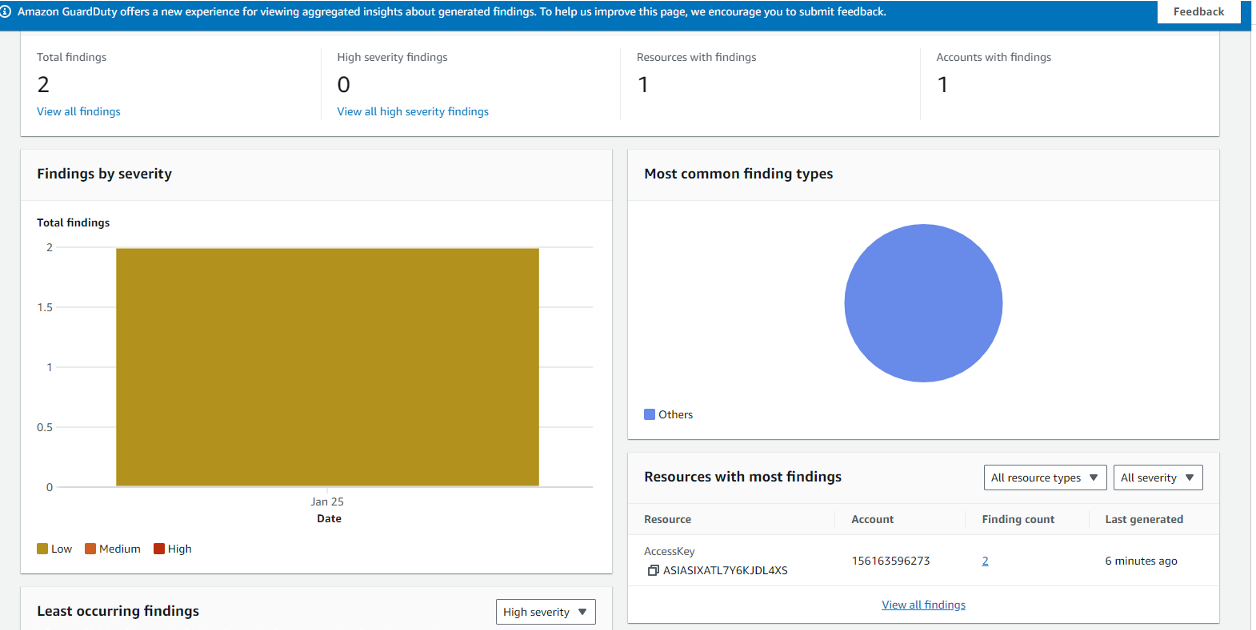
Amazon GuardDuty uses a specific nomenclature for its finding types. A finding is a notification that contains details about a potential security issue that GuardDuty discovers. The naming convention for finding types in GuardDuty is generally structured as follows:
ThreatPurpose:ResourceType/ThreatFamilyName.ThreatFamilyVariant!Artifact
Here’s a breakdown of the components:
ThreatPurpose: This represents the purpose or objective of the threat, such as ‘Backdoor’, ‘Behavior’, ‘CryptoCurrency’, ‘DefenseEvasion’, ‘Impact’, ‘Recon’, ‘Trojan’, 'UnauthorizedAccess’.
ResourceType: This indicates the AWS resource type that the finding applies to, such as ‘EC2’, ‘IAMUser’, 'S3’.
ThreatFamilyName: This is the name of the threat family that the finding belongs to.
ThreatFamilyVariant: This is a variant of the threat family.
Artifact: This is an additional specifier.
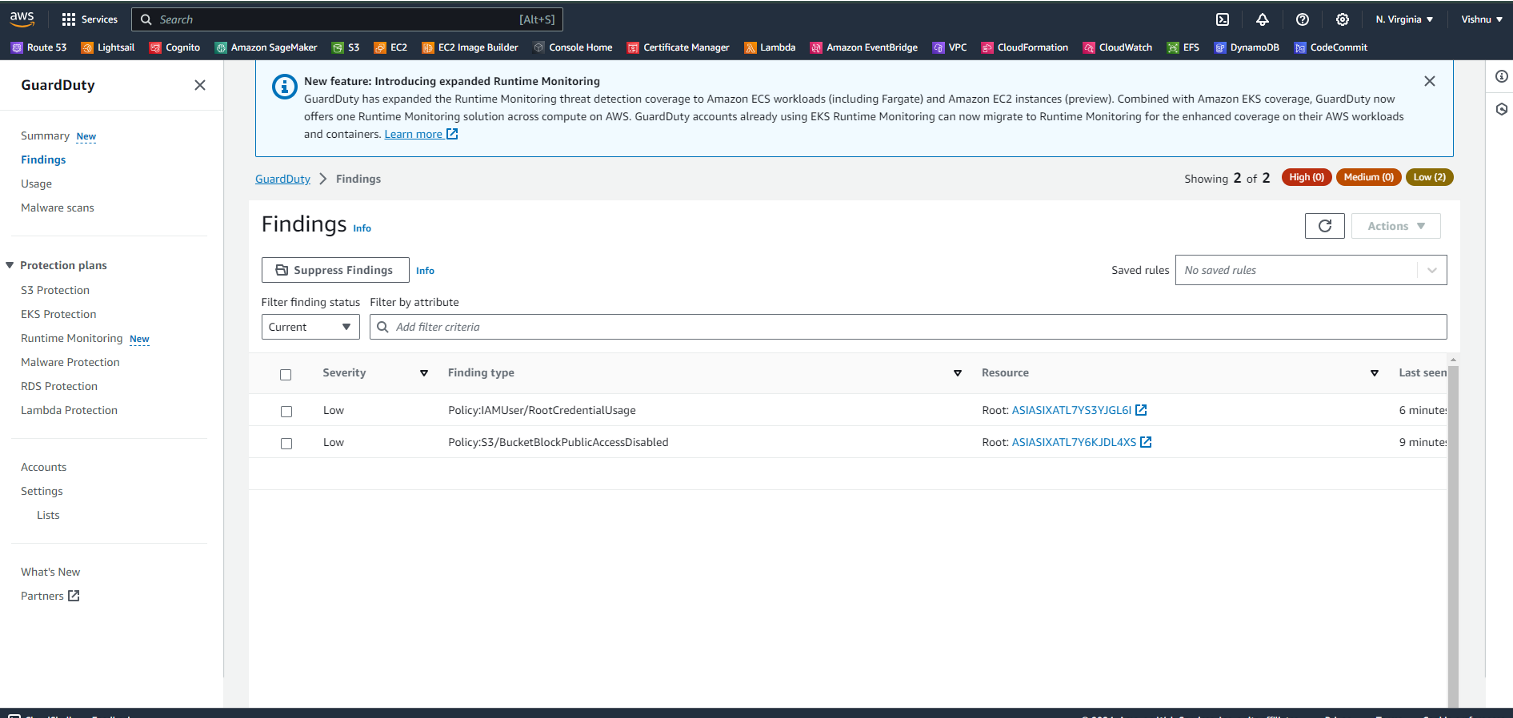
“Policy: IAMUser/RootCredentialUsage”. This finding type is part of the GuardDuty’s threat detection system. Let’s break it down:
Policy: This is the ThreatPurpose, which describes the primary purpose of a threat, an attack type, or a stage of a potential attack.
IAMUser: This is the ResourceTypeAffected, which describes which AWS resource type is identified in this finding as the potential target of an adversary.
RootCredentialUsage: This is the ThreatFamilyName, which describes the overall threat or potential malicious activity that GuardDuty is detecting.
The “Policy: IAMUser/RootCredentialUsage” finding indicates that the root credentials of an IAM user were used. The severity of this finding is typically low, but if this activity is unexpected, it can be very critical as it may indicate that your root credentials have been compromised. In such cases, it’s recommended to take action and ensure that the permissions follow the best practice of least privilege.
Conclusion
In the ever-evolving landscape of cyber threats, it’s crucial to have robust and proactive security measures in place. Amazon GuardDuty stands as a testament to this need, offering continuous security monitoring and threat detection in your AWS environment.
With its ability to analyze vast amounts of data across various AWS services, GuardDuty provides an additional layer of protection to help secure your resources. It’s easy to deploy, integrates well with other AWS tools, and is continuously updated with the latest threat intelligence.
Happy Learning :)
Subscribe to my newsletter
Read articles from Venkata Pavan Vishnu Rachapudi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu Rachapudi
I'm Venkata Pavan Vishnu, a cloud enthusiast with a strong passion for sharing knowledge and exploring the latest in cloud technology. With 3 years of hands-on experience in AWS Cloud, I specialize in leveraging cloud services to deliver practical solutions and insights for real-world scenarios. Whether it's through engaging content, cloud security best practices, or deep dives into storage solutions, I'm dedicated to helping others succeed in the ever-evolving world of cloud computing. Let's connect and explore the cloud together!