Brute Force Attack
 sudip adhikari
sudip adhikari
What is Brute Force Attack ?
A brute force attack is a Cybersecurity term describing a method hackers use to crack passwords or encryption by trying every possible combination until they find the correct one.With brute force, the hacker uses a program that mathematically attempts every possible key to break into the wireless network.
Imagine you have a locked door, and you forgot the key. A brute force attack is like trying every possible key one by one until you find the one that opens the lock. It's like checking every single combination until you get it right. It might take a long time, but eventually, it might work if the key isn't too complicated.
Fun fact : I used to set my password like something123 ,What about yours ??😂
Types of Brute Force Attack
There are mainly two types of brute force attacks :
Password Brute Force: This is when someone tries every possible combination of letters, numbers, and symbols until they guess your password. It's like trying every possible word in the dictionary until one works.
Cryptographic Brute Force: This one is a bit more complex. It's when someone tries every possible decryption key to unlock encrypted data. It's like trying every possible combination to unlock a secret code.
Motives behind Brute Force Attack
The motive behind a brute force attack is usually to gain unauthorized access to a system, network, or sensitive information. Here are some common motives:
Stealing Data: Hackers may want to access sensitive data such as personal information, financial records, or trade secrets for various purposes, including identity theft, financial fraud, or industrial espionage.
System Compromise: Some attackers aim to gain control over a system or network for malicious activities such as installing malware, launching further attacks, or disrupting operations.
Privilege Escalation: By obtaining valid credentials through a brute force attack, hackers can escalate their privileges within a system or network, gaining access to additional resources and capabilities that they wouldn't normally have.
Reputation Damage: In some cases, hackers may carry out brute force attacks to deface websites, leak sensitive information, or disrupt services, aiming to damage the reputation of individuals, organizations, or even entire industries.
Profit: There's also the potential for financial gain. For instance, hackers may steal sensitive information and then sell it on the black market, or they may demand ransom payments in exchange for restoring access to compromised systems or data.
In summary, the motives behind brute force attacks can vary widely, ranging from financial gain and data theft to sabotage and reputational damage.
How do Hacker do it ?
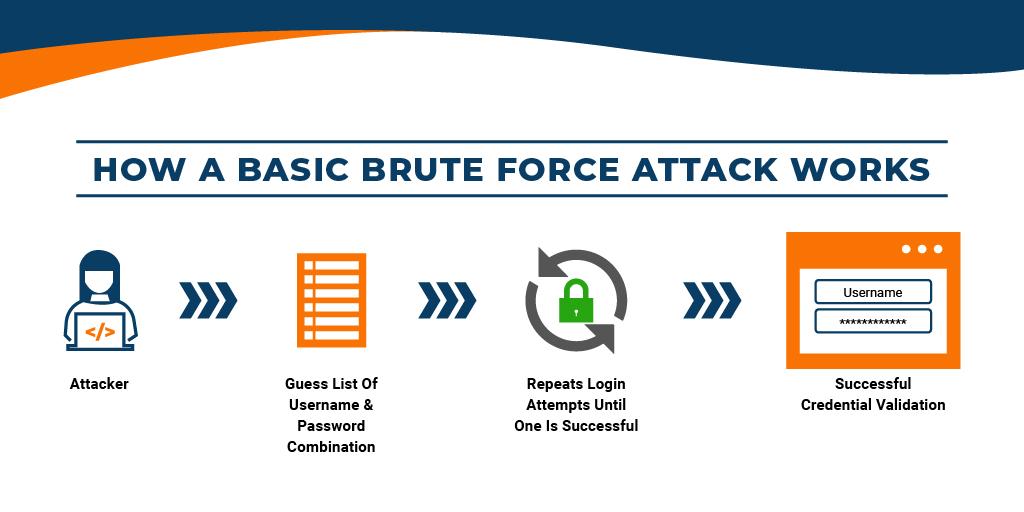
The process that hacker follows while doing brute force attack are listed below :
Finding the Target: Hackers pick something they want to break into, like a website, email account, or computer system.
Getting Ready: They gather the tools they need, like special software that tries lots of passwords automatically.
Setting Up the Attack: They tell the software what to do, like which passwords to try and where to try them.
Starting the Attack: They press the "go" button, and the software starts trying loads of different passwords one after the other.
Waiting for Success: The software keeps trying passwords until it gets the right one, or until it gives up after trying for a while.
Getting In: If they're lucky and the software finds the right password, they get into the target they were aiming for.
It's like trying every key on a keyring until you find the one that opens the lock. They just keep trying until they get it right, hoping that nobody notices what they're doing.
Brute Force Attack tools with Links
How to prevent Brute Force Attack
Strong Passwords: Use complex passwords with a mix of letters, numbers, and symbols.
Account Lockout: Temporarily lock accounts after multiple failed login attempts.
Two-Factor Authentication: Add a second layer of verification beyond passwords.
Rate Limiting: Limit the number of login attempts per time period.
CAPTCHA: Use CAPTCHA challenges to prevent automated login attempts.
Monitor and Log: Keep track of login attempts and look for suspicious activity.
Keep Software Updated: Install security updates and patches regularly.
Firewalls and IDS: Use network security tools to block suspicious traffic.
Subscribe to my newsletter
Read articles from sudip adhikari directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

sudip adhikari
sudip adhikari
I am an explorer of IT field.