From Metadata to Mayhem: Protecting AWS account from SSRF Attacks via IMDSV2
 Sourav Chakraborty
Sourav Chakraborty
Server-Side Request Forgery (SSRF) is a critical security vulnerability that allows attackers to manipulate a server into making unintended requests to internal or external systems. In this article, we explore the relationship between SSRF and the AWS Instance Metadata Service (IMDS). Let’s dive in!
SSRF: The Basics
What Is SSRF?
SSRF occurs when an attacker tricks a server into sending requests to unintended locations.
Common targets include internal services, external systems, and trust relationships.
Impact of SSRF:
Unauthorized actions: Attackers can execute arbitrary commands or perform malicious actions.
Data exposure: Sensitive information can be leaked.
What is the purpose of IMDS?The Instance Metadata Service (IMDS) in Amazon Elastic Compute Cloud (EC2) serves several crucial purposes:
Dynamic Configuration: IMDS provides a way to retrieve metadata about an EC2 instance dynamically. This metadata includes details such as the instance ID, instance type, security group information, and more. It allows applications running on the instance to adapt their behavior based on this configuration data.
Bootstrap and Initialization: During instance startup, applications can query IMDS to obtain essential information. For example, an application might retrieve its instance ID to register itself with a load balancer or to set up logging.
Security Credentials: IMDS is used by EC2 instances to retrieve temporary security credentials (such as IAM roles) associated with the instance. These credentials allow applications to securely interact with other AWS services without hardcoding long-term access keys.
Auto Scaling and Self-Healing: IMDS enables auto-scaling groups and self-healing mechanisms to retrieve metadata about the instance they manage. This information helps them make informed decisions about scaling actions or recovery procedures.
User Data: IMDS provides access to user data that can be passed to an instance during launch. User data often contains scripts or configuration instructions that customize the instance behavior.
Troubleshooting and Debugging: When diagnosing issues or debugging applications, administrators can query IMDS to gather information about the instance’s environment, network configuration, and more.
The Instance Metadata Service (IMDS) in Amazon Elastic Compute Cloud (EC2) allows you to access metadata from a running EC2 instance. There are two versions of IMDS:· IMDSv1 (Instance Metadata Service Version 1): This is a simple request/response method. You can retrieve metadata by making an HTTP GET request to the IMDS endpoint.To get the instance ID, you can use the following command:
curl http://169.254.169.254/latest/meta-data/instance-id
· IMDSv2 (Instance Metadata Service Version 2): IMDSv2 uses a session-oriented model. Before retrieving metadata, you must first create a session by obtaining a token using a PUT request. This token is then included in subsequent GET requests to access metadata..
SSRF and IMDS Relationship:
o Attackers exploit SSRF to access IMDS.
o IMDSv1 vulnerabilities allow unauthorized access to instance metadata.
o IMDSv2 mitigates these risks by introducing session tokens.
IMDSv2: The Solution
What Is IMDSv2?
IMDSv2 enhances security by requiring session tokens.
Tokens are short-lived and tied to the instance’s lifecycle.
IMDSv2 prevents unauthorized requests to the metadata endpoint.
Enforcing IMDSv2:
- Configure your EC2 instances to use IMDSv2.
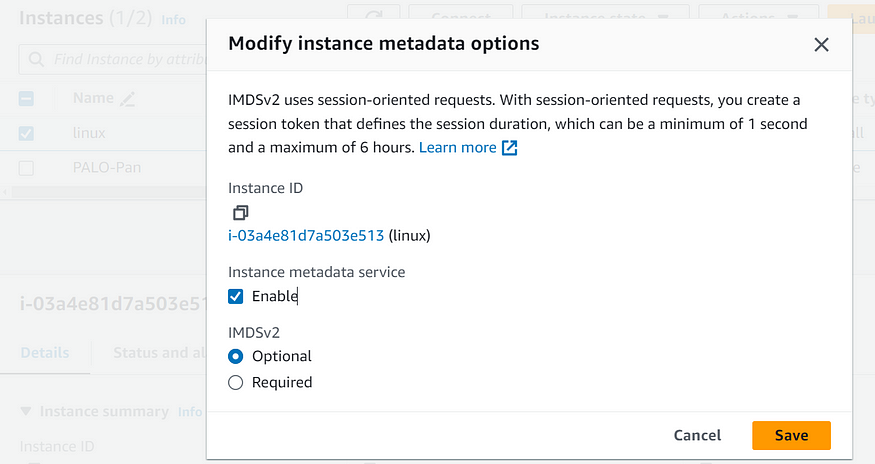
To enable Instance Metadata Service Version 2 (IMDSv2) for existing Amazon EC2 instances, we can follow these steps using aws AWS console :
· Modify Instance Metadata Options:
Open the Amazon EC2 console at this link.
In the navigation pane, choose Instances.
Select the EC2 instance for which you want to enforce IMDSv2.
Choose Actions, then select Instance Settings, and finally click Modify instance metadata and select IMDSV2 as required
Set it as the default for your account.
Modify existing instances programmatically.
Best Practices
Secure Your Code:
Validate user input to prevent SSRF.
Avoid hardcoding sensitive data.
Logging and Monitoring:
Log metadata requests.
Monitor for unusual activity.
We’ll explore real-world scenarios and case studies that highlight the impact of SSRF and its connection to the AWS Instance Metadata Service (IMDS).
Case Study 1: Exploiting IMDSv1
Scenario:
An attacker gains access to a vulnerable web application that allows users to fetch external content via URLs. The application uses SSRF-prone code to retrieve data from arbitrary URLs.
Attack Steps:
The attacker crafts a malicious request with an internal IP address (e.g., http://169.254.169.254/latest/meta-data/instance-id)..)
The application blindly fetches data from the specified URL.
The attacker successfully retrieves sensitive information, such as the EC2 instance ID, security credentials, or other metadata.
Impact:
The attacker gains unauthorized access to instance metadata.
They can potentially escalate privileges or compromise the entire infrastructure.
Case Study 2: Using IMDSv2 to Prevent SSRF Attacks
Scenario:
A security-conscious organization migrates to IMDSv2 to enhance security and prevent SSRF attacks.
Implementation:
The organization updates their EC2 instances to use IMDSv2.
IMDSv2 requires session tokens obtained via a PUT request before accessing metadata.
The application code is modified to include the session token in metadata requests.
Benefits:
IMDSv2 prevents unauthorized requests to the metadata endpoint.
Even if an attacker exploits SSRF, they cannot directly access sensitive metadata without a valid token
Conclusion
Understanding SSRF and securing IMDSv2 is crucial for protecting AWS infrastructure. Implement best practices, stay informed, and keep your systems safe!
Most of the CSPM tools like AWS SecurityHub notifies alerts if IMDSv1 is being used.
Security is a shared responsibility. Let’s build robust and secure applications together! 🛡️
Subscribe to my newsletter
Read articles from Sourav Chakraborty directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
