Powerpipe Insights: Your Comprehensive DevOps Dashboard and Compliance Benchmarks Guide
 Debjyoti Koner
Debjyoti Koner
In today's fast-paced digital world, DevOps and security teams face numerous challenges in effectively and securely managing cloud infrastructure. From meeting industry standards to optimizing resource usage and controlling costs, the complexities of cloud setups can lead to inefficiencies and operational issues.
Fortunately, there's a solution: Powerpipe. This robust tool offers a variety of features designed to address the common issues encountered by DevOps and security teams. Let's explore how Powerpipe can help your teams overcome these obstacles and simplify cloud management processes.
Are you seeking a robust tool to visualize your cloud infrastructure and ensure compliance with industry standards? Look no further than Powerpipe! In this guide, we will dig into Powerpipe, an open-source tool from Turbot, that empowers DevOps teams to gain valuable insights and effortlessly maintain compliance.
Introduction to Powerpipe
Powerpipe is a versatile tool designed to streamline DevOps operations by offering a suite of features:
Visualize Cloud Infrastructure: Utilize pre-built dashboards tailored for AWS, Azure, GCP, Kubernetes, and more to gain insights into your cloud resources' quantity, cost, usage, and relationships.
Run Security and Compliance Benchmarks: Assess your cloud environment's compliance with standard frameworks such as CIS, GDPR, NIST, PCI, SOC 2, and more using pre-built benchmarks.
Getting Started with Powerpipe
Before diving in, let's ensure we have the prerequisites installed:
Install Powerpipe, Steampipe, and the AWS plugin for Steampipe.
# Install Powerpipe sudo /bin/sh -c "$(curl -fsSL https://powerpipe.io/install/powerpipe.sh)" # Install Steampipe sudo /bin/sh -c "$(curl -fsSL https://steampipe.io/install/steampipe.sh)" # Install the AWS plugin for Steampipe steampipe plugin install aws
Starting the Steampipe Service:
To get started, let's start the Steampipe service:
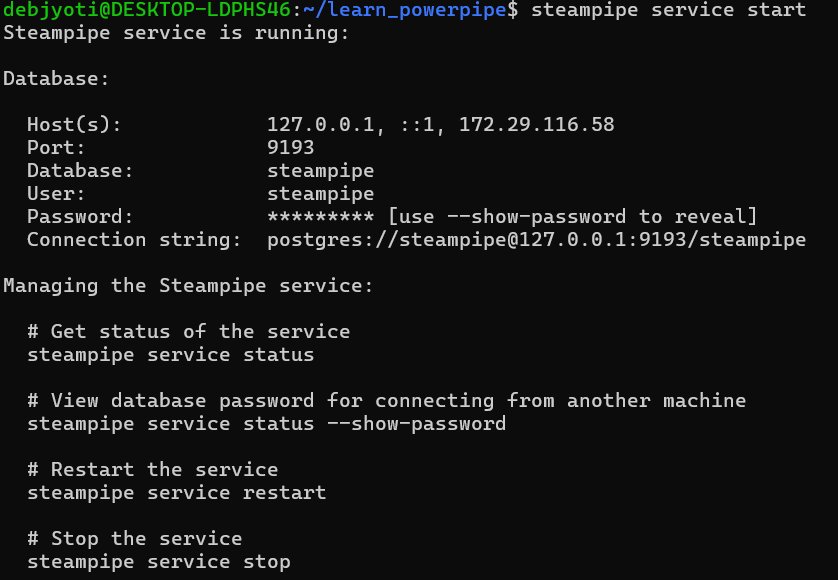
steampipe service start
Once started, the Steampipe database will be up and running, ready to handle your queries.
Running Queries:
Now that Steampipe is running, let's run an ad-hoc query to retrieve information about AWS accounts. We'll use Powerpipe, which seamlessly integrates with Steampipe, to execute our query:
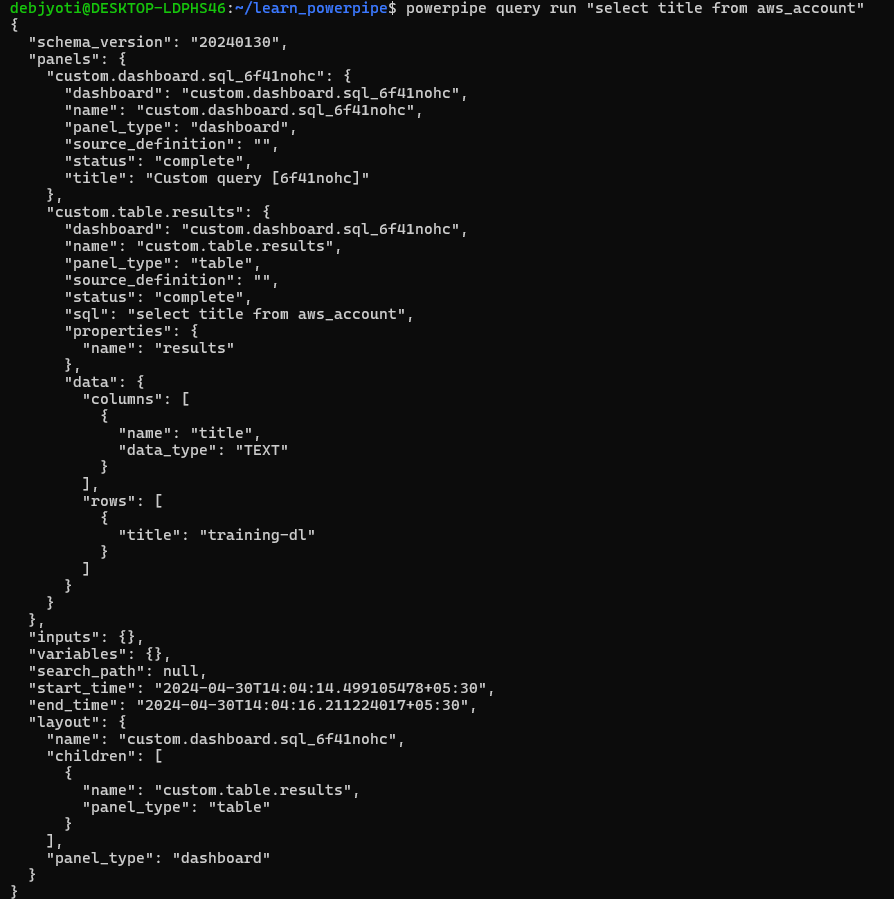
powerpipe query run "select title from aws_account"
This query will fetch the titles of all AWS accounts in your environment, providing you with valuable insights into your cloud setup.
Now, let's Visualize Cloud Infrastructure:
Powerpipe dashboards offer dynamic data visualizations in a format known as HCL (HashiCorp Configuration Language). These dashboards are conveniently packaged into mods for easy distribution and use. Mods, in essence, are self-contained collections of Powerpipe resources like dashboards, benchmarks, queries, and controls. These resources are defined in simple text files using HCL. Powerpipe operates within the context of a mod, meaning it always interacts with the resources within that mod.
Creating your own dashboard is straightforward, thanks to the simplicity of HCL. However, if you prefer not to create one from scratch, there's a wealth of pre-existing dashboards available on the Powerpipe Hub, providing a variety of options to suit different needs.
When Powerpipe is invoked, it loads the mod from a designated location, typically the current directory unless specified otherwise. This mod serves as the framework within which Powerpipe operates, enabling users to leverage its functionalities effectively.
Let's create a new directory for our mod and initialize this mod :
mkdir learn_powerpipe
cd learn_powerpipe
powerpipe mod init
Powerpipe mods may depend on other mods. When running Powerpipe from a mod, all dashboards in the mod and its direct dependencies will be available to run. Let's install the AWS Insights mod.
powerpipe mod install github.com/turbot/steampipe-mod-aws-insights
Now let's start the Powerpipe server:
powerpipe server
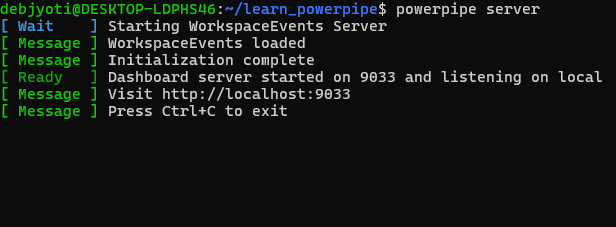
Navigate tohttp://localhost:9033in your browser to explore the available dashboards.
From AWS VPC Detail to EC2 Instance Insights, these dashboards offer rich visualizations to understand your cloud resources better.
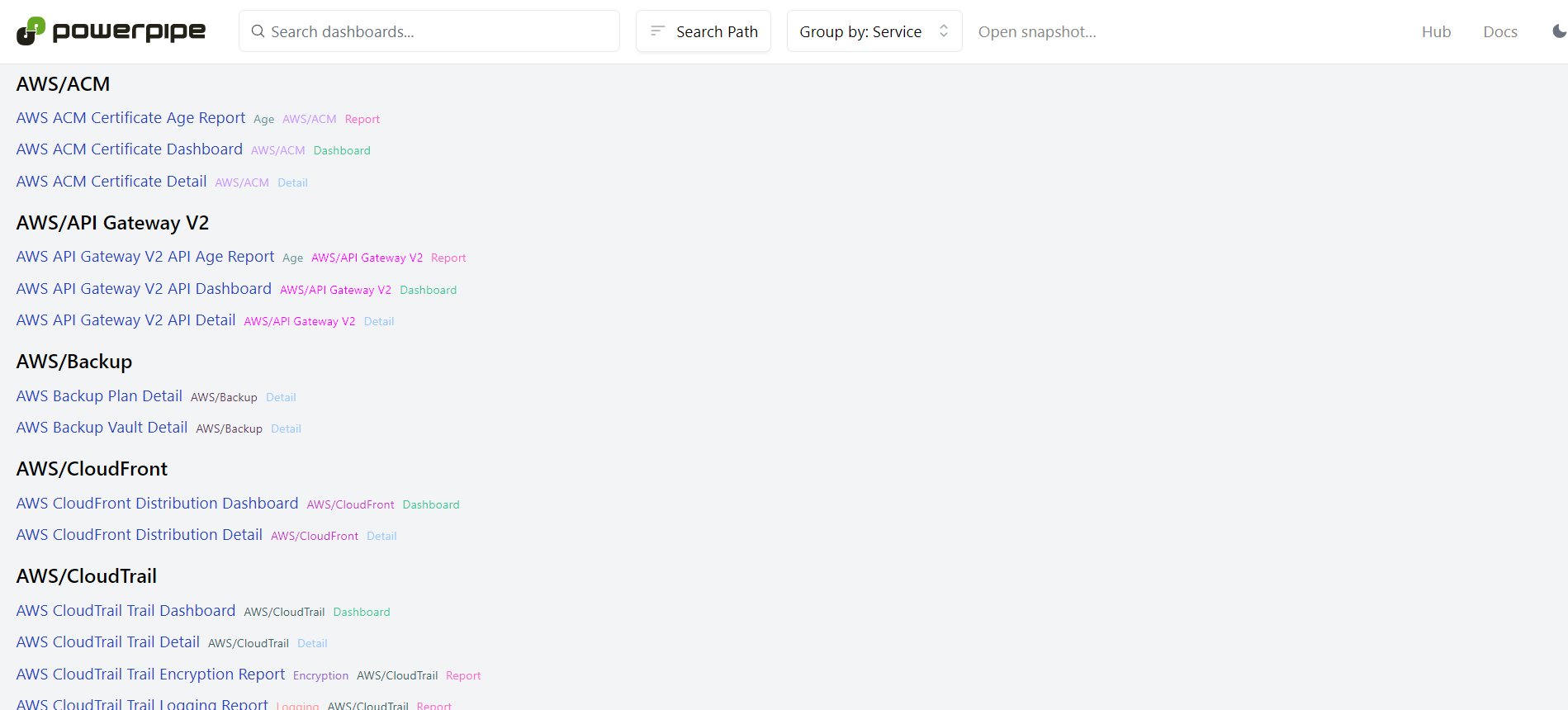
Let's view the**AWS VPC Detail. You can scroll to find it, or use the searchbox*at the top of the page.*
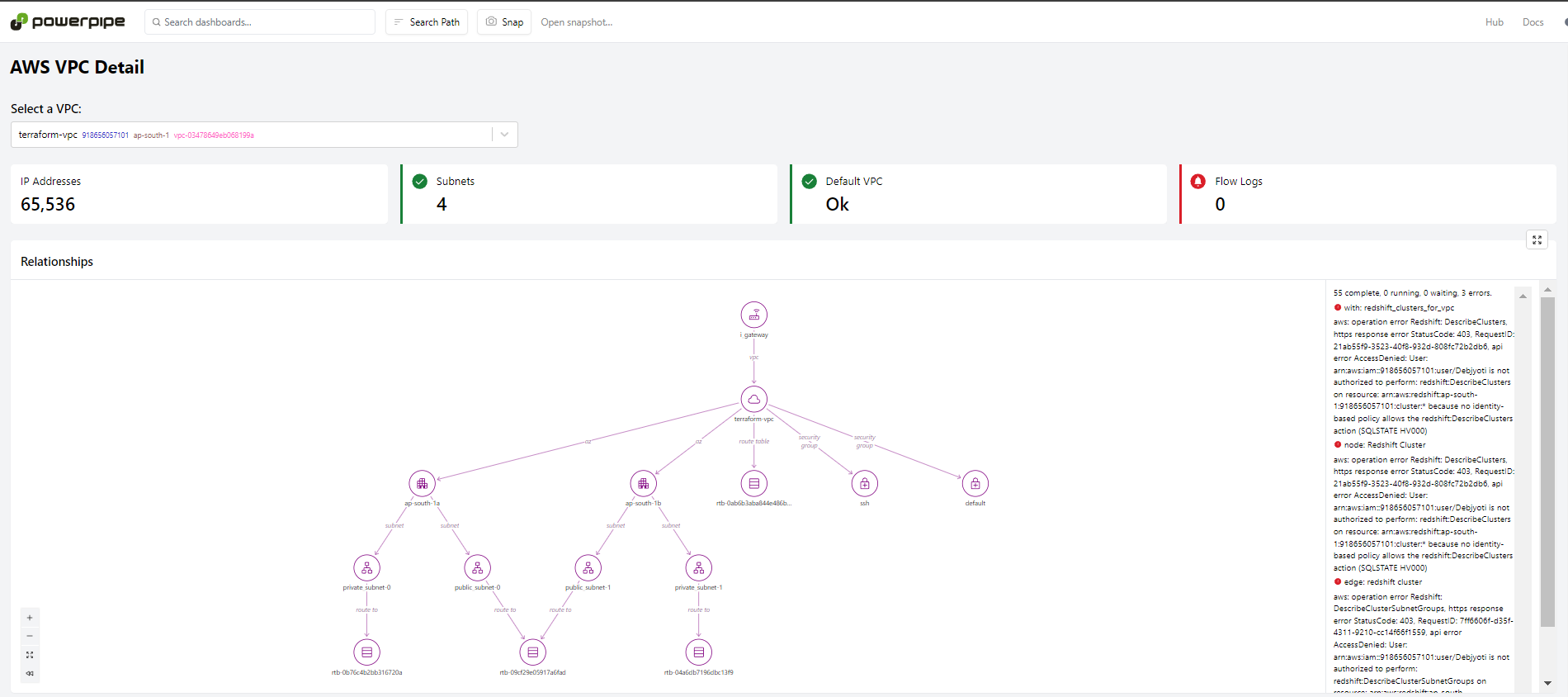
You can type in the search bar at the top of any page to navigate to another dashboard. Alternatively, you can click the Powerpipe logo in the top left to return to the home page. When you are finished, you can return to the terminal console and typeCtrl+cto stop the server.
Run security and compliance benchmarks
Powerpipe benchmarks provide a robust framework for evaluating environments against various control frameworks, including industry standards such as CIS, NIST, HIPAA, and customized control groups. These benchmarks assist in assessments related to security, compliance, operations, and cost.
To start benchmarking, let's install the AWS Compliance mod and run some benchmarks.
powerpipe mod install github.com/turbot/steampipe-mod-aws-compliance
Let's run the CIS 3.0.0 benchmark:
powerpipe benchmark run aws_compliance.benchmark.cis_v300
The benchmark will run, reporting progress as it executes. When it is complete, you will see the results printed to the console.
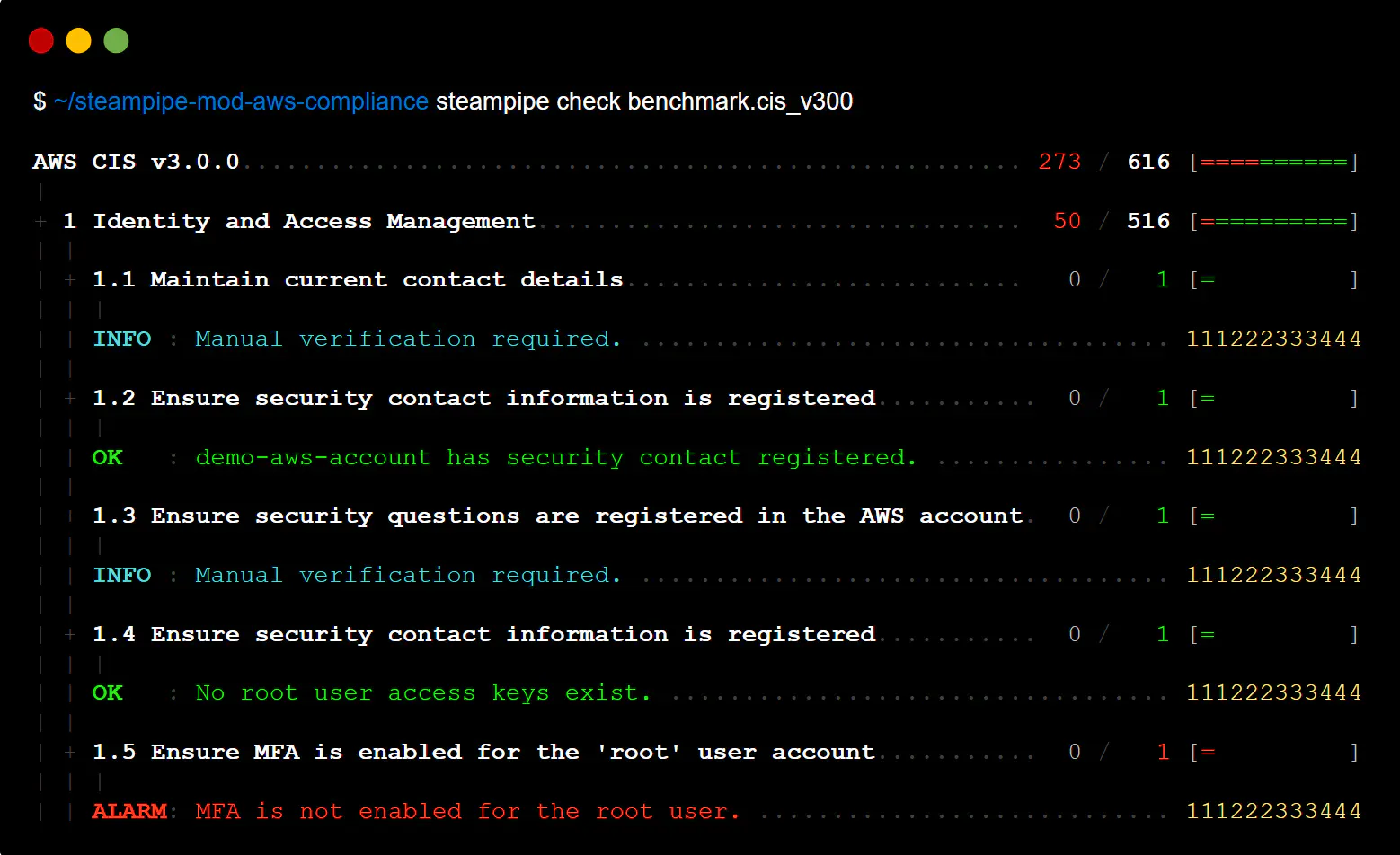
This mod is designed to evaluate AWS accounts against compliance frameworks like the CIS Amazon Web Services Foundations Benchmark.
Once the mod is installed, we can utilize its benchmarks and controls to assess the compliance status of our AWS environment. This involves performing checks against specific criteria to ensure compliance with defined standards and best practices.
By making use of Powerpipe's features and the resources from the AWS Compliance mod, users can effectively monitor and maintain compliance in their AWS infrastructure. This aids in reducing risks and enhancing overall security measures.
Running Benchmarks Non-Interactively
Thepowerpipe benchmark runcommand provides a versatile way to run benchmarks without interaction. You can choose specific controls to run and export the results in various formats like CSV, HTML, JSON, Markdown, NUnit3, Snapshot (PPS), and ASFF.
To run a benchmark non-interactively and export the results in HTML format, use the command below:
powerpipe benchmark run aws_compliance.benchmark.cis_v300 --output html > results.html
This command will execute the CIS 3.0.0 benchmark and save the results in an HTML file namedresults.html. You can customize the benchmark, control the output format, and redirect the output to the desired file as needed.
Benchmarks are also accessible as dashboards, enabling you to group and sort the results interactively. Begin the server (if it is not running), and open the dashboard homepage in your browser (http://localhost:9033):
powerpipe server
Notice that the benchmarks from the AWS Compliance now appear in the list. You can use theGroup bybutton at the top of the page toGroup by: ModorGroup by: Typeto find them more easily.
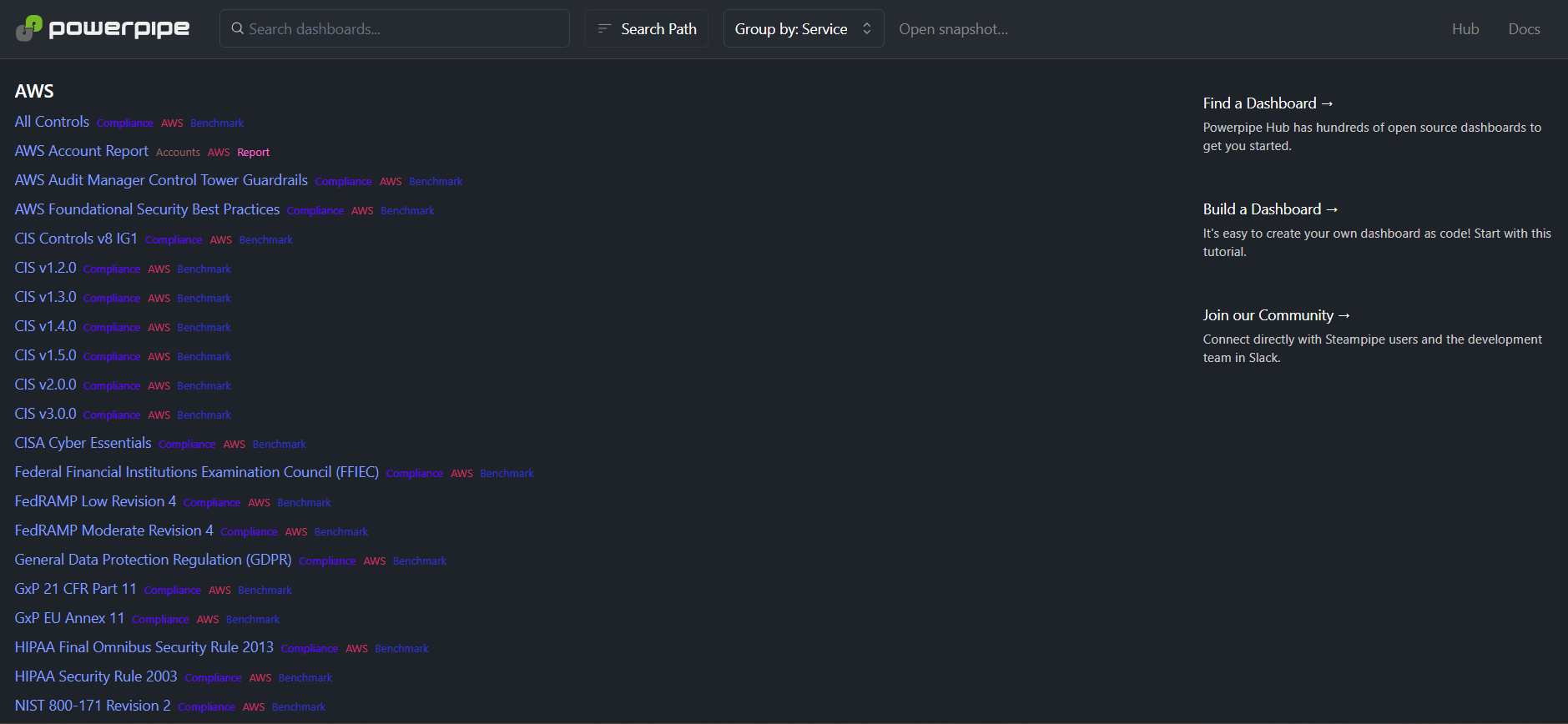
Click onCIS v3.0.0to run the CIS 3.0.0 benchmark. You will see the results update as it runs, but you can interact with it even while the benchmark is running.
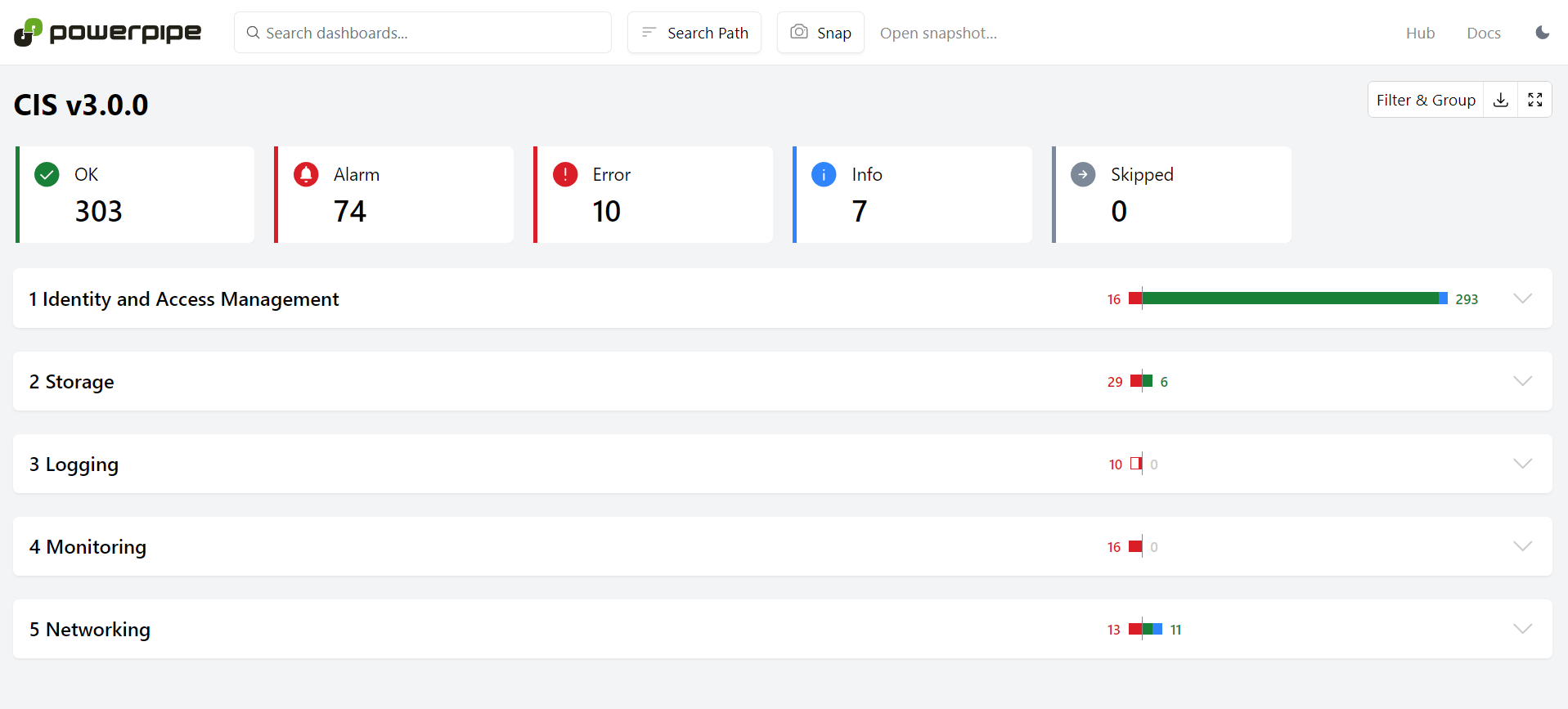
Click on a section to expand it, and click again to collapse it. You can drill down to see the results for each individual control!
As with any dashboard, you can modify the search path, capture a snapshot*once the **benchmark is finished, view details in the panel view , and download the results in a CSV file*.
Conclusion
With Powerpipe, following industry standards is easy. By using thepowerpipe benchmark runcommand, you can simplify the compliance assessment process and save the results in different formats as needed.
Ready to manage compliance assessment with Powerpipe? Begin running benchmarks now!
Subscribe to my newsletter
Read articles from Debjyoti Koner directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
